Updated: 14 November, 2025
12 December, 2024
The terms information security and cybersecurity are often used interchangeably, which frequently leads to confusion. If we dig deeper, we find more related concepts making matters worse. It is not just about infosec vs cybersec, but also application security (AppSec) and the secure software development lifecycle (SSDLC). These concepts represent distinct layers within a broader security hierarchy. Understanding these differences requires recognizing the foundational roles of SDLC and AppSec. The layers are actually building on top of each other and should be considered as complementary for reducing risk.
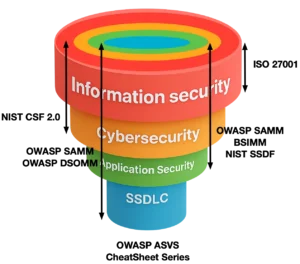
This blog breaks down these four layers: SDLC, Application Security, Cybersecurity, and Information Security. We’ll explore their unique focuses, provide example frameworks you could use to implement them, and describe how they build upon each other.
Listen to the summary of this article on The AppSec Management Podcast:
Framework scope vs level of detail
In general, the broader the frameworks the less details they provide. Take for instance the ISO 27001 framework. It is an Information Security program framework that allows organizations to manage their overall information security strategy. While ISO 27001 covers in general everything there is for an InfoSec program, it is also very high level and abstract. Though the ISO 27001 does come with a mapping to ISO 27002 that provides a list of controls which zoom deeper into the InfoSec and Cybersecurity layers. But then, ISO 27002 barely scratches the surface of the AppSec layer. Now contrast this with OWASP Cheat Sheet Series that tell you exactly which configuration options to enable for your .NET environment. The Cheat Sheet Series covers a tiny area of your SDLC, however the level of detail and the depth is immense.
This is what makes the domain of security so hard. There are so many layers of abstractions and every layer can go to an extreme level of detail, sometimes all the way to the machine executable code.
In the rest of the blog, we will focus on each layer separately.
Layer 1: Secure Software Development Lifecycle (SDLC)
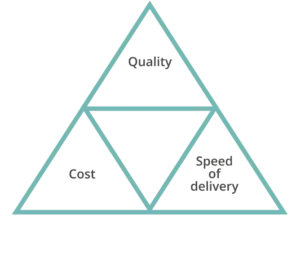
Quality is an integral aspect of the software development lifecycle (SDLC), alongside functionality. Every SDLC methodology must address quality based on the specific needs of a project. However, software development often involves balancing quality, cost, and delivery speed, and unfortunately, quality is frequently the area that receives the least attention.
To make matters worse, security—an essential dimension of quality—is even more intangible compared to other qualities like usability or performance. For instance, if a software system has poor usability, customers will quickly notice the subpar user experience. Similarly, performance issues during a pilot phase are likely to lead to rejection. In contrast, security flaws often go unnoticed until the worst-case scenario occurs: a system breach.
Whether you are leveraging Agile or Waterfall methodologies the SDLC typically consists with the following phases.
- Requirements: This stage ensures the project starts on the right foot by clearly identifying both functional and non-functional (i.e., security) goals.
- Architecture and Detailed Design: The architecture defines the system components and their interactions. A detailed design zooms further into the components and interactions.
- Implementation: At this stage, developers translate the design into actual code, emphasizing clarity and maintainability. Secure coding practices are essential for this stage.
- Verification and Validation: Verification ensures the software meets its specified requirements, while validation confirms it performs correctly in real-world conditions.
- Deployment: Deployment involves transitioning the software from development to a live environment.
Example: Adding a Secure Payment Feature to a Food Delivery App
Let’s consider a food delivery app integrating a secure payment feature. I am providing a simplified view of how the different phases in the SDLC would deal with the implementation of this feature.
- Requirements: The team decides to integrate a payment provider like Stripe or PayPal to handle transactions securely. The key requirement is to avoid storing sensitive payment data and ensure all transactions are encrypted.
- Architecture and Design: The system is designed to delegate payment processing to the provider via secure APIs. Communication uses HTTPS, and token-based authentication verifies transactions.
- Implementation: Developers integrate the payment provider’s SDK, ensuring payment tokens are securely handled. Input validation is added to protect against tampering (e.g., negative amounts).
- Verification and Validation: The feature undergoes functional and security testing. Tests confirm that communication with the payment provider is encrypted, and invalid requests are rejected.
- Deployment: Before release, API keys are securely stored in environment variables, and the feature is rolled out incrementally to monitor performance and address any issues.
