Updated: 2 September, 2025
23 March, 2023
In the dynamic digital realm, security is not a luxury, it is an imperative. As software development evolves and applications grow more intricate, the risk of vulnerabilities and cyberattacks escalates. The Secure Software Development Lifecycle (SSDLC) provides a systematic approach to embed security into every stage of development, safeguarding applications and protecting valuable data. When aligned with OWASP’s guidance, this approach is can be referred to as the OWASP SDLC, a secure SDLC guided by the community’s most trusted security practices.
This blog explores how organizations can implement a secure SDLC using guidance from the Open Web Application Security Project (OWASP). While OWASP does not prescribe a standalone SDLC, the community offers a mature and structured recommendation through the OWASP Software Assurance Maturity Model (SAMM). In many ways, OWASP SAMM represents OWASP’s vision of a secure SDLC, combining technical best practices with broader governance, strategic, and operational concerns.
We will also introduce SAMMY, Codific’s platform for managing secure software development programs in line with OWASP SAMM. Whether you’re building new systems or improving existing ones, SAMMY helps align your SDLC with OWASP’s best practices to create a robust, secure, and sustainable development lifecycle.
Key Takeaways
-
Integrating security throughout the SDLC is essential for reducing risk and building resilient software in today’s digital landscape.
-
OWASP SAMM provides the structure and guidance needed to implement an effective and measurable secure SDLC, which can be referred to as the OWASP SDLC.
-
Mapping SAMM practices to each SDLC phase helps teams apply security systematically, from planning through maintenance.
-
SAMM extends beyond development by including governance, training, and strategic measurement practices not traditionally covered in the SDLC.
-
Codific’s SAMMY platform helps organizations manage and improve their security posture using OWASP SAMM, with actionable insights and clear dashboards.
-
Adopting the OWASP SDLC with SAMM and SAMMY positions organizations to reduce vulnerabilities, meet compliance, and strengthen long-term security posture.
Why is it important to integrate security into the SDLC?
In today’s digital world, cybersecurity is not optional. As software grows more complex and interconnected, the risks from vulnerabilities, data breaches, and supply chain attacks rise sharply. The Secure Software Development Lifecycle (SSDLC) ensures that security is not an afterthought, but a core part of the development process. When this secure approach is guided by OWASP principles and practices, it becomes what some refer to as the OWASP SDLC.
The numbers tell the story. According to the Consortium for Information and Software Quality (CISQ), poor software quality cost the U.S. economy $2.4 trillion in 2022. These losses were driven by:
-
Cybercrime: Global costs from attacks reached an estimated $7 trillion, rising 64% between 2020 and 2021.
-
Technical debt: Fixing vulnerabilities after deployment is expensive and time-consuming
-
Open-source vulnerabilities: Software supply chains are increasingly under attack, with a 650% rise in component vulnerabilities between 2020 and 2021.
Nowadays, this numbers are even scarier, with cybercrime, for example, costing the world $9.5 trillion in 2024.
These challenges show why integrating security early, and continuously, is essential. The OWASP SDLC approach helps organizations reduce risks, avoid costly rework, and build resilient systems. Beyond just reducing vulnerabilities, it helps teams meet regulatory requirements, earn user trust, and prevent reputational damage.
That’s where OWASP SAMM comes in. SAMM provides a structured framework to implement a secure SDLC, offering detailed guidance for technical security, process governance, and team education. It transforms the high-level goals of the OWASP SDLC into actionable steps across your entire organization.
Understanding the OWASP SAMM Model as the OWASP SDLC
The OWASP Software Assurance Maturity Model (SAMM) is a powerful framework that helps organizations embed security throughout their software development processes. Created and maintained by the OWASP community, SAMM supports teams in building, measuring, and improving their application security posture over time.
The model is organized into five business functions: Governance, Design, Implementation, Verification, and Operations. Each function contains three security practices, resulting in a total of 15 well-defined practices that span both technical and organizational aspects of software security.
