The U.S. cybersecurity strategy seems to be lightyears ahead of the EU. I strongly believe […]
Application security is a complex discipline. To make things even harder for us, it is[…]
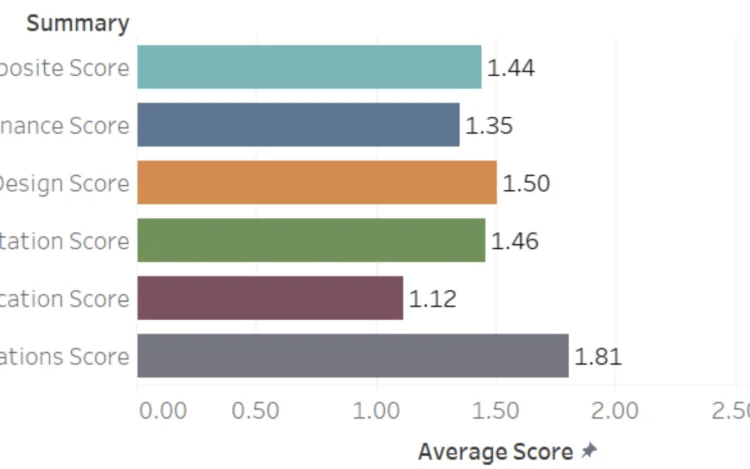
Over the past year, our SAMMY tool has grown significantly. It now supports not just[…]
What is FISMA and why is it important? The Federal Information Security Modernization Act (FISMA)[…]
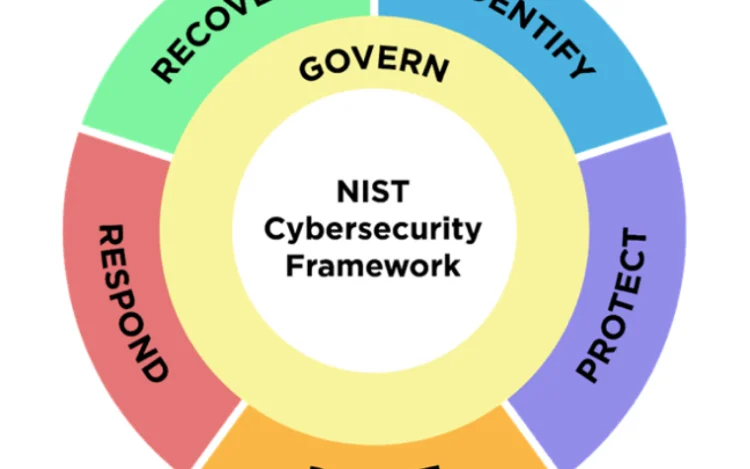
Managing cybersecurity risks requires a clear strategy combining people, processes, tools, and knowledge, all guided[…]
OWASP Software Assurance Maturity Model (SAMM) is one of the only comprehensive frameworks available for[…]
What is supplier risk management about? Outsourcing software development has become a cornerstone for many[…]
Introduction to software security requirements Despite clearly understanding the importance of security requirements, organizations seem[…]
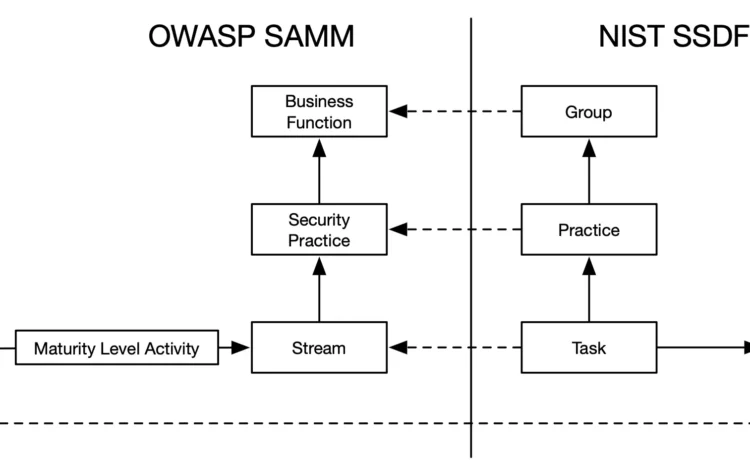
The OWASP Software Assurance Maturity Model (SAMM) is rapidly becoming the go-to framework for application[…]
Cybersecurity in general and application security (AppSec) in particular are extremely challenging topics. They run[…]
It this article we explore the essentials of the EU Cyber Resilience Act (CRA), and[…]
Want to get started with SAMM? We have just the thing! Take the free OWASP[…]