Updated: 3 November, 2025
31 October, 2025
Most organizations conduct security assessments, yet few turn them into meaningful improvement. Traditional cybersecurity gap analyses often stop at identifying weaknesses without showing how to close them or measure progress. As frameworks multiply, teams end up repeating the same work under different names.
A modern cybersecurity gap analysis changes that. By aligning frameworks, defining target maturity, and automating the process, organizations can transform isolated audits into a continuous improvement cycle. With platforms like SAMMY, mapping between frameworks and tracking progress over time becomes effortless, revealing one clear picture of security maturity and compliance readiness.
Key Takeaways
- Modern cybersecurity gap analysis goes beyond identifying weaknesses; it aligns multiple frameworks, defines clear maturity targets, and uses automation to turn assessments into continuous improvement cycles.
- Framework mapping eliminates duplication by linking related controls across models like OWASP SAMM, ISO/IEC 27001, NIST CSF, BSIMM, and CyFun, creating a unified view of progress.
- Measuring maturity rather than just compliance provides a clearer picture of capability, showing how deeply security practices are integrated into everyday work.
- SAMMY enables this process by automating framework mappings, defining target postures, generating gap reports, and managing improvement tasks with built-in tracking and Jira integration.
- Continuous reassessment, supported by expiry dates and stored assessment history in SAMMY, ensures organizations stay aligned with evolving risks while steadily strengthening their cybersecurity resilience.
What Is a Cybersecurity Gap Analysis?
A cybersecurity gap analysis is a structured process that compares your current security practices with a defined target state. That target may be a regulatory standard, a maturity model, or an internal policy. The goal is to find where your organization’s controls, processes, or capabilities fall short and to create a clear plan for improvement.
Unlike a risk assessment, which estimates the likelihood and impact of potential threats, a gap analysis looks inward. It asks how well your existing security measures align with what is expected or required. In other words, a risk assessment shows where danger comes from, while a gap analysis shows where protection is missing. Together, they form the foundation of a strong security program.
Many organizations benchmark their results against recognized frameworks such as the NIST Cybersecurity Framework, ISO/IEC 27001, OWASP SAMM, or BSIMM. Each of these frameworks offers a different perspective. NIST focuses on operational resilience. ISO 27001 defines governance and management controls. SAMM measures software security maturity, and CyFun provides a proportional baseline for national and sector-level assurance.
New regulations such as the EU Cyber Resilience Act (CRA) are also expanding the scope of cybersecurity expectations. The CRA emphasizes secure design, continuous risk management, and post-market monitoring for digital products. Conducting a cybersecurity gap analysis helps organizations evaluate how their current controls align with these emerging requirements and identify where additional assurance is needed.
The outcome is much more than a checklist of missing actions. A well-run cybersecurity gap analysis gives a clear picture of where you stand today versus where you need to be. It highlights strengths and weaknesses, identifies improvement priorities, and produces a roadmap for measurable progress. When performed regularly, it becomes a key part of a continuous improvement cycle that keeps security, compliance, and business goals aligned.
Why Framework Mappings Matter for Cybersecurity Gap Analysis
Most organizations rely on more than one cybersecurity framework. A company might measure software assurance with OWASP SAMM or BSIMM, manage compliance through ISO/IEC 27001, and benchmark resilience using the NIST Cybersecurity Framework. Each of these frameworks defines its own set of concepts such as controls, outcomes, or requirements that often overlap but use different terminology. This overlap makes it hard to see how one activity contributes to multiple standards.
New regulations like the EU Cyber Resilience Act (CRA) add another layer of complexity. The CRA extends security and resilience obligations across the entire product lifecycle, from design to maintenance. As organizations prepare to demonstrate compliance, understanding how existing frameworks already address CRA requirements becomes critical.