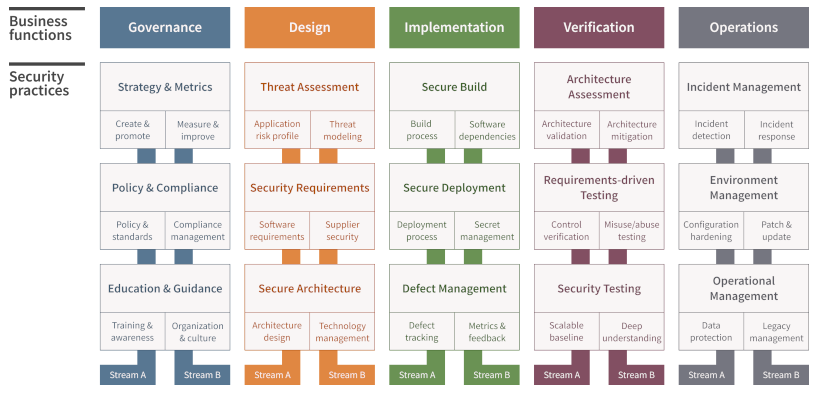
This structure makes SAMM more than just a development guideline. It provides a complete roadmap for what OWASP recommends as a secure SDLC, or OWASP SDLC, combining technical security with strategy, governance, and ongoing improvement.
OWASP SAMM vs. SSDLC — A Comparative Perspective
The Secure Software Development Lifecycle (SSDLC) focuses on integrating security into each stage of software development, from planning to maintenance. It defines when security activities should occur during the lifecycle. However, it often stops short of explaining how to perform these activities effectively or how to measure progress across teams and projects.
This is where OWASP SAMM brings unique value.
SAMM is a maturity model that helps organizations build a structured, repeatable, and measurable application security program. It provides a complete blueprint for the OWASP SDLC, combining tactical development practices with strategic guidance, governance, and operational insight.
While SSDLC tells you that you should perform activities like threat modeling, secure coding, and vulnerability testing, SAMM explains how to organize these activities, how to improve them over time, and how to align them with business priorities. It also covers areas the SSDLC does not traditionally address, such as policy development, security awareness training, and measurement through security metrics.
By embedding OWASP SAMM into your secure SDLC, you transform it from a checklist into a living, evolving program. This alignment gives you a structured path to maturing your security posture across development, governance, and operations. In other words, SAMM helps you operationalize the OWASP SDLC.
What are the seven phases of the SSDLC and how can SAMM be used to manage them?
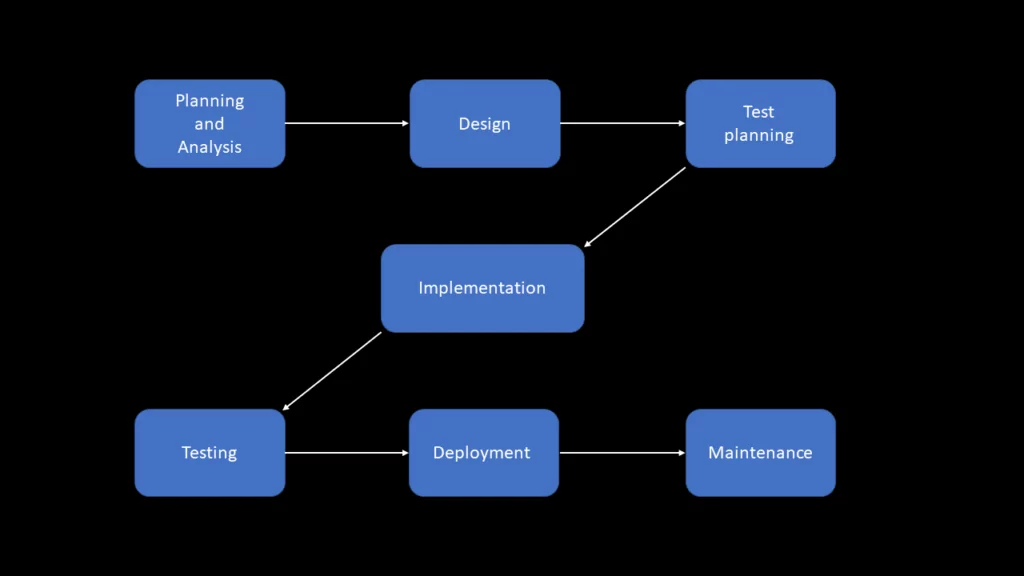
The OWASP SDLC represents a security-focused approach to software development. It integrates security from the first idea to ongoing maintenance. The traditional secure software development lifecycle consists of seven core phases: Planning and Analysis, Design, Test Planning, Implementation, Testing, Deployment, and Maintenance. Let us explore how the OWASP SAMM model strengthens each of these phases and transforms the SDLC into a truly secure and sustainable process.
