Introduction to security in the context of outsourced development
Many organizations rely on outsourced software development to accelerate innovation, reduce costs, and acc…
Introduction to software security requirements
Despite clearly understanding the importance of security requirements, organizations seem to struggle with figuring out how …
Cybersecurity in general and application security (AppSec) in particular are extremely challenging topics. They run broad and deep and success in one area is just not enough. A s…
Application security requires a systematic approach and requires dealing with software security throughout every stage of the software development lifecycle (SDLC). Howeve…
Introduction to the security tool frenzy
“Invest in Outcomes, not Tools and Capabilities” – Paul Proctor, Gartner.
Security tools are overrated. They are e…
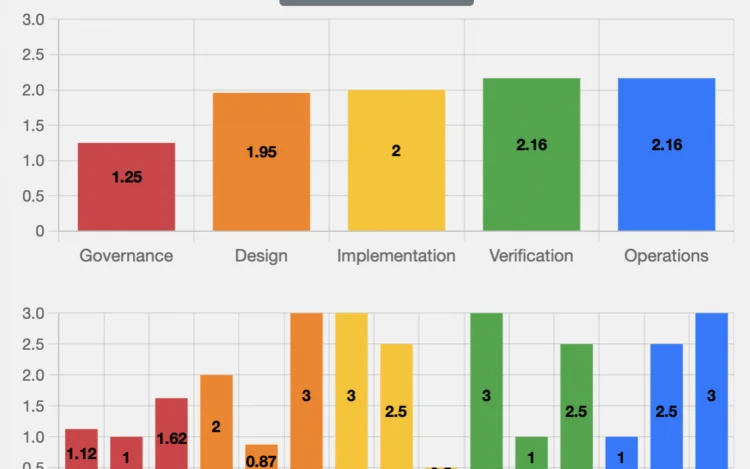
Security verification is about validating that a system or application adheres to predefined security requirements or standards. There are many types of security verificatio…

Codific is proud to receive the renewal of the ISO 27001 audit certification.

ISO 27001 a is a widely recognized international standard that specifies the requirements for an Inf…
Ever heard the saying “our team is our greatest asset”. I’d dare to say that this is rule number 1 through 10 if you are running a company. Any company! Well, exce…
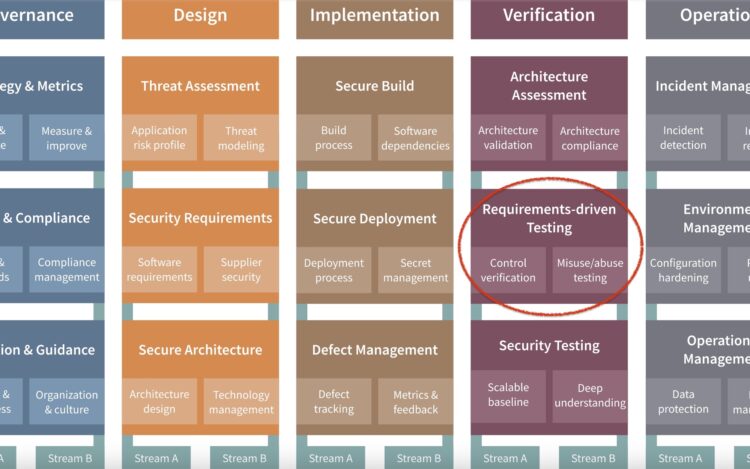
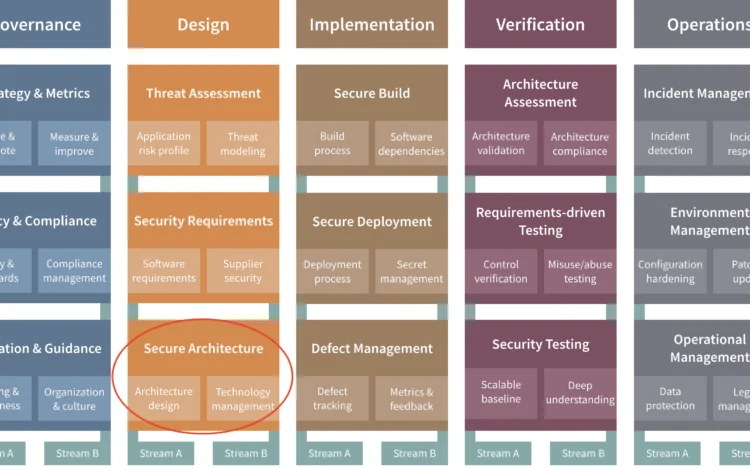
Secure architecture in a nutshell
The secure architecture practice focuses on security during the architectural design of the software system. The essence of this practice is t…
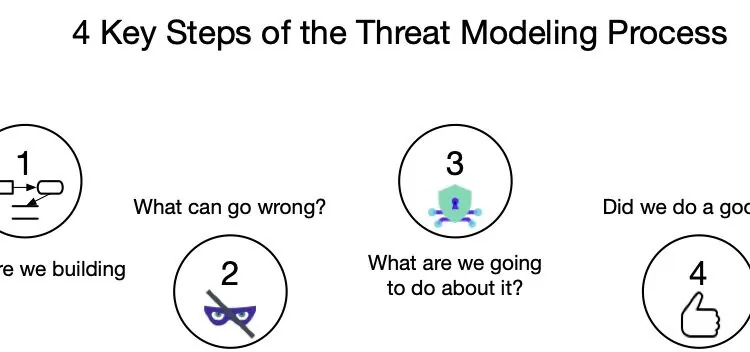
Threat modeling yields the highest return on investment when it comes to your Application Security program. Even if your current security posture is close to a zero OWASP SAMM sco…