Updated: 18 January, 2024
4 May, 2023
If you are building software the best way to manage your security posture is with the SAMMY tool. It builds on SAMM ( Software Assurance Maturity Model) which is the most complete and prescriptive security posture management model. SAMM is created and maintained by the OWASP Foundation (Open Web Application Security Project) the world’s leading authority in software security. SAMMY is created by Codific, it turns the maturity model into a management tool allowing users to assess, audit, assign roles and create roadmaps of improvements.
 SAMMY is free, and you can start using it right now! Go to the SAMMY tool.
SAMMY is free, and you can start using it right now! Go to the SAMMY tool.
If you want to learn more about OWASP SAMM you can take the free SAMM training.
Key takeaways
- SAMMY is used to manage your Appsec programme.
- Perform assessments with internal or external validations
- Assign responsibilities and timelines
- Get started with SAMMY
Why use OWASP SAMM to manage your security posture?
If you are responsible for application security at your organization you have a highly complex task. You need to cover all the bases all the time, the bad guys only need to win once. To be consistent in all the aspects of security your weapon of choice is structure. You need a structured map with all the bases that you need to cover. You need an easy way to see where you are at, and where you are going. OWASP SAMM provides the map and itinerary of your security journey.
OWASP SAMM is prescriptive rather than descriptive. Other frameworks only benchmark against industry practices. The threat landscape is moving fast and you need to be best of class, not play catchup with your peers. OWASP SAMM is designed to lead the way.
It is also an open source framework with a strong community updating it continuously.
OWASP SAMM is a maturity model with 3 levels of maturity levels in 15 security practices and 90 activities. This is much more nuanced than a boolean checklist.
And with all these detailed prescriptive practices it is by far the most comprehensive map of your battlefield. OWASP SAMM is the most complete Software Assurance Maturity Model. It can easily be mapped to your compliance frameworks (ISO, NIST GDPR, HIPAA, etc…).
There are many compliance driven approaches where security is, hoped to be, the byproduct of compliance. OWASP SAMM does the opposite, it is a security driven approach where easy compliance is the byproduct of good security.
There is a shift from compliance driven security management to risk driven security management. For risk driven security management OWASP SAMM is your model and SAMMY is your tool.
What exactly does SAMMY do?
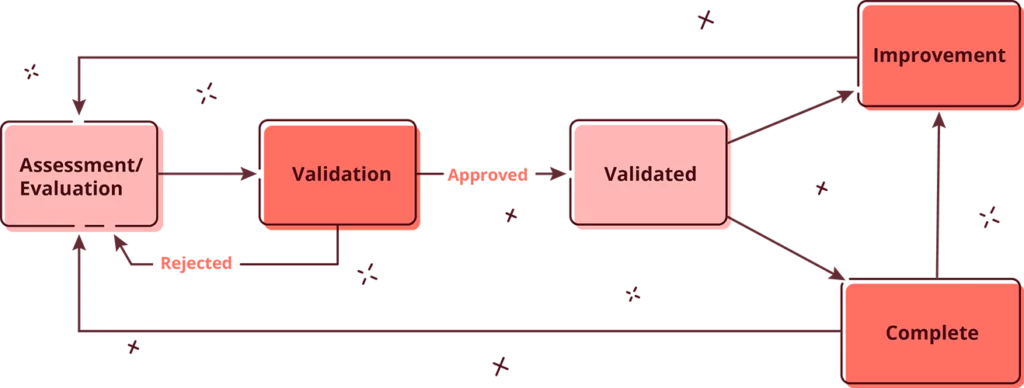
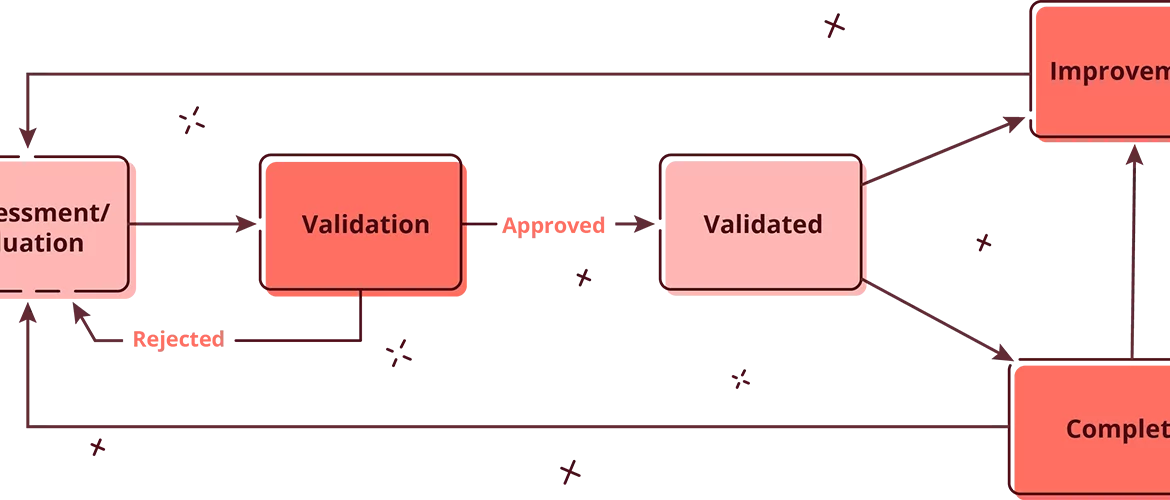
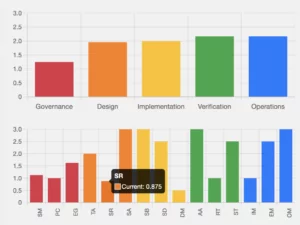
Assessment: SAMMY is used as a tool to assess the 90 activities covered in the OWASP SAMM framework. Maturity is expressed with an overall score, a score for each of the 5 business functions and a score for each of the 15 security practices. Scores range from 0 to 3.
