Updated: 30 September, 2025
7 December, 2024
The U.S. cybersecurity strategy seems to be lightyears ahead of the EU. I strongly believe that much of the credit goes to the National Institute of Standards and Technology (NIST). This organization has been helping the U.S. federal government secure its information and systems for decades. Unlike the fragmented approach in the EU, the U.S. benefits from a centralized and specialized unit. NIST consistently produces world-class standards.
Many NIST publications are broad and high-level. However two of their more prominent special publications, NIST SP 800-53 and NIST SP 800-171, focus specifically on security controls. But what’s the difference between the two? Surprisingly, not that much—yet they serve distinct purposes. Let’s dive into it.
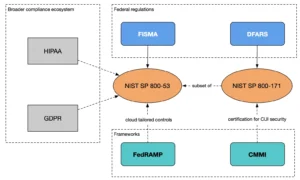
Overview of NIST SP 800-53
NIST SP 800-53 is a comprehensive catalog of security and privacy controls. Think of it as a giant toolbox of risk-mitigating measures designed to adapt to different contexts and remain future-proof against emerging threats and regulations.
NIST SP 800-53 integrates well with various frameworks, like the NIST Cybersecurity Framework (CSF). In a previous blog, we have provided an overview of CSF 2.0 and how it maps to 800-53. You can use NIST SP 800-53 even in the context of ISO27001 certification. NIST SP 800-53 is also versatile enough to support compliance with other regulations, such as HIPAA or GDPR.
Compliance Obligations with NIST SP 800-53: FISMA and FedRAMP
Compliance with NIST SP 800-53 is a cornerstone of securing federal information systems and extends to various organizations that interact with or support federal data. Here are the two most prominent compliance use cases for NIST 800-53.
- Federal Agencies: Under the Federal Information Security Modernization Act (FISMA), all U.S. federal agencies must secure their information systems using controls from NIST SP 800-53. In this blog, we have provided an overview of what is FISMA and how to implement it.
- Cloud Service Providers (CSPs): Providers offering cloud services to federal agencies must comply with FedRAMP, which tailors NIST SP 800-53 for cloud environments.
- Other Scenarios: State and local agencies that handle federal data may also need to adopt NIST SP 800-53 controls to ensure consistency in safeguarding federally sourced information.
In other words, NIST SP 800-53 creates a unified framework for addressing security challenges at scale. While it’s easy to critique, I can’t resist highlighting—yet again—how fragmented and ineffective the EU’s approach to cybersecurity often appears in comparison.
Challenges of NIST SP 800-53
NIST SP 800-53 is a classic good news–bad news situation. The good news: it’s incredibly comprehensive, offering detailed guidance to secure even the most complex information systems. The bad news: its sheer volume and complexity can easily overwhelm smaller organizations.
NIST SP 800-53 isn’t a standalone framework either. Instead, it often serves as the implementation layer for broader frameworks, like NIST CSF. While its flexibility and customizability are strengths, they also make implementation more challenging, requiring a tailored approach for specific systems and missions.
Overview of NIST SP 800-171
NIST SP 800-171 focuses on protecting Controlled Unclassified Information (CUI) in non-federal systems and organizations. It’s essentially a scaled-down version of NIST SP 800-53, tailored specifically for environments outside the federal government. This special publication outlines a simplified set of security requirements to help contractors, universities, and other organizations secure sensitive federal data.
Compliance Obligations with NIST SP 800-171: DFARS and CMMC
Compliance with NIST SP 800-171 is a mandatory requirement for organizations that handle Controlled Unclassified Information (CUI). Unlike NIST SP 800-53, which is designed for federal information systems, NIST SP 800-171 focuses on protecting CUI within non-federal environments, offering a streamlined approach tailored for external contractors and partners.
- Department of Defense (DoD) Contractors: The Defense Federal Acquisition Regulation Supplement (DFARS) Clause 252.204-7012 requires DoD contractors to implement the security controls outlined in NIST SP 800-171. This ensures that CUI remains protected across all points of the supply chain, even in non-federal systems.
