Updated: 30 September, 2025
22 November, 2024
What is FISMA and why is it important?
The Federal Information Security Modernization Act (FISMA) is a U.S. federal legislation that ensures federal agencies and contractors take a systematic approach to securing government data. Compliance with FISMA is essential for protecting sensitive information and reducing risks in federal systems. Unlike European frameworks like CRA, NIS2, and DORA, which can sometimes feel vague or complex, FISMA provides clear, actionable guidelines, making it both practical and effective.
Listen to the summary of this article on The AppSec Management Podcast:
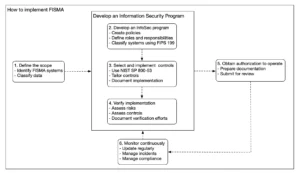
How to implement FISMA in a nutshell
- Understand and define the scope.
- Develop an information security program
- Create a security policy that aligns with NIST guidelines outlining the organization’s commitment to security federal information systems.
- Define roles and responsibilities
- Use FIPS 199 to categorize your information security system to determine the security impact level (Low, Medium, High).
- Select and implement security controls from NIST SP 800-53.
- Verify you have implemented the controls correctly. This step includes an assessment of risks and control implementation.
- Obtain approval for the system to operate.
- Regularly monitor and update controls to address emerging risks and maintain compliance.
In the remainder of this blog, I will first focus on the FISMA key elements. Then, I will provide a high level description and the steps to implement FISMA successfully.
Key elements to FISMA
The Federal Information Security Modernization Act (FISMA) establishes requirements to secure federal information systems. It ensures federal agencies, contractors, and other organizations handling federal data follow stringent cybersecurity practices. Below, we break down the key elements of FISMA into simple, actionable insights.
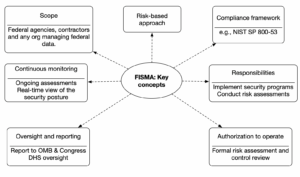
Scope of FISMA
FISMA applies to federal agencies, their contractors, and any organizations managing federal data. It covers all information systems used or operated by these entities on behalf of the federal government. This broad scope ensures that both internally operated and outsourced systems are held to the same security standards, safeguarding sensitive federal information from unauthorized access or disruption.
Risk-based approach
FISMA requires agencies to adopt a risk-based approach to information security. This means focusing on identifying, assessing, and managing risks to federal data. Agencies prioritize security measures based on the potential impact on confidentiality, integrity, and availability of their information systems. This approach ensures resources are allocated to mitigate the most critical risks first.
Compliance framework
FISMA mandates that agencies follow cybersecurity standards set by the National Institute of Standards and Technology (NIST). The most widely used standard is NIST Special Publication (SP) 800-53, which outlines security and privacy controls for federal information systems. These guidelines provide a clear framework for implementing effective security measures and achieving compliance.
Responsibilities
Federal agencies must create, document, and implement agency-wide security programs. These programs should outline how risks are identified, managed, and mitigated. Agencies are also required to conduct periodic risk assessments and perform annual security reviews and audits. These actions ensure compliance with FISMA and help maintain a strong security posture over time.
Authorization to operate
Under FISMA, every federal information system must receive an Authorization to Operate (ATO). This involves a formal review of the system’s risk assessments and security controls. The ATO process ensures that systems meet all required security standards before they are approved for use. Without an ATO, a system cannot legally operate.
Oversight and reporting
FISMA emphasizes the importance of oversight and accountability. Agencies must report their compliance efforts to the Office of Management and Budget (OMB) and Congress. The Department of Homeland Security (DHS) supports FISMA implementation and oversees federal security programs. This reporting process ensures transparency and helps maintain consistent security practices across agencies.
Continuous monitoring
Continuous monitoring is a cornerstone of FISMA compliance. Agencies must implement ongoing assessments of their security controls and systems. This helps them quickly identify and respond to emerging threats or vulnerabilities. By maintaining a real-time view of their security posture, agencies can ensure their systems remain protected against evolving risks.