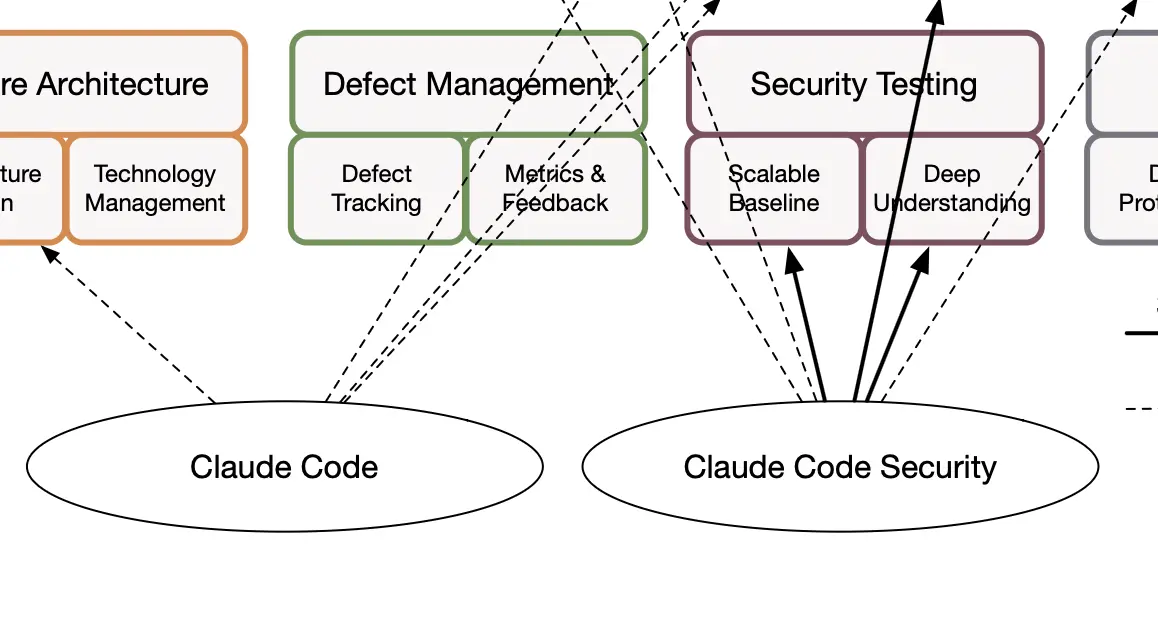
Framework mapping bridges that gap. According to NIST IR 8477, mapping defines clear relationships between the concepts in different frameworks. It can show when one control supports, is equivalent to, or is a subset of another. This structure turns an abstract comparison into a transparent, evidence-based connection. For example, a control in SAMM’s Security Testing practice might support the NIST CSF’s Detect function or align with ISO 27001’s requirements for vulnerability management.
When applied to gap analysis, mappings make results far more actionable. They let assessors reuse findings across frameworks, reduce duplicated work, and understand which gaps affect multiple compliance goals at once. A single improvement can strengthen several frameworks simultaneously.
NIST’s approach also encourages documenting the purpose and assumptions behind each mapping. Doing so ensures consistency and helps future users interpret relationships accurately. For organizations, this means better interoperability, clearer communication, and faster progress from assessment to improvement.
By adopting structured mappings, a gap analysis evolves from a framework-by-framework review into an integrated view of the organization’s maturity. It becomes possible to connect every improvement effort directly to multiple compliance and governance objectives, saving time, reducing confusion, and increasing trust in results.
Measuring Maturity, Not Just Compliance
Traditional security gap analyses often focus on compliance checklists. They show whether specific controls exist but not how effective or consistent those controls are in practice. A maturity-based approach looks deeper. It evaluates how well security activities are defined, implemented, and improved over time. This distinction matters because real progress in cybersecurity depends on capability, not only on coverage.
Frameworks such as OWASP SAMM and BSIMM define clear maturity levels that describe how security practices evolve. SAMM measures maturity across three stages: establishing processes, integrating them into the development lifecycle, and governing them through metrics and continuous improvement. BSIMM follows a similar logic by tracking observable activities across multiple practice areas. These models help organizations move beyond binary compliance and measure how deeply security is embedded in daily work.
Other frameworks apply the same idea on a broader scale. The NIST Cybersecurity Framework organizes activities into Identify, Protect, Detect, Respond, and Recover, which together reflect increasing organizational maturity. The CyFun framework from the Centre for Cybersecurity Belgium builds on this principle with assurance levels such as Basic, Important, and Essential, each representing a higher degree of implementation and resilience.
