25 February, 2025
Introduction: Application Risk Profile with Heeler
A clear understanding of risk is the foundation of any strong application security program. Yet, many organizations still rely on intuition and implicit assumptions to assess risks. This approach often leaves critical gaps in addressing real-world threats. Application Risk Profiles offer a structured way to model and manage risks, providing a roadmap to align security efforts with actual business priorities.
Building and maintaining Application Risk Profiles can seem daunting, but the right tools make all the difference. Heeler provides an automated and systematic approach to crafting these profiles, saving time and ensuring consistency. From scanning repositories and analyzing source code to offering real-time insights into vulnerabilities and architectural risks, Heeler simplifies and accelerates the entire process.
As you explore the path to maturity in managing Application Risk Profiles, this article will guide you through the key milestones of OWASP SAMM’s Application Risk Profile stream. I will also show how Heeler supports these efforts, from generating initial profiles to enabling continuous risk management and integrating with other critical security activities.
Understanding Application Risk Profiles: Why They Matter
What are Application Risk Profiles?
Application Risk Profiles are the currency of the security realm.
You have probably heard the phrase, “our application is 100% secure.” It’s an impossible claim. Security isn’t an absolute state; it’s a balance of confidentiality, integrity, and availability. Without risks, these qualities would be guaranteed by design.
An application risk profile models the threats and risks unique to a specific application. It typically includes details about threat sources, threat events, vulnerabilities, predisposing conditions, likelihood, and impact. By connecting these elements, we build a comprehensive picture of an application’s risk landscape—its risk profile.
Why Application Risk Profiles are Essential for Your Application Security Program
Application risk profiles lay the foundation for your application security (AppSec) program.
Your AppSec program should provide a structured way to address security across your software development lifecycle (SDLC). But one size doesn’t fit all. For example, OWASP SAMM outlines 30 security activities you can implement. Trying to tackle all 30 at once is costly and inefficient. On the flip side, doing nothing invites a breach.
Application risk profiles help define your organization’s acceptable risk level. They guide your focus, ensuring you allocate resources to the activities that matter most. Without them, your AppSec strategy is unfocused and reactive.
Why Should We Prioritize Application Risk Profiles?
Prioritizing Application Risk Profiles means aligning your security strategy with your actual threat landscape.
Not all security activities are equally relevant for every product or team. For instance, let’s say your team works in a controlled ecosystem like Salesforce. In that case, activities around managing third-party dependencies might not be as relevant. Alternatively, if your team builds libraries for external use, operational activities may lose significance.
Understanding your threat landscape and associated risks is the first step in crafting an effective AppSec strategy. That process begins with application risk profiles. They ensure your security program addresses your real-world risks, making them one of the highest-priority tasks in your AppSec program.
The Path to Maturity With Heeler
In this section, I will explore the maturity path for the Application Risk Profiles stream in SAMM. There are many ways to approach the risk profiles. However, having the right tools can make the process significantly more efficient and structured.
What is Heeler?
Heeler’s tool simplifies modern application security by combining code analysis, runtime monitoring, and business context. It integrates Application Security Posture Management (ASPM), Software Composition Analysis (SCA), and runtime threat modeling. All these features come together in a unified dashboard. It helps organizations prioritize and address threats based on code-level vulnerabilities. More importantly, the dashboard provides a comprehensive overview of technological risks across the entire application portfolio.
In the remainder of this section, we will focus on what good looks like for OWASP SAMM’s Application Risk Profiles and how Heeler is helping with achieving maturity.
Maturity Level 1: The Ad-Hoc Approach for Application Risk Profiles
The first step is to create an inventory of all applications in scope. This includes every application in your organization’s portfolio. Once the inventory is complete, categorize each application based on its risk and potential business impact. Evaluate and communicate to key stakeholders how confidentiality, integrity, and availability impact the business for each application.
A data breach is never pleasant. But there’s a big difference between a breach affecting your crown jewel product with sensitive private data and one involving a proof-of-concept application with minimal data.
To define the business impact, consider these questions:
- Are there compliance requirements for the application (e.g., GDPR)?
- Can external users register and use the application?
- How sensitive is the data?
- What is the application’s reputation impact on your organization?
- What is the security knowledge of the developers working on it?
- What are the availability requirements?
Heeler simplifies this process by automatically discovering, mapping, and modeling all software services into applications—without requiring an agent, tagging, or build modifications. By analyzing both runtime identity and network configuration alongside source code repositories, Heeler builds a complete, real-time inventory of applications. You can then label applications based on business impact. Heeler keeps this information up-to-date in real-time by continuously analyzing source code, third-party dependencies, and runtime behavior.
