Updated: 2 September, 2025
19 December, 2024
Navigating the complexities of cybersecurity frameworks can be challenging, but understanding how to implement NIST 800-53 is essential for organizations looking to strengthen their security and privacy practices. NIST 800-53 provides a strategic framework that helps organizations effectively manage risks and align security measures with their operational needs.
This blog offers a step-by-step guide to implementing NIST 800-53, from categorizing systems to tailoring and managing controls. Whether you’re a federal agency, contractor, or private organization, this practical approach ensures that your implementation is not only efficient but also tailored to your unique context. With insights into leveraging tools like SAMMY to streamline the process, you’ll discover how to simplify what might otherwise feel like an overwhelming task.
Listen to the summary of this article on the AppSec Management podcast:
Step 1: Categorize your systems using FIPS 199 and NIST 800-60
The first step in implementing NIST 800-53 is categorizing your systems based on their level of risk. This process is essential for determining which controls are relevant to each system.
FIPS 199 serves as the foundation for categorizing systems by their potential impact on confidentiality, integrity, and availability. For each system, you need to determine the impact level—Low, Moderate, or High—for each of these three objectives.
The security category for a system is expressed as:
SC = {(confidentiality, impact), (integrity, impact), (availability, impact)}
For example:
- A financial system might be categorized as:
SC = {(confidentiality, MODERATE), (integrity, HIGH), (availability, MODERATE)}
To arrive at the overall system risk classification, apply the high water mark principle. This means the system’s overall impact level is determined by the highest impact level across the three security objectives.
Using the example above:
- Since the highest impact level is High (for integrity), the overall system classification would be High risk.
NIST SP 800-60 provides guidance on identifying and assigning these impact levels based on the types of information your systems process. It maps common information types—such as financial, medical, or operational data—to provisional impact levels. You can review and adjust these levels to reflect your organization’s unique context.
Selecting the controls
Once your systems are categorized, the next step is selecting the appropriate controls from NIST 800-53. This process can be significantly simplified using SAMMY, our secure SDLC Management Tool.
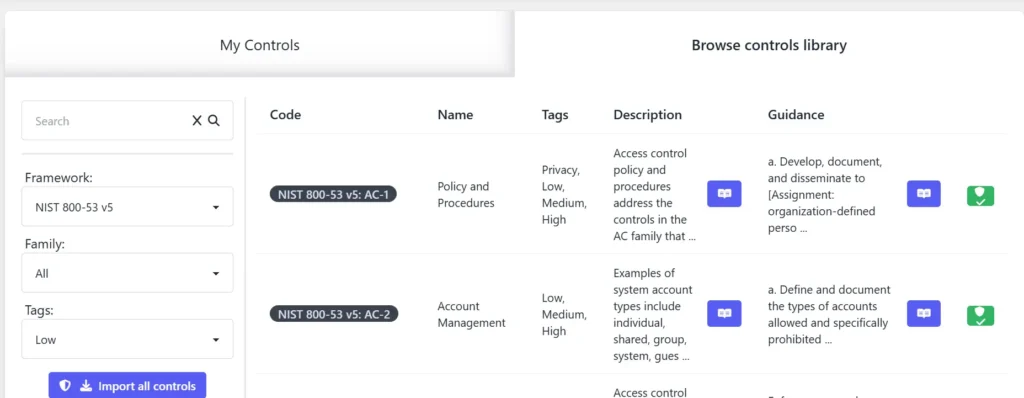
Inside SAMMY, you can find the Controls screen under the Manage menu. Clicking on it takes you to the My Controls page, which initially will be empty. To select the controls relevant to your system’s risk classification, navigate to the Browse Controls Library option and filter the controls by their tags on the left. Once filtered, click on Import All Controls to add these controls to your My Controls page.
Step 2: Tailor controls to your organization’s context
After selecting the relevant controls, the next step is tailoring them to your organization’s specific context, systems, and applications. NIST 800-53 emphasizes tailoring controls to reflect your organization’s unique risks, mission, and operational environment, rather than implementing them as-is.
Tailoring controls in SAMMY
Within SAMMY, the tailoring process is streamlined through the Status column for each control. Here’s how you can manage and document tailoring:
- Mark controls as “Not applicable” where necessary:
- Some controls may not be relevant to certain systems. For example, a control related to supply chain management might not apply to an internal-only system. Use the Status column to mark such controls appropriately.
