Updated: 24 September, 2025
4 April, 2025
Understanding OWASP SAMM is only the beginning. The real value comes from using it to drive measurable improvements in your software security posture. But OWASP SAMM implementation isn’t just about filling out an assessment, it’s about creating a practical, risk-aligned process your teams can follow over time.
In this guide, we walk through a step-by-step approach to implementing OWASP SAMM using SAMMY. You’ll see how to define scope, assess maturity, set meaningful targets, and track progress. All supported by real features and screenshots from SAMMY’s Playground environment. You’ll also see how SAMM is applied in a real-life case study and learn about common mistakes to avoid during implementation.
Whether you’re just getting started or looking to strengthen an existing program, this blog will help you turn SAMM from a static model into a living, continuous improvement cycle.
Listen to the summary of this article on The AppSec Management Podcast:
Key takeaways
- Implementing SAMM is a continuous, risk-driven process that goes beyond a one-time assessment.
- Defining a clear target posture is critical for guiding improvement efforts and tracking meaningful progress.
- SAMMY helps structure the entire SAMM journey by offering features like evidence uploads, target posture guidance, and improvement tracking.
- Maturity gaps can be effectively measured using the “percentage to target” metric, which highlights underperforming areas.
- Expiration dates and reassessments ensure that your security posture remains aligned with evolving risks over time.
Six key steps to implement OWASP SAMM
Translating OWASP SAMM from a framework into a working program takes more than just theory. It requires structure, alignment, and the right tooling. This section breaks down a practical, step-by-step process for implementation, focused on setting clear goals, evaluating maturity, and driving continuous improvement.
Along the way, we’ll highlight how SAMMY, our application security management platform, supports each stage with real examples. The screenshots come from Playground mode, a safe demo environment that includes realistic SAMM assessments, observations, and improvement data to help you explore the platform without touching live projects.
Define goals and scope
Before starting any assessment, it’s essential to clarify why you’re implementing SAMM and what you plan to assess. OWASP SAMM is intentionally flexible, and how you apply it depends on your organization’s structure, size, and goals.
There are two key decisions to make at this stage:
- What are your goals?
Are you trying to benchmark your current state, meet a compliance requirement, reduce risk in a specific product line, or mature your security program overall? Defining your goals early will guide the rest of the process, especially how you interpret assessment results and prioritize improvements. - What is your scope?
You don’t have to assess your entire organization at once. Many teams start with a specific business unit, product, development team, or even a single application. The official SAMM blog post on determining scope offers helpful examples and guidance for tailoring your scope to fit your context, whether centralized, decentralized, or hybrid.
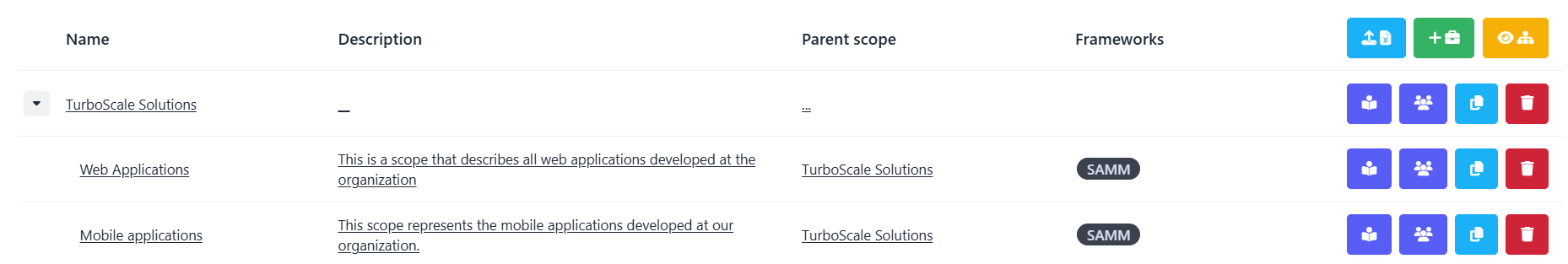
In SAMMY, scopes are a core feature of the platform. You can define and describe scopes at different levels, from broad organizational groups to focused areas like individual applications. The screenshot below shows how scopes are created and structured, each with its own description, hierarchy, and linked frameworks:
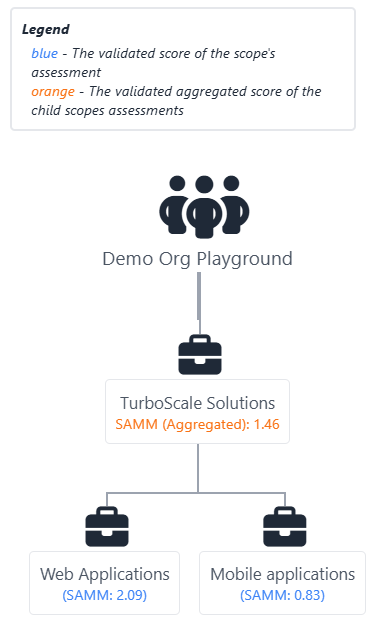
SAMMY also provides a visual hierarchy of scopes, making it easier to understand how individual assessments contribute to overall maturity. This is especially useful when assessing multiple units independently while tracking organizational progress. In the example below, you can see how the platform aggregates SAMM scores across scopes and presents both individual and overall maturity:
Clearly defining your goals and carefully scoping your assessment sets the foundation for a focused, relevant, and actionable SAMM implementation.
Conduct and validate the assessment
There are two key moments when you’ll conduct a SAMM assessment:
- Initial full assessment – to establish your baseline maturity across all streams.
- Follow-up assessments – to measure progress on practices that were targeted for improvement.
Regardless of the timing, there are two types of assessments:
- Self-assessment: Typically carried out by internal team members. This involves evaluators reviewing each stream, selecting maturity levels, and documenting supporting evidence. An optional validation step can be added, where another internal party reviews and approves the assessment. Validation tends to work well for follow-up assessments to maintain objectivity.