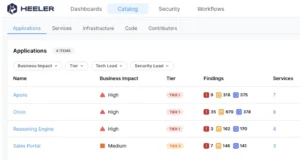
Maturity Level 2: Achieving Efficiency and Effectiveness in Application Risk Profiles
Achieving maturity level 2 in this SAMM stream requires a structured, systematic approach. A simple set of questions is no longer enough. You need to adopt a formal risk assessment methodology to analyze the risks your organization faces. Two widely recognized methodologies are NIST SP 800-30 and Factor Analysis of Information Risk (FAIR).
To make this concept tangible, let’s explore FAIR and its approach to risk analysis.

There are many ways to define risk, but it ultimately comes down to loss. Risk always includes a value component. It’s common to equate vulnerability with risk, but vulnerability is only one part of the equation. Threat Event Frequency and Loss Magnitude are the other key components. FAIR provides a clear framework for breaking risk into these factors.
Risk is defined as the probable frequency and magnitude of loss. Loss event frequency includes two elements: threat event frequency and vulnerability. Threat event frequency measures how likely it is that a threat agent will act against an asset within a specific timeframe. Vulnerability refers to the probability that the asset cannot resist the threat agent’s actions.
For example, non-internet-facing systems typically have very low threat event frequency since attackers are unlikely to act against them. At the other extreme, high-critical systems may be targeted frequently, but can resist attacks effectively if they are well-defended.
As mentioned earlier, loss is the second component of risk. FAIR breaks this down into Primary Loss Factors and Secondary Loss Factors. Primary Loss Factors represent direct, immediate losses caused by a threat event, such as a breach of data confidentiality, system downtime, or financial costs. Secondary Loss Factors refer to indirect impacts, such as reputational damage, regulatory fines, or lost business opportunities. These often arise from external reactions by customers, regulators, or the public.
Advancing to Maturity Level 2: Heeler’s Role in Risk Analysis
Heeler plays a central role in addressing this stream. It provides a detailed overview of code-level vulnerabilities and third-party dependencies, covering a significant portion of the Loss Event Frequency side of risk. Each vulnerability identified in Heeler is enriched with Common Vulnerability Scoring System (CVSS), CISA Known Exploited Vulnerabilities (KEV), and Exploit Prediction Scoring System (EPSS) . This enrichment offers valuable input for the left and right side of the risk equation. More importantly, Heeler allows organizations to define the Business Impact for each application based on a risk analysis. Business Impact is a critical element of the Probable Loss Magnitude component of risk.
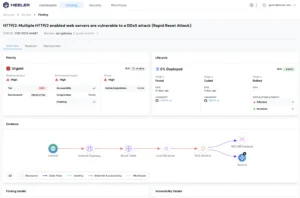
To achieve full points in this SAMM activity, you must consider all potential threats that could lead to vulnerabilities. These include insecure design, insider threats (both malicious and accidental), and misconfigurations. Despite the variety of threats, code-level vulnerabilities remain a primary attack vector for modern applications and should be a priority in any risk management strategy.
Maturity Level 3: Mastering Application Risk Profiles
Achieving maturity level 3 for this SAMM stream has two key requirements.
First, you must revisit your risk profiles regularly. Ensure they remain up-to-date by accounting for the changing threat landscape, new business risks, and significant application changes. Teams often assume nothing has changed, but this is rarely true. Threats evolve constantly—consider the rise of supply chain risks, the growing impact of ransomware, or architectural changes like adding a “Sign in with Google” feature.
Your first risk profile won’t be perfect, and that’s okay. Consistency is more important than perfection. Revisiting and refining risk profiles over time will get you closer to accuracy than trying to achieve perfection on the first attempt.
Heeler can help fast track your maturity by continuously modeling runtime software deployments (including architecture diagrams) and code changes, ensuring that any new risks, vulnerabilities, or even architectural shifts are identified in real time.
The second requirement is creating a feedback loop with other SAMM activities. At maturity level 3, your application security program should be highly integrated. Risk profiles serve as a foundation for many other streams. Let’s explore some of the key dependencies.
Application Risk Profile Dependencies with other SAMM Streams
Risk profiles directly influence your Threat Modeling (D-TA-B). Threat modeling focuses on identifying threats originating from your application, especially in architecture and data flows. It is essentially a subset of risk analysis that relies on an accurate risk profile. Hence, threat modeling depends on an accurate understanding of risk. However teams rarely have a risk profile in place, let alone understanding it. Heeler continuously updates the risk landscape, ensuring that threat models reflect current risks, not assumptions.
Risk profiles also drive your Overall Strategy (G-SM-A). Your security strategy should align with the risks you’ve identified, ensuring resources are directed toward the most critical areas. With Heeler’s real-time dashboards, security leaders can adjust security investments based on actual risks, ensuring that critical vulnerabilities in high-value applications are prioritized.
