Updated: 30 September, 2025
26 April, 2023
Software Backups
Reasons to back up your software seem pretty obvious, however as it can be a tedious task, it is something that takes the backseat.
If you rely on digital data, whether you are an organisation or an individual, it is essential you understand the types of software backups there are.
Backups are copies of your data that can be used to restore your system in a case of data loss, corruption, or catastrophic events. There are several types of backup, including full backups, incremental backups, and differential backups. More on these below.
Software backups not only protect against data loss, but also help against financial loss, repetitional damage and legal liability, these applying mostly in organisations. Data backups allow for disaster recovery, enabling a business to quickly recover from unexpected events.
Key takeaways:
-
Data backups are crucial for protecting against data loss, corruption, and catastrophic events.
-
Choosing the right backup strategy depends on your specific needs and data usage patterns.
- SAMMY is the tool Codific has developed that helps you build processes to correctly backup your data. SAMMY has a community version that is completely free.
- In the case of a data breach, having a disaster recovery plan in place is essential to minimise the damage.

What to backup?
This blog is related to types of software backups, however, it is important to note it is less common to backup the actual software, but more so, backup the data from the software. Although this does depend on the customisation of a piece of software, if it is highly customised, you may want to backup the software with an image. “System image backup is a backup technique that allows to copy all drives of the computer and the state of its operating system at a given point in time and allows it to recover that computer to this state.”
In today’s cloud-based setup, software often operates within virtual computers known as containers. These containers have images called dockers. If something goes wrong with the original container or if new instances are needed, these docker images can be used to redeploy the container. However, it’s important to note that relying solely on docker images doesn’t replace the need for independent data backups. Data backups directly pull information from databases and can be restored without having to redeploy the docker image. This is particularly common when dealing with ‘off the shelf’ software, where organisations are more likely to back up the data separately. In case of any issues, they can then re-deploy the software using the backed-up data.
If an organisation is unable to backup all the files due to coast, size or accessibility, NIST guide on how to backup files recommends to prioritise file backup based on the business value the files have in the organisation.
How often should you backup your data?
Keep in mind that when choosing how to backup, where, what type and so on, everything depends on the specific risk profile of the application and the data.
Backing up data frequently is crucial for business, but how often should the backup take place? Generally, it should be as often as possible. However, it does depend on the amount of data that is changing throughout an hour, day or week. Hourly backups would be the ideal scenario, but businesses more typically opt for daily backups. (1) This depends extremely on the choice of the business. Some factors to consider when deciding how often a business should backup data are (2):
- How important is the data?
- How often does the data change?
- How sensitive is the information?
- Where should this backup data be saved?
- Who is responsible for this backup?
- When is a safe time to back up this data?
Having a clear understanding and response to all the questions allows a business to properly determine the safest and most suitable option to how often a backup should take place.
There are two elements that are important to consider which are not typically thought of. Firstly, the time of a backup. Overnight is a good time as activity is typically at its lowest, servers are not trying to do other things while being back up. Secondly, there is such a thing as backing up data too often. The more a business backs up their data, the more they are exposing this backup server to the world, and this connection may be hijacked in a ransomware attack.
Where should you keep the software backups?
3-2-1 backup rule is simply a strategy.
3 – you should keep 3 copies of your data. One being the original and two backups.
2 – Keep the files on two different media types, e.g. one on the cloud and another on an external drive, both backups should be encrypted. (3)
Two very common and good examples of backup services are, iCloud and Amazon Web Services. If you wish to keep a backup of your data on the iCloud, ideally, another backup should be kept on Amazon Web Services. Kept in a secure location and not connected to the network ensures there’s no way ransomware can gain access.
1 – store one copy of the data in a separate location.
Testing and monitoring software backups
According to NIST, it’s crucial to employ both manual and automated approaches to test and monitor data backup and recovery. The goal when testing is to verify the integrity of the backup files and assess the efficiency of recovery processes, from this information, organisations can enhance their overall procedures.
Testing involves various parameters such as the time taken to retrieve files from off-site locations (be it cloud or data centres across the internet), the correlation between file retrieval time and sizes, the duration for restoring files to systems, rebuilding systems, and understanding the responsibilities among involved personnel. This process also identifies gaps, both technical and procedural, highlighting areas for improvement.
