Updated: 16 March, 2024
18 September, 2022

September 14, 2022, the Executive Office of the US President has released the memorandum M-22-18. M-22-18 mandates all software suppliers to the US Federal Government to comply with the NIST Secure Software Development Framework (SSDF). In plain English – if you supply the Feds with any software you will have to implement a security assurance programme conform to NIST SSDF. Moreover, you have 362 days to comply (as of the date of this blog’s publication). If you aren’t developing any software systems for the US Government you should still stick around. US is setting the bar so high that most software firms worldwide are not even remotely close to being there.
What is M-22-18?
M-22-18 is a memorandum that gives teeth to the NIST Secure Software Development Framework and makes a security assurance programme a must-have. The SSDF used to be a recommendation, but it is now becoming mandatory for all software providers to the US Government. M-22-18 is not yet another GDPR where you can lawyer your way out of it. It is not an ISO27001 that you can get by having a bunch of documents. The memorandum is about software security as we – the security experts – envision it in our small “hobbyist” groups. It’s about threat modeling going mainstream; it’s about explicit security requirements analysis and validation; it’s about having security champions in your dev teams with role-specific trainings. M-22-18 is about having a systematic approach to software security practiced throughout the entire software development lifecycle.
What is NIST Secure Software Development Framework (SSDF)?
NIST SSDF is a security assurance programme to be integrated within your software development lifecycle (SDLC). SSDF consists of 19 security practices divided across 42 tasks. To put it bluntly – you have to cover 42 topics in software security to get the attestation required by the Feds. And trust me, it is not a security questionnaire you can go through in an afternoon. We are talking about the introduction of actual security best practices. Examples include mandatory and role-specific security trainings for your team, identifying and documenting all security requirements, running threat modeling and risk assessment exercises. Honestly, the chances to get ready in 362 days for a software company with no idea what e.g., threat modeling is are slim.
I am a fan of the NIST SSDF, however the framework is relatively challenging to start with unless you have an advanced security assurance prog
ramme in place. To some extent that is by design. Security assurance frameworks are relatively abstract to remain applicable for any software organization independent from its size and industry. Luckily, NIST SSDF comes with a handy list of references for each security practice and task. Amongst these references is the OWASP Security Assurance Maturity Model (SAMM). The great news is that NIST SSDF has a complete mapping to OWASP SAMM. Inversely, SAMM has a complete mapping to SSDF. Hence, you can simply implement SAMM and automatically check your SSDF compliance.
What is OWASP Software Assurance Maturity Model (SAMM)?
OWASP SAMM is an alternative security assurance programme and an OWASP flagship project. OWASP SAMM was created in 2009 by Pravir Chandra sponsored and donated to OWASP by Fortify. Like many other tech inventions / methodologies SAMM was way ahead of its time. A group of security experts led by Bart De Win, Sebastien Deleersnijder and Brian Glas gave it a second breath by creating versions 1.5 and 2.0. 14 years after its inception SAMM is ready for the spotlight. SAMM Core Team grew overtime to a dozen of world class security practitioners and experts.
Codific’s mission statement is that we believe in a simple and safe digital future. I strongly believe that SAMM is an inseparable part of that secure future.
The key advantages of SAMM compared to any other security assurance programme are based on the following observations:
- Organization behaviour changes slowly over time and changes need to be small and iterative to really take hold and make a difference. SAMM is a maturity model that provides a roadmap for step-by-step improvements in the organizations’ security postures.
- No single recipe works for all organizations. SAMM offers tailore-made assurance programme for organization of any size, risk profile, culture and IT maturity.
- SAMM offers prescriptive guidance with clear details on how to implement security activities.
- SAMM is a simple, well-defined and measurable programme.
Codific has made its mission to contribute to the project by becoming a Leader sponsor. We have also created the SAMMY tool that is free to use and allows any organization to manage the adoption of SAMM programme. Hence, powered by SAMMY, SAMM is your easiest and fastest path to NIST SSDF compliance.
