Updated: 30 September, 2025
20 November, 2024
Managing cybersecurity risks requires a clear strategy combining people, processes, tools, and knowledge, all guided by risk management. The NIST Cybersecurity Framework (CSF) 2.0 provides an actionable approach to addressing these challenges. It offers guidance on everything from improving operational resilience to integrating secure software development lifecycle (SDLC) practices.
In this blog, we’ll explain how to implement NIST CSF 2.0 effectively, highlight its key features, and explore its use across different organizational contexts.
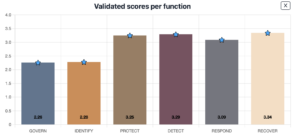
What is NIST CSF 2.0: Structural Overview
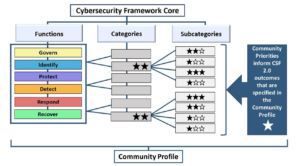
NIST CSF 2.0 is built on six core functions, which guide organizations through the cybersecurity lifecycle. These functions are Govern, Identify, Protect, Detect, Respond, and Recover. Each function plays a unique role in strengthening an organization’s security posture.
The newly added Govern function focuses on aligning cybersecurity efforts with broader organizational objectives. Identify helps pinpoint risks to systems and assets, ensuring a comprehensive understanding of vulnerabilities. Protect outlines measures to safeguard essential services. Meanwhile, Detect emphasizes mechanisms to recognize threats, and Respond focuses on mitigating the impact of incidents. Finally, Recover facilitates the timely restoration of operations while improving resilience.
Within each function, categories and subcategories (also known as outcomes) break down specific goals. This layered structure ensures clarity and allows organizations to map progress across multiple dimensions.
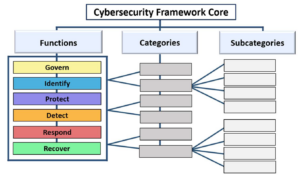
Application Security in the context: the synergy between CSF 2.0 and OWASP SAMM
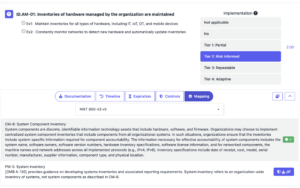
NIST CSF 2.0 is a comprehensive framework addressing all aspects of cybersecurity, with application security and the Secure Software Development Lifecycle (SSDLC) playing a critical role. The outcome “PR.DS-8: Software is securely developed and managed” directly aligns with secure development practices and points to the Secure Software Development Framework (SSDF) (NIST SP 800-218) for detailed guidance.
While SSDF provides a strong foundation, we believe OWASP SAMM (Software Assurance Maturity Model) offers a more precise and actionable approach to managing application security programs. Check out our previous blog where we provide a comprehensive analysis and comparison of NIST SSDF and OWASP SAMM. By leveraging SAMM alongside CSF 2.0, organizations can achieve a more targeted and effective application security strategy.
Tiers: measuring maturity in NIST CSF 2.0
Another key aspect of CSF 2.0 is its tier system, which provides a practical way to measure and improve cybersecurity maturity. The four tiers represent increasing levels of sophistication:
- Tier 1 (Partial): Practices are reactive and inconsistent.
- Tier 2 (Risk-Informed): Some processes are guided by risk assessments.
- Tier 3 (Repeatable): Policies and procedures are formalized and repeatable.
- Tier 4 (Adaptive): Processes are continuously evolving and proactive.
Organizations can assess their current tier for each CSF 2.0 outcome, assigning numerical values to these tiers to calculate a maturity score. By averaging these scores, they gain a clear view of their overall cybersecurity posture. While NIST doesn’t explicitly endorse this scoring method, Codific’s SAMMY tool simplifies the process. It offers built-in support and a practical methodology for those looking to understand how to implement NIST CSF 2.0 effectively.
Scopes: Tailoring NIST CSF 2.0 to your needs
Organizations are rarely homogeneous. Different business units, teams, or products often face unique cybersecurity challenges. That’s where the concept of scopes comes into play. Scopes allow organizations to focus assessments on specific areas, such as individual teams, product lines, or business units.
This flexibility enables organizations to allocate resources where they’re needed most. For example, one business unit might focus on protecting critical assets, while another prioritizes operational resilience. Additionally, tracking scores by scope makes it easier to monitor progress across the organization and address disparities. Obviously, for smaller organizations you could use a single scope for the CSF 2.0 assessment.
Profiles: Aligning cybersecurity with goals
Profiles are another powerful feature of CSF 2.0. They allow organizations to align their cybersecurity practices with specific goals or risks. There are several types of profiles, including:
- Current Profile: Captures the organization’s current state of cybersecurity.
- Target Profile: Defines desired outcomes based on strategic goals, threats and risks.
- Community Profiles: Address specific threats, such as anti-malware or anti-DDoS efforts.
By using profiles, organizations can plan targeted improvements. They also provide a clear path from the current state to the desired state, making cybersecurity investments more strategic.
Balancing flexibility and consistency
CSF 2.0 is intentionally descriptive, providing guidance that organizations can adapt to their needs. While it includes examples and mappings to NIST 800-53, these are neither exhaustive nor mandatory. This flexibility is both a strength and a challenge. It allows customization but can lead to inconsistencies in implementation.
In contrast, frameworks like OWASP SAMM offer prescriptive scoring methods to ensure uniformity. Fortunately, Codific’s SAMMY tool bridges this gap by integrating CSF 2.0 with NIST 800-53. This combination provides a structured yet flexible approach, ensuring consistent and measurable progress.
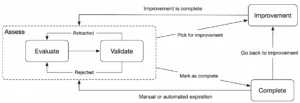
How to implement NIST CSF 2.0 using SAMMY
To implement NIST CSF 2.0 effectively using the SAMMY tool, start by defining your scope. For smaller organizations, the scope might encompass the entire company, while larger organizations might focus on a specific business unit. Next, use SAMMY to create an assessment that evaluates how well your current implementation aligns with CSF 2.0 outcomes. Based on the results and your cybersecurity risks, develop an improvement plan tailored to address identified gaps. Implement this plan, and then use SAMMY again to measure and demonstrate your progress through clear metrics. As the saying goes, “If you can’t measure it, you can’t improve it.” SAMMY is your essential measurement tool for mastering NIST CSF 2.0.
Conclusion: simplify cybersecurity with CSF 2.0 and SAMMY
The NIST CSF 2.0 framework is an invaluable resource for managing cybersecurity risks and aligning practices with organizational goals. Its functions, tiers, scopes, and profiles offer a comprehensive approach to building resilience. Its effective implementation requires people, processes and tools. This is where Codific’s SAMMY tool comes in. With support for CSF 2.0, NIST 800-53, and other standards, SAMMY makes it easier to measure, monitor, and improve your cybersecurity posture. Best of all, it’s available in a free version, so you can get started right away. Take the first step toward a stronger cybersecurity strategy today!
Official resources and further reading
- NIST Cybersecurity Framework
- NIST Secure Software Development Framework
- OWASP SAMM
- NIST 800-53
- A comparison between NIST CSF 2.0 and OWASP SAMM



