Updated: 2 September, 2025
27 January, 2025
In today’s rapidly evolving digital landscape, ensuring software security is more critical than ever. Recognizing the growing threat of software vulnerabilities, the National Institute of Standards and Technology (NIST) introduced the Secure Software Development Framework (SSDF) in February 2022, published as NIST Special Publication (SP) 800-218. The framework provides a structured set of practices aimed at reducing vulnerabilities, improving resilience, and aligning software security with organizational goals.
Compliance with NIST SSDF was mandated for U.S. federal agencies through OMB Memorandum M-22-18 in September 2022, requiring them to adopt secure development practices for all software used within government systems. This mandate underscores the increasing importance of secure software development and the need for organizations—both public and private—to align their processes with SSDF recommendations.
This guide explores the key aspects of NIST SSDF, why it matters, and how organizations can implement it effectively using SAMMY to enhance their security posture. Whether you’re a software producer, acquirer, or security professional, this guide will help you navigate the framework and apply its principles to your software development lifecycle.
Key takeaways
- NIST SSDF provides a structured approach to secure software development, reducing vulnerabilities and enhancing resilience.
- Compliance with NIST SSDF is mandatory for U.S. federal agencies under OMB Memorandum M-22-18.
- The framework is adaptable to various development methodologies, including Agile and DevOps.
- Effective implementation involves assessing security posture, setting policies, and continuous monitoring.
- SAMMY simplifies SSDF implementation by offering structured assessments and progress tracking.
- SSDF complements frameworks like OWASP SAMM and BSIMM, supporting both compliance and security maturity.
- Future trends include automation, cloud security, and evolving regulatory alignment.
What is NIST SSDF?
The NIST Secure Software Development Framework (SSDF) is a set of best practices aimed at integrating security into the software development lifecycle (SDLC). It provides a structured, high-level approach that organizations can adopt to improve software security while maintaining flexibility to fit their existing processes. The SSDF helps organizations systematically address security concerns, reduce vulnerabilities, and comply with regulatory requirements, such as those of Memorandum M-22-18, without prescribing specific tools or methodologies. By following SSDF organizations can effectively implement security by design, i.e., security practiced across every stage of the software development lifecycle.
Listen to the summary of this article on The Appsec Management Podcast:
The structure of NIST SSDF
The NIST SSDF framework consists of 42 specific tasks across 19 practices, organized into four categories, each addressing critical aspects of secure software development. These categories provide a comprehensive and adaptable approach to integrating security throughout the software development lifecycle (SDLC).
1. Prepare the Organization (PO)
This category establishes the foundation for secure development by:
- Defining security policies and requirements.
- Assigning responsibilities and training personnel.
- Implementing secure development environments and toolchains.
2. Protect the Software (PS)
This category focuses on securing software components by:
- Controlling access to code and development environments.
- Ensuring the integrity of software components.
- Securely archiving software releases and tracking provenance.
3. Produce Well-Secured Software (PW)
Ensuring security is embedded into development processes through:
- Incorporating security requirements into design and implementation.
- Applying secure coding practices and automated security testing.
- Leveraging tools to identify and mitigate vulnerabilities.
4. Respond to Vulnerabilities (RV)
Handling post-release security concerns by:
- Identifying and remediating vulnerabilities.
- Establishing effective incident response processes.
- Continuously improving security measures based on lessons learned.
By understanding these categories, organizations can systematically implement the SSDF to enhance software security and reduce risk exposure.
Why is NIST SSDF important?
The NIST Secure Software Development Framework (SSDF) plays a crucial role in enhancing software security across industries. As cyber threats continue to grow, organizations must adopt structured and effective security practices to protect their software assets, comply with regulatory requirements, and build trust with stakeholders.
1. Strengthening Software Security
By embedding security practices throughout the software development lifecycle (SDLC), SSDF helps organizations minimize vulnerabilities, ensuring that security is considered from planning to deployment and beyond. This proactive approach reduces the risk of data breaches and other harmful events.