- External assessment: Conducted by a specialized team of security experts, either from within your organization (but independent from the assessed team) or an outside third party. For initial assessments, this approach is recommended to ensure a thorough and unbiased baseline.
Whether self-led or externally driven, the goal of the assessment is not just to assign scores but to spark meaningful discussion and gather actionable insights based on evidence.
For more detailed guidance on setting up and running assessments, including tips for first-time teams, refer to our How to conduct effective SAMM assessments blog.
SAMMY simplifies and streamlines this process by supporting role-based assessments and structured documentation:
- Evaluators select maturity levels and provide evidence through written observations and file uploads.
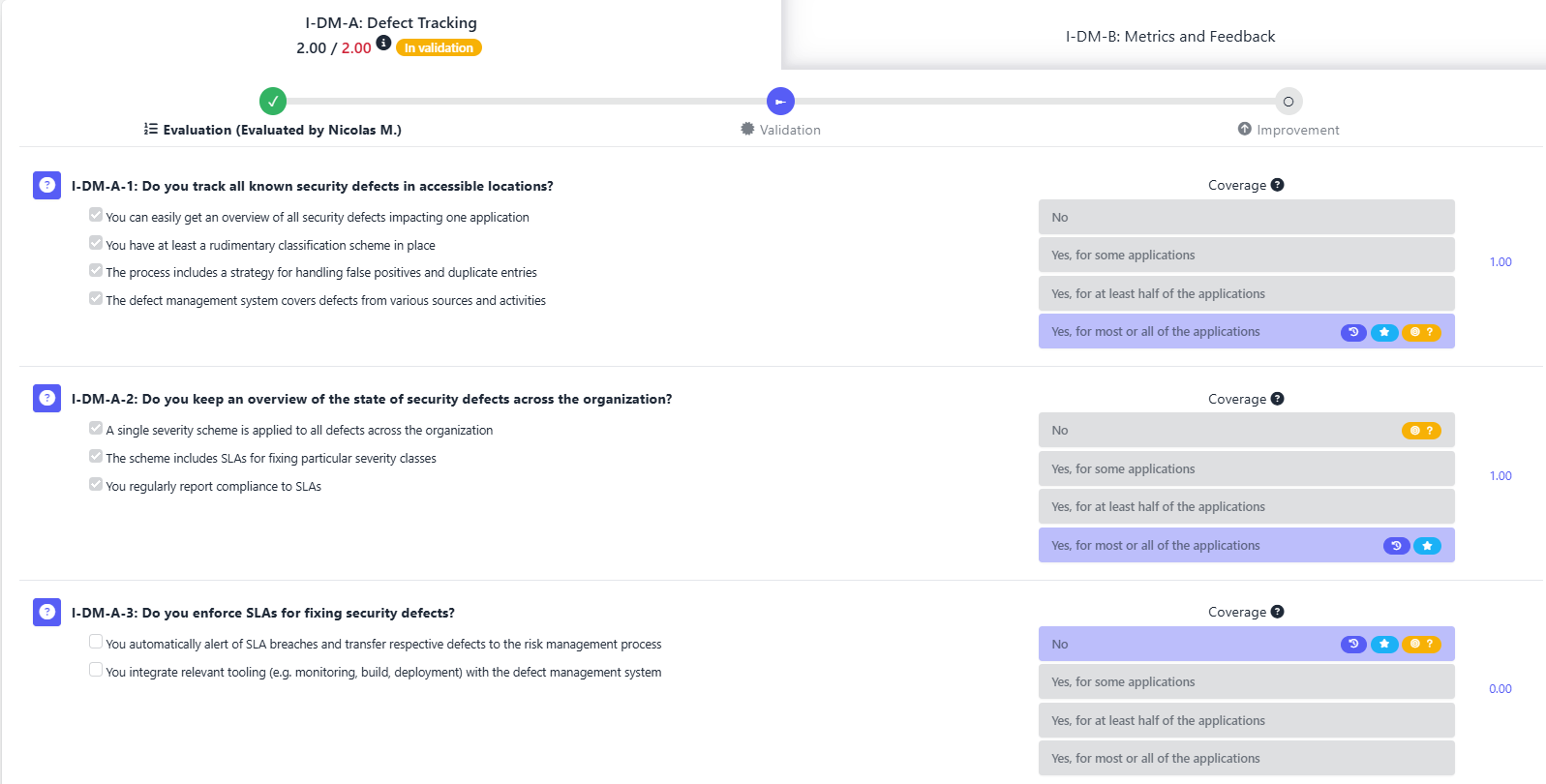
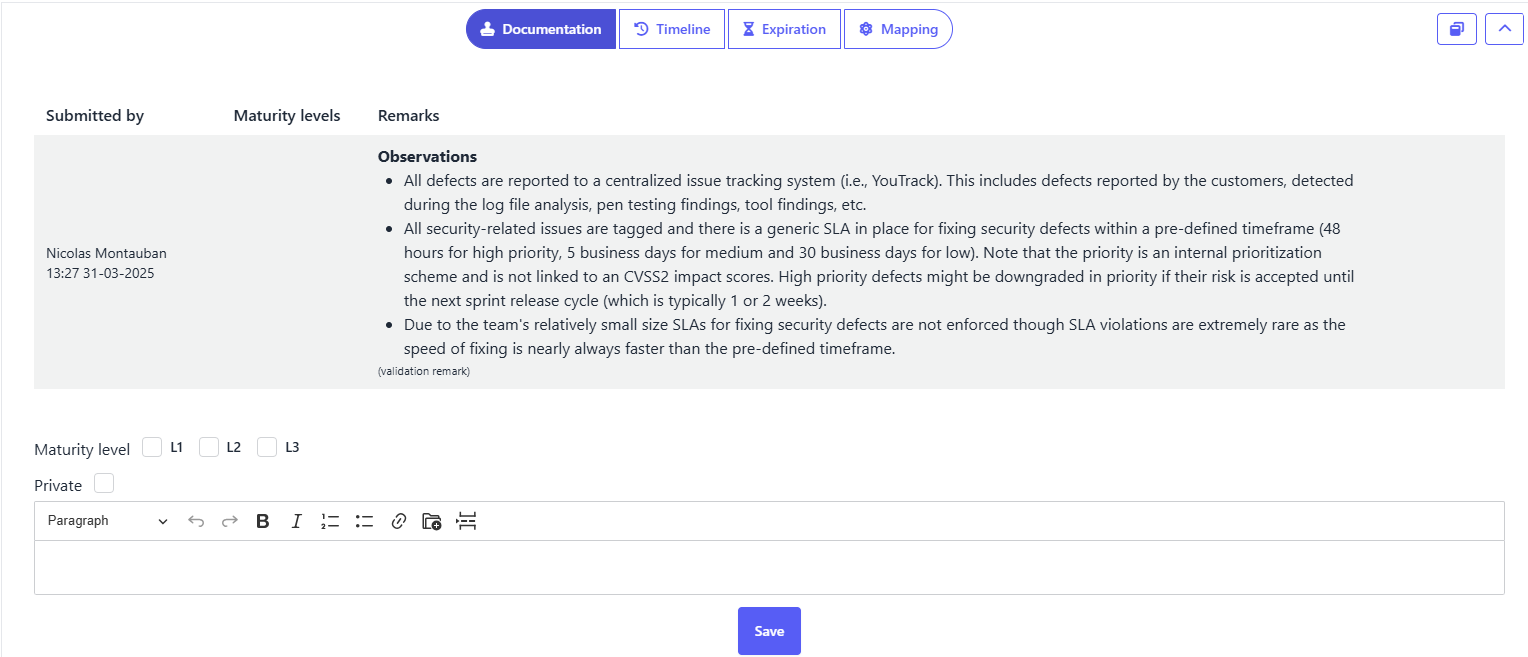
- Validators review this evidence and decide whether to confirm or adjust the score.
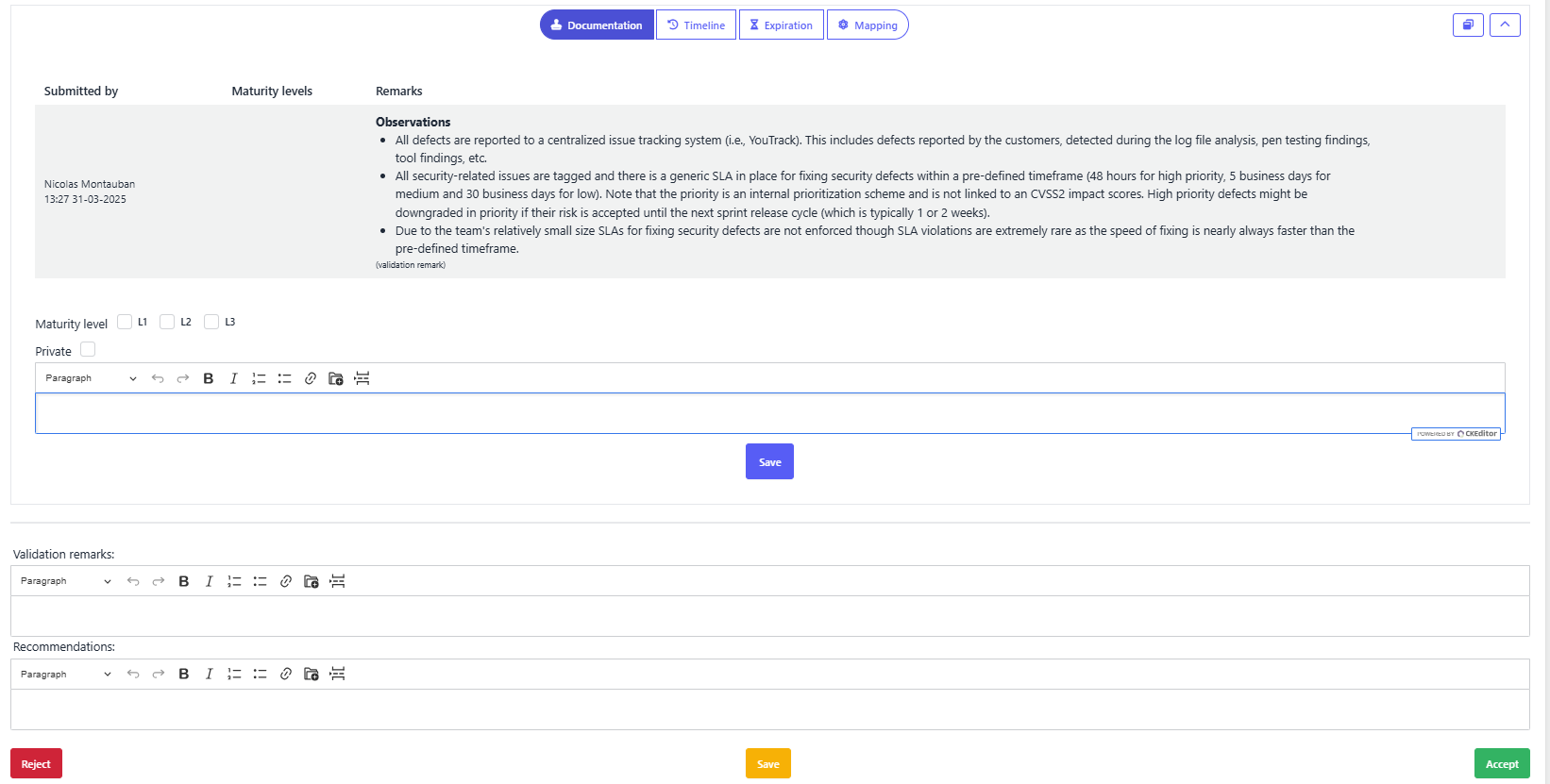
In external assessments, SAMMY enables a streamlined workflow where evaluation and validation into one step.