Research shows that maturity assessments reveal valuable insight that compliance audits alone cannot provide. In one study, involving multiple stakeholders in maturity evaluations uncovered significant perception gaps between teams, proving that security cannot be judged from a single viewpoint. Another study found that raising maturity levels led to measurable benefits such as shorter recovery times and more reliable release cycles.
Together, these findings show that maturity-based assessments provide richer and more reliable insights than compliance checks alone. They make progress measurable, highlight inconsistencies between perception and practice, and connect technical improvement with strategic goals. When organizations track maturity as part of every gap analysis, they build a living picture of their security posture that evolves with time and evidence.
Multi-Stakeholder Perspective
A cybersecurity gap analysis is only as reliable as the perspectives it includes. When assessments rely on a single viewpoint, they often miss how security is experienced in different parts of the organization. Developers, operations teams, security specialists, and business leaders all interact with security controls in distinct ways. Each role understands the same framework through a different lens, which can lead to inconsistent scoring and misaligned priorities.
Research shows that involving multiple stakeholders produces a more accurate and useful picture of security maturity. In one study, participants completed an OWASP SAMM assessment individually, then compared results in group sessions. The findings revealed that different roles consistently rated the same practices at different maturity levels. Developers tended to score technical activities higher, while management rated governance and strategy areas more favorably. The exercise highlighted communication gaps that directly affected how resources were allocated and how success was measured.
Including diverse perspectives also improves the credibility of assessment results. When stakeholders collaborate, they build shared ownership of outcomes and agree on what progress looks like. This makes remediation plans easier to implement and ensures that improvements address both technical and organizational challenges.
A modern gap assessment should therefore be a cross-functional exercise rather than a security-led audit. Collecting feedback from multiple roles, discussing differences openly, and recording levels of confidence in each response transforms the process from a static evaluation into an informed conversation about how security actually works in practice. This foundation makes it possible to run assessments that are both repeatable and trustworthy, setting the stage for a consistent, step-by-step approach to improvement.
How to Do a Cybersecurity Gap Analysis
A cybersecurity gap analysis follows a structured process. It combines evidence, collaboration, and framework alignment to turn complex evaluations into clear, actionable results. The steps below outline a practical approach that any organization can adapt, whether it is starting from scratch or refining an existing security program.
- Define scope and objectives
Start by deciding which systems, teams, and frameworks the analysis will cover. The scope might include the full organization or focus on specific domains such as software development or incident response. Setting clear objectives helps determine what “good” looks like and prevents the assessment from becoming a checklist exercise. - Select and map frameworks for alignment
Choose one or more frameworks that reflect your security and compliance goals. Common examples include OWASP SAMM for software security, ISO/IEC 27001 for information security management, and the NIST Cybersecurity Framework for operational resilience. Because these frameworks often overlap, mapping them helps reveal shared controls and reduce duplicated work.
Modern platforms such as SAMMY make this step far easier by automatically mapping assessment data across frameworks. A single SAMM or BSIMM assessment can now be translated into multiple models, including NIST SSDF or and CyFun. This automation eliminates repetitive tasks, ensures consistent scoring, and allows teams to see how one improvement strengthens several frameworks at once. Learn more about this in this video:
- Define your target posture
Next, determine the desired maturity level or target posture you aim to reach. Frameworks like SAMM and CyFun include predefined levels that describe progressive implementation and governance stages. Others, such as ISO/IEC 27001, allow you to set your own objectives based on risk tolerance, industry standards, or business priorities. Defining a clear target posture provides a reference point for measuring progress and understanding the size of the gap.
In SAMMY, you can define this target posture directly within the platform. Once it is set, SAMMY automatically compares assessment results to your defined objectives and generates a complete gap analysis report in Excel. This makes it easy to visualize where your organization already meets expectations and where improvement is still required across frameworks.
