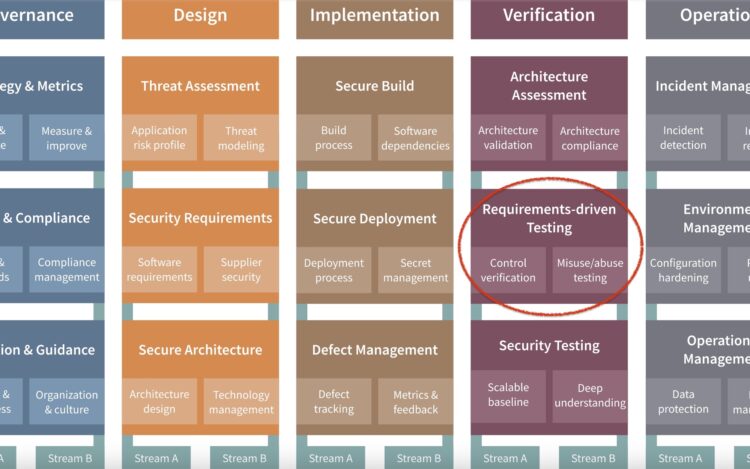
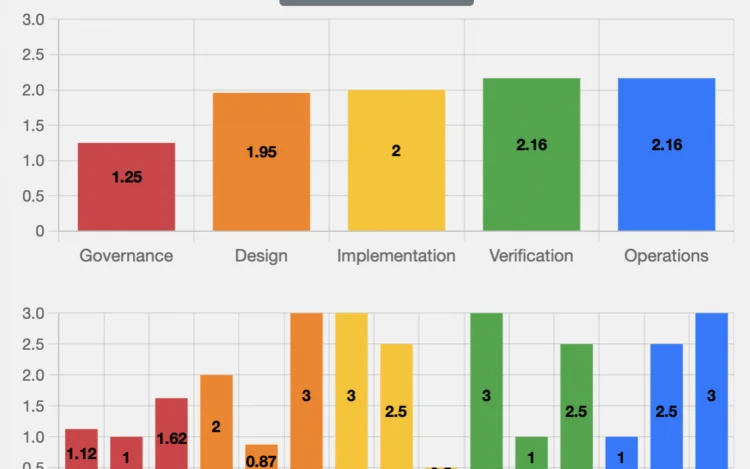
Security verification is about validating that a system or application adheres to predefined security requirements […]
Ever heard the saying “our team is our greatest asset”. I’d dare to say that[…]
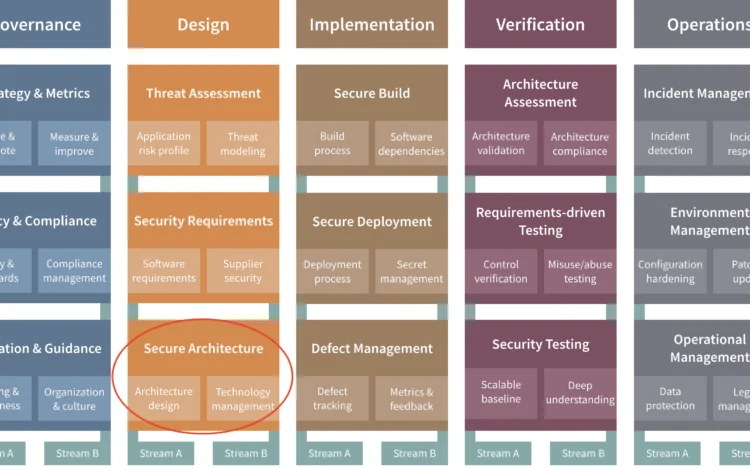
Secure architecture in a nutshell The secure architecture practice focuses on security during the architectural[…]
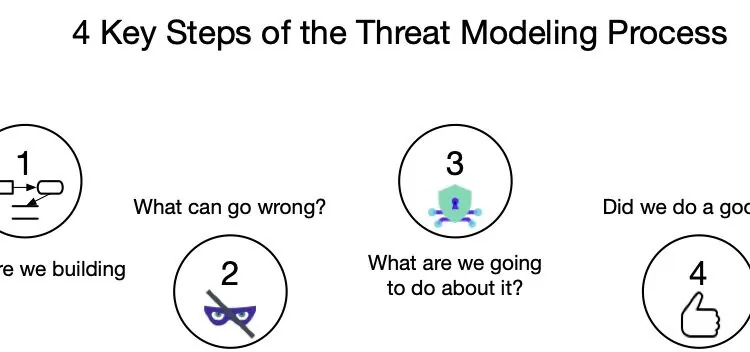
Threat modeling yields the highest return on investment when it comes to your Application Security[…]
The secure deployment of your software is a central piece in your secure software development[…]