Updated: 4 March, 2025
12 February, 2025
Introduction: Architecture Validation with IcePanel
Architecture validation is the process of reviewing your architecture to ensure that all requirements are correctly implemented. It’s a crucial step because design mistakes can lead to costly issues down the line. SAMM’s architecture validation stream focuses on this process, helping you confirm the security quality of your architecture before proceeding to implementation.
IcePanel simplifies architecture validation by providing a structured, collaborative approach. With its out-of-the-box support for the C4 models and interactive features, IcePanel helps teams document, refine, and validate architecture efficiently. In this blog, I will provide a complete guide to implementing OWASP SAMM’s Architecture Validation according to best practices and show how IcePanel can be an essential part of your tooling.
Understanding Architecture Validation: Why it matters
What is Architecture Validation
Architecture validation ensures that your application’s foundation correctly implements all functional and quality requirements.
OWASP SAMM’s Architecture Validation focuses on verifying security at the architectural level. This activity ensures that security decisions made early in the design process hold up in the actual implementation. Security is universally recognized as a critical and non-negotiable aspect of modern software. However we often misperceive it as something that emerges from source code and test cases alone. In reality, your architecture forms the foundation upon which detailed design and code are built. If security flaws exist at this level, they will propagate throughout the application, making later-stage fixes significantly more costly and complex.
Why is Architecture Validation Essential for Your Application Security Program
Architecture validation is the first checkpoint to ensure that all requirements have been correctly implemented.
Developers often treat architecture as a given – something defined by technology rather than deliberate design. Many frameworks provide built-in architectural patterns and components. For example, the .NET framework addresses several security concerns out of the box. However, the architecture itself provides a foundation, ensuring security is integrated by design rather than relying solely on framework defaults. Architecture validation ensures that security decisions are implemented correctly, rather than becoming ad hoc fixes scattered throughout the codebase.
Why Should We Prioritize Architecture Validation
A secure-by-design architecture provides the necessary guardrails for secure coding, and validating those guardrails early saves time and money.
A well-structured architecture is key to addressing security concerns systematically. You should design and implement security controls at the architecture level first. Examples include input validation, encryption strategies, and access control. If you misconfigure or misapply these controls, every dependent component will inherit the flaws.
A Real-World Example
I’ve seen firsthand how architectural decisions shape security outcomes. In one of our applications, we had well-defined security requirements enforcing user input sanitization and output escaping. At the architectural level, we decided to introduce a global sanitizer for all user input and a separate component to escape all user output. However, at the code level, the implementation team realized that some sanitized input was being unintentionally altered or dropped. For example, O’Reilly was being escaped into O'Reilly. Instead of fixing the issue at the architectural level, the dev team has modified the implementation of the sanitizer instead. The right solution was to revisit the architecture instead and make sure that sanitizing was only applied to rich text input. For all other user input we would only use output escaping. Fortunately, this architectural misstep wasn’t too costly, as we had already implemented consistent output escaping across the application.
This experience reinforces a key lesson: architectural validation is crucial in preventing security issues before they reach production. Without a structured validation process, seemingly good architectural decisions can lead to expensive implementations or, even worse, security vulnerabilities.
The Path to Maturity with IcePanel
In this section, I will explore the path to security maturity for the Architecture Validation stream in SAMM. While there are many ways to approach architecture validation, having the right tools can make the process significantly more efficient and structured. IcePanel not only simplifies architectural documentation, but also provides a formal architectural notation method. The latter is a critical component of this SAMM stream. With built-in support for the C4 model, IcePanel ensures that teams follow a structured approach to modeling and validating their architecture.
What is IcePanel 🧊
Effective architecture modeling and validation are key to a strong application security program. However many teams struggle with ad-hoc documentation methods that lack consistency and scalability. IcePanel addresses this challenge by providing a dedicated architecture modeling tool that simplifies the creation, visualization, and refinement of software architectures. IcePanel enables teams to document their architecture in a structured way with a single source of truth, ensuring security principles are baked into the design from the start. With built-in support for formal modeling techniques, IcePanel makes architecture validation more efficient, interactive, and actionable, helping teams continuously improve security.
What is the C4 Model Standard
The C4 model is a widely adopted approach that breaks down architecture into four levels: Context, Container, Component, and Code. C4 provides a practical, scalable, and intuitive way to visualize architecture at different levels of abstraction. This structured approach allows teams to focus on relevant security concerns at each level, making it particularly useful for other SAMM activities, such as Threat Modeling and Architecture Mitigation. IcePanel serves as a dedicated C4 model implementation tool, enabling teams to seamlessly adopt and apply this methodology to their security and development workflows.
Maturity Level 1: The Ad-hoc Approach for Architecture Validation
The essence of this activity requires you to adopt a modeling notation for your architecture and use an informal review process.
A model of your architecture
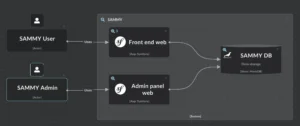
Architecture Validation requires “an agreed upon model of the architecture”. While a rough sketch on paper might work, IcePanel offers significant advantages.
- The architecture is easy to create and adapt with IcePanel
Your architectural diagram is never perfect from the first draft. With IcePanel, components can be easily adjusted, unlike static paper sketches.
- IcePanel leverages the C4 model for structure and simplicity
SAMM encourages formalism in architecture modeling and mandates it at higher maturity levels. The C4 model is an excellent choice for visualizing software architecture, offering four layers of abstraction: Context, Container, Component, and Code. IcePanel makes it easier to understand and communicate these complex systems effectively.
- IcePanel supports collaboration and interactivity with “intelligent zoom”
The collaboration and interactivity of IcePanel allow technical and non-technical teams to align on key aspects of your security. IcePanel’s “intelligent zoom” allows stakeholders to zoom in for more details or out for a broader view, ensuring everyone gets the right level of understanding of the system.