2. Regulatory Compliance
Compliance with security frameworks is becoming increasingly mandatory, particularly for organizations that work with federal agencies. OMB Memorandum M-22-18 requires federal agencies to adopt SSDF practices to enhance software security across their ecosystems. Adopting SSDF helps organizations align with regulations such as:
- Executive Order 14028 and Executive Order 14144, which emphasizes software supply chain security.
- FedRAMP and FISMA, which require secure development processes for cloud and government systems.
3. Improved Risk Management
The SSDF framework allows organizations to identify and mitigate security risks early in the development process. By incorporating structured security measures, organizations can better allocate resources, prioritize security efforts, and ensure ongoing resilience against evolving threats.
4. Enhanced Supply Chain Security
With the increasing reliance on third-party software components, SSDF provides guidelines to ensure that suppliers and vendors follow secure development practices. This strengthens the entire software supply chain, reducing the risk of compromised dependencies.
5. Cost and Efficiency Benefits
Implementing security measures early in the SDLC leads to lower remediation costs and improved efficiency. Addressing security vulnerabilities post-release is significantly more expensive and time-consuming compared to integrating security from the outset.
6. Trust and Market Differentiation
Adhering to a recognized framework like SSDF demonstrates an organization’s commitment to security best practices. This can provide a competitive advantage, instilling confidence in customers, partners, and regulatory bodies.
By adopting NIST SSDF, organizations can build more resilient software systems, streamline compliance efforts, and stay ahead of cybersecurity threats in an ever-evolving digital landscape.
How to Implement NIST SSDF
Implementing NIST SSDF requires a structured, phased approach that aligns with your organization’s existing software development lifecycle (SDLC). By following these steps, organizations can embed security practices effectively while balancing operational efficiency and compliance requirements.
1. Assess Your Current Security Posture
Begin by evaluating your current software development processes against SSDF requirements. Identify gaps in security practices, tools, and policies. Conducting a security maturity assessment will help set a baseline and determine areas for improvement. For this, we highly recommend using SAMMY. With this AppSec Management Tool, you can conduct an in-depth SSDF evaluation, collaborate with your team, and provide documentation to support and validate your assessment. For this a measurement of the maturity of each element in NIST SSDF is provided using CMMI (Capability Maturity Model Integration), which is not a standard approach but something that Codific’s team of experts created.
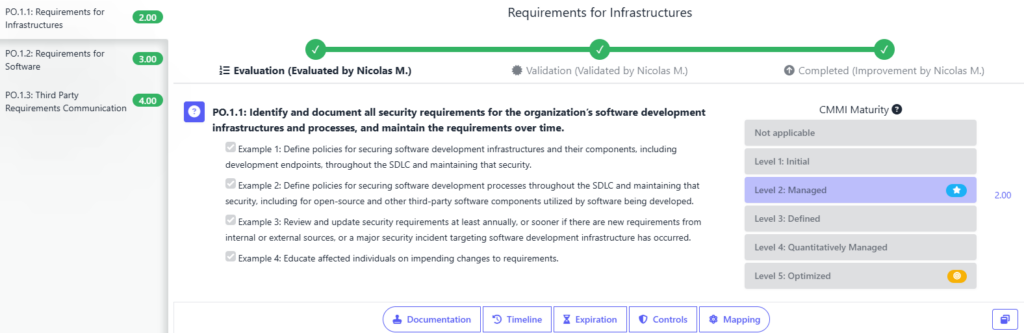
2. Define Security Policies and Objectives
Establish clear security objectives aligned with SSDF’s four practice categories—Prepare the Organization, Protect the Software, Produce Well-Secured Software, and Respond to Vulnerabilities. In SAMMY, you can create an improvement plan that outlines these objectives, assigns responsibilities, and sets deadlines. Moreover, you can provide documentation to evidence these improvements or provide further guidance on how to implement them.
