
This is the success story of how Zebra Technologies works with SAMMY and Codific to implement OWASP SAMM
“Spreadsheets are not the way to manage large organizations, you need a solid tool,”
Dr. Jasyn Voshell, director of product security at Zebra Technologies

From logistics to robotics to healthcare, across 8 major industries and in 128 countries, Zebra Technologies is the best in class. Cutting edge technology and smart analytics are core to their business of keeping everything and everyone visible, connected and optimized.
What is OWASP SAMM?
As the readers of this blog now know, OWASP SAMM is the best model to manage your security posture. SAMM covers 5 business functions split over 15 security practices containing a total of 90 security activities. It is an exhaustive and prescriptive list of things you need to do as an organization to measure and improve your application security programme, spread over three maturity levels. Tangible management of your security posture will lay the groundwork for certifications such as ISO27001 and compliance with standards such as NIST SSDF. Under SAMM, the output of the efforts is an improved security posture, the byproduct is compliance. It is the ideal model for executives who want to systematically manage security risk across their organization, rather than the “check boxes and pray” driven compliance approach.
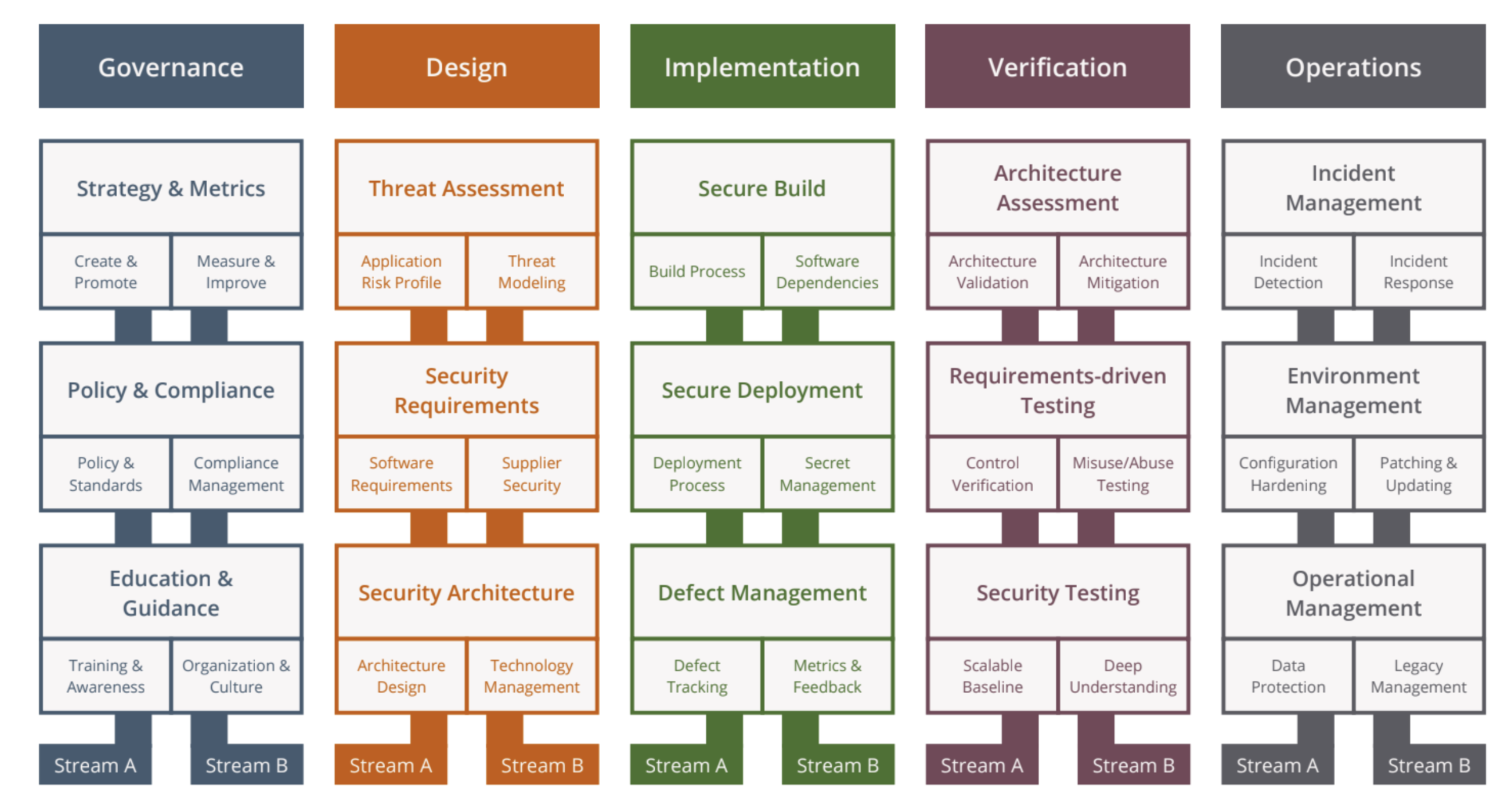
OWASP SAMM: Software Assurance Maturity Model
The executives at Zebra Technologies immediately realized the power of the model. They started implementing it, but soon realized that at a large scale, they need a dedicated tool to manage the process.
What is Codific’s role in OWASP SAMM?
At the OWASP community, the CEO of Codific, Dr. Aram Hovsepyan, is a core member of the intellectual team behind the SAMM model. Meanwhile Codific is working on a free to use OWASP SAMM management tool called SAMMY. Our vision is to leverage the model and turn it into an iterative improvement process with different roles and responsibilities allocated per activity. Zebra was the first major organization to see the power of the SAMMY tool and to provide Codific with suggestions and user stories guiding the product roadmap. Thus the newest dedicated version of the tool became well fitted for the complex environment of large multinational organizations.