On the monitoring front, ensuring backup files are created and ensuring files can be successfully recovered and are useable is proactive management. Ensuring that organisations are well-prepared to handle data disruptions and recover swiftly when needed.
What types of software backups are there?
How are you meant to know what software backup suits your organisation’s needs? There are three main types of backup, full, differential and incremental. (4)
Full Backup
The most comprehensive backup is a full backup, which copies all the chosen data. This includes documents, directories, Sass applications, hard drives and more. A complete backup’s best feature is how quickly data can be restored. However, it is also one of the longer ways to backup data as everything is done at once. Full backups on a regular basis require the most storage out of each type. (5)
Full backups are straightforward to manage and restore. Nonetheless, it is recommended to encrypt your backups independent of the type of software backup you choose. If a hacker or unauthorised user accesses your backup, without any encryption, they have access to everything. However, with encryption backups, they can steal the entire backup drive and still be unable to access the data without the key.
Advantages:
- You always have a complete copy of all your data
- Hardest to corrupt/access (granted it is safely stored and encrypted)
Disadvantages:
- Takes time
- Requires the most storage space
- If stolen and unencrypted, the user has access to everything
Incremental Backup
To use the incremental backup method, it is necessary to create a full backup initially. Then, subsequent backups will only contain the data that has changed since the last backup. This approach takes up less storage space and requires less time than differential or full backups. (6)
However, restoring a complete system with incremental backups is the most time-consuming method. The process involves restoring the most recent full backup set, followed by each incremental backup set in sequence. If any of these sets are missing or damaged, a full restoration will not be possible.
Businesses dealing with significant amounts of data can benefit from using incremental backups over full backups alone as they take up less space. With that being said, if there is little tolerance for data inaccessibility before facing business or financial losses, and the recovery time objective is short, it may be more practical to go for differential backups instead.
Advantages:
- Requires less time and storage to backup, once the first backup is done
Disadvantages:
- Takes much more time to recover the data
- If you are missing any data, all the data following cannot be recovered
- Easiest to corrupt
Differential Backup
Differential backups offer a middle ground between conducting frequent full backups and regular incremental backups. They store the changes made since the last full backup, compared to incremental backups, which restore and rely on the data from the previous incremental backup. Differential backups are quicker to restore than an incremental backup, but longer than a full backup. And takes less space than a full backup, but more than incremental backups.
With a differential backup, duplicate files are stored as it backs up all data from the first backup, rather than from the changes in data.
Advantages:
- Requires less time to restore compared to incremental backups
- Takes slightly less space than full backups
Disadvantages:
- Consumes more storage space in comparison to incremental backups
- compared to full backups, restoration is slow and complex
Overview:
| Full Backup | Incremental Backup | Differential Backup | |
|
Backup Speed |
Slowest |
Fastest |
Moderate |
|
Storage Space |
Most |
Least |
Moderate |
| Restoration Speed | Fastest | Slowest |
Moderate |
Source: (7)
What backup type best fits you?
It is important to have a backup strategy that fits your needs. For example, if you are an individual user, you may only need to back up your personal documents and files. In this case, you may want to do a full backup every so often, however, if these documents are files that are likely not to change for a few years/never (e.i. Passport, residence, birth certificate etc.). Then after a full backup, incremental backups or differential backups should be sufficient.
On the other hand, specifically for businesses, the choice made between the types of software backups is based on the needs and preferences of the business. But it is important to consider how much new data is created daily, how confidential is this data, and how long are you able to not have access to this data? If you are not able to go without your data before financial or reputational consequences, incremental backups may be too high risk.
Having a backup strategy is necessary, but it is equally essential to test your backups regularly to ensure they are working correctly. Other than storing backup files in a secure location, it is good practice to encrypt your backups to protect your data from unauthorised access.
Alternatively, you can refer to any of the following NIST publications that describe solutions and implementation guides:
- NIST SP 1800-11, Data Integrity: Recovering from Ransomware and Other Destructive Events
- NIST SP 1800-25, Identifying and Protecting Assets Against Ransomware and Other Destructive Events
- NIST SP 1800-26, Detecting and Responding to Ransomware and Other Destructive Events
What data protection strategy can you use?
