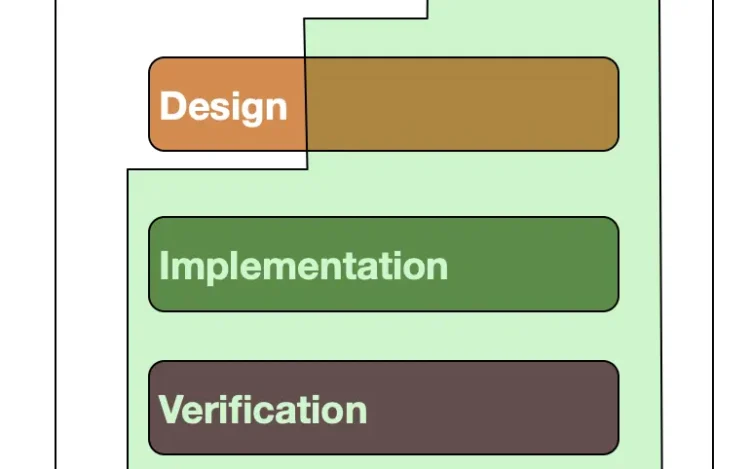
By embracing the Japanese Kaizen philosophy of continuous incremental improvement, your AppSec program can evolve […]
Your DevSecOps pipeline is fast, automated, and built to scale. But is security truly integrated,[…]
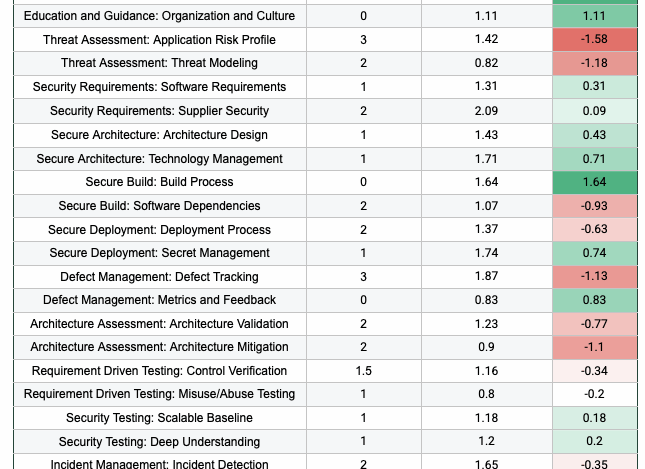
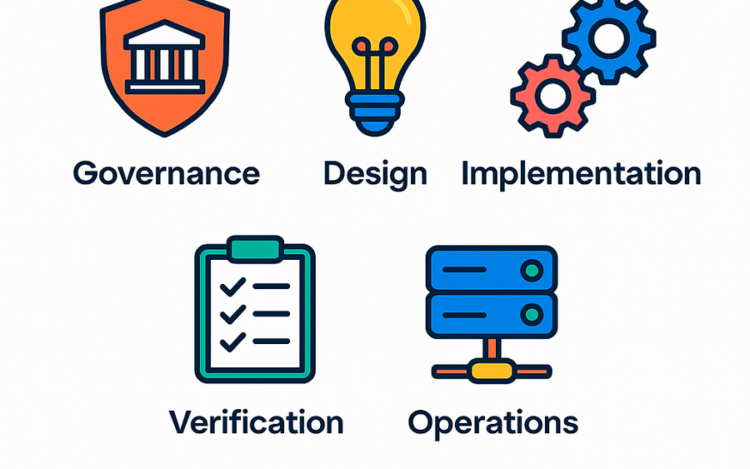
About 4 years ago I have joined the OWASP Software Assurance Maturity Model (SAMM) project[…]
In this technical article, we will explore how to improve your DevSecOps processes by integrating[…]
This article contains a variety of different cybersecurity statistics and trends of 2025 and recent[…]
Most security issues in software stem from one simple problem: teams try to fix them[…]
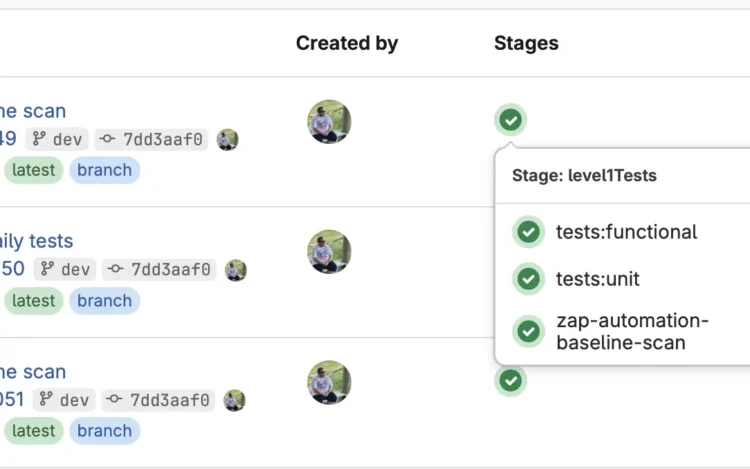
