Updated: 27 January, 2025
23 March, 2023
In the dynamic digital realm, security is not a luxury; it’s an imperative. As software development evolves and applications grow more intricate, the risk of vulnerabilities and cyberattacks escalates. The Secure Software Development Lifecycle (SSDLC) emerges as a systematic approach to embed security into every stage of software development, safeguarding applications and protecting valuable data. This blog aims to shed light on the Secure Software Development Lifecycle (SSDLC), its importance, and how it can be implemented using the Open Web Application Security Project (OWASP) Software Assurance Maturity Model (SAMM) application security (AppSec) programme. It will also discuss how SAMMY can be utilized to manage the entire process, ensuring a secure and reliable software development lifecycle.
Key Takeaways
- Integration of security into software development through SSDLC is crucial in the digital era, dramatically reducing vulnerabilities.
- OWASP SAMM‘s structured framework significantly enhances SSDLC security, revolutionizing organizational processes.
- Embedding SAMM in SSDLC phases ensures continuous, integral security in software development.
- SAMM’s Governance function brings substantial value to SSDLC, focusing on policy, education, and strategy.
- Codific’s SAMMY excels in managing and implementing robust security practices within SSDLC, utilizing SAMM’s strengths.
- Adopting SSDLC and SAMM is essential for organizations to combat the escalating financial and reputational risks of cyber threats.
What is our expertise and experience with the SSDLC?
Before we dive into the SSDLC, let us showcase our expertise in this area to build your trust in our knowledge. At Codific, we have over a decade of experience incorporating security into every stage of the software development lifecycle (SDLC), employing AppSec programmes like SAMM. Our flagship product, Videolab, exemplifies our dedication to security. It’s a secure video-sharing platform designed to handle sensitive patient recordings for medical education purposes in Belgium and the Netherlands. Our commitment to AppSec goes beyond our own products; we’ve even developed SAMMY, a management tool specifically designed for SAMM, empowering organizations to effectively manage their security posture. This blog post is partly based on insights from Nikolay Dyakov, our most experienced secure software engineer and an expert in the SSDLC.
Why is it important to integrate security into the SDLC?
In today’s digital landscape, cybersecurity is a critical necessity. With the increasing complexity of software development, the risks of vulnerabilities and cyberattacks are escalating. The SSDLC is vital for embedding security throughout the software development process, thereby protecting applications and data.
The Consortium for Information and Software Quality (CISQ) reports that in 2022, the U.S. incurred $2.4 trillion in costs due to poor software quality, primarily due to:
- Cybercrime Losses: Losses from cyberattacks rose by 64% between 2020 and 2021, with global costs reaching an estimated $7 trillion in 2022.
- Technical Debt: Addressing post-deployment vulnerabilities leads to costly rework. Integrating security early in development reduces this technical debt.
- Software Supply Chain Vulnerabilities: Modern software often includes open-source components, which can be vulnerable. Between 2020 and 2021, vulnerabilities in these components increased by 650%. SSDLC helps manage these risks.
These statistics, coupled with growing legal consequences for security breaches, make SSDLC essential for contemporary organizations. Implementing SSDLC safeguards applications, protects data, and reduces financial and reputational risks from cyberattacks and technical debt.
Given the importance of security in the software development lifecycle (SDLC), frameworks like the OWASP Software Assurance Maturity Model (SAMM) are crucial. SAMM provides a structured approach to embedding security throughout the SDLC and organizational application security processes, enhancing overall security posture.
Understanding the OWASP SAMM Model in the Context of SSDLC
The Open Web Application Security Project (OWASP) Software Assurance Maturity Model (SAMM) is a crucial framework designed to guide organizations in integrating effective security practices into their software development processes. Distinctly structured into five business functions – Governance, Design, Implementation, Verification, and Operations – OWASP SAMM offers a comprehensive approach to application security (AppSec).
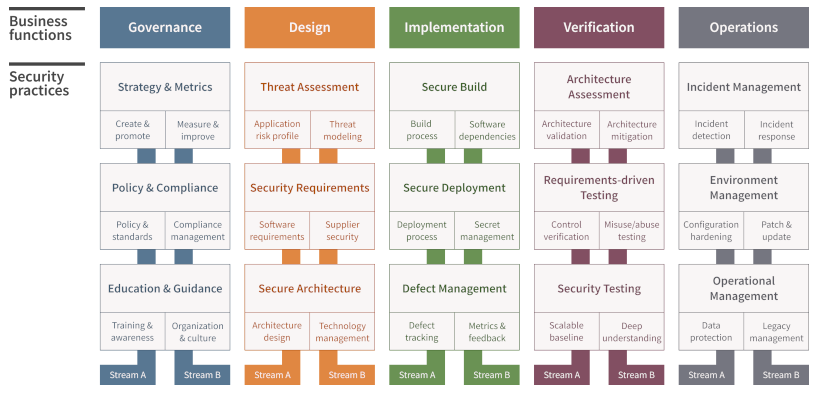
Each business function in SAMM is further divided into three security practices, encapsulating a total of 15 security practices. This structure facilitates a holistic approach to AppSec, encompassing various aspects of software development and operational security.