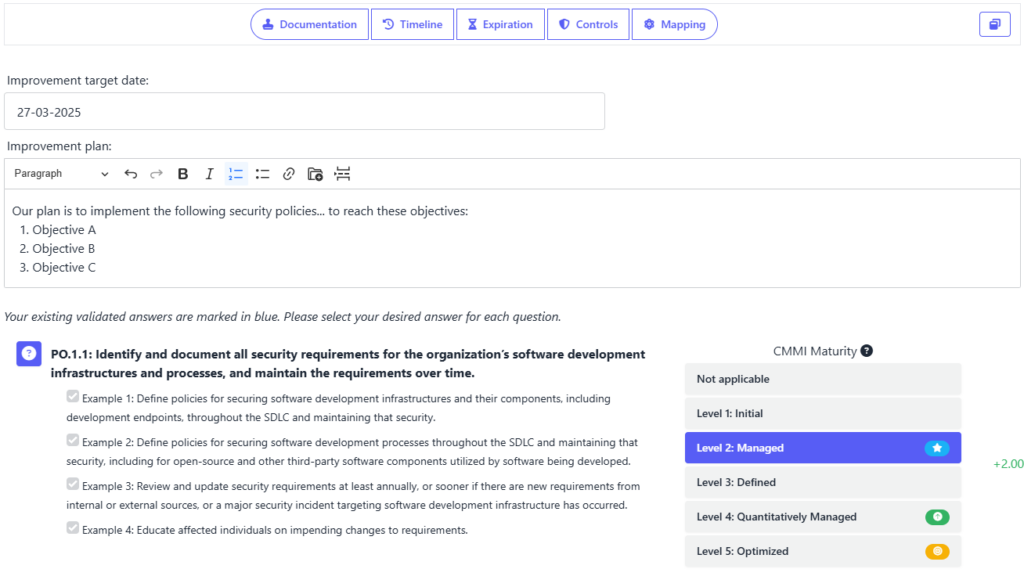
Additionally, SAMMY allows you to define long-term target scopes, helping you set and track future security goals effectively:

It is also possible to add further guidance on how to reach target postures, which will appear if you click on the yellow target mark:

3. Assign Roles and Responsibilities
Clearly define roles for key stakeholders, including developers, security teams, and management. Security champions within teams can help in translating security practices. SAMMY makes it easy to assign responsibilities and track progress, offering seamless integrations with issue tracking tools like Jira for better coordination.
4. Implementing NIST SSDF Improvements
Once the necessary improvements have been identified through assessment and planning, the next step is their systematic implementation. This involves integrating security measures across the software development lifecycle (SDLC), leveraging automation, fostering a security-aware culture, and ensuring collaboration.
Embedding Security into Development
Security improvements should be embedded throughout the SDLC by adopting a “security by design” approach. This includes implementing secure coding practices, conducting threat modeling, and incorporating automated security testing such as static (SAST) and dynamic (DAST) analysis. Establishing these improvements early helps prevent vulnerabilities from escalating and ensures security remains a core component of software development.
Leveraging Automation and Tooling
Automation is crucial to maintaining consistency and efficiency in security processes. Integrating security tools within CI/CD pipelines enables continuous scanning for vulnerabilities, software composition analysis, and build integrity verification. Automation reduces manual effort and provides real-time insights to maintain compliance with SSDF requirements.
Collaboration with Third Parties
Many organizations rely on third-party software and services, making it essential to ensure their compliance with SSDF guidelines. This involves setting contractual agreements that require vendors to follow secure development practices and undergo periodic security assessments to verify compliance.
Proactive Vulnerability Management
Addressing vulnerabilities post-deployment is critical to maintaining security. Organizations should establish structured processes for identifying, tracking, and remediating vulnerabilities, alongside incident response plans to quickly contain and resolve security issues. Lessons learned from incidents should feed into continuous improvement efforts.
By following these steps, organizations can effectively implement SSDF improvements, strengthening their security posture and fostering a culture of continuous security enhancement
5. Measure Success and Report Progress
Define key performance indicators (KPIs) to measure the effectiveness of SSDF implementation. Reporting progress to leadership and stakeholders will ensure continued investment in secure software development efforts. SAMMY simplifies this by generating automated reports that showcase the current security posture, improvement progress, and future targets. These reports offer valuable insights, making it easier to communicate results to stakeholders.