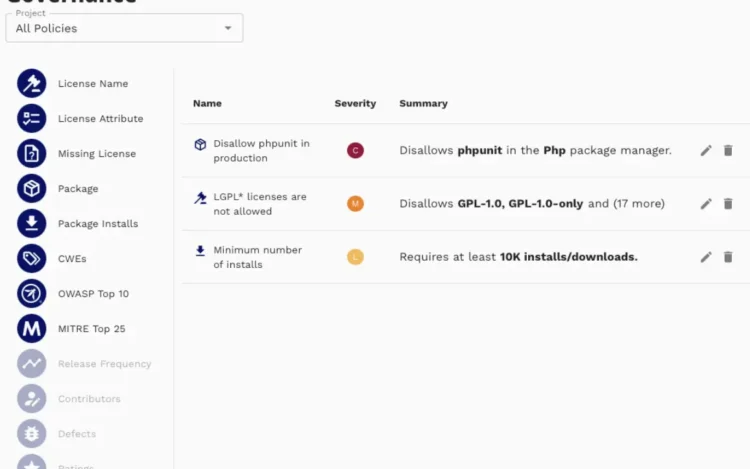
Dependency management has become one of the most critical aspects of modern software development. Third-party[…]
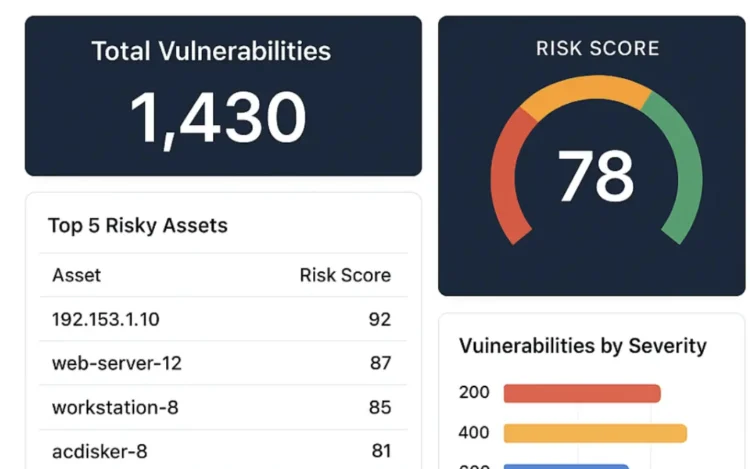
You’ve probably heard the saying, “You can’t manage what you don’t measure.” If you are[…]
Official framework, regulation and standard pages mentioned in this article CRA GDPR OWASP SAMM[…]
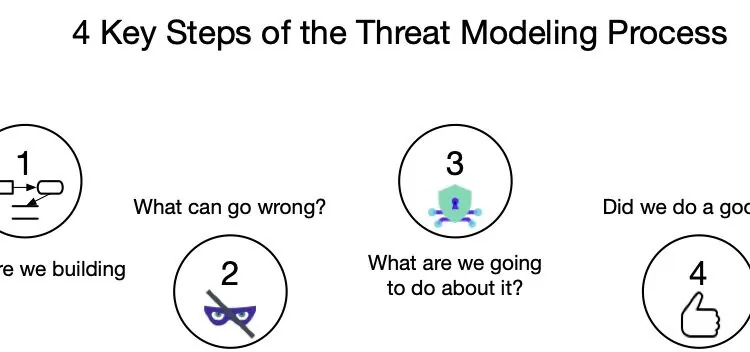
Threat modeling shaped my AppSec career. It helped me wrestle with one of security’s most[…]
Modern software development moves fast, and so do the security challenges that come with it.[…]
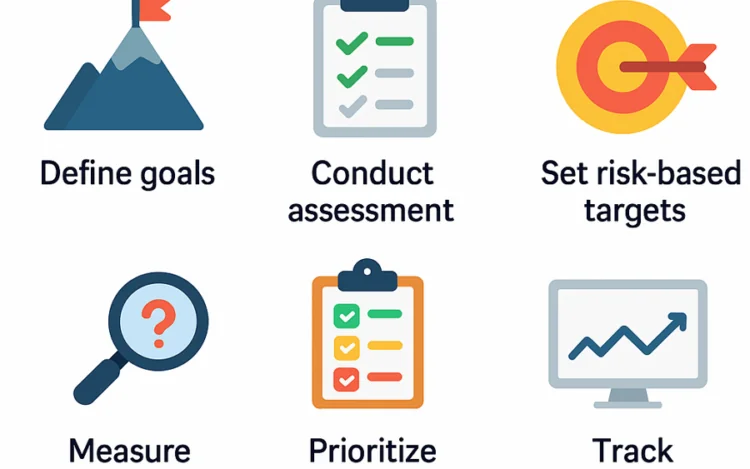
Understanding OWASP SAMM is only the beginning. The real value comes from using it to[…]