When it comes to software security and data protection, OWASP SAMM is Codific’s favourite guide. By leveraging the OWASP Software Assurance Maturity Model, you are able to improve your security posture in all sections of your business.
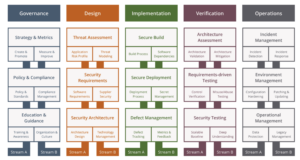
The model is made up of 15 security practices, with 3 maturity levels. It is designed to assist organisations in evaluating, measuring and enhancing their software security position and strategy.
Data Protection is outlined in the Operational Management side of security practices and guides you through questions and criteria in order to properly store and process data. This includes starting from Level 1 which consists of understanding the different types of software backups, types of data, their sensitivity and protection requirements. Continuing to Maturity Level 3 which includes activities such as automating data protection, reducing the reliance on human effort to access, managing data and regular audit compliance and reviews to maintain data integrity.
We believe SAMM is the best security assurance model to follow, so much so that we made a management tool, called SAMMY. We developed the tool to reduce the complexity of SAMM implementation in organisations. SAMMY adopts an approach that starts with small and quick wins, gradually expanding to streamline proactivity of implementation.

Manage your security posture with SAMMY.
After reading this blog, I hope you realise the importance of data protection and management, and specifically what should be done in times of crisis. Which takes us into the final topic of this, Disaster Recovery Plan.
Disaster Recovery Plan
Having a disaster recovery plan in place is essential for businesses for several key reasons. Firstly, it enables the business to minimise downtime during major disruptions such as cyberattacks, data breaches or data loss, natural disasters and more. By having a plan ready, the business can respond swiftly and recover quickly, ensuring continuity of operations.
If you aren’t sure how to get started on this plan, we’ve got your back, read more on SAMMY’s disaster recovery plan model here. This model is based on many of the NIST 800-34 Rev 1 standards. And is an easy step-by-step guide on how to build a disaster recovery plan that is tailored for your business.
The NIST 800-34 Rev 1 standard refers to a security standard published by the National Institute of Standards and Technology, U.S. It provides guidance on developing and implementing effective contingency planning (specify for IT systems within an organisation).
The standard contains many steps, but when looking into businesses processes and recovery we will only be going through the following as they are the most relevant in terms of backup strategy. (Source – PDF linked here)
-
The Maximum Tolerable Downtime (MTD)
This represents the total time that the system owner/authorising official is willing to accept for a process disruptions, taking all impact considerations into account. Determining MTD is the most important as it guides the selection of a suitable recovery methods and determines the level of detail needed when developing recovery procedures.
-
The Recovery Time Objective (RTO)
This defines the maximum duration that a system can remain unavailable before it has an unrecoverable impact on other resources in the business. Determining the RTO helps in selecting the appropriate technologies to support MTD.
-
The Recovery Point Objective (RPO)
The business must decide the Recovery Point Objective (RPO) prior to a disruption as it sets the standard for the amount of data loss the business can tolerate during the recovery process. This decision determines the frequency of backups.
Establishing these three points is of utmost importance in the Disaster Recovery/Business Continuity Plan. They need to be assessed together to understand the business’s ability and limitations when recovering from a crisis.
Conclusion: Choosing the right type of software backup matter
Understanding the types of software backups (full, incremental, and differential) is critical for building a resilient data protection strategy. Whether you’re an individual safeguarding personal files or an organisation managing sensitive business data, selecting the right backup approach ensures you can recover quickly from data loss, corruption, or cyber incidents.
There’s no one-size-fits-all solution. Your ideal backup method depends on how often your data changes, how critical it is, and how fast you need to restore it in case of a disruption. As part of a broader disaster recovery plan, regular testing, secure storage, and encryption are just as essential as choosing the right type of backup.
If you’re unsure where to start, tools like SAMMY can guide you through building a secure, practical backup and recovery process tailored to your needs. Backups are not just a technical task—they are a strategic necessity.
Make backups a priority, and let the right types of software backups protect your business from costly downtime and data loss.




