Updated: 1 December, 2025
4 April, 2025
Modern software development moves fast, and so do the security challenges that come with it. For many organizations, building secure software isn’t just about following a checklist. It’s about having a structured, practical, and realistic approach to improving security over time. That’s where the OWASP Software Assurance Maturity Model (SAMM) comes in.
OWASP SAMM provides a flexible framework for assessing and growing your organization’s software security posture. Whether you’re starting from scratch or looking to refine a mature program, SAMM helps you align security with business risk, measure progress, and plan concrete improvements.
In this guide, we’ll walk you through what OWASP SAMM is, how it’s structured, and how it compares to other popular frameworks. You’ll also learn how to get started with implementation and where SAMM fits within the broader application security landscape.
Five key takeaways of this article
- OWASP SAMM is a flexible and risk-driven maturity model designed to help organizations assess and improve their software security posture.
- The model is built around five business functions, 15 security practices, and 30 streams. Each stream has clearly defined maturity levels.
- SAMM stands out for its prescriptive guidance, making it actionable for organizations that want a clear roadmap toward better security.
- While it is not a compliance framework, SAMM can complement standards like NIST CSF 2.0 and OWASP DSOMM by helping teams improve underlying security practices.
- A successful implementation involves assessing current practices, setting risk-based targets, planning improvements, and tracking progress over time. All of this can be streamlined using platforms like SAMMY.
Listen to the summary of this article on the AppSec Management Podcast.
What is OWASP SAMM?
OWASP SAMM, short for Software Assurance Maturity Model, is a framework for evaluating and improving software security practices within an organization. Developed by the OWASP Foundation, SAMM is designed to be flexible and adaptable, recognizing that organizations operate in different industries, face different risks, and are at different stages of their security journey.
Unlike fixed security checklists, SAMM helps organizations grow and mature their security practices over time in a risk-driven way. It outlines a set of security practices that cover the entire software development lifecycle, grouped into five business functions. Each practice is further divided into streams and maturity levels, which define concrete, measurable goals organizations can work toward.
In essence, SAMM helps organizations move from ad-hoc security efforts to a well-structured set of best practices that align with business objectives and start from the organization’s risk profile.
Who created OWASP SAMM and when?
OWASP SAMM has its origins in OpenSAMM, a project led by Pravir Chandra and released in beta in 2008. The initial version was funded by Fortify, a company co-founded by Brian Chess. From the start, the goal was to create a free, open-source, and community-driven framework that organizations of all sizes could use to improve their software security maturity.
In 2009, OpenSAMM was officially donated to the OWASP Foundation and became OWASP SAMM. The first full release, SAMM 1.0, retained its open model and laid the groundwork for what would become one of OWASP’s flagship projects.
That same year, a separate group—led by Gary McGraw, Sammy Migues, and Brian Chess—released BSIMM1, a commercially licensed model that took inspiration from OpenSAMM Beta but focused on documenting observed practices in the industry. Since then, SAMM and BSIMM have evolved independently, with SAMM staying true to its open, transparent, and community-driven roots.
In 2019, the OWASP SAMM team launched SAMM 2.0, a major update that modernized the framework to reflect current development practices, including DevOps, agile delivery, and cloud-native architectures. The update also improved the model’s usability, consistency, and scalability for organizations of different sizes and maturity levels. Read more about the SAMM 2.0 community release here.
OWASP SAMM is actively maintained by a dedicated core team of volunteers and contributors from across the software security industry. Their work ensures that the framework continues to evolve with community input and stays aligned with real-world challenges.
Why does OWASP SAMM matter?
OWASP SAMM offers a practical way for organizations to manage and improve application security in a structured, measurable way. Many organizations struggle with fragmented or inconsistent security efforts. SAMM provides a framework to bring these together into a structured and integrated set of security best practices.
One of SAMM’s key strengths is its focus on realistic, incremental improvement. Its maturity levels help organizations set achievable goals, making it valuable for both established security programs and those just beginning to formalize their approach.
SAMM also bridges the gap between security teams and business leaders by linking improvements to business goals and risk. It encourages teams to prioritize the practices that deliver the most value and risk reduction, rather than trying to do everything at once.
As an open-source, community-driven framework, SAMM is transparent, accessible, and open to feedback. You don’t need expensive consultants to interpret it. The guidance is publicly available, shaped by practitioners, and designed to be understandable and actionable.