This structured approach helps ensure assessments are consistent, transparent, and lead directly into measurable improvements.
Start Implementing OWASP SAMM with Confidence
SAMM isn’t just about assessment—it’s about making real, measurable improvements. That’s where SAMMY comes in.
With SAMMY, you can:
-
Run and validate assessments (self or external)
-
Define target postures based on risk
-
Upload evidence and track improvement plans
-
Monitor progress with clear, visual dashboards
Try SAMMY in Playground mode, a sandbox environment pre-loaded with realistic data to help you explore the full SAMM workflow—without touching your real projects.
Ready to put SAMM into practice?
Click below to get started for free.
Set risk-based targets
Once your assessment is complete, the next step is to define your target posture, which represents where your organization wants to be in terms of software security maturity. In SAMM, this is captured using a target scope.
A target scope defines your organization’s maturity goals across all streams, guided by business priorities and risk tolerance. Rather than aiming for the maximum maturity across the board, SAMM encourages organizations to be pragmatic—setting realistic, risk-driven targets for each stream based on the sensitivity and criticality of their applications.
SAMMY allows you to create your own custom target scopes, but also offers two predefined examples:
- SAMM Low Baseline: A starting point for organizations that want lightweight, foundational controls.
- CRA Readiness Baseline: Designed to support compliance with the upcoming EU Cyber Resilience Act (CRA).
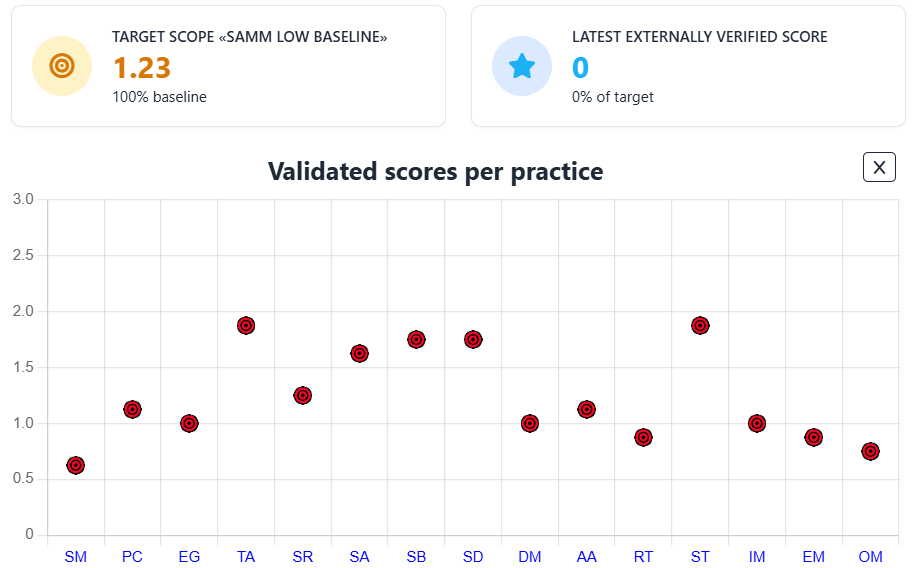
Here are examples of how these predefined target scopes look in SAMMY:
SAMM Low Baseline Targets:
CRA Readiness Baseline Target Scope:
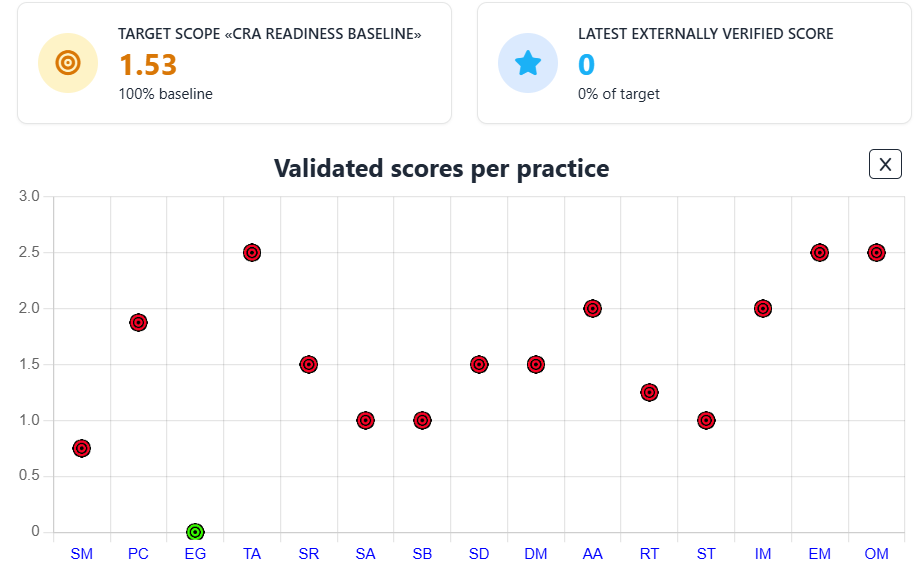
An important feature of these scopes is that they include prescriptive guidance to help teams understand exactly what’s expected to reach the defined targets. For example, in the Scalable Baseline stream of the SAMM Low Baseline, the guidance outlines what teams need to do at each level—from scanning with basic tools to fully integrating scanning into the build pipeline.
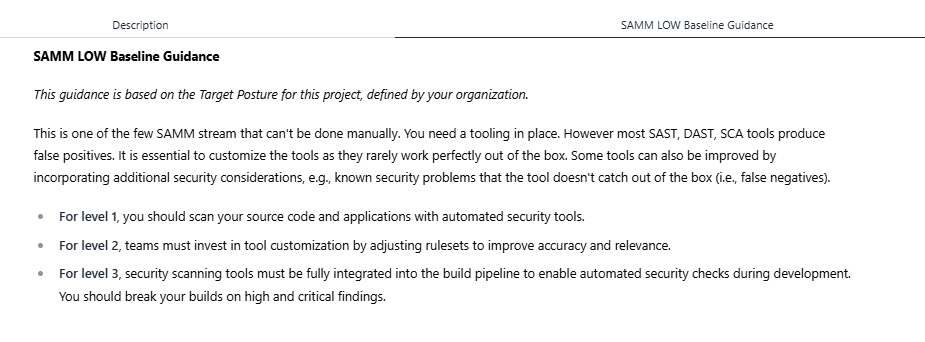
When creating a custom target scope, you can also define your own guidance for any stream. This allows you to tailor the model to your context and provide actionable advice to those responsible for implementing improvements.
