Updated: 30 September, 2025
28 November, 2024
Over the past year, our SAMMY tool has grown significantly. It now supports not just OWASP Software Assurance Maturity Model (SAMM) but also many other frameworks and standards. Whether you need a cybersecurity framework, quality framework, maturity model, or compliance standard, SAMMY unifies them all. This versatility often raises a key question: “Which framework is best for an application security program?” OWASP SAMM stands out, but what about Building Security In Maturity Model (BSIMM) or NIST Secure Software Development Framework (SSDF)? SAMM looks excellent on paper, but SSDF comes from NIST, a highly respected organization. Meanwhile, BSIMM is popular among large enterprises. I have already written a blog on BSIMM vs SAMM. BSIMM is not cheap and even if your organization has the budget, SAMM is likely a better pick. In this post, I will focus on comparing OWASP SAMM and NIST SSDF.
Key Takeaways
- Reputable Frameworks: Both SAMM and SSDF are developed by world-class security experts.
- Similar Coverage: SAMM and SSDF address the same core security topics.
- Measurability: SAMM offers built-in maturity measurement. SSDF can add this with frameworks like CMMI, but interpretation can be tricky.
- Guidance Style: SAMM is prescriptive, with clear quality criteria and definitions of done. SSDF is descriptive and includes optional implementation examples.
- Adoption: SAMM seems more widely used, based on personal experience.
- My Recommendation: I would choose SAMM without hesitation.
Security Frameworks
Security, like most things in life, demands a systematic approach. Fortunately—or unfortunately—the list of systematic approaches in security is extensive. Frameworks such as NIST CSF 2.0, NIST SSDF, OWASP SAMM, BSIMM, ISO 27001, COBIT, MITRE ATT&CK, CIS Controls, CSA CCM, and SAFECode are just a few examples.
To bring clarity to this list, we can categorize security frameworks into four overlapping layers, as illustrated in the figure below:
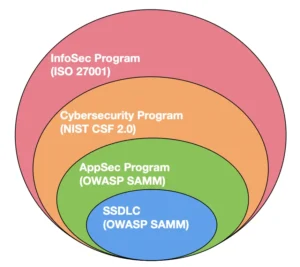
- Secure Software Development Lifecycle (SSDLC or simply SDLC)
SSDLC is a process framework that embeds security practices and controls at every stage of software development to ensure secure code and systems. Examples: OWASP SAMM, Microsoft SDL, SAFECode. - Application Security
An Application Security Program is a structured approach to managing and improving the security of applications throughout their lifecycle by integrating security practices into the SDLC. Examples: NIST SSDF, OWASP SAMM, BSIMM. - Cybersecurity
A Cybersecurity Program is a comprehensive strategy for managing and mitigating security risks across an organization’s digital infrastructure, including networks, systems, and applications. Examples: NIST CSF, Cybersecurity Fundamentals. - Information Security
An Information Security Program is a broad initiative to protect an organization’s information assets—both digital and physical—through policies, controls, and risk management practices. Examples: ISO 27001, COBIT.
Application Security Programs: A Focused List
When it comes to application security programs, the list is much shorter and easier to navigate. Here are the main frameworks you need to know:
- BSIMM (Building Security In Maturity Model): Observational framework based on practices used in large organizations.
- OWASP SAMM (Software Assurance Maturity Model): Maturity model for proactively improving application security across teams.
- NIST SSDF (Secure Software Development Framework): Government-backed framework providing guidelines for integrating security into the software development lifecycle.
These three programs form the core of application security management and provide organizations with clear paths to improve software security systematically.
NIST SSDF Overview
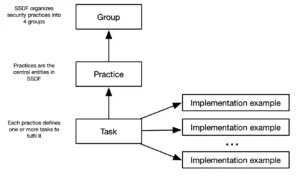
The NIST Secure Software Development Framework (SSDF) is an application security framework that provides a systematic approach to managing security throughout the software development lifecycle (SDLC). It helps organizations integrate security practices seamlessly into every stage of software development, ensuring secure and reliable applications.
SSDF structure
The framework is structured around four core practice groups: Prepare the Organization, Protect the Software, Produce Well-Secured Software, and Respond to Vulnerabilities. Each practice group addresses specific security topics and consists of multiple practices. These practices are further broken down into tasks—concrete actions required to achieve the goals of the practice. This clear hierarchy makes it easier for organizations to implement the framework step by step.
