Your Guide to OWASP SAMM: Insights and Best Practices
The OWASP Software Assurance Maturity Model (SAMM) is a powerful tool for improving software security practices. It provides clear steps and a structured approach, enabling teams to assess their current security posture and build better strategies. Our OWASP SAMM Guidance page is here to help you make the most of this framework. It includes practical tips, expert advice, and useful resources to guide you through implementing OWASP SAMM in your organization.
What to expect from EU CRA fines?
Updated: 25 September, 2025 24 April, 2025 Official framework, regulation and standard pages mentioned in this article CRA GDPR OWASP SAMM Regulation (EU) 2024/2847
Master Threat Modeling with Toreon’s World-Class Approach
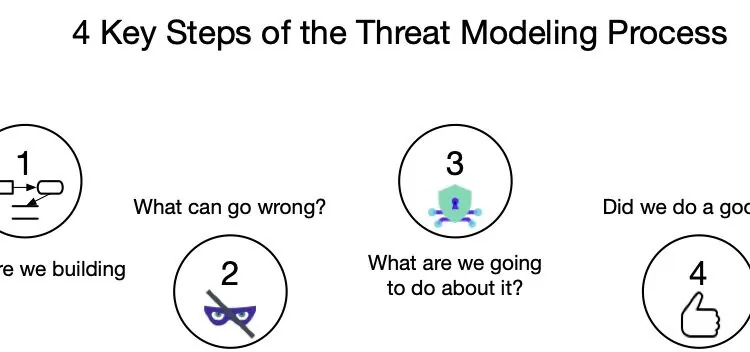
Updated: 2 September, 2025 10 April, 2025 Threat modeling shaped my AppSec career. It helped me wrestle with one of security’s most deceptively simple questions: “Is your system secure?”. “No” is clearly not a good answer. But “yes” is even worse. It signals that someone has no idea how security really works. Learning how to do threat modeling gave me a better way to answer that question: “Here are the threats and the risks we identified. And here’s how we are mitigating them.” Over the past few years, threat modeling has gone through a strange evolution. Once ignored, it is now getting attention. Yet many organizations still struggle to do it right. Some even claim that threat modeling is dead and suggest we should start calling it “attack modeling” instead. Others have embraced it, but often in ways that miss the point entirely. What I have seen time and time again[…]
OWASP SAMM: A Comprehensive Introduction
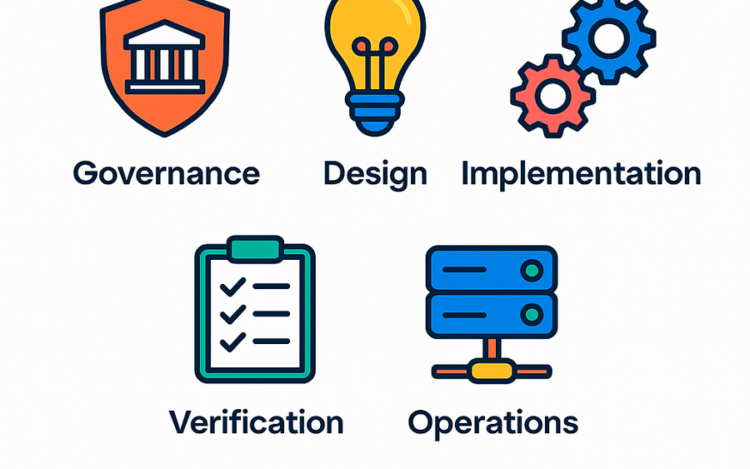
Updated: 1 December, 2025 4 April, 2025 Modern software development moves fast, and so do the security challenges that come with it. For many organizations, building secure software isn’t just about following a checklist. It’s about having a structured, practical, and realistic approach to improving security over time. That’s where the OWASP Software Assurance Maturity Model (SAMM) comes in. OWASP SAMM provides a flexible framework for assessing and growing your organization’s software security posture. Whether you’re starting from scratch or looking to refine a mature program, SAMM helps you align security with business risk, measure progress, and plan concrete improvements. In this guide, we’ll walk you through what OWASP SAMM is, how it’s structured, and how it compares to other popular frameworks. You’ll also learn how to get started with implementation and where SAMM fits within the broader application security landscape. Five key takeaways of this article OWASP SAMM[…]
How to implement OWASP SAMM: Tooling, Example and Mistakes to Avoid
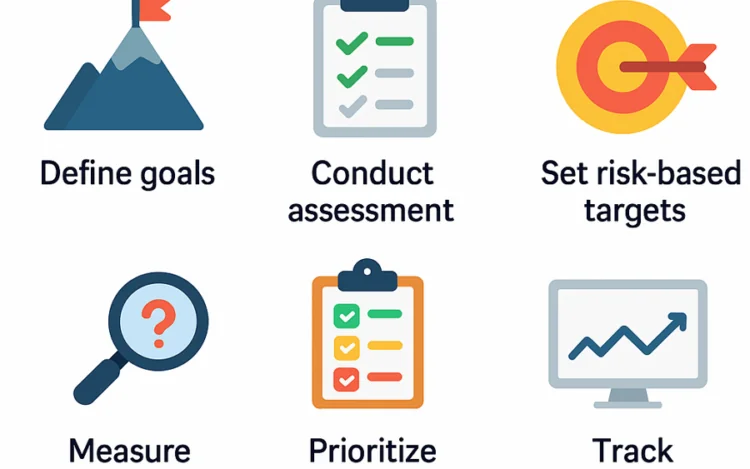
Updated: 24 September, 2025 4 April, 2025 Understanding OWASP SAMM is only the beginning. The real value comes from using it to drive measurable improvements in your software security posture. But OWASP SAMM implementation isn’t just about filling out an assessment, it’s about creating a practical, risk-aligned process your teams can follow over time. In this guide, we walk through a step-by-step approach to implementing OWASP SAMM using SAMMY. You’ll see how to define scope, assess maturity, set meaningful targets, and track progress. All supported by real features and screenshots from SAMMY’s Playground environment. You’ll also see how SAMM is applied in a real-life case study and learn about common mistakes to avoid during implementation. Whether you’re just getting started or looking to strengthen an existing program, this blog will help you turn SAMM from a static model into a living, continuous improvement cycle. Listen to the summary of[…]