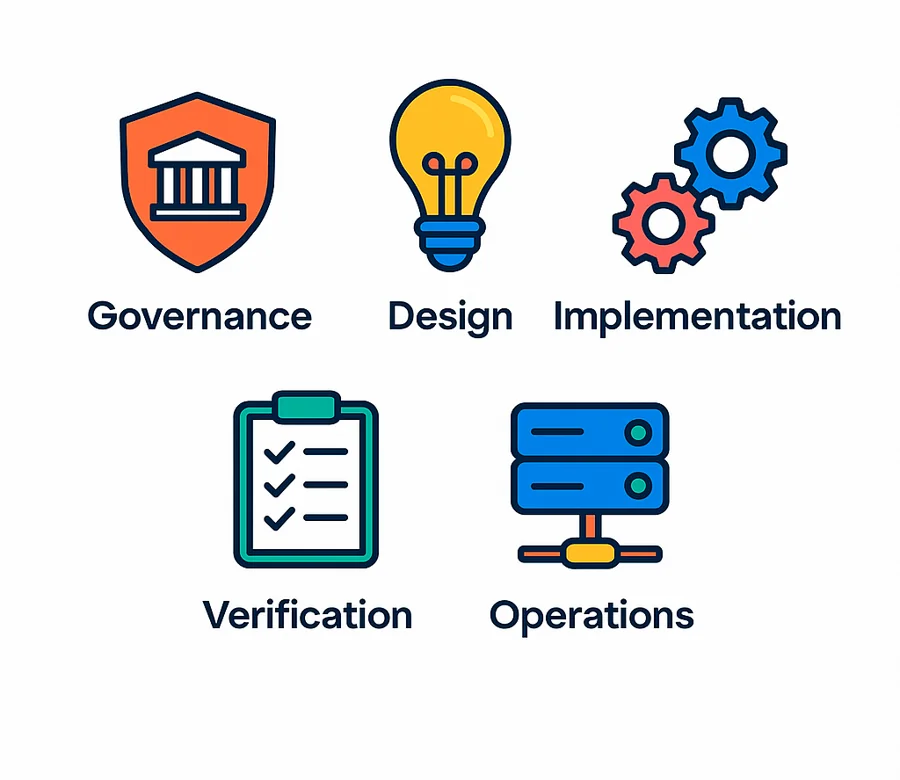
Understanding the OWASP SAMM structure
OWASP SAMM is structured to help organizations approach software security in a way that reflects how they actually design, build, and maintain software. The model is organized into five business functions. Each function is divided into three security practices, and every practice contains two streams that focus on specific areas of activity.
The image below shows how these business functions, practices, and streams are organized within the SAMM model:
This structure makes SAMM flexible and adaptable. It allows organizations to focus on the areas most relevant to their goals and risks.
Each stream is assessed across three maturity levels, which reflect how advanced an organization’s security activities are. Level 1 typically involves basic or ad-hoc activities. Level 2 represents more structured and consistent practices. Level 3 reflects optimized processes that are embedded into the organization’s way of working. There is also a tacit level 0, which means that no activity is currently being performed for that specific stream.
These levels help organizations understand their current capabilities and plan realistic improvements over time.
If you’d like a more detailed explanation of how these levels and streams work together in practice, this 14-minute video offers a clear and structured overview of the full model:
Video from the OWASP SAMM Fundamentals Course
Advantages and disadvantages of OWASP SAMM
Like any framework, OWASP SAMM comes with its strengths and limitations. Understanding both helps teams decide how to apply it effectively.
Advantages
One of SAMM’s biggest advantages is that it offers a prescriptive and practical roadmap for improving software security over time. Unlike descriptive models like BSIMM or catalogs like NIST SSDF, SAMM defines concrete, measurable maturity levels across 30 distinct streams. This helps organizations understand where they stand, where they want to go, and how to get there.
It’s also a flexible and risk-driven model. Organizations are not expected to reach the same level across all streams. Instead, SAMM encourages teams to define a target maturity based on the risk profile of their systems, making it both realistic and resource-aware.
Another key strength is that SAMM is open-source and community-driven. It’s freely available, continuously evolving, and doesn’t require buying into proprietary tooling or consulting to get started. And because SAMM has an active and growing community, teams can ask questions, share experiences, and get support from practitioners with real-world implementation experience, without needing to pay hundreds or thousands of dollars per hour for external consultants.
Disadvantages
SAMM does require some upfront effort to learn and interpret, especially for teams new to maturity models. While it provides structured guidance, its flexibility also means teams need to make thoughtful decisions about scope, targets, and priorities.
Additionally, SAMM doesn’t come with a strong built-in benchmarking dataset like BSIMM does. While BSIMM aggregates data from hundreds of real-world assessments, SAMM is focused on internal measurement and continuous improvement. SAMM does have an initial benchmark but there is still room for improvement before it is comparable to the BSIMM one.
It’s also important to note that SAMM is not a compliance framework. While implementing SAMM may help organizations move closer to compliance with standards like ISO 27001 or the NIS 2 directive, it doesn’t always map directly to regulatory checklists. If your primary goal is to meet legal or contractual obligations and avoid penalties, then a compliance-focused framework may be more suitable. However, if your objective is to build real, risk-aligned security capabilities, SAMM is a more effective long-term approach.