Key facts about NIST SSDF
SSDF is descriptive, offering flexibility for organizations to tailor its implementation to their needs. For each task, the framework provides notional examples to illustrate possible implementation approaches. However, these examples are optional and not exhaustive, giving teams the freedom to adapt. Additionally, the SSDF includes references to other relevant standards and frameworks, offering guidance for deeper implementation support.
One key aspect of the SSDF is its regulatory role. It is mandatory for all organizations delivering software to U.S. federal agencies, underscoring its importance in government and high-security environments. This requirement ensures that software provided to federal agencies meets stringent security standards, reducing risks and vulnerabilities.
OWASP SAMM Overview
The OWASP Software Assurance Maturity Model (SAMM) is an application security program designed to help organizations assess their current security posture, identify gaps, and develop an actionable improvement plan. Originating from OpenSAMM, first introduced in 2009, SAMM has evolved into a robust and widely adopted framework for improving software security.
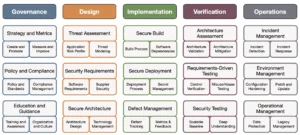
SAMM structure
SAMM is organized into five business functions, each representing a key area for security improvement: Governance, Design, Implementation, Verification, and Operations. These functions resonate strongly with stakeholders, providing a logical structure that aligns with real-world roles and responsibilities.
Each business function is divided into three security practices, offering clear guidance on specific areas of focus. These practices are further broken down into two streams, each stream outlining three activities—one for each maturity level. This structured approach ensures that organizations can progressively enhance their security practices while tracking measurable improvements.
Key facts about OWASP SAMM
SAMM is inherently prescriptive. It provides explicit guidance on what actions to take to achieve security goals, making it actionable and easy to implement. It’s also measurable by design, allowing organizations to evaluate their progress and demonstrate improvements over time. This measurability is built into the framework, enabling organizations to confidently assess their maturity and align efforts with strategic goals.
As an open-source and versatile framework, SAMM benefits from a thriving community of contributors and users. Its accessibility and flexibility have driven strong adoption across industries, making it one of the leading tools for building and maintaining effective application security programs.
Comparing NIST SSDF and OWASP SAMM
Structural comparison
When comparing the structure of NIST SSDF and OWASP SAMM, there are notable similarities at first glance.
- SSDF groups align conceptually with SAMM business functions, as both represent overarching areas of focus.
- SSDF practices correspond to SAMM security practices, addressing specific security topics within those focus areas.
- SSDF tasks resemble SAMM streams, breaking practices into actionable items.
These parallels make it easier to draw high-level comparisons between the two frameworks.
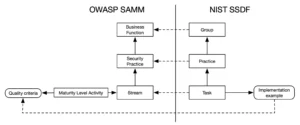
However SSDF and SAMM diverge in their depth, purpose, and level of prescriptiveness. In the next sections, I will highlight the key differences.
Content comparison
The OWASP SAMM core team and the NIST team have collaborated to create a complete mapping between SSDF and SAMM, highlighting a nearly 100% content overlap between the two frameworks. This significant alignment is good news for organizations, as it confirms that both frameworks cover all critical aspects of application security, making them robust and comprehensive solutions.
You can explore the mapping in Excel format or simplify the process with tools like SAMMY, which integrates this mapping seamlessly, helping you adopt SAMM while maintaining SSDF compliance effortlessly.
Maturity levels
A key differentiator is that SAMM is a maturity model, while SSDF is not. SAMM streams are refined further into three activities, each corresponding to a maturity level. These activities grow progressively more advanced, challenging organizations to achieve higher levels of security rigor over time. In theory, SSDF’s implementation examples could be mapped to SAMM activities, but they lack the structured progression and defined maturity levels that SAMM provides.
Quality criteria vs. implementation examples
SAMM’s quality criteria and SSDF’s implementation examples might seem similar but differ significantly:
- SAMM’s quality criteria are mandatory, exhaustive, and provide high-level guidance that organizations must meet.
- SSDF’s implementation examples are optional, specific, and not comprehensive, leaving room for interpretation and flexibility.
This makes SAMM more prescriptive and precise when we move into the measurability aspect of it. SSDF on the other hand offers more flexibility and adaptability.
Versatility
Both SAMM and SSDF are designed to be versatile, claiming agnosticism to organizational type, technology stack, or application domain. However, SSDF’s implementation examples make it more naturally adaptable to diverse contexts. SAMM’s quality criteria, while comprehensive, can sometimes feel rigid or impractical. That is especially the case for anything outside web and mobile application development. For example, criteria such as secrets rotation are easily applied to web applications, but feel disconnected from embedded software use cases.
