As I reflect on my experience at the 4YFN conference in Barcelona, one thing stands […]
Have you every been hacked? It sucks right? But don’t worry now, let’s make sure[…]
Fraud against government programs costs taxpayers billions of dollars every year, threatening the integrity of[…]
In today’s digital landscape, cybercrime is escalating at an alarming rate, with projected damages reaching[…]
In today’s rapidly evolving digital landscape, ensuring software security is more critical than ever. Recognizing[…]
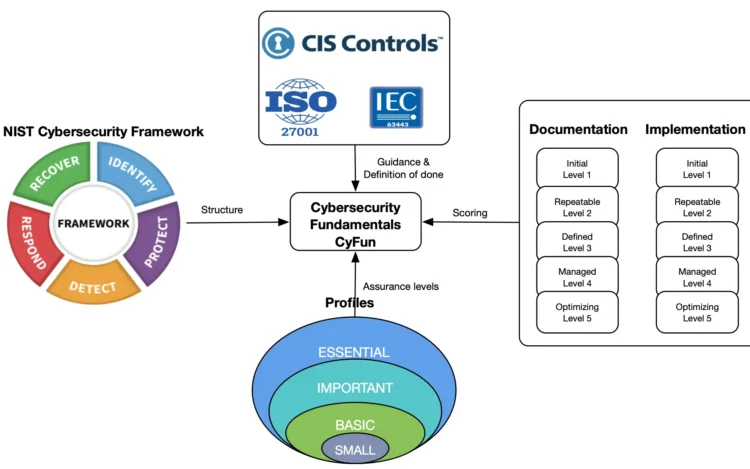
Introduction In this blog, we will focus on helping you understand what is Cybersecurity Fundamentals[…]
Dear disgruntled employee (let’s call you Mallory): Tired of working long hours with no holidays,[…]
Navigating the complexities of cybersecurity frameworks can be challenging, but understanding how to implement NIST[…]
In the evolving landscape of cybersecurity, organizations face the challenge of protecting their systems and[…]
Implementing ISO 27001 is crucial for organisations looking to protect sensitive information and ensure compliance[…]
HIPAA, the Health Insurance Portability and Accountability Act of 1996, is a critical federal law[…]
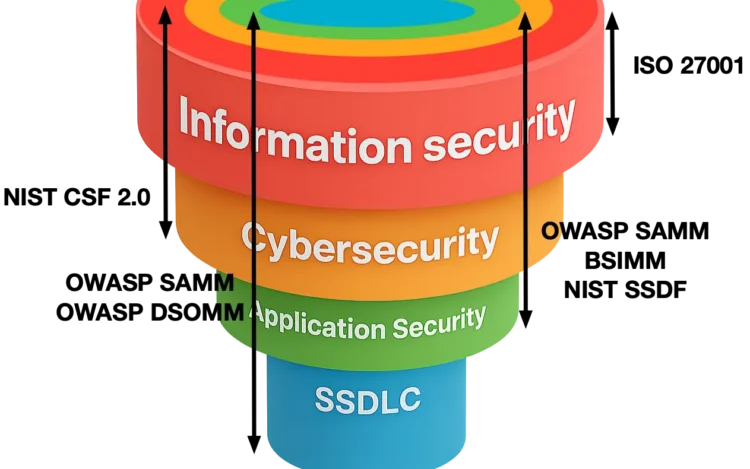
The terms information security and cybersecurity are often used interchangeably, which frequently leads to confusion.[…]