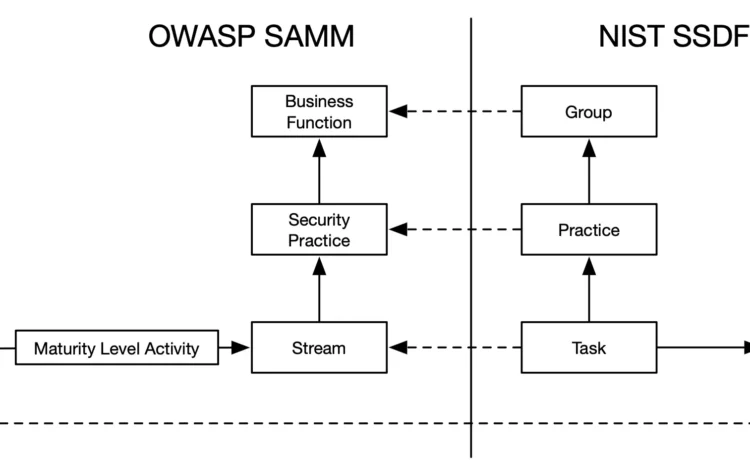
Comparing NIST SSDF and OWASP SAMM: A Comprehensive Analysis
Updated: 30 September, 2025 28 November, 2024 Over the past year, our SAMMY tool has grown significantly. It now supports not just OWASP Software Assurance Maturity Model (SAMM) but also many other frameworks and standards. Whether you need a cybersecurity framework, quality framework, maturity model, or compliance standard, SAMMY unifies them all. This versatility often raises a key question: “Which framework is best for an application security program?” OWASP SAMM stands out, but what about Building Security In Maturity Model (BSIMM) or NIST Secure Software Development Framework (SSDF)? SAMM looks excellent on paper, but SSDF comes from NIST, a highly respected organization. Meanwhile, BSIMM is popular among large enterprises. I have already written a blog on BSIMM vs SAMM. BSIMM is not cheap and even if your organization has the budget, SAMM is likely a better pick. In this post, I will focus on comparing OWASP SAMM and NIST SSDF. Key[…]
Common mistakes when implementing OWASP SAMM
Updated: 30 September, 2025 2 November, 2024 OWASP Software Assurance Maturity Model (SAMM) is one of the only comprehensive frameworks available for application security program management. Aside from BSIMM, there’s not much else around. Moreover, SAMM is open-source, making it accessible to everyone with zero barriers to entry. However there’s a catch: implementing OWASP SAMM comes with a learning curve. Beginner and even intermediate users seem to struggle with certain aspects of the model. Based on my experience, users have the hardest time figuring out: How to deal with quality criteria (or the “definition of done”) and what they mean; How to come up with a meaningful prioritization for the improvement roadmap; What type of evidence is required for demonstrating “compliance”; How to interpret the model for domains other than web application development; How can SAMM help for a smaller company. In this blog, I will offer 12 foolproof ways[…]
Supplier Security Explained: Best Practices to Manage Supplier Risk
Updated: 1 December, 2025 20 October, 2024 What is supplier risk management about? Outsourcing software development has become a cornerstone for many organizations, enabling them to accelerate innovation, reduce costs, and tap into specialized expertise. However, outsourcing also introduces specific risks, particularly in ensuring strong application security throughout the development process. This is where supplier risk management plays a critical role. By systematically addressing supplier-related risks, organizations can maintain a secure software supply chain while reaping the benefits of outsourced development. In this blog, I will explore best practices for supplier risk management in the context of outsourced software development, offering actionable steps to ensure security is embedded across the software development lifecycle (SDLC). Here’s a quick overview of three key pillars of managing supplier risks in outsourced development, adapted from OWASP SAMM, listed in order of progressive difficulty: Supplier Evaluation: Assess potential suppliers against your organization’s security requirements, ensuring[…]