Surprisingly, risk profiles play a role in Incident Management (O-IM). Based on certain risks, you may choose to invest more heavily in incident detection or response for high-risk applications. By correlating security findings to deployed applications, Heeler helps security teams prioritize risks dynamically based on real-world exposure rather than relying on static assessments.
Another critical feedback loop is with Training and Awareness (G-EG-A). Teams must clearly understand the risks your organization and applications face. Effective training programs rely on accurate risk profiles to ensure your teams focus on the most relevant threats. One key way Heeler helps is by identifying the most common security anti-patterns and most prolific contributors, allowing for targeted education and coaching.
By automating the tracking of software deployments, vulnerabilities, and their impact on the application, Heeler ensures that risk profiles are always current, actionable, and tightly integrated into an organization’s security strategy. This directly supports organizations striving to reach Maturity Level 3 in SAMM’s risk profile management.
Master Your Application Risk Profiles with Heeler
Security isn’t just about patching vulnerabilities—it’s about understanding and managing risk systematically. Application Risk Profiles provide the foundation for a mature and strategic AppSec program, and Heeler is the ultimate tool to help you achieve the highest maturity in OWASP SAMM.
With Heeler, you can:
🔹 Automatically discover, map, and model your applications—no agent, tagging, or build modifications required.
🔹 Analyze risk at multiple levels—from code vulnerabilities and third-party dependencies to runtime behavior.
🔹 Use FAIR and NIST 800-30 methodologies to quantify risk with real-world loss estimation.
🔹 Continuously update risk profiles in real-time to adapt to evolving threats, vulnerabilities, and architectural changes.
🔹 Integrate risk profiles into your AppSec program—guiding threat modeling, security strategy, incident management, and training.
Want to take your security strategy to the next level?
Discover how Heeler helps organizations master Application Risk Profiles and reach SAMM Maturity Level 3.
Why Heeler Should be Part of Your Security Strategy
A strong application security program starts with a clear understanding of risk. Yet, many organizations still rely on intuition and implicit understanding to assess risks. This approach is not only subjective but often leads to gaps in addressing real threats. Heeler offers a practical and automated solution, helping organizations build robust application risk profiles with minimal effort. By combining architectural and source code-level analysis, Heeler automates a significant portion of the risk assessment process, making it an essential tool for security-focused organizations.
Heeler will generate a starting point for your application risk profiles
Heeler provides an excellent starting point for building risk profiles across your application portfolio. It unifies static analysis of all your repositories with runtime and business insights and generates an initial risk profile for each application based on detailed modeling of every software service that makes up the application. The tool also offers insights into your applications’ architectures, enabling you to further enhance your risk analysis process. For example, you can use this architectural data to create Data Flow Diagrams (DFDs) and conduct thorough threat modeling exercises. By automating these foundational steps, Heeler saves time and ensures consistency in your risk assessment.
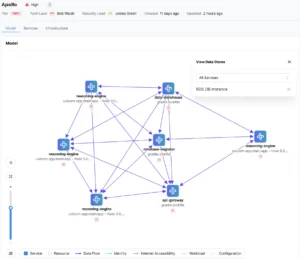
Heeler ensures continuous risk management
Managing risk isn’t a one-time effort—it requires constant vigilance. Heeler supports continuous lifecycle management by tracking, prioritizing, and resolving risks throughout the development process. As your applications evolve, Heeler keeps your risk profiles up-to-date, ensuring your security program adapts to changes in real-time. This ongoing visibility helps your organization stay ahead of emerging threats and maintain alignment between application security and business priorities.
Heeler is an answer to many other security activities
Heeler isn’t just about risk profiles; it supports many other critical SAMM activities, making it a versatile tool for your application security program.
First, Heeler integrates Software Composition Analysis (SCA), which is essential for the Secure Build -> Software Dependencies stream. By analyzing third-party dependencies, Heeler ensures you can identify and address vulnerabilities in your software supply chain.
Second, Heeler incorporates Static Application Security Testing (SAST). This capability supports the Security Testing -> Scalable Baseline stream, making Heeler a reliable choice for detecting and mitigating code-level vulnerabilities at scale.
Finally, Heeler offers seamless integration with JIRA, which aligns perfectly with the Defect Management -> Defect Tracking stream. This integration helps streamline issue tracking and resolution, ensuring risks and vulnerabilities identified by Heeler are effectively managed within your development workflows.
Heeler helps security teams eliminate friction with developers, surfacing the right risks, and enables teams to build secure-by-design without sacrificing speed. By automatically providing the runtime and business context needed to make informed decisions, Heeler empowers teams to detect, understand, and mitigate application security risks before they can be exploited.
Heeler’s versatility and automation make it a critical component for organizations seeking to build, maintain, and optimize their application security programs. From generating initial risk profiles to integrating with other key SAMM activities, Heeler delivers actionable insights and continuous support to help security teams stay ahead of evolving threats.