- Modify and document tailored controls:
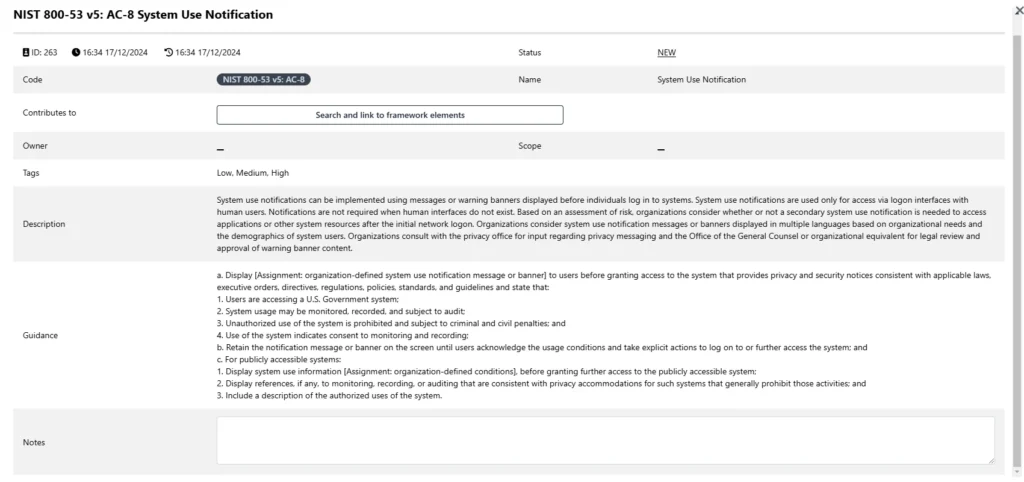
- SAMMY allows you to edit the details of each control to align with your organization’s specific needs. Use the Notes section to document how and why a control was tailored. This transparency ensures clarity and accountability in your implementation process.
Considering untagged controls
In addition to controls tagged with Low, Moderate, or High classifications, NIST 800-53 includes some controls without predefined tags. These untagged controls are often foundational or broadly applicable, and they provide flexibility to address nuanced risks. During tailoring, evaluate these controls and include those that are relevant to your organization.
For example:
- Controls related to overarching security policies or privacy considerations may not have specific tags but are still critical for comprehensive implementation.
SAMMY’s interface highlights such controls, making it easy to review and integrate them as part of your tailored approach.

Step 3: Implement the controls and assign responsibilities
Once the relevant controls have been selected and tailored to your organization’s needs, the next step is to focus on implementation. This requires assigning responsibilities, defining scopes, and managing progress to effectively put the controls into practice.
Managing control implementation in SAMMY
In SAMMY, control implementation is streamlined through a structured interface that allows you to clearly define ownership and scope for each control. Here’s how it works:
- Assign an owner for each control:
- Each control can be assigned to a specific individual or team responsible for its implementation.
- Ownership ensures accountability and transparency, as the person in charge can update the control’s progress status.
- Define the scope:
- Controls can be applied to various levels within your organization, such as:
- Specific product groups
- Individual business units
- Specific products or systems
- This flexibility ensures that controls are implemented where they are most relevant.
- Controls can be applied to various levels within your organization, such as:
The screenshot below illustrates the My Controls page in SAMMY, showing how controls are organized:
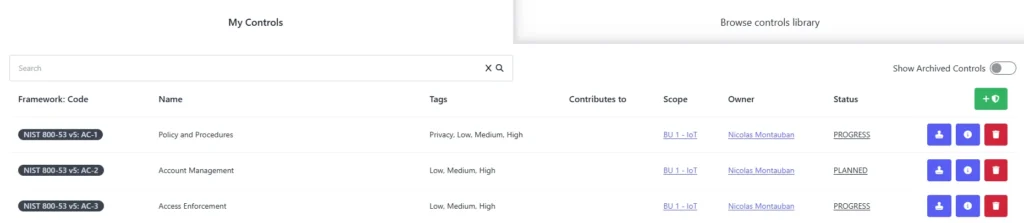
- Each control includes its framework code, name, tags, and current status.