For example, in the Create and Promote stream, you might write custom guidance to clarify what constitutes a strong strategic AppSec plan for your organization.
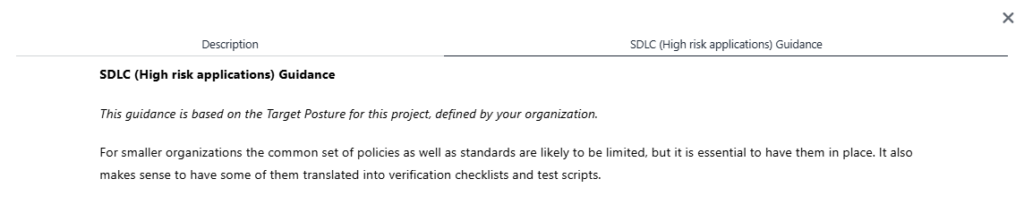
By combining structured goals with clear guidance, SAMM helps you bridge the gap between where you are and where you want to be, while keeping your teams aligned and informed.
Identify and measure maturity gaps
With your current posture and target scope defined, the next step is to measure the distance between the two, your maturity gaps.
In SAMMY, the most effective way to track this is through the Percentage to Target metric. This shows how close a scope, business function, practice, or stream is to meeting its defined targets. It’s calculated by comparing each assessed maturity level against the expected level and weighting by coverage. For example, if a scope is targeting maturity level 3 across the board but averaging level 2, it would show as 67% to target.
This metric helps you prioritize gaps by showing not just where you’re falling short, but by how much.
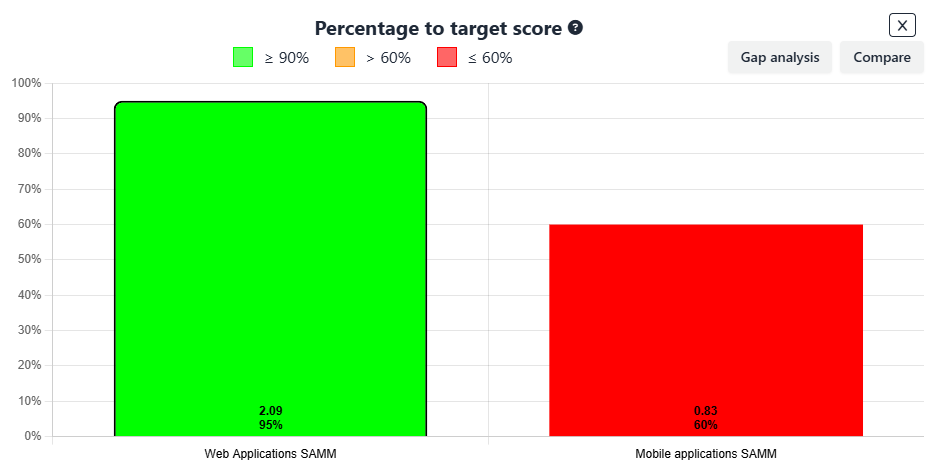
Let’s say you’re comparing two scopes, Web Applications and Mobile Applications. Comparing this based on the overall score is not ideal as the risk-profile of the applications may be completely different. Therefore, using the percentage to target, you can easily compare both scopes and see how they are doing, in the case above Mobile Applications are falling short, only reaching 60% of the target, while web application reach 95% of it.
You can also view this percentage at any level, zooming into business functions, practices, or even individual streams. In the example below, although the Design function has a strong overall maturity score of 2.38, it’s still only 85% to target:
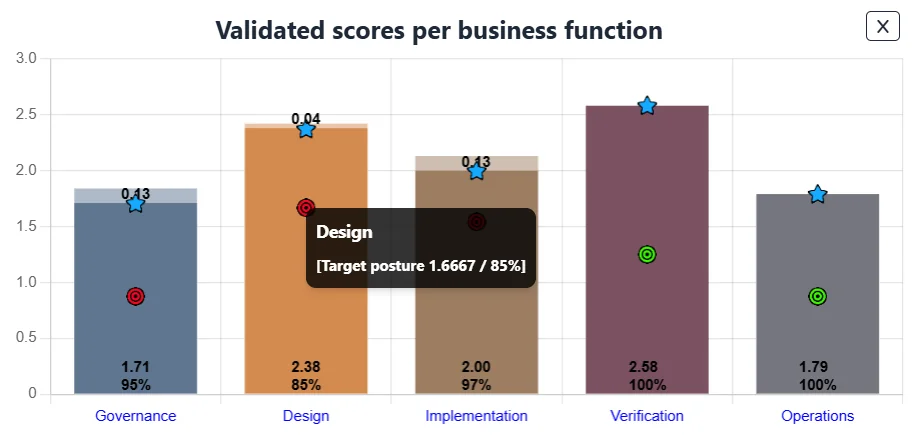
This is where SAMMY’s gap logic adds clarity. It doesn’t average performance, it checks whether each stream has met or exceeded its specific target. If one stream falls short, the entire practice or function may still be flagged, even if other areas are overperforming.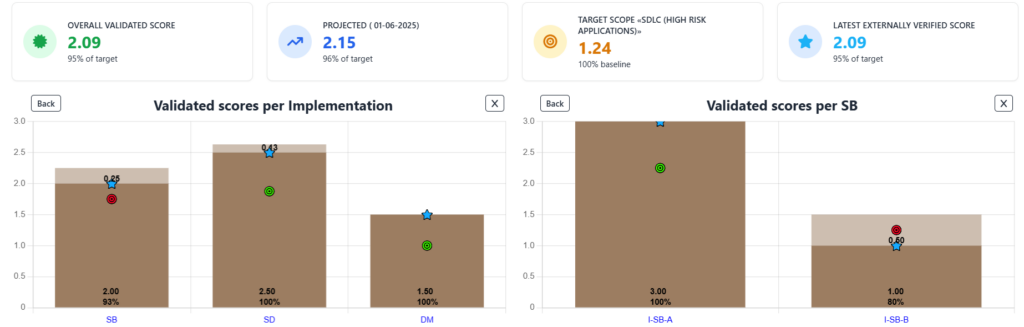 This granular view helps avoid false confidence. You might be scoring well in Secure Build – Build Process, but if Secure Build – Software Dependencies is under target, that’s a clear signal that improvement is still needed.