We are now a few months down that road, the relationship between Zebra and Codific is blossoming and other large organizations are starting to notice SAMM and SAMMY.

“Codific’s team goes above and beyond expectations and its intricate expert knowledge of SAMM helps us better understand and implement it.” Dr. Voshell
What are the challenges in implementing OWASP SAMM?
OWASP SAMM is a prescriptive model that is technology, process, and organization agnostic. The model fits any software development process, industry or environment. However thanks to / because of that the prescriptive guidance is very high-level by design. Thus there are two major considerations per activity that the model users need to address in order to set up an efficient application security programme:
- How can we practically implement this activity for our environment (by environment we refer to the tech stack, development process, tooling, etc)?
- How should we prioritize the different activities and improvements? There are 90 activities in SAMM and trying to boil the ocean is not sensible.
Practical Implementation Guidance for OWASP SAMM
The OWASP SAMM core team has been discussing the best way to provide practical guidance per activity and per industry. As the possibilities are broad, providing up-to-date guidance for any specific setup is challenging and not even realistic. However there are some relatively high-level guidelines in the works. The guidance is expected to be largely community driven, but curated by the core team. Many of the guidance elements per activity are readily available in other OWASP projects, and those will be mapped to SAMM activities.
On the other hand for many organization-specific details the expertise comes from within the organization. Hence for large organizations the sweet spot is to combine the internal and the external experts. The internal experts know everything about the environments, the external experts are SAMM experts and will help mold the process. Together they can define the practical implementation and the improvement roadmap. The OWASP SAMM project provides a list of practitioners that can assist with SAMM assessments and the implementation of SAMMY. Codific is that external expert for Zebra.
Dr. Voshell: “From a company perspective, Codific is able to pivot quickly to work to our needs at our speed. They do not feel like a vendor but an extension of our team.”