- The Owner column identifies the individual responsible for the control.
- The Scope column highlights the areas where the control is applied.
Tracking implementation status
SAMMY allows you to monitor and update the implementation progress of each control using the Status column. Each status represents a stage in the implementation lifecycle and ensures visibility across the organization.
- NEW: The control has just been added to the My Controls page and has not been addressed yet.
- PLANNED: The control has been identified, and its implementation is scheduled to begin soon.
- PROGRESS: Work is actively underway to implement the control.
- PARTIALLY IMPLEMENTED: Some aspects of the control have been implemented, but further work is still required.
- IMPLEMENTED: The control has been fully implemented and is now operational.
- ALTERNATIVE IMPLEMENTATION: The control’s intent is being addressed using an alternative approach or method.
- NOT APPLICABLE: The control is not relevant for the specific system or scope due to its context.
By providing clear status options, SAMMY enables organizations to track the progress of their control implementation with precision. Owners can update the status as work advances, ensuring real-time visibility and accountability.
Step 4: Review progress and manage documentation
Once controls are in the process of being implemented, it is essential to track progress and review evidence to ensure they are implemented effectively. Accurate documentation enables organizations to demonstrate compliance and verify proper implementation of each control.
Updating control status and tracking progress
In SAMMY, the person assigned as the control owner is responsible for keeping the control status up to date. This ensures transparency and accountability throughout the implementation process. Regularly reviewing the status helps meet implementation timelines and promptly address any issues.
Providing evidence through documentation
To verify the implementation of a control, SAMMY includes a Documentation feature where control owners can provide evidence. This evidence can include:
- Policies or procedures created
- Screenshots of implemented security measures
- Reports or logs demonstrating compliance
- Notes on how the control was tailored or adjusted
The documentation screen allows control owners to upload and maintain records efficiently. Use the remarks section to provide context, such as:
- What evidence is being submitted
- Any additional information to explain how the control meets its objectives
The screenshot below illustrates how the Documentation page works within SAMMY:
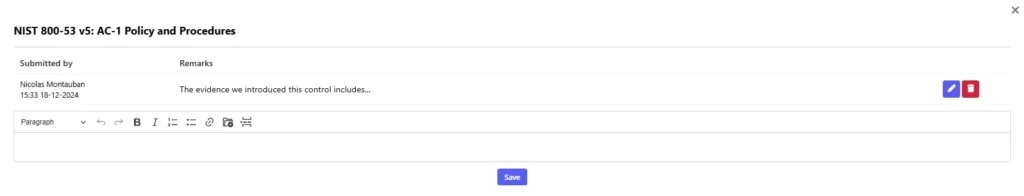
By centralizing documentation, SAMMY helps organizations maintain a clear audit trail and simplifies compliance reporting. This ensures all stakeholders can access the necessary evidence to confirm proper implementation of controls.
Optional Step: Link controls to application security frameworks
While implementing NIST 800-53 controls strengthens your organization’s security posture, these efforts can also contribute to implementing other application security frameworks. SAMMY allows you to link controls to specific elements in widely used frameworks, such as ISO 27001, OWASP SAMM, BSIMM, and NIST SSDF. This feature ensures that implementing a single control can support progress across multiple frameworks, saving time and resources.
Linking controls to SAMM elements
For example, a NIST 800-53 control like AC-1: Policy and Procedures can be mapped to the Compliance Management elements under the Governance – Policy and Compliance stream in OWASP SAMM. This highlights how implementing the control helps advance the implementation of a related element in OWASP SAMM.
The screenshot below shows how SAMMY displays these relationships, clearly indicating which framework elements a control contributes to:

By leveraging this feature, organizations can:
- Streamline efforts: Avoid duplication of work by mapping a single control to multiple frameworks.
- Demonstrate alignment: Show how implementing NIST 800-53 controls supports progress within other application security frameworks.
- Simplify tracking: Easily monitor and report on the overlap between NIST 800-53 controls and additional frameworks.
A unified approach to security and framework implementation
This capability in SAMMY helps organizations adopt a unified approach to implementing security frameworks. By connecting NIST 800-53 controls to other frameworks, you can efficiently align your security efforts and demonstrate meaningful progress across multiple standards.
Conclusion