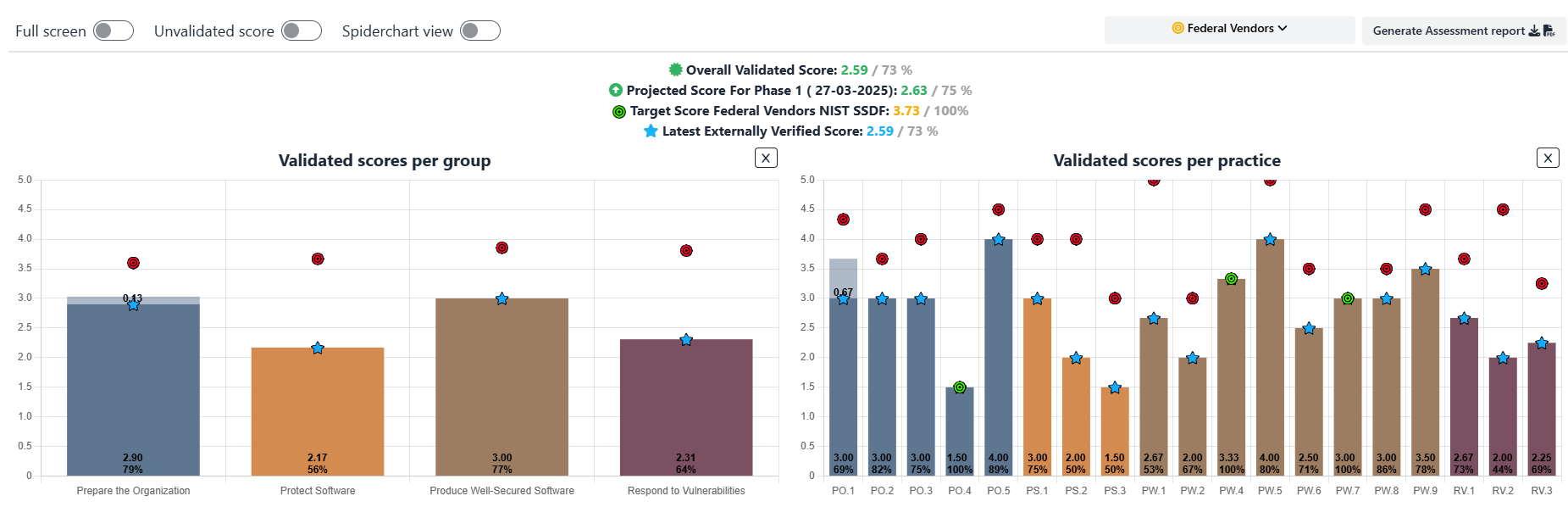
By following these steps and utilizing tools like SAMMY, organizations can integrate NIST SSDF effectively into their software development processes, ensuring continuous security improvements and compliance.
6. Continuously evaluate and refine your security
Once SSDF practices are in place, establish monitoring mechanisms to track security metrics and compliance levels. Regularly review security findings, conduct audits, and refine processes to address emerging threats and evolving regulatory requirements. SAMMY supports continuous monitoring by providing expiration dates for assessments and deadlines for improvement plans, helping organizations stay on track and maintain security efforts over time.
