Updated: 25 September, 2025
6 August, 2025
By embracing the Japanese Kaizen philosophy of continuous incremental improvement, your AppSec program can evolve from a reactive checklist into a dynamic engine of continuous improvement. A quality control program for AppSec. At the OWASP Global AppSec conference, I gave a talk about these principles based on 27 interviews with AppSec program leaders around the world. Kaizen principles applied to AppSec, particularly through OWASP SAMM and DSOMM, can guide organizations to sustained progress.
What is Kaizen?
Kaizen (改善) meaning “good change” is rooted in quality systems like the Plan‑Do‑Check‑Act cycle. Its hallmark? It is all about breaking large challenges into small tasks and creating a consistent schedule with recurrent dedicated timeslots.
There are three specific things that are needed in order to be successful in a Kaizen approach.
1: Breaking big challenges down into small challenges.
2: Being consistent in the time and resource allocation to the steps.
3: Keeping a good overview of the big picture and a state of processes.
Listen to the podcast on building quality control for AppSec
The AppSec conundrum: Finite resources, daunting needs
Most security efforts succumb to some form of paralysis: projects pile up (DevSecOps pipelines, SAST/DAST tools, threat modeling, pentests, AI experiments…), but teams rarely have bandwidth for “all of it.” Kaizen reframes this by shifting the question from “How do we do everything?” to “Which one thing do we improve today?”.
Breaking the challenge down with maturity models
Maturity models such as OWASP SAMM (Software Assurance Maturity Model) and OWASP DSOMM (DevSecOps Maturity Model) have gained a lot of momentum in the last few years. They serve as an inventory of best practices, organized by maturity level.
OWASP SAMM, for example, divides everything we should be doing into 30 activity groups called “streams” and each stream has 3 maturity levels with its respective quality criteria. This gives a finite list of 90 processes to put in place. Nobody really does them all, nor should they, it is the map on which to pick your strategy with everything categorized into attainable steps.
Being consistent in cadence
Small steps are fine, as long as you never stop. It is important to set up a recurring circular process that never ends. Resist the urge to assign more resources in the beginning, it is a marathon not a sprint. Agree upon a cycle length, we have seen anywhere from a month to a year, and the amount of resources allocated. Much like you would do a sprint planning in other lean methodologies like Scrum, the AppSec team will then pick the processes to upgrade in the next cycle.
Keep an overview and avoid the “whack a mole” problem
The ‘whack-a-mole’ problem refers to the common feeling of constantly rushing to put out fires, only to have new ones flare up as soon as the last is resolved. It keeps us busy but not moving forward. In Kaizen there are no “patches” to processes, only fundamental improvement. Here the quality criteria and the scoring system of the maturity models comes in. It tells us what “good” looks like, and from that we can derive what process needs to be put in place to maintain “good”.
Maturity models vs compliance frameworks
In many industries you will be required to have some form of certification in order to do business. Commonly ISO27001 or SOC2. However, these frameworks are not great backbones for your application security program because they are binary. What happens when you comply with them? Is your job done? Of course not! But how do we measure progress then?
So Kaizen is not for everyone, organizations focused solely on achieving product compliance are unlikely to use maturity frameworks. Those who are interested in having a robust application security program with continuous improvements and clear visibility on the state of affairs will.
While this excludes many small tech startups, it encompasses all major industrial players. This observation aligns with the typical user profile of SAMM and implementation tools like SAMMY.
Maturity models deliver strategic process improvement, not just a stamp. While certifications may check boxes, maturity models embed systems and drive measurable progress over time.
How the use of maturity models has evolved into quality control for AppSec
Traditional assessments end with a PDF snapshot already outdated by delivery, yet this is often where many organizations begin. From that point onwards the improvement roadmaps start. Real evolution happens when the streams become self-sustaining cycles, and the assessment model becomes a continuous improvement loop, with living, iterative dashboards powered by your organization’s visualization tools and integrated with workflow management tools, truly embedding the Kaizen process into your organization.
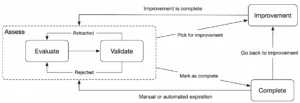
The power of Kaizen in AppSec quality control programs
“Don’t be afraid of little steps, as long as you have the map well laid out… consistent little steps produce pristine quality and security in the long run.”
That’s the Kaizen edge. Clarity of purpose. Clarity of progress. And a steady cadence of success. For AppSec teams, it’s time to trade overwhelm for excellence one micro‑improvement at a time.
Call to Actions:
- Start with a maturity assessment (SAMM/DSOMM).
- Break your roadmap into bite-size cycles.
- Build a live dashboard to track progress.
- Empower teams to own their improvements.
- Follow the free OWASP SAMM fundamentals course provided by OWASP.
Get started building your AppSec quality control program by using SAMMY.
This article originally appeared on the Process Excellence Network.