NIST SSDF – OWASP SAMM mapping
NIST SSDF originally defines a mapping to OWASP SAMM albeit in version 1.5. Unfortunately the mapping is imprecise and incomplete even for version 1.5. This is why the SAMM core team will be releasing an updated version of the mapping. As part of the core team I managed to get a sneak peak in the mapping. All SSDF tasks have a full mapping to SAMM activities. The reverse is also almost true, with a minor exception though. Hence by adopting SAMM your organization should be ready for SSDF compliance.
As of 15/01/2023 the SAMM core team has released a final submission mapping between SSDF and SAMM. NIST is still in the process of reviewing this submission. However the SAMM Core Team has been collaborating closely with NIST so I expect relatively minor changes.
What is SAMMY?

SAMMY Is a Software Assurance Maturity Model management tool. It enables companies formulate and implement a security assurance program tuned to the risks they are facing. SAMMY allows you to set up roles and responsibilities when designing your assurance programme. It also allows everyone in your firm to follow up on the current priorities, improvements in progress and security posture metrics.
We are currently improving SAMMY to actually support SSDF. Codific will add 2 NIST SSDF specific features to SAMMY:
- A feature to run SAMM assessments and convert those validated assessments into SSDF. You will be able to check your compliance with SSDF based on your SAMM assessments.
- A feature to run SSDF assessments, validate them and plan for improvements. You will be able to demonstrate compliance with SSDF directly.
How can SAMMY help with your NIST SSDF compliance?
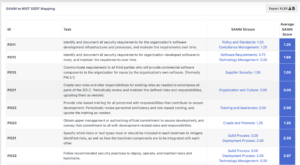
As of 16 February 2023 Codific has added a NIST SSDF coverage generation feature to the SAMMY tool. For each SSDF task SAMMY will provide you with an overview of all SAMM streams along with their corresponding SAMM scores. We also provide an indication of what your average score for NIST SSDF would be based on SAMM. Note SSDF is not a maturity model, nor does it provide any scoring or coverage recommendations. Nonetheless you could use this score to demonstrate improvements in terms of SSDF.
Finally, SAMMY can export your security posture in terms of SSDF to Excel.
Conclusion
The Executive Office of the US President has released the memorandum with a funky name – M-22-18. It essentially mandates all suppliers to US Federal agencies to commit to a security assurance programme. M-22-18 requires compliance to the NIST Secure Software Development Framework. However SSDF itself is too abstract and comes with a set of references for concrete implementations. OWASP SAMM is amongst these references and it has a complete mapping to NIST SSDF tasks. SAMM is a simple, well-defined and measurable secure SDLC methodology. SAMMY is the most mature OWASP SAMM supporting tool that will help you in your security journey.
Codific has a relatively short release cycle for updates and new features in SAMMY. Two noteworthy upcoming updates to SAMMY are worth mentioning. Firstly, you will be able to use SAMM as an AppSec programme and demonstrate your compliance with SSDF. Secondly, SAMMY will let you run assessments in native SSDF terminology.
Secure your software development lifecycle with OWASP SAMM. Introduce the SAMMY tooling to help your business units and your organization manage SAMM. SAMMY is free and includes additional community-driven guidance on best practices for each security activity.
What do we build with SAMM and SAMMY?
Codific is a team of security software engineers that leverage privacy by design principles to build secure cloud solutions. We build applications in different verticals such as HR-tech, Ed-Tech and Med-Tech. Secure collaboration and secure sharing are at the core of our solutions.
Videolab is used by top universities, academies and hospitals to put the care in healthcare. Communication skills, empathy and other soft skills are trained by sharing patient interviews recordings for feedback.
SARA is used by top HR-Consultants to deliver team assessments, psychometric tests, 360 degree feedback, cultural analysis and other analytical HR tools.
We believe in collaboration and open innovation, we would love to hear about your projects an see how we can contribute in developing secure software and privacy by design architecture. Contact us.