- Cybersecurity Maturity Model Certification (CMMC): Building on NIST SP 800-171, CMMC introduces a tiered certification system. Organizations must not only implement the required controls but also demonstrate compliance through third-party assessments to achieve specific certification levels. This added layer of accountability helps elevate cybersecurity standards across all entities managing CUI.
While NIST SP 800-171 is narrower in scope than 800-53, its focus on non-federal systems ensures that sensitive federal information remains secure even when handled outside government networks.
NIST SP 800-53 and NIST SP 800-171: Key Differences
While both NIST SP 800-53 and NIST SP 800-171 focus on security controls, they differ in purpose, scope, and applicability. NIST SP 800-53 is broader and more comprehensive, designed for federal information systems, while NIST SP 800-171 is streamlined for non-federal systems handling Controlled Unclassified Information (CUI). Here’s a closer look at their distinctions:
| Aspect | NIST SP 800-171 | NIST SP 800-53 |
|---|---|---|
| Purpose | Protecting Controlled Unclassified Information (CUI) on non-federal systems. | Securing federal information systems and environments. |
| Scope | Limited to the security needs for handling CUI. | Comprehensive, covering all aspects of federal information systems. |
| Applicability | Non-federal organizations (e.g., contractors and subcontractors). | Federal agencies and federal contractors. |
| Control Set | 110 security requirements grouped into 14 families. | Hundreds of controls across 20 families, supporting customization. |
| Complexity | Simplified for organizations without extensive security expertise. | Detailed, robust, and highly customizable for diverse federal environments. |
| Regulatory Context | Mandated under DFARS for DoD contracts and CUI protection. | Mandated under FISMA for all federal systems. |
| Baseline | Derived from NIST SP 800-53 Moderate baseline, with tailored requirements for non-federal systems. | Full control catalog for Low, Moderate, and High impact levels. |
| Customization | Fixed requirements—no need for tailoring to specific use cases. | Flexible and customizable to fit different federal systems and missions. |
NIST 800-53 and 800-171 in SAMMY
Both NIST SP 800-53 and NIST SP 800-171 are fully supported within the SAMMY tool, enabling organizations to streamline their compliance efforts. The SAMMY platform provides an intuitive interface to navigate, implement, and monitor controls from either framework, making it easier to align your security strategy with your organizational goals.
One of SAMMY’s unique capabilities is its flexibility to mix and match controls from different frameworks. For example, an organization implementing NIST SP 800-171 to meet CUI requirements may also want to start aligning with the broader NIST SP 800-53 framework as part of a long-term goal to adopt a more comprehensive security posture, such as transitioning towards compliance with FedRAMP or other federal standards. SAMMY facilitates this hybrid approach by allowing users to map controls, identify overlaps, and manage incremental changes.
If you are interested in learning how to implement NIST 800-53 with SAMMY, you can refer to this article titled: “How to implement NIST 800-53“.
Conclusion
In short, use NIST SP 800-53 when securing federal systems and environments, especially for high-impact and diverse contexts. It offers unmatched flexibility but demands significant effort and resources.
For non-federal systems handling Controlled Unclassified Information (CUI), NIST SP 800-171 provides a streamlined and simplified approach. It’s the go-to standard for contractors and subcontractors working with sensitive federal data.
Both publications are critical for securing U.S. information, each addressing a unique set of challenges. Understanding their differences ensures organizations can meet their compliance obligations effectively while maintaining robust security.
Essential sources and references
- Federal Information Security Modernization Act.
- NIST Special Publication 800-53 Rev. 5: Security and Privacy Controls for Information Systems and Organizations.
- NIST Special Publication 800-171 Rev. 3: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.
- Cybersecurity Maturity Model Certification 2.0 Program.
- Defense Federal Acquisition Regulation Supplement (DFARS) Clause 252.204-7012.
- NIST Cybersecurity Framework 2.0