OWASP SAMM vs. SSDLC: A Comparative Perspective
While the Secure Software Development Lifecycle (SSDLC) is a methodology that embeds security into every phase of software development, the OWASP SAMM model serves as a guiding framework for implementing and managing an effective AppSec programme. The key difference lies in their scope and application: SSDLC focuses on the process of software development itself, ensuring security considerations are integrated at each stage, from planning to deployment and maintenance. In contrast, OWASP SAMM provides a broader, more strategic viewpoint, offering guidance on how to structure and enhance an organization’s overall AppSec programme.
Incorporating the OWASP SAMM model within the SSDLC framework allows organizations to not only secure their software development processes but also establish a robust, ongoing AppSec programme. This integration ensures that security is not just a phase in development but a continuous, evolving practice, aligning with the organization’s security goals and compliance requirements.
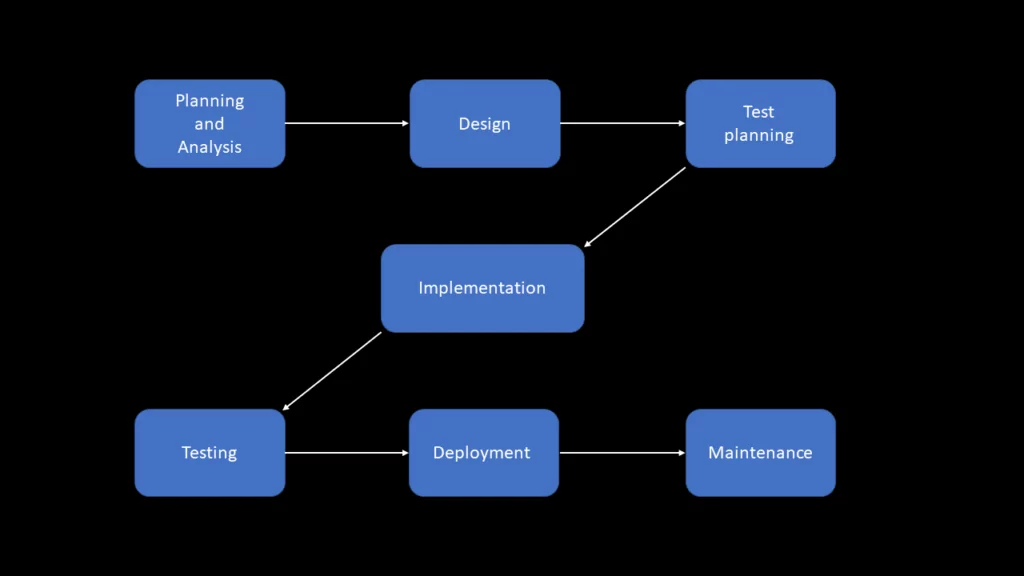
What are the 7 phases of the SSDLC and how can SAMM be used to manage it?
Seven distinct phases compose the SSDLC, each crucial for ensuring the security and integrity of the final product. These phases are Planning and Analysis, Design, Test Planning, Implementation, Testing, Deployment, and Maintenance. Let’s explore how the OWASP SAMM model can be effectively leveraged in each of these phases.
1 Planning and Analysis
This initial phase involves defining the project’s scope, requirements, and identifying potential risks. The Design function of SAMM, particularly the Threat Assessment and Security Requirements practices, is essential here. Threat Assessment helps to map out the application risk profile and model threats which helps with defining software security requirements in the Security Requirement practice. In addition, the Security Requirements practice also helps to define and introduce security requirements and defect-remediation services level agreements (SLAs) for suppliers. This tandem approach lays a secure foundation for the project.
2 Design
This phase outlines the software’s architecture and design. The Secure Architecture practice of SAMM’s Design function ensures that security is embedded in the architecture. This is done by leveraging security by design principles and approving or disapproving the use of certain technologies in the project, according to their security quality. Additionally, the Architecture Assessment practice of the Verification function evaluates the security aspects of the design, enhancing its robustness against potential threats. This helps to ensure that the application and its infrastructure architecture meet all the relevant security and compliance requirements, while sufficiently mitigating identified security threats.
3 Test Planning
This phase involves developing strategies for testing the software, including security testing. The Requirements-driven Testing and Security Testing practices within SAMM’s Verification function provide a framework for planning comprehensive security tests that align with the defined security requirements. The former of these two practices helps to ensure that the implemented security controls are working properly and satisfy the security requirements. The latter focuses on uncovering vulnerabilities in the application, irrespective of requirements and in this phase would involve planning SAST, DAST and IAST processes, as well as manual tests.
