Updated: 1 October, 2025
26 September, 2023
NIST has finalized the Cybersecurity Framework (CSF) 2.0. CSF 2.0 focuses on understanding, assessing, prioritising, communicating, and above all reducing cybersecurity risks in organisations. CSF can be leveraged to describe an organisation’s current as well as target security posture. Organisations can also (in theory) compare their CSF scores between each other…. wait a minute. I’ve heard that before! I bet you did as well, especially if you’ve read our blogs on OWASP SAMM. So, I’ve decided to dive deep and provide a comparison of NIST CSF 2.0 and OWASP SAMM frameworks.
Key takeaways:
- Security is a relative concept. Both CSF 2.0 and SAMM are risk-based approaches.
- Security is everyone’s job and communication is key in both frameworks.
- CSF and SAMM are focused on security and not compliance.
- CSF is broad and covers all types of cybersecurity risks an organisation may face. SAMM is deep and zooms in on application security risks. Application security is actually missing from CSF, albeit with a reference to the NIST Secure Software Development Framework. SSDF has a full semantic mapping to SAMM, available in SAMMY.
- I would recommend using a combination of CSF 2.0 and OWASP SAMM to cover the complete spectrum of cybersecurity within your organization.
Scope: Application security vs Cybersecurity
The primary difference between NIST CSF 2.0 and OWASP SAMM lies in their scope. Please refer to an article where we provide an in-depth analysis of security layers and scopes.
OWASP SAMM is focused exclusively on application security, including the software development lifecycle (SDLC) and adjacent topics like development policies and standards, organizational security strategies tied to application security, secure development training, and operational security specific to software. In the figure below, SAMM covers both the blue and the green area of security.
NIST CSF 2.0, by contrast, takes a broader approach to cybersecurity. It addresses organizational concerns such as risk management, incident response, and infrastructure protection. While CSF 2.0 encompasses application security as part of its broader strategy, it refers to the Secure Software Development Framework (SSDF) for specific guidance on secure software practices. However we strongly believe that OWASP SAMM would be a better alternative to SSDF. In the figure below, CSF 2.0 covers only the orange area, and refers to SSDF for the blue and green areas.
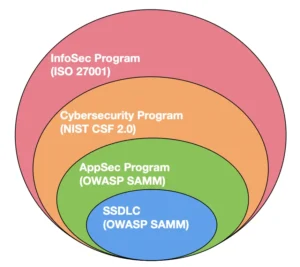
OWASP SAMM provides a precise focus on application security. CSF 2.0 delivers a comprehensive view of overall cybersecurity. Combining the two frameworks creates the most effective approach. CSF 2.0 offers the overarching structure for managing an organization’s cybersecurity strategy, while SAMM ensures a specialized and mature focus on building secure software. Together, they form a powerful, complementary toolkit for organizations aiming to address both application-specific and broader cybersecurity challenges.
In the remainder of this blog, we will focus on the conceptual similarities between the two frameworks.
The core concepts in NIST CSF 2.0 and OWASP SAMM
Conceptually both CSF 2.0 and SAMM are very similar.
- It all starts with understanding your risks and building a strategy around it.
- That strategy should not be some obscure document only the executive board knows about. You should communicate it to all stakeholders and get their buy-in.
- Finally, organisations’ behaviour change slowly overtime. Don’t try to boil the ocean. Change must be iterative driven by the right prioritisation.
Security Profiles
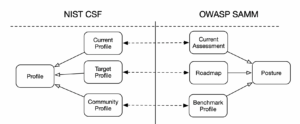
NIST CSF 2.0 and OWASP SAMM have nearly identical views when it comes to security profiles.
- Current Profile / Assessment provides an overview of the current security activities within the organisation (or scope in SAMM terminology). This is the baseline to start from.
- Target Profile / Improvement Roadmap is where an organisation aspires to get over a well-defined period in time. SAMM provides a slightly more nuanced approach where the roadmap can be defined in several increments. However this is syntactical sugar as CSF advocates running the improvement cycles repetitively.
- Community Profile / Benchmark Roadmap represent a recommended target profile for specific type of organisations or applications.