Software Security Requirements Explained: Why It Matters and How to Implement It Effectively
Updated: 1 December, 2025 19 October, 2024 Introduction to software security requirements Despite clearly understanding the importance of security requirements, organizations seem to struggle with figuring out how to implement security requirements for their SDLC (secure software development lifecycle). In this blog, we will provide an in-depth analysis and insights on how to do this right. Requirements in general and security requirements in particular establish the common theme throughout the software development lifecycle (SDLC). The whole product and solution development starts with business analysts specifying what needs to be developed. Requirements are the building blocks for those specification documents. The architects create a software architecture that implements those requirements. Developers implement those requirements conform to the specified architecture. Then verification engineers and quality assurance (QA) teams validate that the implementation correctly addresses all the requirements. Finally, the customers use the product and achieve their initial goal. In a nutshell, requirements[…]
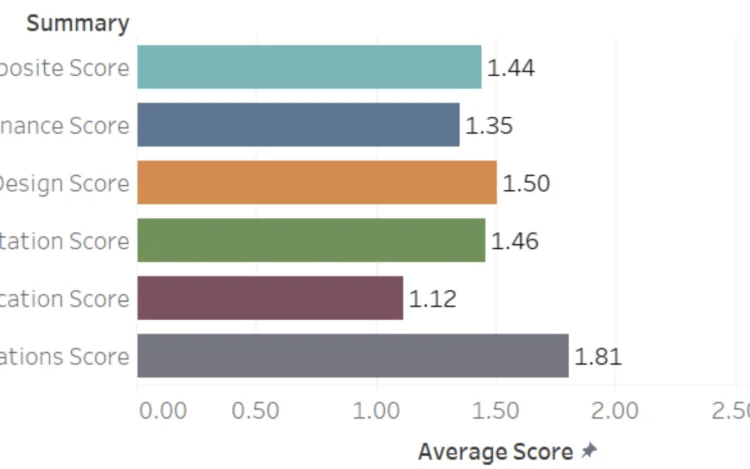
OWASP SAMM Benchmark Data Analysis
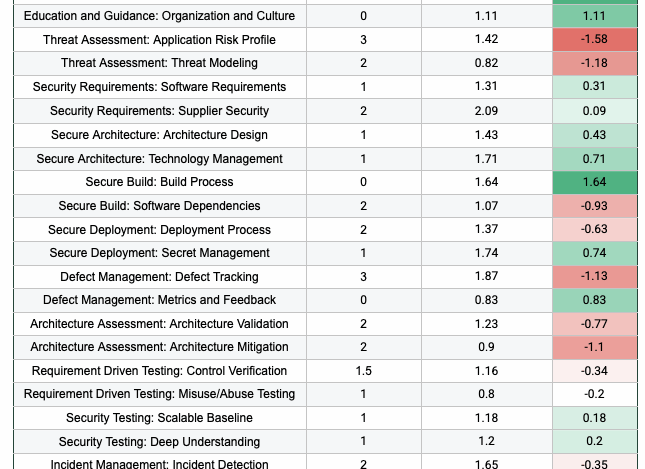
Updated: 1 October, 2025 5 October, 2024 The OWASP Software Assurance Maturity Model (SAMM) is rapidly becoming the go-to framework for application security programs, and it’s easy to see why. SAMM offers a structured, measurement-driven approach to improving product security. As a well-established framework since 2009, it helps organizations evaluate their software security maturity on a scale from 0 to 3. However, many organizations face challenges after completing their initial SAMM assessment. There’s growing interest in understanding how other organizations are progressing, making real-world data one of the hottest topics in the SAMM community. SAMM Benchmarking project aims to provide exactly that. During the past OWASP Global AppSec Conference in San Francisco the SAMM Core Team has shared the latest benchmark data. In this blog, we provide an in-depth analysis and interpretation of the OWASP SAMM Benchmark data. Key takeaways Most of the currently limited benchmark data (30 assessments) is[…]
Mapping compliance standards: Harnessing SAMMY and OpenCRE
Updated: 30 September, 2025 2 October, 2024 Cybersecurity in general and application security (AppSec) in particular are extremely challenging topics. They run broad and deep and success in one area is just not enough. A systematic solution is provided by the myriad of various (compliance) cybersecurity standards, frameworks and maturity models. CIS Controls, Cloud Controls Matrix (CCM), ISO27001, NIST SSDF, NIST CSF, BSIMM, OWASP SAMM, Cybersecurity Fundamentals, OWASP DSOMM just to name a few. Amongst one of the most promising solutions is the OWASP Software Assurance Maturity Model that is rapidly becoming an industry standard within the AppSec domain. Nonetheless organizations often have to deal with more than one overlapping, complementing and even competing standards. Hence, mapping cybersecurity compliance standards and frameworks is essential in order to make sure that organizations are not reinventing the wheel. Amongst the key pressing questions nearly every organization has to deal with are: How[…]