4 Implementation
This phase involves coding the software. The Secure Build practice within SAMM’s Implementation function focuses on ensuring a secure development of the code, adhering to best practices and security standards. This involves striving for automation in the software build processes to remove subjectivity and managing software dependencies to contain the impact of their insecurity.
5 Testing
The software undergoes rigorous testing for defects, including security vulnerabilities, following the tests planned in the Test Planning phase. SAMM’s Security Testing practice in the Verification function ensures thorough evaluation for security issues, while the Defect Management practice within the Implementation function helps in tracking and managing defects while developing feedback streams to other practices that are enabled by defect analysis.
6 Deployment
Involves the release of the software into a production environment. The Secure Deployment practice within the Implementation function of SAMM is critical, ensuring that the deployment process is secure and maintains the software’s integrity and security. This practice involves automating the deployment process to remove manual error, integrating security verification checks to mark a successful deployment and protecting the privacy and integrity of sensitive data during the deployment process.
7 Maintenance
Involves ongoing support and updates of the software. During this phase, the Operations function of SAMM becomes particularly relevant. Practices such as Incident Management, and Environment management play key roles in maintaining the security of the software, ensuring it remains secure against new and evolving threats. Incident Management helps with the detection and response to security incidents which most often leads to security updates based on detected vulnerabilities. Moreover, Environment Management helps to monitor vulnerability reports and perform timely patches, while encouraging a pro-active hardening of all technology components and infrastructure based on changes in the environment. This helps to keep your software’s security ahead of the curve, reducing its security risks through maintenance.
By integrating these specific SAMM model practices into each SSDLC phase, organizations can establish a comprehensive, structured, and effective approach to security throughout the software development lifecycle. Nevertheless, using OWASP SAMM to manage your security posture has additional benefits that the SSDLC does not capture.
What parts of OWASP SAMM does the SSDLC not consider?
As mentioned, SAMM is an AppSec programme, meaning that it is a more holistic model than the secure software development lifecycle framework as it also considers governance, education and strategy. While the SSDLC primarily focuses on the technical aspects of software development, OWASP SAMM broadens the scope to include organizational and strategic elements, especially within its Governance business function. This function encompasses practices that, while not traditionally part of the SSDLC, significantly contribute to an organization’s overall security posture.

Policy & Compliance
This practice involves the development and enforcement of security policies and ensuring compliance with legal and regulatory requirements. Unlike SSDLC, which is more process-oriented, this practice helps create a structured and standardized approach to security across the organization, enhancing the overall security culture and ensuring legal and regulatory adherence.
Education & Guidance
This practice focuses on training and educating the workforce about security best practices and risks. This practice goes beyond the SSDLC’s scope by building a security-aware culture among employees, which is crucial for preventing security breaches that could arise from human error or lack of knowledge. Codific’s CEO, Aram Hovsepyan, who is an expert in AppSec, has even mentioned in the OWASP SAMM Fundamentals Course that the Training and Awareness stream of this security practice is possibly the single most important stream of any security practice, across all business functions of the SAMM model.
Strategy & Metrics
Involves developing a security strategy aligned with business objectives and establishing metrics to measure the effectiveness of security practices. This approach offers insights into the overall effectiveness of security efforts and identifies areas for improvement, something not typically covered in the SSDLC.
These practices under the Governance function of SAMM contribute significantly to an organization’s security posture by embedding a security mindset into the organizational culture, ensuring compliance and continuous improvement. This holistic approach, encompassing governance, education, and strategy, is what sets SAMM apart from the more narrowly focused SSDLC.
Utilizing SAMMY to Effectively Manage Your SSDLC with OWASP SAMM

In our journey through integrating OWASP SAMM into the SSDLC, we’ve seen how it enriches the security process. But how do we effectively manage and implement this integration? Enter SAMMY, Codific’s innovative solution for managing your SSDLC using OWASP SAMM. SAMMY is not just a tool; it’s a gateway to a more secure software development lifecycle
SAMMY offers a dynamic and intuitive platform to assess, validate, and improve your security practices in line with the OWASP SAMM framework. It covers a comprehensive range of activities across five business functions and fifteen security practices, each scored to track progress and identify areas needing attention. With features like assessment validation, quantitative prioritization, and management of improvement cycles, SAMMY is designed to adapt to your unique security needs, supporting other models like NIST SSDF and ISO27001 as well.
What truly sets SAMMY apart is its ability to transform the often abstract elements of security frameworks into actionable and measurable tasks. Whether you’re a small startup or a large enterprise, SAMMY equips you with the tools to systematically enhance your security posture, aligning perfectly with both SAMM and your SSDLC processes. It empowers teams to not just manage, but excel in implementing robust security measures.
For organizations seeking a reliable, structured, and effective way to manage their security posture in the SSDLC, SAMMY is the right solution. Don’t believe us? Well then see what Zebra Technologies, a world-renowned American mobile computing company with 10000+ employees that is present in over 55 countries, has to say about the tool and why they use it.
Interested in using SAMMY? We have some great news for you then, you can use it for free!