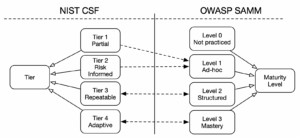
Framework Tiers and Maturity Levels
Framework Tiers in CSF and Maturity Levels in SAMM represent roughly the same idea. They characterise the level of rigor and systematically of an organisation’s security efforts within a specific security practice. The mapping between the tiers and maturity levels is not identical. Level 0 is implicit in SAMM and arguably it is also actually there in CSF. CSF differentiates between a Partial and Risk Informed outcomes. I believe both map to the level 1 maturity in SAMM, which denotes an ad-hoc approach to fulfilling a certain security practice. Tiers 3 and 4 from CSF clearly seem to map to maturity levels 2 and 3 in SAMM respectively.
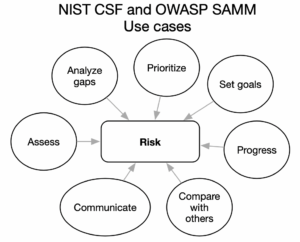
The main use cases for CSF 2.0 and SAMM
The two models take a slightly different perspective on the security realities within an organisation. However the use cases are nearly identical.
- You can leverage both CSF and SAMM to first of all assess your current security posture.
- Once you have done that you can go further and run a gap analysis.
- Chances are you will be scared how bad the situation is. Hence, to help you “eat the elephant” both frameworks can help you prioritise and set your goals.
- Once you’ve set your improvement target both frameworks provide references and implementation examples to help you progress to that target.
- One of the most common questions in the industry is “how are my peers doing”? Both frameworks enable comparing your own security posture to that of other organisations. SAMM is a lot closer to publishing such a dashboard through its Benchmark Initiative.
- Finally, an overall security posture can be communicated to external parties to assure them of your cybersecurity efforts.
The core structures in NIST CSF 2.0 and OWASP SAMM
As far as the structural comparison between CSF 2.0 and OWASP SAMM goes both models come with three main levels of security activity categorisation. In addition to the structural categories, SAMM also provides quality criteria that represent the definition of done. SAMM’s quality criteria are an extremely powerful mechanism in ensuring consistency and objectivity in SAMM assessments. To the best of my knowledge a similar mechanism is currently missing from CSF.
CSF has a planned mapping to Informative References and Implementation Examples to help organisations translate the WHAT into the HOW. In a similar way SAMM comes with a mapping to the OpenCRE project as well as core team and community guidance documents.
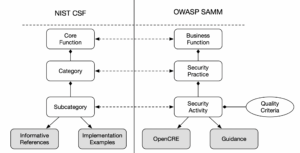
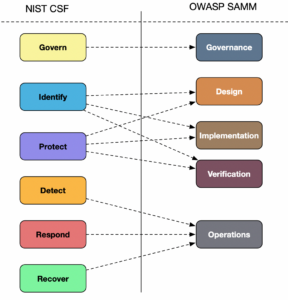
Content mapping
As I’ve already mentioned the two models have different perspectives on the security practices within an organisation. Hence a semantically rich mapping between the Core Functions in CSF and Business Functions in SAMM is not feasible. For example, consider the PR.PS-6 subcategory from CSF, which requires that “secure software development practices are integrated and their performance is monitored throughout the software development life cycle”. This single subcategory from CSF could easily be mapped to most of the SAMM model as SAMM is concerned with secure software development practices. Hence, the mapping links between the highest level entities is almost as meaningful as comparing apples to oranges. Thus take this figure with a pinch of salt.
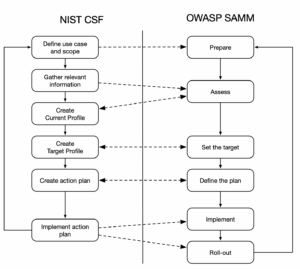
Process
Finally, the last topic we’d like to analyse is the process behind each of the two frameworks. The process is largely the same. For both CSF and SAMM the process steps are as follows:
- We prepare the assessment by defining the scope and identifying the stakeholders.
- Then we gather any relevant information and create a current profile.
- Once the baseline assessment is ready we create the target profile.
- Given the start and endpoints in our security journey we create a prioritised action plan to address the current gaps.
- Finally, we implement the plan and roll it out.
Conclusion
In this blog we’ve looked at the NIST Cybersecurity Framework through the prism of OWASP Software Assurance Maturity Model. CSF is a broader framework when it comes to viewing cybersecurity risks within an organisation. SAMM is only focused on security risks that are relevant to application security. Aside from that both frameworks are very similar in terms their core concepts and process.
If you want to learn more about OWASP SAMM you can take the free SAMM training.