Measurability
SAMM provides built-in measurability, allowing organizations to assess their current security posture and use this as a baseline for improvement. Its quality criteria serve as a “definition of done” for scoring maturity levels, ensuring consistency and accuracy in evaluations.
SSDF, on the other hand, lacks any inherent measurability. While tools like SAMMY have added CMMI-based scoring options to SSDF tasks, the lack of quality criteria in SSDF makes achieving a reliable score challenging. SAMM’s quality criteria address this gap, though they are sometimes criticized for being complex and unclear.
Implementation guidance
SAMM offers detailed, prescriptive guidance through its quality criteria, which specify exactly what organizations need to achieve to advance their maturity. This makes it actionable and suitable for structured improvement plans.
SSDF provides descriptive guidance with implementation examples, which are non-mandatory and adaptable. While this flexibility makes SSDF versatile, it lacks the clear progression that SAMM provides for systematically improving security practices.
Purpose and scope
SAMM is completely open source, developed to be accessible to all organizations worldwide. Its sole mission is to make every organization and application more secure, regardless of geography or industry.
SSDF is part of the NIST standards family and primarily focuses on organizations within the United States. SSDF is actually part of the CSF 2.0 cybersecurity framework. It is mandatory for organizations delivering software to U.S. federal agencies, emphasizing its national scope.
Summary: Comparing NIST SSDF and OWASP SAMM
I am very much biased towards OWASP SAMM as I am highly involved in SAMM’s ecosystem. Codific is a SAMM practitioner. However SAMM offers a number of clear advantages over SSDF and it is without any doubt in my mind the better model.
| Aspect | NIST SSDF | OWASP SAMM |
|---|---|---|
| Purpose and scope |
Developed by NIST, primarily U.S.-focused; mandatory for federal suppliers. |
Open source, designed for global use, suitable for any organization. |
| Measurability |
Requires external adaptation (e.g., CMMI) for scoring and assessment. |
Built-in measurability with clear and structured quality criteria. |
| Benchmarking |
No benchmarking provided. |
Offers a limited, but growing benchmarking to compare your security posture with peers. |
| Implementation guidance | Descriptive: provides examples but lacks clear guidance on improvements. |
Prescriptive: includes a strict “definition of done” for actionable steps. |
| Updates |
Updated once: v1.0 (April 2020) and v1.1 (February 2022). |
No fixed cadence, but updated regularly, typically at least once a year. |
| Tooling |
Limited tooling; SAMMY supports SSDF with a CMMI-based approach. |
Tools include SAMM Excel Toolbox, SAMMWise, and SAMMY. |
| Community |
No established community or engagement platforms. |
Active community with Slack channel, bi-monthly calls and biannual SAMM User Days. |
Mapping between SSDF and OWASP SAMM
While OWASP SAMM is the better choice for an application security program, SSDF is mandatory for U.S. federal suppliers. These organizations must complete an SSDF assessment to demonstrate compliance (either done as a self- or a third-party assessment). Fortunately, the SSDF-to-SAMM mapping, developed in collaboration between OWASP and NIST, allows you to use SAMM as your primary program while meeting SSDF requirements. The mapping ensures all SSDF entities align with SAMM streams, enabling you to adopt SAMM and still demonstrate SSDF conformity.
The SAMMY tool makes this even easier by automating the mapping process and generating SSDF compliance reports. This lets you benefit from SAMM’s prescriptive guidance while meeting federal obligations efficiently.

Conclusion
When it comes to selecting an application security program, OWASP SAMM is the clear winner. Its prescriptive nature and built-in measurability make it the most effective framework for driving tangible security improvements. For those needing to comply with SSDF, the SSDF-to-SAMM mapping ensures that you can adopt SAMM as your primary program and demonstrate SSDF conformity. Tools like SAMMY take this a step further by automating the mapping process, simplifying compliance, and unlocking the full potential of SAMM.
Whether your goal is to meet compliance requirements, improve security maturity, or adopt a robust application security program, starting with SAMM and SAMMY will set you on the right path. The future of application security belongs to those who choose tools and frameworks that deliver actionable guidance, measurable results, and scalable solutions—and SAMM, supported by SAMMY, is that solution.
Official frameworks
- OWASP SAMM
- BSIMM
- NIST SSDF
- NIST CSF 2.0
- ISO 27001
- COBIT
- MITRE ATT&CK
- CIS Controls
- CSA CCM
- SAFECode
- CMMI
- Microsoft SDL