Updated: 24 September, 2025
28 August, 2025
Finding vulnerabilities is not the hard part anymore. Every build and every pipeline produces a flood of scanner results. The real challenge is turning that flood into a focused set of security defects that actually get fixed. That is where security defect tracking comes in.
Before tracking can work, teams need strong vulnerability management. This means taking raw findings from many tools and turning them into something usable by aggregating, normalizing, removing duplicates, and triaging by risk and context. This produces a confirmed set of vulnerabilities that require remediation. Those items become security defects and move into issue tracking in tools such as Jira for fixing.
DefectDojo excels at this stage. It aggregates findings across your stack, normalizes vulnerabilities, deduplicates them, supports triage and then hands off to your issue tracker. In this post we start with what defect tracking is, explain why it matters, outline how OWASP SAMM defines maturity, highlight the most common challenges, and finish with a step by step implementation in DefectDojo with links to key resources and a demo video.
What Is Security Defect Tracking?
Security defect tracking manages the collection and follow up of potential issues in software, from architectural flaws to coding issues and run time vulnerabilities.
Teams define what counts as a security defect, capture them from sources such as threat assessments, penetration tests, and static and dynamic analysis tools, record them in a defined location, apply basic classification, and work to limit duplicates and false positives.
Vulnerabilities are a key input, and through triage and classification they become the security defects that are tracked and resolved through the organization’s issue management process.
Why Is Security Defect Tracking Important?
When you first put structure around security defect tracking, you gain clarity. Teams get a transparent view of known security issues per application, so it becomes possible to answer simple questions like what is open, where it sits, how long it has been there, and who owns it. That visibility makes planning and follow up possible.
As the practice matures, consistency follows. A shared severity model and clear handling rules for security defects create a common language across teams. Priorities align, handoffs speed up, and progress becomes measurable instead of anecdotal.
With advanced capabilities, assurance becomes the norm. Work runs against defined service levels, alerts surface missed targets, and reports show timely fixes to leadership and auditors.
In short, security defect tracking connects discovery to delivery, keeps issues from slipping through the cracks, and turns findings into steady risk reduction.
Listen to this episode on the Appsec Management Podcast.
What Are the Challenges with Security Defect Tracking?
Most teams know they should track security defects, but turning intent into daily practice is hard. The issue is usually structure, consistency, and integration across tools and teams.
- Fragmented systems: Findings live in spreadsheets, emails, issue trackers, and scanner reports, so work gets missed or duplicated.
- Inconsistent classification: Teams rate severity differently, which blocks prioritization and makes progress hard to compare.
- Manual workflows: Copying results or creating tickets by hand is slow, error prone, and hard to scale.
- Unclear ownership: When no one owns a defect, it lingers without follow up.
- Noisy data: Duplicates and false positives erode trust and waste time.
- Limited visibility and reporting: Leaders lack a clear view of what is open, what is overdue, and whether targets are being met.
- Not integrated with the development lifecycle: Tracking sits outside testing tools, pipelines, and planning, so it is treated as an afterthought.
These challenges are common even in mature organizations. The good news is they are solvable with a clear process and the right tooling.
How to Improve Security Defect Tracking with Defect Dojo
This section focuses on how you can improve security defect tracking by following OWASP SAMM and implementing DefectDojo. DefectDojo’s solution focuses on vulnerability management which is a step before defect tracking.
It focuses on aggregating vulnerabilities from a variety of different sources and allowing you to normalize, deduplicate and triage them to identify the security defects you need to fix.
In this section we go over what each Defect Tracking maturity level in OWASP SAMM requires, following the quality criteria and explain how DefectDojo can help with this.
Level 1: Visibility Into Known Defects
The focus in this maturity level is to create transparency around known security defects impacting particular applications.
Quality criteria:
- You can easily get an overview of all security defects impacting one application.
- You have at least a rudimentary classification scheme in place.
- The process includes a strategy for handling false positives and duplicate entries.
- The defect management system covers defects from various sources and activities.
How can DefectDojo help with this?
DefectDojo allows you to import vulnerability findings from a variety of different sources, like automated testing tools, penetration tests, bug bounty programs, amongst others, in one central location.