- Gather data and involve stakeholders
Collect information from policies, processes, and existing audits, but also from the people who apply them daily. Interviews, surveys, and workshops reveal how controls actually work in practice. Including multiple roles, as research shows, creates a balanced and credible picture of maturity. - Identify gaps and assess maturity
Compare current practices against the selected frameworks. Document which controls exist, which are missing, and which are partially implemented. Use maturity scales to show progress rather than simple compliance. Look for low-confidence answers or areas where different roles disagree, since these often point to unclear ownership or communication gaps. - Prioritize and plan improvements
Translate findings into a roadmap. High-impact gaps that affect several frameworks should come first. Define short-term actions for quick wins and long-term initiatives for structural improvement. Use measurable goals and assign owners for each activity. When mappings and target tracking are automated, progress can be monitored once and reflected everywhere, saving significant time and ensuring consistency.
Running a cybersecurity gap analysis in this structured way turns the process from an audit into an engine for continuous improvement. When frameworks are mapped intelligently, targets are defined clearly, and automation supports the process, each assessment builds lasting value and moves the organization closer to resilience.
How to Create Actionable Roadmaps Based on Gaps
The purpose of a cybersecurity gap analysis is not just to identify weaknesses but to guide improvement. A list of missing controls or low maturity scores has little value until it becomes a structured plan for change. Turning findings into an actionable roadmap ensures that every insight leads to measurable progress.
- Prioritize what matters most
Start by ranking gaps based on impact and dependency. Focus first on weaknesses that expose critical assets or affect multiple frameworks at once. Framework mappings help identify these shared areas, showing where one control supports several objectives. By closing a single high-impact gap, you can often improve your standing across multiple standards simultaneously. - Define clear improvement paths
Each identified gap should lead to a specific next step. Short-term actions might include updating a security policy, enforcing multi-factor authentication, or refining training programs. Long-term actions often involve deeper changes such as embedding security into development workflows or establishing stronger governance structures. Combining quick wins with long-term goals helps maintain momentum while building sustainable capability.
SAMMY can be used to define these improvement paths directly within the platform. For each element of every framework, you can create detailed improvement plans, attach supporting images, videos, and documents, and explain the rationale behind each step. This ensures that improvement activities are well understood, documented, and easy to communicate across teams.
- Assign ownership and track progress
Every improvement should have a responsible owner, a timeline, and measurable outcomes. Metrics can include maturity level, control implementation rate, or incident frequency. Regular progress reviews keep teams accountable and highlight areas where priorities need to shift as new risks emerge.
SAMMY allows you to track progress over time and assign improvement tasks either within the platform itself or through integration with Jira, giving teams a seamless way to manage remediation work.
- Integrate the roadmap into your improvement cycle
A roadmap should not be a one-time document. Treat it as a living plan that evolves with every reassessment. Each completed action becomes new evidence of maturity, feeding into the next cycle of improvement. This approach turns compliance work into a continuous learning process and builds lasting resilience over time.
When organizations act on gaps through structured, mapped, and measurable roadmaps, they turn assessments into progress engines. Framework alignment and automation remove friction, letting teams focus on what truly matters: building secure systems and maintaining confidence in their security posture.
Continuous Improvement as the Goal
A cybersecurity gap analysis should never be a one-time exercise. Security threats, business priorities, and frameworks all evolve, which means yesterday’s results can quickly lose relevance. The real objective is to turn assessments into an ongoing cycle of measurement, action, and review.
Frameworks such as OWASP SAMM, ISO/IEC 27001, and the NIST Cybersecurity Framework all promote this principle through continuous improvement models. Each recommends regular reassessment to verify that progress is real and that implemented controls remain effective over time. Periodic evaluations also help detect when maturity levels plateau or when new risks demand attention.