Adopting a systematic approach is vital to ensuring secure development. Frameworks such as Microsoft SDL, DevSecOps Maturity Model (DSOMM), and OWASP SAMM provide structured guidance. Among these, OWASP SAMM stands out for its comprehensive coverage, prescriptive guidance as well as the measurement driven approach.
Layer 2: Application Security (AppSec)
Application Security expands upon the SDLC by adding two critical capabilities: governance and operations.
Governance ensures alignment with the organization’s broader security strategy. It includes at the very least:
- Defining the security strategy for applications.
- Measuring program effectiveness through metrics.
- Awareness and training programs for everyone involved in the software development lifecycle (e.g., developers, architects, testers).
- Compliance obligations to meet regulatory requirements.
Operations focuses on running and maintaining secure applications. Among the most critical topics in operations are:
- Incident detection and response for application-specific threats.
- Business continuity planning for applications.
- Software component and infrastructure hardening as well as secure environment management.
- Decommissioning processes for retiring applications.
Extending the Example: Application Security for a Food Delivery App
Building on the secure payment feature developed in the SDLC, the AppSec layer adds governance and operational capabilities to ensure long-term security.
Governance: The organization establishes a security strategy that aligns with its broader business goals. For instance, the team tracks metrics like the average time to address security vulnerabilities reported by users. Regular training sessions ensure developers remain proficient in secure coding practices, while periodic reviews verify compliance with organizational policies.
Operations: AppSec focuses on the ongoing maintenance and security of the app. For example:
- Incident Detection and Response: A monitoring system is implemented to identify unusual payment activity, such as repeated failed transactions, and trigger alerts for further investigation.
- Environment Hardening: The infrastructure and hosting environment are regularly patched and configured with the latest benchmark baselines from CIS.
- Business Continuity: Backups and failover systems are established to ensure the payment feature continues to function during server outages or unexpected issues.
- Decommissioning: When switching to a new payment provider, decommissioning ensures all integration points with the old provider are securely removed to prevent accidental exposure.
By expanding beyond the development process, the AppSec layer ensures that the payment feature not only starts securely but also remains secure during operation.
Frameworks like NIST SSDF, OWASP SAMM, and BSIMM support AppSec programs. For a deeper comparison of these frameworks, refer to SSDF vs SAMM and BSIMM vs SAMM. It’s worth noting that OWASP SAMM often emerges as the better choice thanks to its conceptual depth and focus on measurability.
Layer 3: Cybersecurity
Cybersecurity takes a broader organizational view, addressing risks to all digital assets. While it encompasses application security, its scope extends further. Key focus areas include:
- Governance: Establish policies and strategies to align security efforts with organizational goals. Define roles, responsibilities, and measurable objectives.
- Asset and Risk Management: Identify and prioritize risks to digital assets like systems and data. Implement controls to mitigate risks and adapt to emerging threats with regular assessments.
- Change Management: Manage system updates and operational changes securely. Test and validate changes, maintain documentation, and communicate updates to minimize vulnerabilities.
- Training and Awareness: Educate all employees on security best practices. Provide role-specific training and regular drills to ensure awareness and readiness against threats like phishing.
- Threat Mitigation: Detect, prevent, and respond to threats like malware and phishing. Use tools like antivirus software and intrusion detection systems, and have incident response plans in place.
When looking at cybersecurity vs AppSec the list of topics is largely similar, however the context and the scope is different. It is obvious that the two layers are complementary.
Extending the Example: Cybersecurity for a Food Delivery App
Building on secure development and application security, the cybersecurity layer protects all digital assets across the organization, broadening the scope beyond the app.
- Governance: A company-wide security policy ensures all departments, including IT, HR, and customer support, follow standardized protocols for handling sensitive data. Regular audits help assess adherence and identify improvements.
- Asset and Risk Management: Digital assets like customer databases, backend servers, and employee devices are cataloged. Risk assessments identify threats such as unauthorized access or misconfigured systems, and controls like network segmentation and multi-factor authentication (MFA) mitigate these risks.
- Training and Awareness: Employees across all departments participate in security awareness programs. They learn to recognize phishing attempts, follow password best practices, and securely handle sensitive information. Periodic drills test readiness for potential incidents.
- Threat Mitigation: Tools such as firewalls, intrusion detection systems, and email filters are deployed to block malware, ransomware, and phishing attempts. A business continuity plan ensures swift containment and recovery if a breach occurs.