An informal process to review the security requirements
The second requirement for Level 1 maturity is to review the architecture with architects and security champions. The team should ensure the architecture aligns with all security requirements and facilitates their actual implementation. The process doesn’t need to be formal. However, as a SAMM assessor, I would expect session notes and architectural diagrams as evidence.
Maturity Level 2: Achieving Efficiency and Effectiveness in Architecture Validation
Reaching Level 2 maturity requires a formal and structured approach. Unlike Level 1, which allows ad-hoc reviews, SAMM expects a systematic method. To meet the basic requirements of this activity, the following must be in place:
Comprehensive security requirements
Create and maintain a detailed list of security requirements. Include external compliance obligations, like GDPR. This step connects directly to the Software Requirements stream and supports the foundation for architecture validation.
Log and track findings
Architecture validation is not a one-time brainstorming session. You should record all findings and track them until resolved. Avoid forgotten discussions by ensuring clear follow-up actions.
The core of Maturity Level 2 lies in a formalized architecture review process, which consists of two key components.
Formalized review process
Define a review process that ensures teams systematically address each security requirement at the architectural level. Use checklists or integrate this process with Threat Modeling. The review should produce a concise document proving the architecture meets the security requirements. Avoid vague claims like “the architecture is secure.” Instead, describe security as clear set of quality scenarios.
Structured notation and tooling
SAMM also requires a structured notation. Tools are essential for this. IcePanel, with C4 models, is an ideal solution. C4 diagrams help validate architecture and integrate with Threat Modeling efforts. Personally, I am a fan and contributor to STRIDE and LINDDUN methodologies, but organizations are free to adapt them to their needs. In my view, C4 context diagrams are often more practical and effective than traditional Data Flow Diagrams (DFDs). Furthermore, IcePanel extends beyond C4 models, offering animated data flows and interactions. These features enhance documentation, especially for critical security requirements. IcePanel Flows also provide a practical way to implement sequence diagrams, making them a versatile and effective tool.
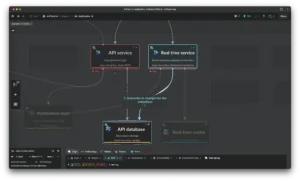
Maturity Level 3: Mastering Architecture Validation
Consistency beats quality – not because quality doesn’t matter, but because true mastery comes from continuous refinement. Level 3 maturity isn’t about a perfect one-time review. It is about making architecture validation an ongoing, systematic process. Here are the key steps for achieving level 3 maturity.
- Regularly revisit your architecture
Even if nothing has changed, you should routinely review your security requirements and ensure they are effectively aligned with your architecture. Use IcePanel and the formalized review process from level 2 to verify preventive, detective, and response capabilities of your architectural security controls. Furthermore, you can easily track changes to your architecture in IcePanel with history logs and versioning. - Align security controls with organizational strategy
At level 3, Architecture Validation goes beyond a single application. You should start aligning with the rest of the broader organizational security strategy. For example, your authentication system may be secure, but if your organization is standardizing on OAuth 2.0 with OpenID Connect, migrating improves consistency and scalability. Using IcePanel, you can easily scale these efforts in a centralized tool. - Integrate with other security practices
As with any other level 3 SAMM activities, Architecture Validation strengthens and depends on other security streams including Architecture Design, Technology Management, Threat Modeling, and Architecture Mitigation.
Strengthen Your Architecture Validation with IcePanel
Security begins with structured and validated architecture—and IcePanel is the tool to get you there. Architecture Validation is a critical part of OWASP SAMM, ensuring your software is designed with security in mind. With built-in C4 model support and interactive architecture visualization, IcePanel enables teams to document, analyze, and refine software architecture efficiently.
With IcePanel, you can:
🔹 Adopt a structured architectural notation with the C4 model for clear, scalable documentation.
🔹 Streamline architecture validation with formalized reviews and structured security requirements.
🔹 Log, track, and refine security decisions with historical insights and versioning.
🔹 Align security controls with organizational strategy for consistency across applications.
🔹 Integrate with other SAMM activities like Threat Modeling and Architecture Mitigation.
Want to reach the highest maturity in Architecture Validation?
Discover how IcePanel helps organizations achieve SAMM Maturity Level 3 with a structured and continuous approach.
Why IcePanel Should be Part of Your Security Strategy
A well-documented architecture is fundamental to a strong application security program. Yet many teams still rely on ad-hoc dry-erase board drawings that lack consistency and traceability. IcePanel provides a standardized, structured way to document and share architecture, making it an essential tool for security-focused organizations.
Create a Pragmatic and Secure Architecture Model
The C4 model offers a practical yet comprehensive approach to documenting architecture. The only alternative I am personally familiar with is the 4+1 architectural model by Philippe Kruchten (whom I had the pleasure of meeting in 2006). However the C4 model is more practical delivering high value with a lower time investment. From a security perspective, C4 enables teams to embed security design principles directly into the architecture from the start.
Validate and Refine the Model
A well-documented architecture isn’t enough, you should validate it systematically. IcePanel’s C4 model allows security teams to analyze each layer in a structured manner, ensuring that critical security controls are present and effective. The ability to zoom in on different levels of abstraction makes it easier to assess security at both high-level system interactions and low-level component details.
Threat Modeling with C4 Context Diagram
Integrating IcePanel into your application security program ensures that architecture is documented, validated, and continuously improved. As a robust architecture modeling and documentation tool, IcePanel helps teams embed security principles into design, validate their effectiveness, and drive ongoing security enhancements, making it an essential component of a strong security strategy. 🚀


