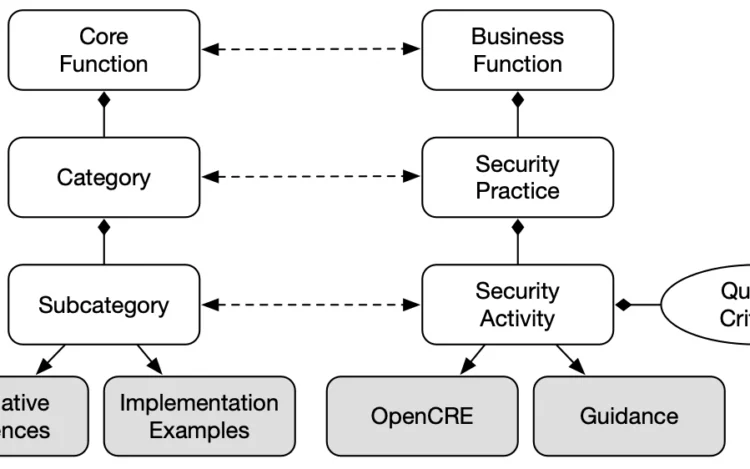
Security programs rarely fail because teams do not care. They fail because the work gets […]
Have you every been hacked? It sucks right? But don’t worry now, let’s make sure[…]
In today’s rapidly evolving digital landscape, ensuring software security is more critical than ever. Recognizing[…]
HIPAA, the Health Insurance Portability and Accountability Act of 1996, is a critical federal law[…]
The U.S. cybersecurity strategy seems to be lightyears ahead of the EU. I strongly believe[…]
Application security is a complex discipline. To make things even harder for us, it is[…]
It this article we explore the essentials of the EU Cyber Resilience Act (CRA), and[…]
Want to get started with SAMM? We have just the thing! Take the free OWASP[…]
How to use OWASP SAMM for effective communication on security? Reporting with OWASP SAMM is[…]
Official resources ISO 27001:2022 ISO 27001:2013 OWASP SAMM CRA NIST SSDF
NIST has finalized the Cybersecurity Framework (CSF) 2.0. CSF 2.0 focuses on understanding, assessing, prioritising,[…]
Is SOC 2 Worth It? In this blogpost we will be discussing SOC 2, what[…]