Cybersecurity frameworks like NIST CSF 2.0 and Cybersecurity Fundamentals provide robust guidance. We believe NIST CSF 2.0 is one of the best frameworks, offering actionable insights and practical alignment with broader organizational goals.
Importantly, cybersecurity should integrate application security into the overall strategy. Tools like SAMMY help organizations align their application security and cybersecurity efforts seamlessly. However, many organizations still approach these domains separately, leading to fragmented strategies.
Layer 4: Information Security
Unlike cybersecurity, which focuses on digital threats, information security covers all threats—physical, environmental, and human. This includes:
-
Policies for Physical Security: InfoSec includes protecting physical assets, such as office buildings, server rooms, and equipment, through access controls, surveillance, and environmental safeguards (e.g., fire suppression systems).
-
Data Governance: InfoSec encompasses defining how all organizational data (both digital and non-digital) is managed, classified, and secured throughout its lifecycle. For example, printed contracts or physical backups are handled under InfoSec.
-
Incident Reporting for Non-Digital Assets: Unlike cybersecurity, InfoSec addresses incidents involving physical assets, such as theft of laptops, unauthorized document access, or breaches of restricted areas.
-
Business Continuity Planning (BCP) for Non-Digital Disruptions: While cybersecurity focuses on digital continuity, InfoSec ensures operational resilience during physical disruptions (e.g., natural disasters, power outages).
-
Legal and Regulatory Compliance Beyond Cybersecurity: InfoSec covers compliance related to physical and organizational security, such as health and safety regulations, which may not fall under cybersecurity frameworks.
Extending the Example: Information Security for a Food Delivery App
At the Information Security (InfoSec) layer, the focus shifts to protecting all organizational assets—both physical and digital—ensuring holistic security across the board.
- Policies for Physical Security: The company secures its physical assets, such as office spaces and server rooms. Access to sensitive areas, like the server room hosting backend infrastructure, is restricted to authorized personnel using access cards and monitored by CCTV. Additionally, safeguards like fire suppression systems protect equipment from environmental risks.
- Data Governance: Printed contracts with restaurant partners or physical backups of critical customer data are securely stored in locked cabinets. Clear policies dictate how these non-digital assets are handled, ensuring confidentiality and integrity.
- Incident Reporting for Non-Digital Assets: If a company laptop is lost or stolen, a process ensures the incident is reported, and appropriate measures are taken, such as disabling access to sensitive systems and tracking device activity.
- Business Continuity Planning (BCP): InfoSec ensures the company can continue operations during physical disruptions, like a power outage at the main office. Backup office spaces and power supply plans are established to avoid downtime.
Frameworks like ISO 27001 guide organizations in building holistic InfoSec programs that encompass every asset, process, and risk.
Added Complexity Through Layers
The complexity increases with each layer. Starting with the SDLC ensures a strong foundation. Progressing through application security, cybersecurity, and finally information security adds broader capabilities, ensuring comprehensive risk management.
To achieve a strong security posture, organizations should build progressively, starting with secure development and scaling outward to align application security, cybersecurity, and information security strategies.
How SAMMY Helps Align, Map and Implement Security Frameworks Seamlessly
The SAMMY tool is designed to simplify the implementation of any security framework while ensuring seamless alignment across different layers of security. Whether your organization is focused on SDLC practices, application security, cybersecurity, or information security, SAMMY provides the flexibility and integration needed to create a unified security strategy.
One of SAMMY’s standout features is its ability to manage and map multiple frameworks simultaneously. For example, if your organization uses OWASP SAMM to secure the SDLC and NIST CSF 2.0 for broader cybersecurity efforts, SAMMY allows you to align these frameworks effectively. The tool identifies overlaps, dependencies, and gaps between the frameworks, ensuring no critical aspects are missed.
In essence, SAMMY acts as a bridge between frameworks and layers, empowering organizations to implement security frameworks effectively while achieving synergy across their security initiatives. This not only reduces complexity but also maximizes the efficiency and effectiveness of your security efforts.
Conclusion
Understanding the layers of security—SDLC, application security, cybersecurity, and information security—clarifies the confusion between terms like information security and cybersecurity. Each layer plays a vital role, building upon the one before it. By adopting the right frameworks and aligning strategies, organizations can achieve a holistic and effective security posture.
Official Resources
- OWASP SAMM
- OWASP DSOMM
- OWASP ASVS
- NIST CSF 2.0
- NIST SSDF
- ISO 27001
- CyFun
- BSIMM
- CIS Security Controls
- Microsoft SDL