OWASP SAMM
OWASP SAMM is the default model in SAMMY. It is the reason why we created SAMMY in the first place.
or
Fill out an OWASP SAMM assessment
The workflow starts by filling out the assessment questions. This could all be filled out by you, or different business functions, activities and streams can be assigned to different users, so each section is filled out by the most relevant person.
Validate an OWASP SAMM assessment
Validation is done on a stream level. When done internally it is typically done by the person that is leading the overall assessment. He or she reviews the answers and the evidence presented, should he not be satisfied the stream returns to the assessment step with his comments. If the assessor approves the stream moves to the improvement track. In some cases the validator may be an external expert.
Implement security roadmaps
When a score on a stream is validated the question arises: “Is this good enough”. If it is: great, then the stream is completed. If it is not good enough an improvement process is initiated, a new target score is set together with a target date. The process is assigned to a team member. At the end of the improvement process the stream returns to assessment to evaluate it’s situation.
Clear visualization of score
In SAMMY you have a quick overview of score in the left navigation menu, this is available both in the light and the full version. In the full version you also have more extensive reports on the reporting tab, these include:
- Overview of score per business function.
- Scores per practice.
- Scores per business function
- Comparison between scopes
- Historic growth per business function
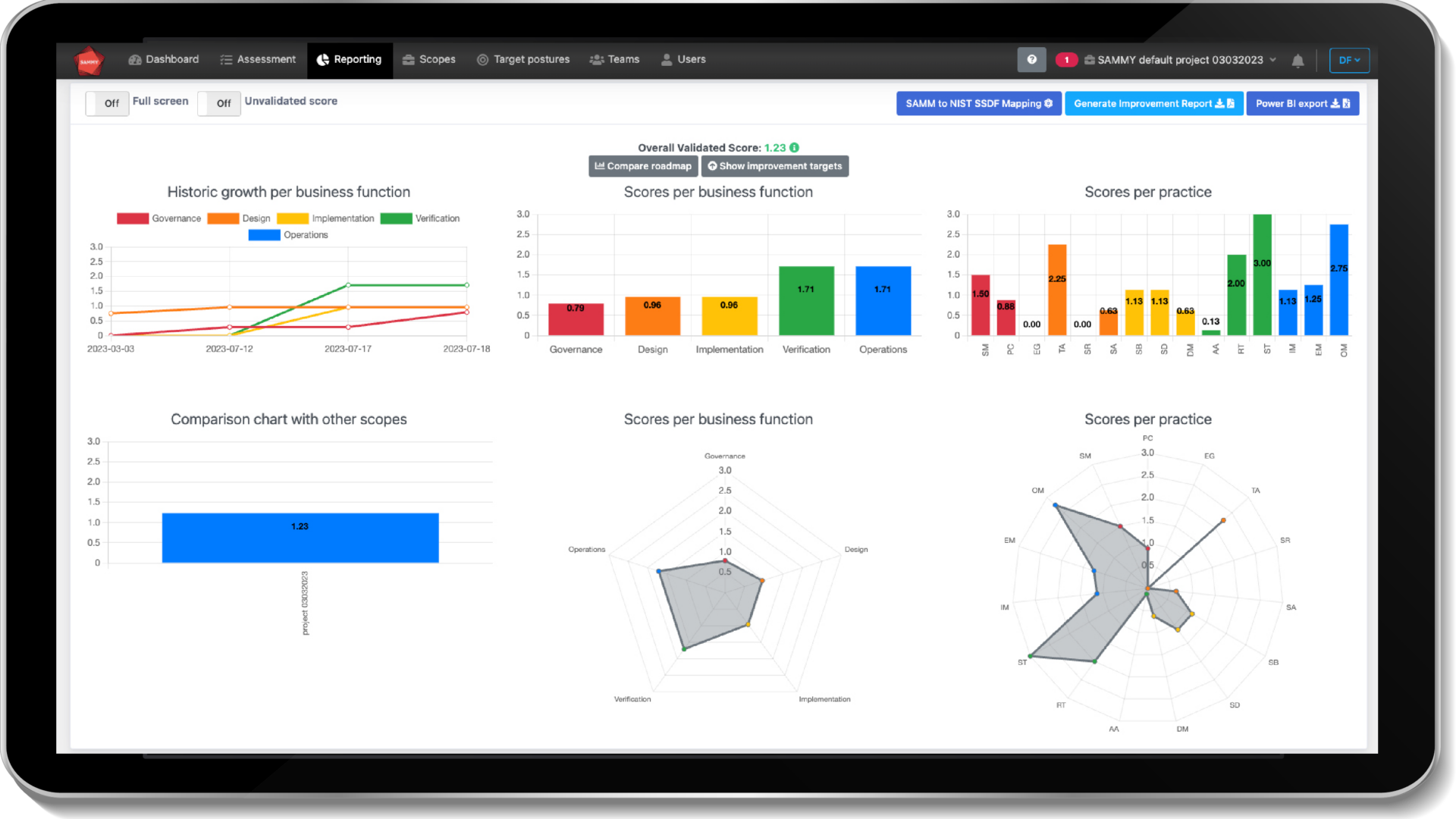
Here you can also visualize the improvement roadmap and show the improvement targets.
Exporting reports
When you have your security posture mapped on SAMMY you use it to automatically generate different reports. Some of the reports that are currently available are:
Improvement reports
This report is generated as a PDF and includes a summary of the assessment, and a detailed overview of the improvement roadmap including details around timelines and ownership of the different improvements. It is an ideal for internal reporting.SAMM to NIST SSDF mapping
This report maps your OWASP SAMM scores to NIST SSDF activities and links the relevant evidence. This functionality can be used to evaluate and demonstrate NIST SSDF compliance. Click here to find out more about NIST SSDF.

Creating different scopes
At larger organizations you will have different scopes for SAMM. Here is some guidance on scope by the SAMM project team. However you define the scopes you can easily implement, compare and manage different scopes in SAMMY.
Setting target postures
It should never be your ambition to have a maturity of 3 on all business functions. In fact this would likely be wasteful. What your ambitions should be depends on many factors of your business, its context and the risk profile of your products. The best way to manage such goals is to set target postures that are tailored to your context. In SAMMY you can easily create such target postures. These target postures may be derived from the company’s security policies and may help to further mature these policies. The target posture is then shown along the process to the different teams in the different scopes. The goal then becomes the elimination of the gap between the current posture and target posture.

User, role and team management
SAMMY is a collaborative tool. Tasks and responsibilities can be assigned on a team and an individual level. There is always clear ownership of any task. And individuals always have a clear overview of what they are expected to do.
Jira integration
As different tasks are assigned to different team members SAMMY is integrated with JIRA in order to automatically feed into your existing task management flow. Soon a similar integration will exist for Microsoft Teams.
If you don’t use JIRA or Teams and would like us to integrate with another tool, or if you have any other suggestions please reach out to us. The roadmap of this tool is community driven.