SAMMY is our application security management tool. It started as an internal tool to keep track of our security posture and activities using OWASP SAMM. We soon notices that many other organization were looking for a tool to manage their security posture with OWASP SAMM, so we made the tool freely available on our website.
The workflow in the app is so smooth and efficient that our users asked to add support for more models. We have added support for Disaster Recovery Plan Management based on the guidance of NIST and support for ISO27001. We also have feature to export OWASP SAMM assessments to NIST SSDF readiness reports. In the coming months and years we intend to add many more models and frameworks to make your application security management measurable, actionable and smooth.
How does SAMMY implement OWASP SAMM?
Assessment
SAMMY is used as a tool to assess the 90 activities covered in the OWASP SAMM framework. Maturity is expressed with an overall score, a score for each of the 5 business functions and a score for each of the 15 security practices. Scores range from 0 to 3.

Validation
The second step in the process is the validation of the scores by a second person, internal in the case of internal controls or external in case of an external auditor. The validator will review the evidence provided by the assessor and compare it with the established threshold for each maturity level. If the assessment is rejected the validator provides information as to why, and how the assessment should be completed. If the assessment is approved then the maturity score on the practice is validated. It now contributes to the overall scores and the practice is considered in the prioritization of future improvements. More about prioritization further down.
Role assignment
Per activity roles can be assigned to different people. For assessment this is typically the person who is responsible for the activity, or the person that is in the best position to evaluate it. The validator can be one overall expert, internal or external, or different experts per business function or security practice. Improvement cycles are assigned per security practice.

Quantitative Prioritization
There are in total 90 activities covered in OWASP SAMM 2.0, together they cover everything you need to keep an eye on. But aspiring to the maximum level of maturity in all activities is neither realistic nor wise because it would be forbiddingly expensive. To address this issue SAMMY provides multiple prioritization parameters that include, industry specific relevance, assessors and validators priority weighting and relative gaps between security activities. With these metrics an ordered list of TODOs for improvement is created.

Improvement cycles and roadmaps
Improvement cycles can be assigned in a push (top down) or pull ( bottom up) way. Either way a security activity is picked from the list of priorities and a new target maturity level and a deadline is defined. With this done for multiple security activities at any given time the security posture and the security posture roadmap can easily be defined.
How does SAMMY implement NIST Disaster Recovery Plan guidance?
We use the same workflow with assessment, validation and improvement activities and roles. So the workflow is the same, buth the underlying model is different. The content of the disaster recovery plan guidance covers:
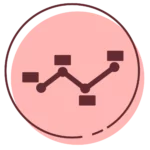
- Supporting Information: Covers the proper definition of purpose, scope and assumptions.
- Concept of operation: Covers the system description, roles and responsibilities and the existence of the three phases (activation, recovery and validation) which are looked at further in the next parts.
- Activation: Covers the procedures around activation, notification and outage assessment.
- Recovery: Covers activities, procedures and escalation.
- Validation: Covers data, functionality and security testing as well as event documentation and recovery declaration.
- Appendices: Covers 13 other components ranging from diagrams to contact lists.DF of version 2.0 here.
How does the scoring system work when managing Disaster Recovery Plans?
OWASP SAMM is a maturity model with maturities ranging from 0 to 3. NIST DRP guidance is not. To solve this SAMMY uses a weighted scoring system based on the relative priority, risk profile and appetite factors of the organization or the product. This scoring system allows you to easily benchmark and set a “good enough” threshold for all business units and teams.
Who uses SAMMY to manage their security posture?
SAMMY can be used by organizations large and small. Anyone who builds software, either to sell or to run their own business, and by now who doesn’t? Codific is a small startup of around 20 employees, and the tool was first developed internally for our own use. With the rise of OWASP SAMM more and more organizations are adopting the tool. Amongst them for example Zebra Technologies that have around 10.000 employees spread across 128 countries. Zebra Technologies security posture is managed with SAMMY.
As the tool is free to use, and can be used anonymously we are not really sure who all the organizations are that are using the tool. We do see growing traffic every day, and we are sure, more users will step into the limelight soon.
If you want to learn more about OWASP SAMM you can take the free SAMM training.
Can I get started with SAMM & SAMMY right now?
Yep, it’s a free tool.
If you want to study SAMM first you can find the PDF of version 2.0 here.
Do you need a tailored solution for your business?
Want to discuss how SAMMY can benefit your organization or need a customized solution? Get in touch with us.
Free
For small
organizations
(limits apply)
Free
features:
3 Scopes
1 Target Scope(s)
Reporting (Limited Use)
OpenCRE Integration
Full Data Privacy
Integrations (Partial)
Multiple Assessment Models
Multitenant deployment
Premium
For growing
organizations
(limits apply)
Everything from
Free plus:
10 Scopes
10 Target Scopes
Unlimited Standard Reports
OpenCRE Integration
Full Data Privacy
All Assessment Models
Controls Management
Mapping Reports
Pro
For medium-sized
organizations
per user /month
Everything from
Premium plus:
Unlimited Scopes
Unlimited Target Scopes
Unlimited Customized Reports
Custom Integrations
SLA
Priority Support
Enterprise
For enterprise
organizations
per user /month
Everything from
Pro plus:
Custom Integrations
Custom Features
Dedicated / On-Prem Deployment
* Pricing depends on nr. of users, nr. of scopes and the assessment models.