Implementing FISMA in a nutshell
Implementing FISMA requires a structured and systematic approach to securing federal information systems. By following the standards established by the National Institute of Standards and Technology (NIST), organizations can achieve compliance and enhance their cybersecurity posture. Here is a step-by-step guide to implementing FISMA effectively.

Understand and set the scope
Identify information systems
Begin by determining which systems fall under FISMA’s jurisdiction. This includes systems owned by federal agencies or operated by contractors on their behalf. Identifying the relevant systems is the foundation for all subsequent steps.
Classify information
Categorize the data handled by each system based on its confidentiality, integrity, and availability. Use NIST SP 800-60 to define these impact levels as low, moderate, or high. Proper classification ensures appropriate controls are applied.
Develop an information security program
Create a security policy
Create an agency-wide information security policy that aligns with NIST guidelines. This policy should outline the organization’s commitment to securing federal information systems.
Define roles and responsibilities
Assign key roles, such as a Chief Information Security Officer (CISO), to oversee the FISMA implementation process. Clearly define responsibilities for managing and monitoring compliance efforts.
Use FIPS 199 to categorize information systems
Use the Federal Information Processing Standard (FIPS) 199 to determine the security categorization of your systems. Assign an impact level—low, moderate, or high—for each system based on the potential consequences of a security breach. These impact levels guide the selection and implementation of appropriate security controls.
Address data sensitivity and criticality
Beyond categorization, evaluate the sensitivity and criticality of the data processed by the system. Systems handling sensitive information, such as Personally Identifiable Information (PII) or classified data, often require stricter controls and additional scrutiny.
Implement security controls
Leverage NIST SP 800-53
Select baseline security controls from NIST SP 800-53, which provides comprehensive guidelines on security and privacy measures. The controls cover areas like access control, encryption, logging, monitoring, and incident response. Tailor these controls based on the system’s impact level and unique requirements.
Customize controls
Tailor the selected controls to address specific risks identified during the risk assessment. For example, a system categorized as “high impact” may require advanced monitoring tools and multi-factor authentication.
Document the implementation
System security plan
The System Security Plan (SSP) is a comprehensive document detailing how the system implements, manages, and monitors security controls. It includes:
- A description of the system and its environment.
- Assigned roles and responsibilities for security management.
- A summary of implemented control as well as details of how each control is implemented to meet the system’s specific security needs.
Supporting documentation
Include references to related documents such as the Risk Assessment Report (see next section), control assessment results, and operational policies. Ensure the SSP aligns with NIST SP 800-18 guidelines for documentation.
Periodic Updates
Keep the SSP updated to reflect changes in the system, such as newly added components, updated controls, or findings from continuous monitoring.
Verify the correct implementation
Conduct risk assessments
Conduct a thorough assessment of potential threats and vulnerabilities to your system. Consider factors like potential attackers, system architecture weaknesses, and external dependencies. Document the findings in a Risk Assessment Report (RAR). This report provides a clear picture of risks and guides decisions on control implementation and prioritization. Finally, make sure to incorporate risk assessment findings into the system’s continuous monitoring process to address risks proactively and update controls as needed.
Perform a controls assessment
Develop a Security Assessment Plan (SAP) that outlines the scope, objectives, and methodology for evaluating controls. Select an independent assessor or assessment team with expertise in federal information security standards. Evaluate the implementation and effectiveness of each control. Assessors may use a combination of automated tools, manual testing, and interviews with system administrators and stakeholders.
Security assessment report
Document the findings in a Security Assessment Report (SAR), which identifies the strengths, weaknesses, and deficiencies of the system’s security posture. Use this report to inform remediation efforts and updates to the SSP.
Plan of Action and Milestones (POA&Ms)
Develop a Plan of Action and Milestones (POA&M) to address security weaknesses identified in the SAR. Each item in the POA&M should include:
- A description of the deficiency.
- Planned corrective actions.
- Assigned responsibilities.
- Target completion dates.
Regularly review and update the POA&M to track progress on remediation efforts. This document demonstrates the organization’s commitment to addressing risks and achieving compliance.
Obtain authorization to operate (ATO)
Security authorization package
Prepare a Security Authorization Package that includes:
- The SSP, detailing the implemented controls and system security.