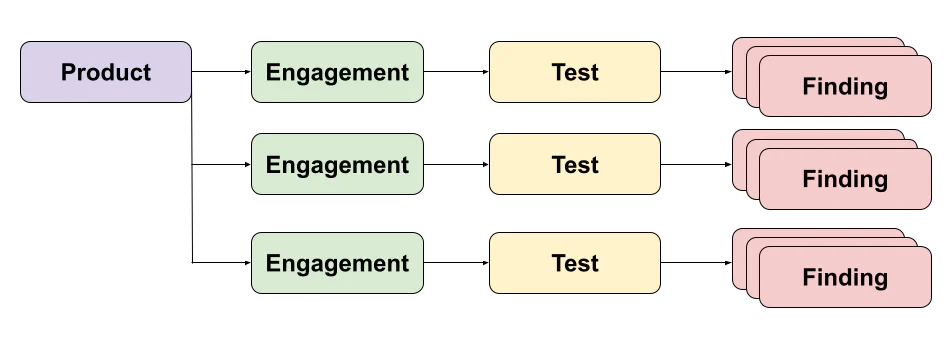
The platform allows you to then group findings by products and engagements, with a product representing an application or system and engagements a moment in time where testing happens, containing one or more tests:
Once all findings are imported and classified into the different products and engagements, DefectDojo allows you to clean the findings by normalizing and deduplicating them, assigning risk and priority scores to them and triaging them for false positives. This then allows you to identify the actual security defects you need to work on, which you can have listed within DefectDojo or export into issue trackers like Jira.
Level 2: Consistent Classification and Handling Remediation Expectations
At Level 2, the focus now turns to heaving a clear way to consistently classify security defects and offer clear expectations on how they will be handled.
Quality criteria:
- A single severity scheme is applied to all defects across the organization.
- The scheme includes SLAs for fixing particular severity classes.
- You regularly report compliance to SLAs.
How can DefectDojo help with this?
DefectDojo Pro introduces Priority and Risk scores for all found vulnerabilities. This can then be used to create a single severity scheme for identified security defects.
- Priority is a numerical rank for each finding that combines product context and finding data to help compare and sort what should be triaged or remediated first.
- Risk is a four level label derived from priority that emphasizes exploitability signals like EPSS or KEV, offering a less granular, executive friendly view that can differ from tool reported severity.
Here is a video from DefectDojo’s CEO, Greg Anderson, that explains this further:
DefectDojo also allows you to define different SLA configurations for your different products and set SLA days dependent upon the severity of the finding. You can then review and report on metrics about remediation and your SLA compliance from the built-in Remediation Insights Dashboard.
Level 3: Ensuring Defects are Handled Within SLA Timelines
Maturity level 3 requires you to ensure that SLAs are properly enforced for all security defects detected.
Quality criteria:
- You automatically alert of SLA breaches and transfer respective defects to the risk management process.
- You integrate relevant tooling (e.g. monitoring, build, deployment) with the defect management system.
How can DefectDojo help with this?
In DefectDojo you can enable notifications when SLAs are close to being breached and/or after they were breached. These notifications can be done through a variety of channels including email, Slack or as Jira comments. It is also possible to configure risk acceptances for these and other defects.
Want to learn more about DefectDojo? Watch the following demo video
Conclusion
Security defect tracking turns discovery into progress. OWASP SAMM gives you a clear plan to mature that practice, from first visibility to consistent handling and assured delivery within service levels.
DefectDojo solves the hard problem of vulnerability management before the vulnerabilities are entered as security defects. It gathers findings from many sources, cleans the noise, and supports triage so only confirmed items move into your issue tracker. With that foundation in place, classification, ownership, and reporting become easier, and meeting SLAs becomes realistic.
Your next steps are simple. Assess where you stand against the SAMM levels, centralize your inputs in DefectDojo, agree on a severity scheme and service levels, connect to Jira for ownership, and add automation where it helps. Then watch the demo video and use the linked resources to put this into practice.
Strengthen Your Defect Tracking with DefectDojo
Security begins with structured, validated vulnerability workflows, and DefectDojo is the platform to get you there. Defect tracking is a critical part of OWASP SAMM, ensuring vulnerabilities are handled with consistency and transparency. DefectDojo centralizes findings, normalizes data, removes duplicates, and supports triage so only confirmed security defects reach your issue tracker.
With DefectDojo, you can:
🔹 Aggregate findings from scanners, penetration tests, bug bounty, and disclosures in one place
🔹 Normalize, deduplicate, and classify with severity to focus effort where it matters
🔹 Push confirmed items to Jira, track ownership and SLAs, and sync status in Pro
🔹 Use dashboards and reports to monitor time to fix, trends, and program health
🔹 Automate ingest and workflows through the REST API and your pipelines
Want to reach the highest maturity in Defect Tracking?
See how DefectDojo helps teams achieve SAMM Maturity Level 3 with consistent handling and assured delivery.