1. Planning and analysis
This phase defines the project’s scope, goals, and potential risks. SAMM’s Threat Assessment and Security Requirements practices, both part of the Design function, are essential here.
-
Threat Assessment helps teams define the application risk profile and identify potential threats early on.
-
Security Requirements ensures these risks are translated into actionable security requirements, including clear expectations for external suppliers.
Together, these practices lay a strong foundation for building secure systems from the start.
2. Design
During design, architecture decisions are made that shape the system’s structure. SAMM supports this phase through:
-
Secure Architecture (Design) encourages architecture decisions based on security-by-design principles, and guides teams on technology choices based on security quality.
-
Architecture Assessment (Verification) ensures that the planned design sufficiently mitigates identified threats and meets security and compliance requirements.
This dual approach ensures that both design intent and security risk are aligned before implementation begins.
3. Test planning
Security tests need to be planned alongside functional tests. SAMM provides two relevant practices under the Verification function:
-
Requirements-driven Testing verifies that implemented controls align with your defined security requirements.
-
Security Testing goes beyond requirements and plans for static analysis (SAST), dynamic analysis (DAST), interactive testing (IAST), and manual security tests.
With these practices, your security testing will be both complete and focused.
4. Implementation
This phase involves coding and preparing the software for release. SAMM provides two practices to support this step:
-
Secure Build promotes automation in the build process, enforces secure coding standards, and manages third-party dependencies to reduce risk.
This practice help teams build and release software securely and reliably.
5. Testing
Security testing is executed in this phase, building on the plans created earlier.
-
Security Testing ensures all planned tests are run and results analyzed.
-
Defect Management (Implementation) helps track findings, coordinate remediation, and improve future security activities through feedback loops.
This structured feedback process strengthens the entire SDLC over time.
6. Deployment
In production, stability and security must be guaranteed.
-
Secure Deployment (Implementation) ensures the release process is automated, monitored, and includes security checks.
-
It also protects sensitive data and verifies that the deployment does not introduce new risks.
Deployment becomes a reliable and secure process, not a point of failure.
7. Maintenance
Security does not end after release. The final phase ensures the system remains secure as threats evolve.
-
Incident Management (Operations) defines how to detect, respond to, and learn from security incidents.
-
Environment Management (Operations) ensures systems are regularly updated, hardened, and monitored for vulnerabilities.
These practices extend your security efforts beyond development and into long-term resilience.
By applying SAMM’s guidance across every phase, organizations can implement a full-featured OWASP SDLC. Security becomes integrated, measurable, and repeatable across teams and time.
What parts of OWASP SAMM does the SSDLC not consider?
The Secure Software Development Lifecycle (SSDLC) focuses primarily on the technical steps involved in building and maintaining secure software. It addresses the development process itself, but often leaves out the broader organizational, strategic, and cultural factors that influence security outcomes.
This is where the OWASP SAMM model goes further. SAMM is not just a development guide, it is a full application security program. It includes key practices under its Governance function that are not traditionally part of the SSDLC, but are essential for building a strong and sustainable security posture. These practices are what make SAMM a true representation of the OWASP SDLC.