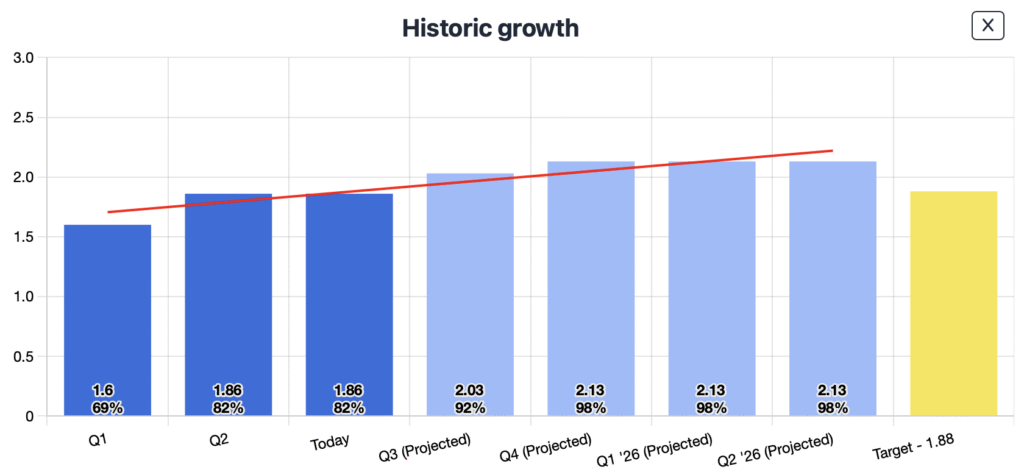
To make this process manageable, organizations should treat gap analysis as part of their broader security management routine. Schedule reassessments at regular intervals, ideally every six to twelve months, and compare current maturity scores with previous results. Tracking trends provides a clear view of whether improvement efforts are paying off and where additional focus is needed.
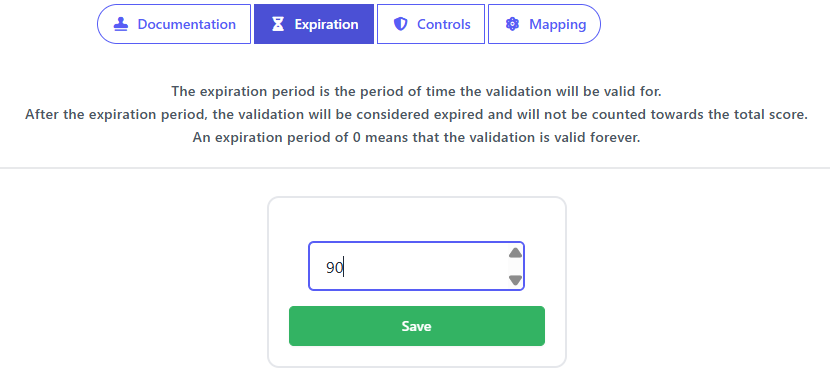
SAMMY supports this cycle by storing assessment history, comparing past and current results, and showing progress at both framework and practice levels. It also allows you to set expiry dates for assessments to ensure they are reviewed and updated at the right time. Because SAMMY includes built-in framework mappings, reassessing one framework makes it easy to revisit related assessments and maintain alignment across all models.
By embracing continuous improvement, security programs stay aligned with change instead of reacting to it. Each iteration brings better visibility, more mature processes, and stronger collaboration. Over time, this steady rhythm of assessment and refinement becomes the foundation of lasting cybersecurity resilience.
Start Simplifying Security Gap Analysis with Confidence
A security gap analysis should be more than a checklist. It’s a structured way to measure maturity, align frameworks, and drive real improvement. That’s where SAMMY comes in.
With SAMMY, you can:
-
Map assessments instantly across multiple frameworks like SAMM, NIST, ISO 27001, and CyFun
-
Define your target posture and generate full gap analysis reports in Excel
-
Identify gaps and create detailed improvement plans with supporting files and context
-
Track progress over time, assign tasks, and ensure assessments are revisited when due
Ready to align your frameworks and turn assessments into measurable progress?
Click below to start your first gap analysis for free.
Conclusion
A cybersecurity gap analysis is far more than a compliance checkpoint. When frameworks are mapped intelligently, maturity is measured consistently, and results are shared across teams, the process becomes a driver of continuous improvement. Tools like SAMMY make this easier by connecting frameworks, automating reports, and tracking progress over time.
The result is a security program that learns and adapts with every cycle. Instead of repeating isolated assessments, organizations gain an evolving picture of their maturity, their risks, and the actions that matter most. This bridge between strategy and practice is what turns a simple gap analysis into a sustainable foundation for long-term cybersecurity resilience.