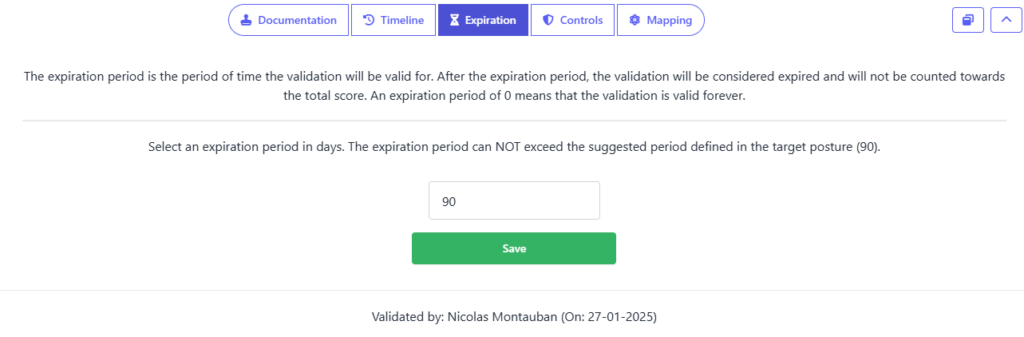
Comparing NIST SSDF with other frameworks: OWASP SAMM and BSIMM
When comparing the NIST Secure Software Development Framework (SSDF) with other established software security frameworks such as OWASP SAMM and BSIMM, it’s essential to understand their distinct approaches and how they can complement each other. While all three frameworks aim to improve software security maturity, they differ in their methodologies, scope, and implementation focus. The table below summarizes the discussion of this section.
| Aspect | NIST SSDF | OWASP SAMM | BSIMM |
| Approach | Example-based framework | Prescriptive framework | Descriptive framework |
| Implementation Focus | High-level security controls | Detailed activities and roadmaps | Real-world data-driven practices |
| Regulatory Alignment | Strong (OMB M-22-18, EO 14028) | None | None |
| Benchmarking capabilities | No measurement capabilities out of the box so no benchmarking capabilities | Great measurement capabilities but not enough data for benchmarking yet | Some measurement capabilities but great benchmarking due to abundant data |
NIST SSDF and OWASP SAMM: A Strategic vs. Practical Approach
NIST SSDF and OWASP SAMM share the goal of enhancing software security but cater to organizations in different ways:
- Scope and Purpose:
NIST SSDF provides a high-level, example-based set of secure development practices applicable to various software development methodologies. It focuses on compliance and risk management, offering a strategic view suitable for regulatory adherence.
In contrast, OWASP SAMM is a prescriptive maturity model that provides detailed, actionable roadmaps for organizations to improve their software security processes incrementally. It is more practical and hands-on, offering organizations a step-by-step approach to security improvement. - Implementation Flexibility:
OWASP SAMM provides detailed implementation guidance with specific activities mapped to different maturity levels, enabling organizations to measure and track their progress. NIST SSDF, on the other hand, offers broad recommendations that organizations can interpret and implement according to their unique needs without predefined maturity levels. - Regulatory Alignment:
NIST SSDF is directly linked to compliance mandates such as OMB M-22-18 and Executive Order 14028, making it essential for organizations dealing with federal agencies. OWASP SAMM is more flexible and can be tailored to different business contexts but lacks the direct regulatory backing that SSDF provides.
Key Takeaway: Organizations seeking a compliance-driven, top-down approach might prefer NIST SSDF, while those looking for a structured maturity model to gradually improve their security practices may benefit more from OWASP SAMM.
We have also written a blog post specifically about how NIST SSDF compares to OWASP SAMM.
NIST SSDF vs. BSIMM: Framework vs. Measurement Model
BSIMM (Building Security In Maturity Model) differs significantly from NIST SSDF in its core purpose and approach:
- Approach and Methodology:
BSIMM is an observational model based on real-world data collected from organizations practicing software security at scale. It provides a measurement tool to benchmark an organization’s security efforts against industry peers. NIST SSDF, in contrast, is a prescriptive framework, offering best practices that organizations should follow to achieve secure software development. - Focus on Data-Driven Insights:
BSIMM provides insights based on how organizations have implemented security practices in the field, helping businesses understand where they stand compared to others. NIST SSDF focuses on establishing a security baseline based on federal guidelines, without offering benchmarking capabilities. - Implementation Philosophy:
BSIMM emphasizes observing and replicating successful security practices in large enterprises, which makes it a valuable tool for organizations looking to align with industry trends. NIST SSDF takes a more generalized, adaptable approach, making it suitable for organizations of all sizes.