Policy & Compliance
This practice defines and enforces organization-wide security policies and ensures alignment with legal and regulatory requirements. While the SSDLC may apply policies, it does not provide a structure for creating or maintaining them. SAMM fills this gap by helping teams define what security means for their organization and how to enforce it consistently.
Education & Guidance
This practice focuses on building a security-aware culture through training and role-specific guidance. SAMM emphasizes the importance of making security a shared responsibility, not just a task for developers. According to Codific’s CEO, Aram Hovsepyan, the Training and Awareness stream may be the most important stream across the entire SAMM model, as it builds long-term resilience through people, not just processes. He mentioned this in the OWASP SAMM Fundamentals Course.
Strategy & Metrics
This practice connects application security to business goals. It helps teams define a clear strategy, set measurable objectives, and track progress over time. The SSDLC does not usually include performance measurement or long-term planning. SAMM ensures that organizations can prove impact, adjust priorities, and continuously improve.
Together, these practices demonstrate how SAMM extends the SSDLC into a complete OWASP SDLC. By including governance, education, and strategic planning, it gives organizations the tools to mature their security program beyond the codebase.
Utilizing SAMMY to manage your OWASP SDLC with OWASP SAMM
By now, it is clear that OWASP SAMM offers a complete and structured path for implementing a secure software development lifecycle. But how do you manage all of this in practice? That is where SAMMY comes in.
SAMMY is Codific’s security program management platform. It helps organizations evaluate, improve, and track their security posture using the full SAMM model. SAMMY supports all five business functions and fifteen security practices, making it the perfect tool for managing what we refer to as the OWASP SDLC.
The platform allows you to perform assessments, validate evidence, and prioritize improvements based on real data. You can measure maturity, plan actions, and monitor your security progress over time. SAMMY also supports other standards like NIST SSDF and ISO 27001, making it a flexible option for security programs that need to align with multiple frameworks.
What sets SAMMY apart is its focus on turning high-level guidance into concrete steps. It helps organizations not just manage their secure SDLC, but embed security into daily practices. Whether you are starting out or looking to scale your program, SAMMY provides structure, visibility, and momentum.
Even better, you can start using SAMMY for free. Join teams around the world, including security leaders like Zebra Technologies, who rely on SAMMY to run their security programs at scale.
Ready to apply the OWASP SDLC in your organization?
You’ve seen how OWASP SAMM helps implement a secure software development lifecycle in a structured, measurable way. But to truly put this into practice, you need more than a framework, you need the right tool.
That’s where SAMMY comes in.
With SAMMY, you can:
-
Explore your current maturity across all 15 SAMM practices
-
Prioritize what to improve next, based on real risk and business goals
-
Collaborate across teams using shared, structured workflows
-
Keep your security efforts visible and on track with built-in dashboards
Want to see how SAMMY can help you build a real OWASP SDLC?
Click below to get started for free.
Conclusion
Security is not something that can be bolted on at the end. It needs to be part of the way you plan, design, build, and maintain your software. That is the promise of a secure software development lifecycle, and that is what the OWASP SDLC represents.
The OWASP community does not offer a prescriptive SDLC process. Instead, it provides a complete framework through OWASP SAMM. SAMM shows you what a secure SDLC should look like and how to build it step by step. It covers not only development activities, but also governance, training, and strategy. That makes it more than just a checklist—it is a maturity model for building secure software in a sustainable way.
Whether you are just starting or already have security processes in place, SAMM can help you assess where you stand and decide what to improve next. And if you need help managing that journey, tools like SAMMY make the process smoother, more measurable, and more effective.
Building a secure development lifecycle is not easy, but with OWASP SAMM as your guide and SAMMY as your companion, it becomes possible, practical, and powerful.
Would you like some implementation guidance on the OWASP SDLC? Make sure to check out our blog post: “OWASP SDLC guidance: A story of OWASP SAMM implementation“