This granular view helps avoid false confidence. You might be scoring well in Secure Build – Build Process, but if Secure Build – Software Dependencies is under target, that’s a clear signal that improvement is still needed.
By using relative scoring and percentage-to-target, SAMMY provides a focused, measurable way to track progress, not toward perfection, but toward goals that align with your organization’s risk tolerance.
For more detail on this scoring approach, check out the official SAMM blog on relative scoring.
Build and prioritize your improvement plan
Once maturity gaps are clear, the next step is to turn them into focused, actionable improvements. The goal is to close the most critical gaps in a way that’s realistic and aligned with your target posture.
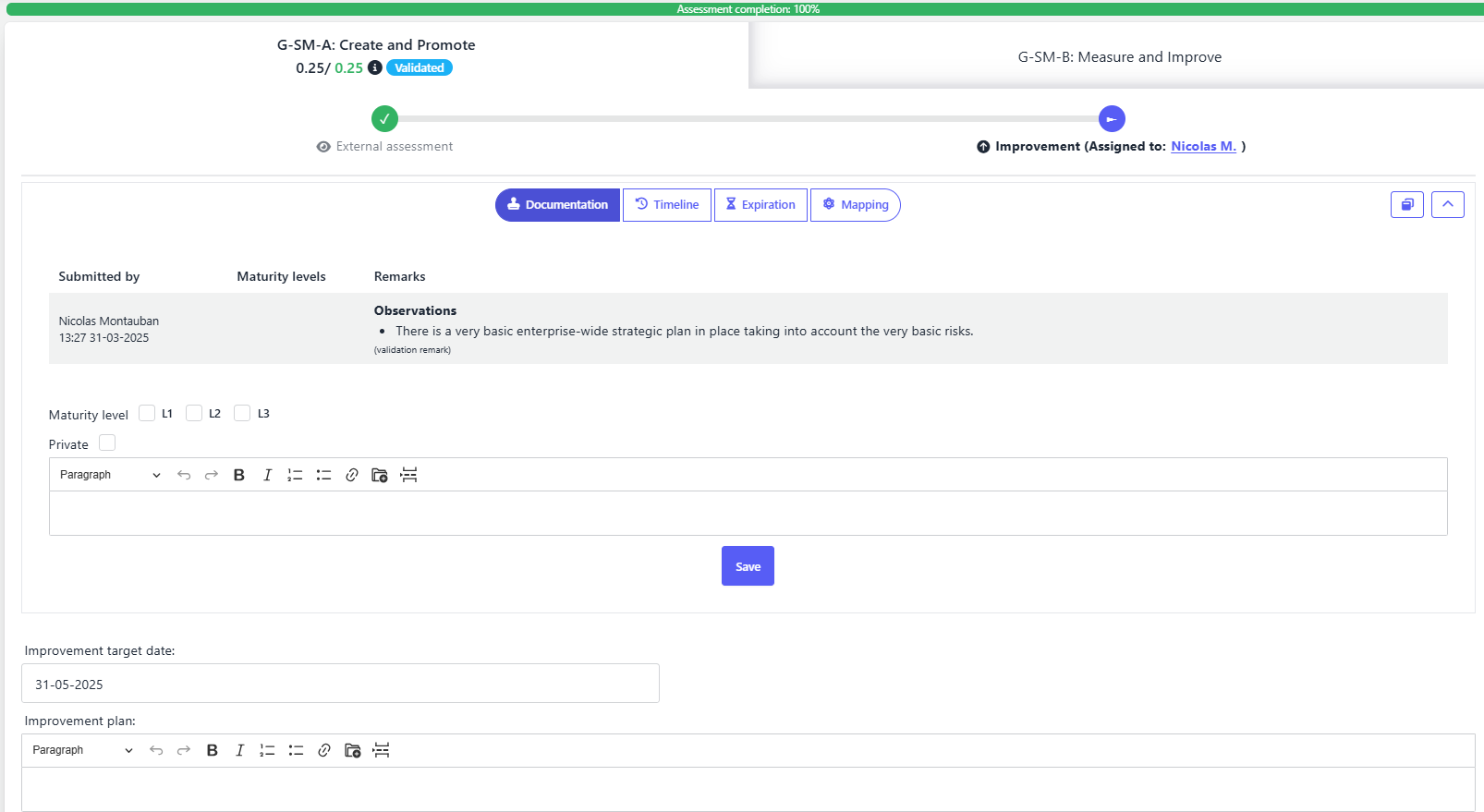
In SAMMY, you can create an improvement plan directly within each stream that hasn’t met its target. Each plan includes:
- A clear description of the actions to be taken
- Supporting documentation to guide implementation
- A target completion date
- An expected post-improvement maturity level
This structured format creates accountability and gives your teams the context they need to act.