How to do SAMM assessments: Everything you need to know
Updated: 30 September, 2025 10 May, 2024 Want to get started with SAMM? We have just the thing! Take the free OWASP SAMM training course to learn all about SAMM assessments and security. The SAMM training consists of 79 lessons with a total of 5 hours of video content. It also includes two practical case studies to practise SAMM assessments. The instructor of the course is our CEO Dr. Aram Hovsepyan. Upon completion of the course you will receive a certificate of completion. Find out more here.
Reporting with OWASP SAMM
Updated: 26 September, 2025 12 April, 2024 How to use OWASP SAMM for effective communication on security? Reporting with OWASP SAMM is very impactful when done correctly. This blog is based on first and second hand experience of implementing SAMM (Software Assurance Maturity Model) as a security programme at organizations large and small. We focus on how security leaders at the organization can communicate upwards, how SAMM can help with this, what challenges arise and how these have been mitigated at different organizations. We start from the perspective of senior leadership. What senior leadership wants. Senior leadership wants clarity, simplicity, and reliability in the information they receive. Clarity to have good visibility on the situation at hand and its implications. Simplicity in order to easily digest information and know what conclusions to draw. Reliability or the ability to trust the numbers. Yet for each of these criteria there are challenges[…]
Why Choose OWASP SAMM?
Using OWASP SAMM can help you pinpoint weak spots in your software development process and uncover actionable ways to improve. This framework is structured to assess your current practices, provide clear benchmarks, and guide you toward a more secure development lifecycle. Furthermore, whether you’re just starting with OWASP SAMM or aiming to refine your existing approach, our OWASP SAMM Guidance delivers the tools and insights you need to succeed.
Unlock Additional Resources
Our guidance connects you to a wealth of additional resources. For example, these include best practices for secure design, development, and deployment. Moreover, internal links throughout this page will direct you to case studies, practical tips, and related articles. By exploring these, you can expand your knowledge and implement improvements step by step.
How SAMMY Supports OWASP SAMM
By focusing on OWASP SAMM Guidance, your team can build stronger, more secure software. Additionally, this framework works seamlessly with SAMMY, our innovative security software. SAMMY integrates OWASP SAMM principles to simplify security assessments and streamline the improvement process. Therefore, for organizations aiming to boost their security quickly and effectively, SAMMY is an invaluable tool.
Take the Next Step
Start your journey today and discover how OWASP SAMM and SAMMY can transform your development processes. With the right tools and guidance, you can ensure your software meets the highest security standards. Furthermore, dive into our related content to explore practical steps for integrating SAMMY into your OWASP SAMM journey. Together, these frameworks empower you to protect your software and strengthen your security posture.