- The RAR, highlighting risks and their management.
- The SAP and SAR, documenting the assessment process and findings.
- The POA&M, outlining planned remediation steps.
Review and approval
Submit the package to the Authorizing Official (AO) for review. The AO evaluates the system’s risk posture and compliance with FISMA requirements. An Authorization to Operate (ATO) is granted if the system meets the necessary security standards.
Continuous Monitoring
Implement Monitoring Processes
Establish continuous monitoring processes to track the effectiveness of implemented controls. This includes automated tools for vulnerability scanning, configuration management, and log analysis.
Regular Updates
Use monitoring results to update risk assessments, SSPs, and other documentation. Continuous monitoring ensures the system remains secure against emerging threats.
Proactive Threat Management
Incorporate threat intelligence and incident response metrics to improve the system’s ability to detect and respond to potential attacks.
Incident Response
Establish an Incident Response Plan
Develop a formal incident response plan that includes procedures for detecting, reporting, and mitigating security incidents. Clearly define roles, responsibilities, and escalation processes.
Reporting and Recovery
Ensure incidents are reported promptly to relevant stakeholders, including the agency’s security team, DHS, or other oversight bodies. Focus on minimizing the impact and recovering normal operations as quickly as possible. Finally, an essential part of the incident response process is to conduct reviews after each incident to identify lessons learned and improve the overall response processes.
Report Compliance
Annual Reports
Submit annual compliance reports to the Office of Management and Budget (OMB). These reports detail the agency’s security posture, risk management efforts, and any identified deficiencies.
Audit Readiness
Prepare for internal and external audits, such as those conducted by the Government Accountability Office (GAO) or Department of Homeland Security (DHS). Regular internal audits ensure the organization remains in compliance and can address issues proactively.
Self-assessment vs. third-party assessment
Finally, one of the coolest (though you might disagree) aspects of FISMA is choosing whether to conduct a self-assessment or hire a reputable third party. While both are valid, accuracy and integrity are crucial. Intentionally lying to the federal government is obviously never a good idea. However misrepresentation can also lead to severe penalties under the False Claims Act.
| Aspect | Self-assessment | Third-party assessment |
|---|---|---|
| Cost | Lower as you will be using internal resources. | Higher as you will require external expertise. |
| Expertise | Your internal team may lack deep knowledge of FISMA and NIST standards. | You are bringing in specialized compliance expertise. |
| Objectivity | Potential internal bias in reporting. | Independent and unbiased. |
| Credibility | Less trusted for high-risk systems or contracts. | Preferred for critical or sensitive systems. |
| Risk | Errors or dishonesty can lead to legal consequences. | More reliable and defensible for audits. |
In general, I would recommend a self-assessment for low-risk systems in case you have strong internal expertise. For high-stakes contracts or critical systems, third-party assessments (e.g., Conquest Security) offer credibility and thoroughness, minimizing compliance risks.
Conclusion
FISMA offers a systematic approach to securing federal information systems, ensuring both compliance and protection against evolving threats. By following the steps outlined in FIPS 199 and NIST SP 800-53, organizations can implement effective security measures tailored to their needs.
Key takeaways:
- Categorize systems using FIPS 199 to determine their sensitivity.
- Apply and implement controls from NIST SP 800-53.
- Verify control implementation and continuously monitor and assess systems to maintain compliance.
FISMA compliance is more than a regulatory requirement; it’s a pathway to building a secure and resilient information security program. By leveraging its clear guidance and complementary standards, organizations can ensure their systems remain secure and reliable.
Essential sources and references
The references are ordered by their relevance and importance for FISMA.
- Conquest Security: Your Trusted FISMA Implementation Partner.
- Federal Information Security Modernization Act.
- FIPS 199: Standards for Security Categorization of Federal Information and Information Systems.
- FIPS 200: Minimum Security Requirements for Federal Information and Information Systems.
- NIST Special Publication 800-53 Rev. 5: Security and Privacy Controls for Information Systems and Organizations.
- NIST Special Publication 800-137: Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations.
- NIST Special Publication 800-34: Contingency Planning Guide for Federal Information Systems.