Once a plan is defined, SAMMY allows you to model its impact. You can see how reaching the new maturity level would shift the overall score for that scope or stream. This helps prioritize which improvements deliver the most value:
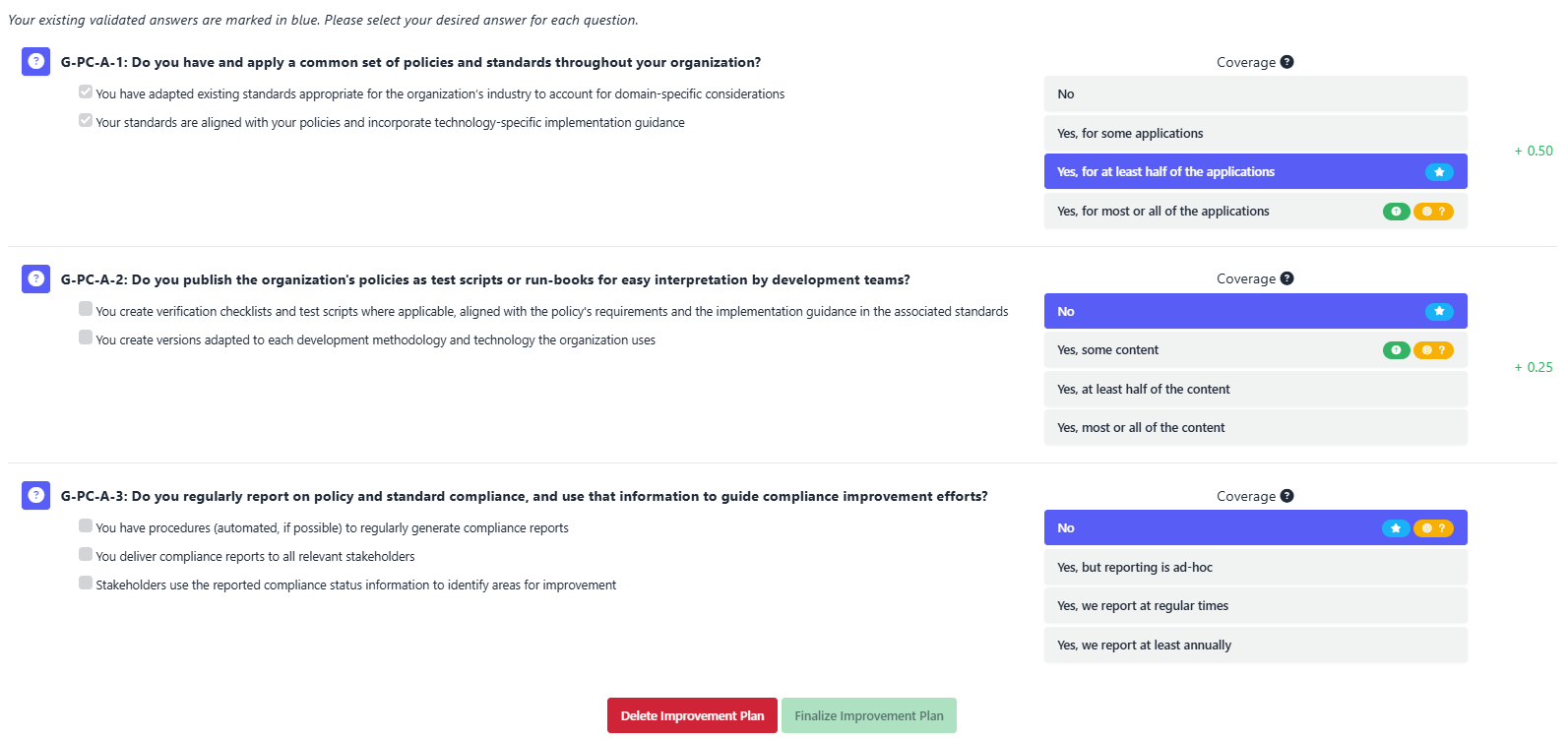
By combining planning, tracking, and scoring in one place, SAMMY removes the need for spreadsheets or disconnected tools. Your team can focus on execution with a clear, measurable path forward.
Track progress and continuously improve
Security maturity isn’t a “set-it-and-forget-it” exercise. Even after you reach your current target posture, your risk profile and organizational context may shift. That’s why SAMM emphasizes continuous improvement, not just initial achievement.
SAMMY supports this mindset with built-in capabilities to track historical performance and future projections based on your defined improvement plans. These trends help you visualize progress and understand whether you’re on track to meet your goals.
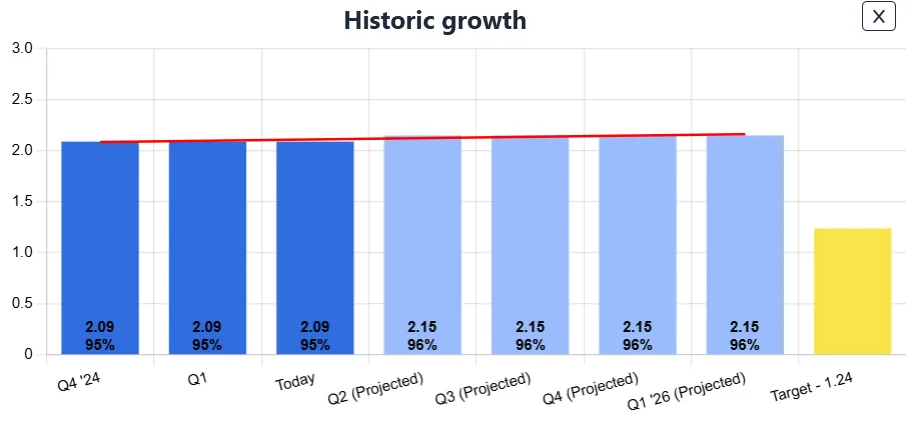
But maintaining maturity also requires regular reassessment. Many SAMM activities assume a certain cadence, such as annual training or quarterly reviews. SAMMY addresses this with score expiration, allowing you to set a validity period for each evaluation.