Validation: The second step in the process is the validation of the scores by a second person, internal in the case of internal controls or external in case of an external auditor. The validator will review the evidence provided by the assessor and compare it with the established threshold for each maturity level. If the assessment is rejected the validator provides information as to why, and how the assessment should be completed. If the assessment is approved then the maturity score on the practice is validated. It now contributes to the overall scores and the practice is considered in the prioritization of future improvements. More about prioritization further down.
Role assignment
Per activity roles can be assigned to different people. For assessment this is typically the person who is responsible for the activity, or the person that is in the best position to evaluate it. The validator can be one overall expert, internal or external, or different experts per business function or security practice. Improvement cycles are assigned per security practice.
Quantitative Prioritization
There are in total 90 activities covered in OWASP SAMM 2.0, together they cover everything you need to keep an eye on. But aspiring to the maximum level of maturity in all activities is neither realistic nor wise because it would be forbiddingly expensive. To address this issue SAMMY provides multiple prioritization parameters that include, industry specific relevance, assessors and validators priority weighting and relative gaps between security activities. With these metrics an ordered list of TODOs for improvement is created.
Improvement cycles and roadmaps
Improvement cycles can be assigned in a push (top down) or pull ( bottom up) way. Either way a security activity is picked from the list of priorities and a new target maturity level and a deadline is defined. With this done for multiple security activities at any given time the security posture and the security posture roadmap can easily be defined.
Who uses SAMMY to manage their security posture?
SAMMY can be used by organizations large and small. Anyone who builds software, either to sell or to run their own business, and by now who doesn’t? Codific is a small startup of around 20 employees, and the tool was first developed internally for our own use. With the rise of OWASP SAMM more and more organizations are adopting the tool. Amongst them for example Zebra Technologies that have around 10.000 employees spread across 128 countries. Zebra Technologies security posture is managed with SAMMY.
As the tool is free to use, and can be used anonymously we are not really sure who all the organizations are that are using the tool. We do see growing traffic every day, and we are sure, more users will step into the limelight soon.
How to manage the secure architecture component of your security posture?
If you want a secure house, be it against burglars or earthquakes or anything else you could think of, you probably want to think of this before you start building. Make architectural choices that mitigate risks in the fundamental design. This “thinking early” is referred to as “shifting left” in the software industry. Codific, in large part because of our founder’s academic research on the topic, is a specialist in security by design and privacy by design architecture (in software, not in houses 🙂 ) . Our founder Dr. Aram Hovsepyan wrote a concise guide on the topic of security architecture.
How to manage the threat modeling component of your security posture?
Burglars, earthquakes, what else could go wrong with your new house. Did you think of everything that could go wrong? How do you minimize the chance of overlooking a threat? Welcome to the world of threat modeling. The challenge is to anticipate potential “unknown unknowns”, the threats you weren’t aware of you should worry about. Here again structure is your friend. There are structured approaches to maximize the coverage of your threat consideration. For security the leading threat model is Microsoft’s STRIDE. For privacy threat modeling it is LINDDUN, of which our founder Dr. Aram Hovespyan is a co-author. The research team at the KU Leuven was led by Dr. Kim Wuyts who we recently interviewed on our podcast. We also have a concise guide on how to implement threat modeling in your projects.
How to manage the secure build component of your security posture?
A secure design does not guarantee a secure build. A secure software development pipeline includes many controls such as static and dynamic analysis tools to minimize the chance of deploying vulnerabilities. Modern applications run on the cloud and continuously update. Continuous updates are a two sided sword, they are essential in defending against the latest published threats, but at the same time they can introduce new supply chain vulnerabilities. The complexity of open source components and all the possible vulnerabilities is far too wide for any security analyst to be able to review manually. That is why this is a tool and automation heavy security practice. But experts are still needed to pilot all these tools and notifications. We have a practical guide to the secure build process.
We also use and recommend OWASP ZAP integrated into the Gitlab CI/CD pipeline. Here is a practical guide on how to integrate OWASP ZAP into Gitlab.
How to manage the education and guidance component of your security posture?
You are the weakest link! Just kidding, of course not you, the other guy! In the majority of recent ransomware attacks there was a human mistake, often as simple as clicking on a phishing link. You can build as many walls as you like, if an employee badges the threat actor in, the walls are useless. We have an article with tips on how to get started with your education and guidance programme, including links to a bunch of free resources.
How to manage the requirements driven testing component of your security posture?
One of the five business functions is verification. This is generally what outsiders think of when they think of security professionals. It consists of three broad security practices, architectural assessment, security testing and requirement driven testing. Here we have a guide to security driven testing.
How many security posture components are there?
In total there are 90 activities grouped into 15 security practices which cover 5 business functions. The business functions are Governance, Design, Implementation, Verification and Operations. You can find the PDF of OWASP SAMM 2.0 here.
What is Codific`s role in OWASP SAMM?
The founder of Codific, Dr. Aram Hovsepyan, is also an active core member of the OWASP team behind the model, together with other experts they are responsible for the model, it’s updated and all the related guidance and documentation.
From an organizational perspective Codific is also a lead sponsor of the OWASP SAMM project. This means we provide resources: money and qualified manpower to help the project and its goals. We do this because it is our mission to build a simple and safe digital future, and our belief that this will be achieved with open source and open innovation.
Can I get started with SAMM & SAMMY right now?
Yep, it’s a free tool. Click here to get started with SAMMY.
If you want to study SAMM first you can find the PDF of version 2.0 here.