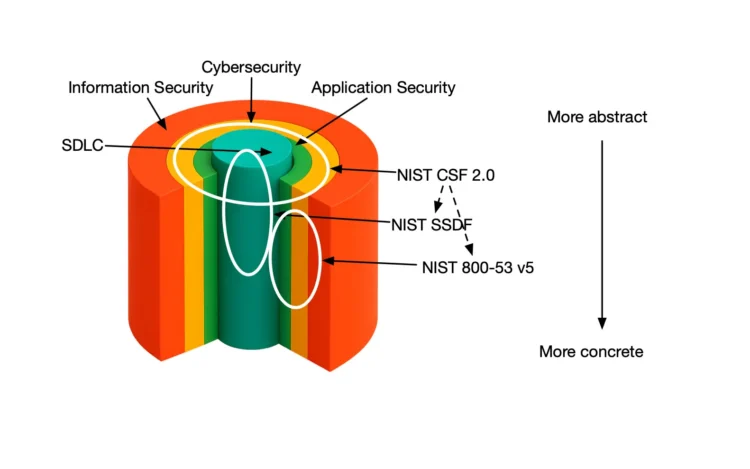
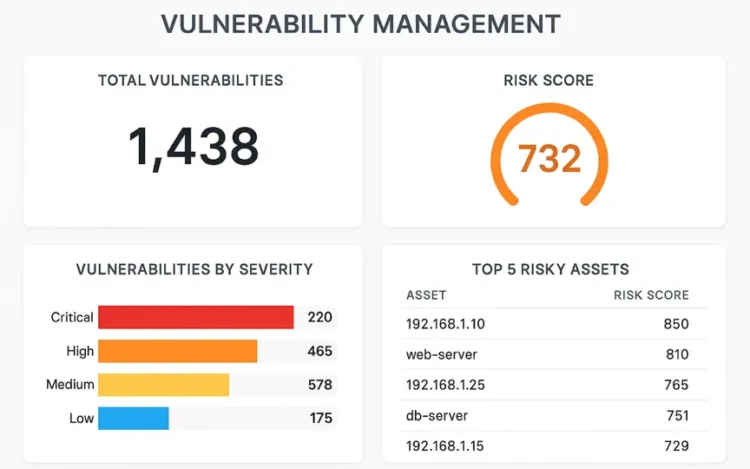
Security programs rarely fail because teams do not care. They fail because the work gets […]
For the past couple of decades, organizations have increasingly invested in security. Unfortunately, they often[…]
If you build or look after web applications, you have probably bumped into the OWASP[…]
The upcoming Cyber Resilience Act (CRA) is a EU regulation that was published on November[…]
The warning shots are over. The NIS 2 Directive is live, and enforcement has begun.[…]
As software systems grow more complex, proving that they are secure has become as important[…]
Most organizations conduct security assessments, yet few turn them into meaningful improvement. Traditional cybersecurity gap[…]
Automated Application Security Testing (AAST) refers to the use of software tools to identify vulnerabilities[…]
Many organizations treat Common Vulnerabilities and Exposures (CVEs) as first-class citizens. Some even enforce strict[…]
Developers are under pressure to deliver fast, but often without the tools to build securely.[…]
Application security (AppSec) remains one of the toughest challenges modern organizations are facing. Despite heavy[…]
Finding vulnerabilities is not the hard part anymore. Every build and every pipeline produces a[…]