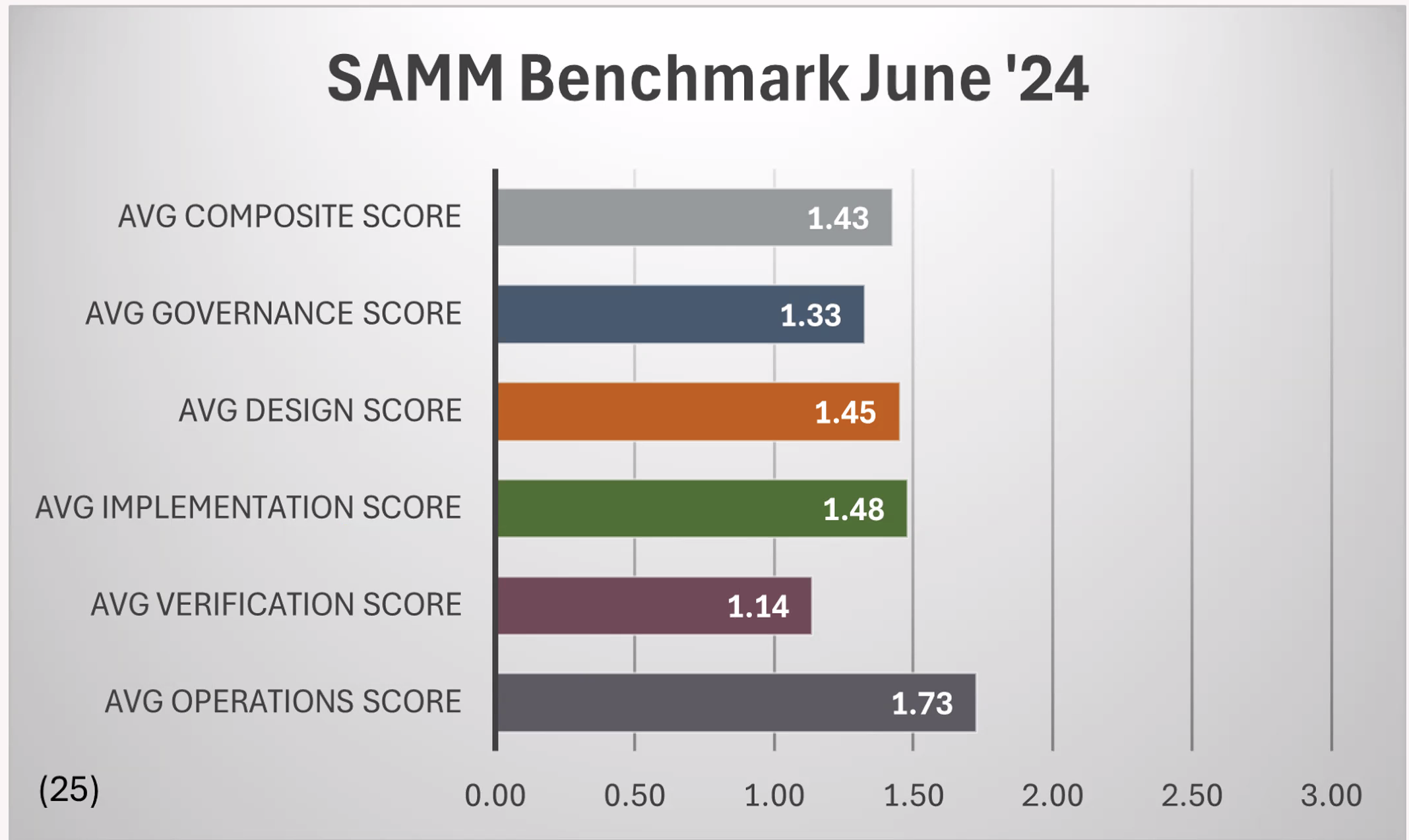



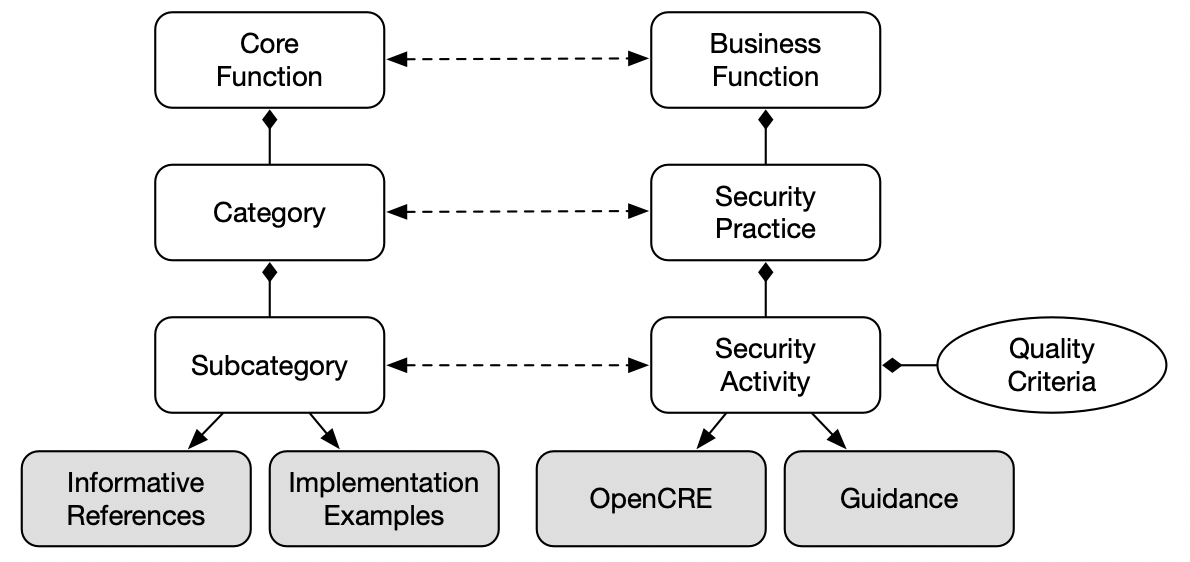



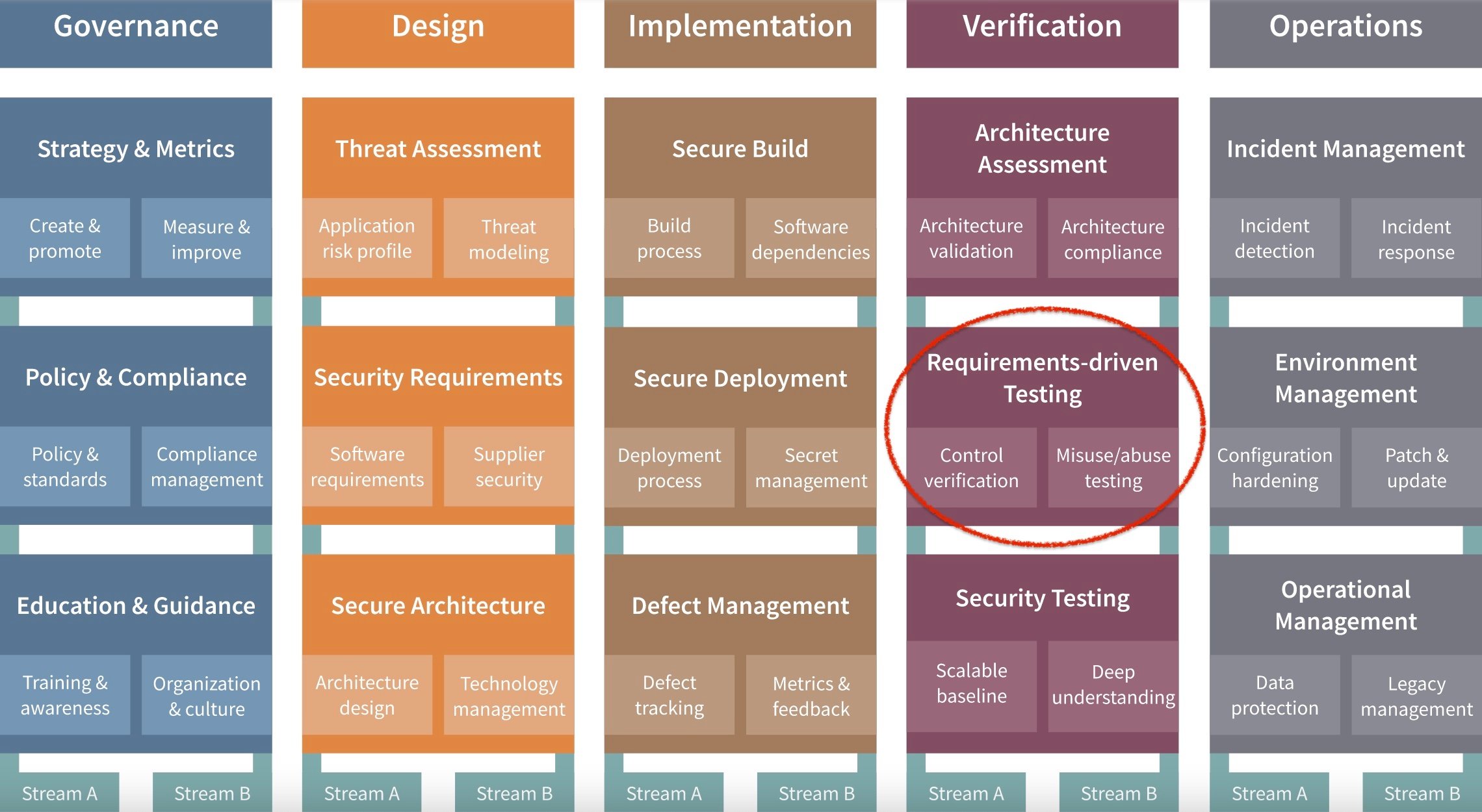
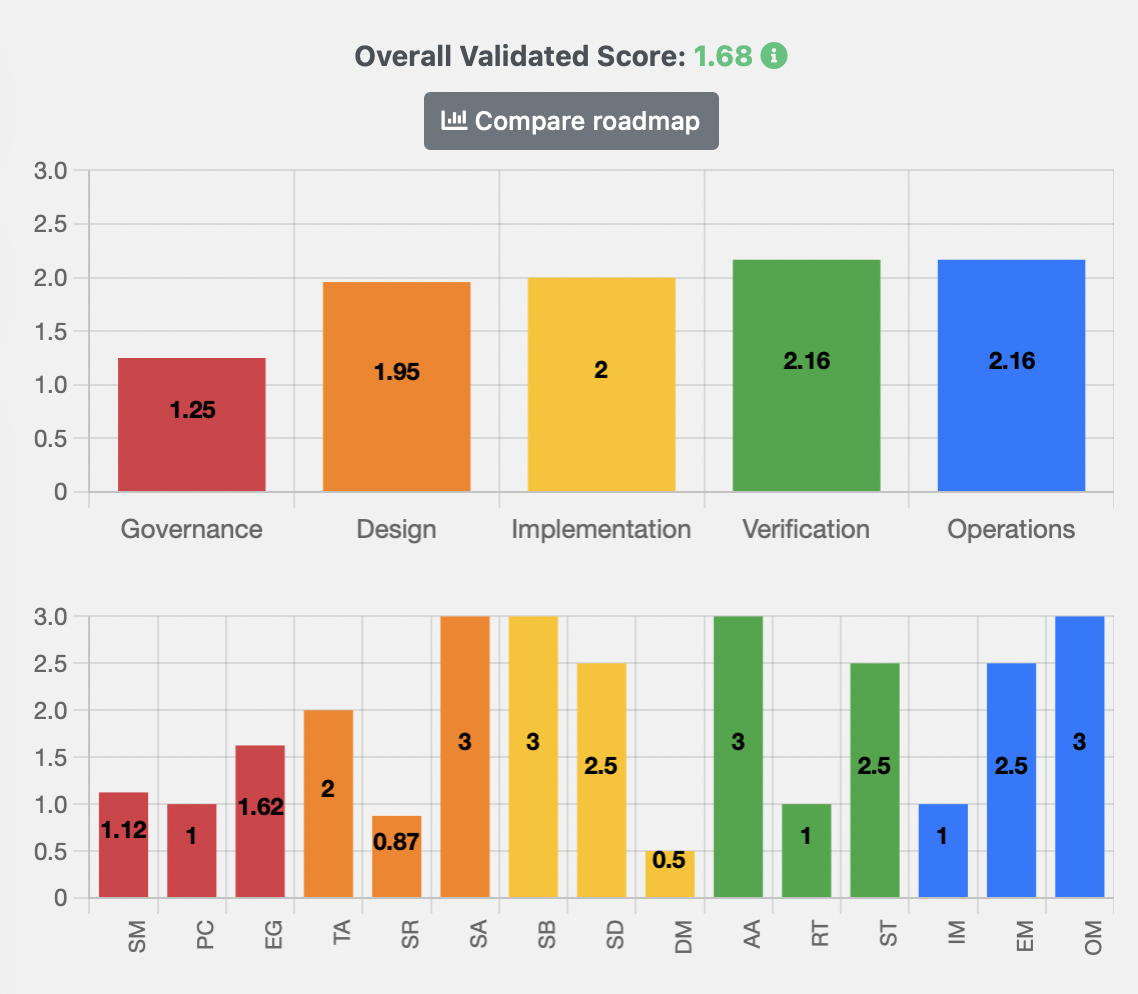
Aram is the founder and the CEO of Codific. With over 15 years of experience, he has a proven track record in building complex software systems by explicitly focusing on software security. Aram has a PhD in cybersecurity from DistriNet KU Leuven. His contributions to the refinement and streamlining of the LINDDUN privacy engineering methodology have been incorporated into ISO and NIST standards. Aram is also a core contributor to OWASP SAMM project and the architecture and security mentor for all our teams. If you have questions, reach out to me hereContact
View all posts