Key Takeaway: If an organization is looking for a framework to establish secure development practices, NIST SSDF is an excellent starting point. If the goal is to benchmark existing efforts and learn from industry leaders, BSIMM provides a more data-driven approach.
We have also written a blog post that provides a comprehensive guide about BSIMM expanding on this comparison further.
Choosing the Right Framework for Your Needs
While NIST SSDF, OWASP SAMM, and BSIMM each offer unique advantages, they are not mutually exclusive. Many organizations find value in combining these frameworks to create a holistic software security program.
- Use NIST SSDF as a baseline to establish foundational security practices and comply with regulatory requirements.
- Leverage OWASP SAMM for its maturity model to track and improve security efforts over time.
- Utilize BSIMM for benchmarking security maturity against industry peers and identifying improvement opportunities.
By understanding these frameworks’ strengths and limitations, organizations can take a strategic approach to secure software.
The Future of Secure Software Development with NIST SSDF
NIST SSDF is a stable and comprehensive framework that is unlikely to undergo significant changes in the foreseeable future. Its well-established structure already covers key aspects of secure software development, including cloud-native security and regulatory alignment. While AI and automation continue to advance, these developments primarily enhance tooling rather than necessitate changes to the framework itself.
Organizations should focus on leveraging SSDF effectively by integrating modern tools and methodologies that align with its existing principles. Key areas of evolution include:
1. Improved Tooling and Automation
The integration of AI-powered tools will enhance the implementation of SSDF by:
- Automating security testing processes more efficiently.
- Providing AI-driven insights for vulnerability detection and remediation.
- Enhancing monitoring within CI/CD pipelines without altering SSDF’s core practices.
2. Cloud-Native Security Applications
SSDF already provides a solid foundation for cloud security, but organizations will need to refine their implementations as cloud environments evolve. This involves:
- Strengthening monitoring and access controls to align with SSDF guidelines.
- Ensuring compliance with existing cloud security frameworks such as FedRAMP.
3. Stability in Regulatory Compliance
SSDF aligns well with existing regulatory requirements, and its applicability will remain consistent as new standards emerge. Organizations should focus on:
- Mapping SSDF practices to evolving regulatory requirements without expecting major framework updates.
- Strengthening vendor and third-party compliance using SSDF guidelines.
While technological advancements will continue to evolve, SSDF’s core principles provide a stable, long-term foundation for secure software development. Organizations should focus on enhancing their security programs within the existing framework, leveraging modern tools and best practices to maximize their effectiveness.
Conclusion and next steps
The NIST Secure Software Development Framework (SSDF) provides organizations with a structured, adaptable approach to integrating security into their software development lifecycle. By following SSDF’s practices, businesses can strengthen their security posture, meet regulatory requirements, and reduce vulnerabilities throughout the software supply chain.
Implementing SSDF requires a strategic approach—assessing current security maturity, defining clear policies, and integrating security into each phase of development. Tools like SAMMY can facilitate this process by providing structured assessments, tracking progress, and supporting continuous improvement.
As cybersecurity threats evolve, the future of SSDF will emphasize automation, cloud security, and regulatory compliance. Organizations that proactively embrace these trends will be better equipped to build secure, resilient software systems.
By adopting NIST SSDF today, organizations can ensure they stay ahead of emerging threats while fostering a culture of secure software development.
Official pages of all frameworks and regulations mentioned in this article
- NIST SSDF (Secure Software Development Framework)
- OWASP SAMM (Software Assurance Maturity Model)
- BSIMM (Building Security In Maturity Model)
- FedRAMP (Federal Risk and Authorization Management Program)
- FISMA (Federal Information Security Management Act)
- ISO 27001
- CMMC (Cybersecurity Maturity Model Certification)
- CIS (Center for Internet Security) Benchmarks
- CMMI (Capability Maturity Model Integration)
- Executive Order 14028
- Executive Order 14144