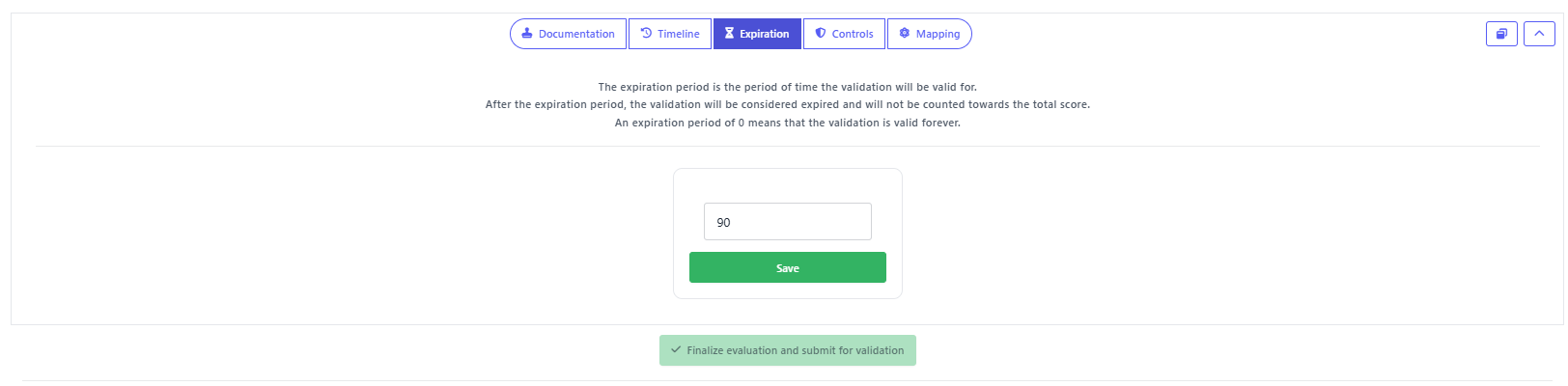 When an evaluation expires, its validation is no longer counted toward your total score. This ensures teams revisit and re-validate their practices over time. It also prevents inflated maturity levels due to outdated evidence or practices that are no longer maintained.
When an evaluation expires, its validation is no longer counted toward your total score. This ensures teams revisit and re-validate their practices over time. It also prevents inflated maturity levels due to outdated evidence or practices that are no longer maintained.
By combining visual progress tracking and automated score expiration, SAMMY reinforces a culture of continuous improvement, ensuring that security posture stays aligned with real-world risks, even as conditions change.
Wrapping up your SAMM implementation
Implementing OWASP SAMM is a practical, iterative journey. From setting clear goals and assessing your current posture to building improvement plans and tracking long-term progress, each step reinforces a structured, risk-driven approach to software assurance.
But SAMM’s real value shines when it’s applied in a real-world setting. In the next section, we’ll look at how Zebra Technologies, a Fortune 500 company, successfully rolled out SAMM across a complex, decentralized environment, bringing theory into practice at scale.
Real-life use case: SAMM at Zebra Technologies
Zebra Technologies, a Fortune 500 company in the digital solutions and automation space, adopted OWASP SAMM to bring consistency and structure to its decentralized software security program. With 35 different product and IT teams, aligning practices across the organization was a significant challenge.
Before SAMM, teams followed different approaches with no shared understanding of what strong software assurance looked like. By introducing SAMM, supported by the SAMMY platform, Zebra established a common maturity model that allowed each team to evaluate their practices, define realistic targets, and measure progress over time.
Business units performed self-assessments that were validated by the central product security team. This hybrid model offered autonomy while maintaining consistency. It also surfaced key differences between teams, encouraging knowledge sharing and the creation of tailored, risk-based target postures for different types of applications.

Using SAMMY, Zebra managed assessments, tracked improvement plans, and visualized maturity trends. This visibility helped leadership understand where investment was most needed and how overall risk posture was evolving.
What makes this case stand out is not just the initial rollout, but how SAMM became embedded in the organization’s culture. Reassessments now happen regularly, and targets are adjusted as product risks change.
For the full story, see the case study: Maturing the SDLC with OWASP SAMM at a Fortune 500 Company
Zebra demonstrates what organizations can achieve by implementing SAMM with the right structure, tools, and mindset. But not every organization gets it right the first time. To help others avoid common pitfalls, let’s take a closer look at the most frequent mistakes teams make when working with SAMM.
Common mistakes to avoid when implementing OWASP SAMM
The way you apply OWASP SAMM determines how much impact it will have even though the framework itself is flexible and well-structured. Even mature organizations often run into similar challenges during implementation.
Here are some of the most common mistakes to watch for:
- Treating maturity as the goal
SAMM isn’t about scoring a 3 everywhere. It’s about aligning software assurance activities with real business risk. Chasing perfect scores often leads to wasted effort and misaligned priorities. - Skipping the risk-based posture discussion
Defining a risk-informed target posture is foundational. Jumping into improvements without this step often results in fragmented efforts that don’t align with organizational needs. - Using SAMM as a one-time exercise
Security maturity must evolve with your environment. Teams that treat SAMM as a “check-the-box” activity miss its value as a framework for ongoing improvement. - Misinterpreting the activities
SAMM streams offer guidance, not rigid prescriptions. Taking them too literally, or without proper training, can cause confusion and poor implementation. Train assessors to understand the model before they begin. - Isolating SAMM in the security team
Software assurance isn’t just a security task. SAMM touches development, architecture, QA, and operations. Limiting involvement to the security team reduces both coverage and effectiveness.
For a deeper dive into these pitfalls, check out the full article: Common Mistakes When Implementing OWASP SAMM
Conclusion
Successfully implementing OWASP SAMM is not about checking boxes, it’s about driving lasting, risk-aligned improvements in software security. By following a structured process, setting realistic targets, and continuously reassessing progress, organizations can embed security into their development culture.
With the help of SAMMY, this journey becomes more actionable and visible. From managing assessments to tracking improvements and expiring outdated validations, SAMMY supports each step of the process with clarity and precision.
Whether you’re just starting or refining a mature program, OWASP SAMM, supported by the right tools and mindset, offers a clear and sustainable path toward better software assurance.