Introduction to security in the context of outsourced development Many organizations rely on outsourced software […]
Introduction to software security requirements Despite clearly understanding the importance of security requirements, organizations seem[…]
The OWASP Software Assurance Maturity Model (SAMM) is rapidly becoming the go-to framework for application[…]
Cybersecurity in general and application security (AppSec) in particular are extremely challenging topics. They run[…]
It this article we explore the essentials of the EU Cyber Resilience Act (CRA), and[…]
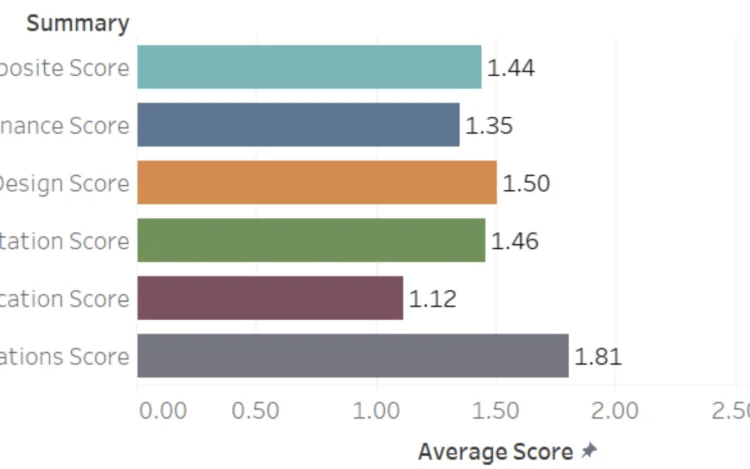
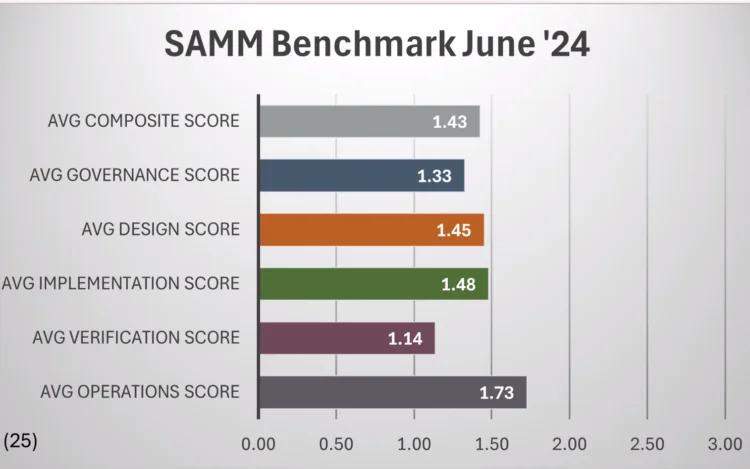
How to use OWASP SAMM for effective communication on security? Reporting with OWASP SAMM is[…]
Application security is a paramount concern for organizations that develop software. However systematically managing AppSec[…]
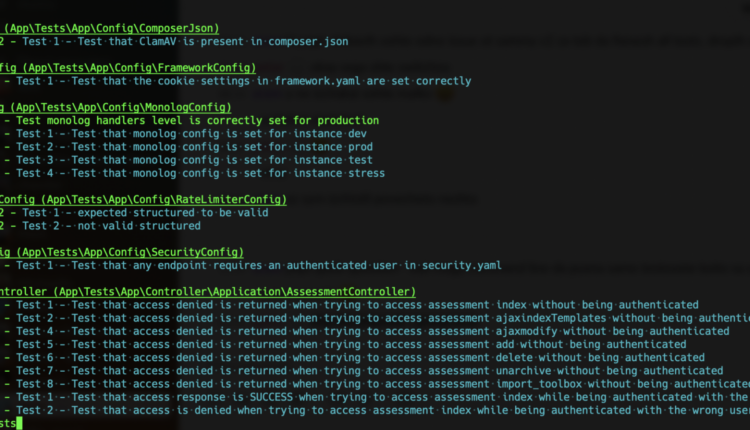
Application security requires a systematic approach and requires dealing with software security throughout every stage[…]
At Codific we are very proud to be the main sponsor of Chess International Master[…]
For the past 20 years web applications have always been the number one action vector[…]