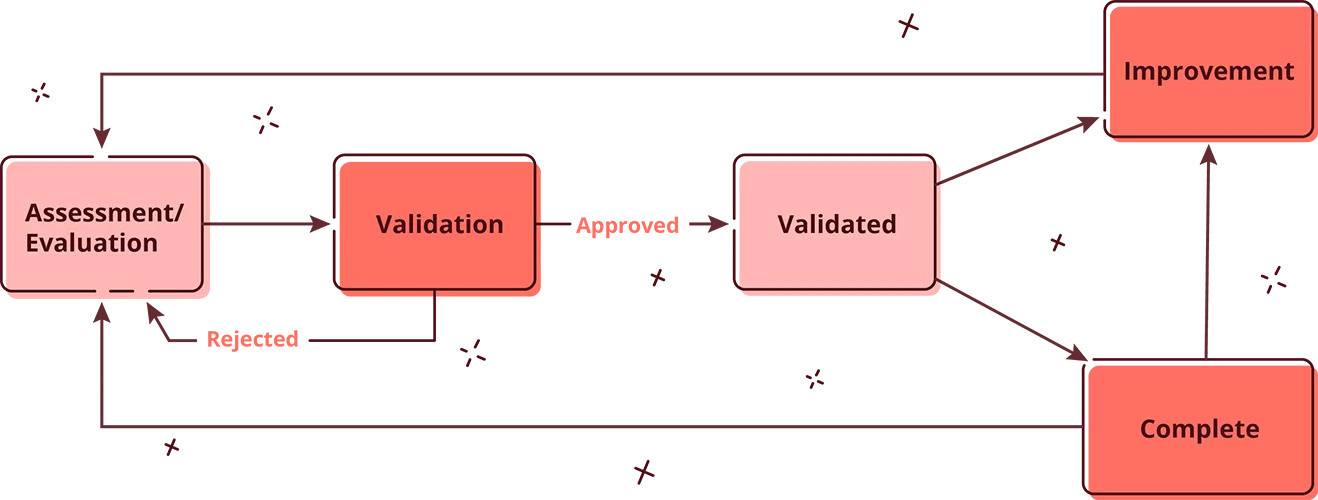
The SAMMY workflow.
Prioritization in OWASP SAMM
Prioritization is the second key aspect for the successful implementation of SAMM. No organization should aspire to have the maximum maturity level in all activities. This would be prohibitively expensive. Instead activities are weighted and prioritized based on factors such as risk, impact and cost. To this purpose SAMMY has developed weighted prioritization metrics that help in the structural and consistent prioritization of activities over large and small organizations. This is a core feature of SAMMY that will be further built upon in the future SAMMY roadmap. The experience with Zebra has helped to define the prioritization mechanisms.
SAMM is the conceptual map on which to draw your risk management strategy. It can visualize where you are and where you want to be. SAMMY is the easiest and most powerful way to implement SAMM.
Dr. Voshell: “SAMMY allows us to have an accurate consistent source of truth.”
Codific, and the other experts in the OWASP community are here to help at every step of the way.
Dr. Voshell: “Codific is a great company to partner with.”

What will the future of security management bring?
Zebra is an early adopter in the new world where security management complexity is managed with adequate models and tools. We actually know the future. Not the nitty gritty details, but we do know that the future will bring at least these three things: more threats, more complexity, and more regulations. Excel sheets and compliance checklists will crumble under the increased complexity. There is a shift from compliance driven security management to risk driven security management. The answers to the complex challenges of tomorrow lie in the integration with ecosystems of experts, such as OWASP, who are continuously updating us and our systems with the answers to the latest threats. Those who position themselves early will triumph, those who are late to adapt will scramble putting out fires day after day. Which one do you want to be?
How can we get started with SAMM and SAMMY?
If you are entirely new to SAMM, you should start by studying the model. Once you feel ready for your first SAMM assessment you can use the free SAMMY tool to help you in the process. From there you can start using the other process oriented features of SAMMY, such as role assignment, prioritization and roadmaps.
If you are a large organization and you would like a dedicated system with a service levels agreement (SLA) or you want assistance with an assessment or audit, please reach out to us. We are super excited to help more organizations on this journey to build a simple and safe digital future.