How OWASP SAMM compares to other maturity models
While OWASP SAMM is one of the leading maturity models for software assurance, it’s not the only option. Many organizations also consider alternatives like NIST CSF 2.0, BSIMM, or OWASP DSOMM, depending on their goals and constraints. The table below provides a high-level overview of how these models compare:
Overview Comparison Table
| Framework | Type | Purpose | Approach | Maturity Levels | Assessment Style | Primary Audience |
| OWASP SAMM | Prescriptive Maturity Model | Guide organizations in evaluating and improving software security posture | Prescriptive, measurable activities across 15 practices and 5 business functions | Yes (0–3) | Self or third-party assessment | All software-producing organizations |
| NIST CSF | Descriptive Maturity Model | Improve cybersecurity risk governance across the enterprise | Defines high-level cybersecurity outcomes across six functions | Yes (0-4) | Self-assessment or third-party assessment | Organizations managing cybersecurity at the enterprise level |
| BSIMM | Descriptive Maturity Model | Describe observed AppSec activities across real organizations | Aggregated insights from 130+ security programs | Yes (activity-based) | Observation-driven benchmarking | Organizations improving AppSec programs |
| OWASP DSOMM | Compliance Framework | Improve security in DevSecOps pipelines | Technical, activity-based maturity levels across DevSecOps domains | 5 levels, tailored per sub-dimension | Self or third-party assessment | Organizations with DevSecOps pipelines |
How do the models compare to each other?
Compared to these models, OWASP SAMM stands out for its prescriptive guidance and flexibility. Unlike BSIMM, which is observational and descriptive, SAMM offers a clear improvement path. It doesn’t just show you what others are doing, it helps you define where you are, where you want to go, and how to get there. For a deeper comparison, see our blog on “BSIMM vs SAMM“.
While NIST CSF 2.0 focuses on strategic, organization-wide cybersecurity outcomes, it does not provide detailed guidance for software security. SAMM complements CSF by translating high-level goals into concrete, measurable practices for development teams. We cover this comparison in more detail in our post on “Comparing NIST CSF and OWASP SAMM“.
While OWASP SAMM focuses on secure software assurance across the organization, OWASP DSOMM targets the implementation layer of modern DevSecOps workflows. SAMM defines security practices at the governance and process level, while DSOMM zooms in on technical activities inside CI/CD pipelines. Used together, SAMM sets the strategic direction and DSOMM drives engineering adoption. We explore this comparison in more detail in our post on “DSOMM vs SAMM“.
In short, if your goal is to build a practical, adaptable, and risk-aligned AppSec program, OWASP SAMM provides a strong foundation. It can be used on its own or in combination with other models. For organizations that value continuous improvement, measurable maturity, and prescriptive guidance, SAMM stands out as a comprehensive and implementation-ready option.
How to implement OWASP SAMM
Implementing OWASP SAMM doesn’t require overhauling your entire development process. It’s designed to be gradual and adaptable, helping organizations of all sizes improve their software security posture in a way that aligns with their existing workflows and risk landscape.
The general process involves six key steps:
- Define your scope and goals — Identify which parts of your organization or development teams will be included, and clarify what you hope to achieve.
- Carry out a maturity assessment — Evaluate your current practices using SAMM’s maturity levels and structure.
- Set realistic, risk-based target postures — Determine where you want to be, based on the nature of your applications and the level of risk you’re willing to accept.
- Identify gaps between current and target maturity — Use the assessment results to spot areas needing improvement.
- Create and execute improvement plans — Prioritize short-term changes that will move you closer to your long-term targets.
- Track progress over time — Reassess periodically to ensure you’re making progress and to adjust your goals as needed.
To simplify this process, we created SAMMY, a platform initially built around OWASP SAMM that helps organizations manage their assessments, track maturity, assign ownership, and plan improvements, all within one intuitive environment. SAMMY also includes a Playground mode so you can explore features without impacting real data.
If you’d like a step-by-step walkthrough of how to put this process into action, including real-world examples, common mistakes to avoid, and how tools like SAMMY support each step, check out our follow-up post:
Conclusion
OWASP SAMM provides organizations with a measurable, structured, and risk-driven framework to improve application security maturity. Unlike rigid compliance frameworks, SAMM offers a flexible model that adapts to your context.
This guide has shown how SAMM helps you define your goals, assess your posture, set realistic targets, and build actionable improvement plans. With the right tooling, such as the SAMMY platform, implementation becomes more streamlined, collaborative, measurable, and actionable.
The true strength of SAMM lies in its focus on continuous improvement. Security maturity is not a one-time achievement. It requires regular reassessment as your applications, teams, and risks evolve.
If you’re ready to move beyond reactive fixes and build a proactive, governance-driven security program, SAMM offers a clear, measurable, and actionable path forward. With consistent implementation, it can help turn software assurance into a business enabler, not just a checkbox.
Whether you’re just getting started or looking to elevate an existing program, OWASP SAMM is a model worth investing in.
Official pages of the frameworks and regulations mentioned in this blog
- OWASP SAMM (Software Assurance Maturity Model)
- OWASP DSOMM (DevSecOps Maturity Model)
- BSIMM (Building Security In Maturity Model)
- NIST SSDF (Secure Software Development Framework)
- NIST CSF 2.0 (Cybersecurity Framework)
- OWASP DSOMM (DevSecOps Maturity Model)
- ISO 27001
- NIS 2