Updated: 30 September, 2025
24 March, 2025
As I reflect on my experience at the 4YFN conference in Barcelona, one thing stands out: the relentless pursuit of robust security measures by large multinationals. The conference showcased a range of cybersecurity trends and advanced strategies being implemented to safeguard data and systems, highlighting the industry’s commitment to staying ahead of emerging threats in our interconnected world. The conference provided a unique opportunity to hear directly from industry leaders and innovators about the strategies they are implementing to stay ahead of the curve. Let’s examine these cybersecurity measures and discuss how organizations can effectively implement them to enhance their overall security posture.
Token Separation
Large e-commerce platforms mentioned separating identification tokens from authorization tokens in an effort to segment access to data by creating distinct layers of cybersecurity. This approach enhances data protection and access control in the following ways.
Benefits of Token Separation
- Improved access segmentation: By separating identification and authorization tokens, organizations can have a more granular control over data access.
- Enhanced security: The separation adds an extra barrier against unauthorized access, as an attacker would need to compromise both token types to gain full system access.
- Reduced risk: In the event of a token compromise, the damage is limited since a single token doesn’t grant full system access.
- Compliance support: This approach aids in meeting regulatory requirements by implementing stronger access controls and data protection measures.
- Flexible authentication: Organizations can implement different authentication methods for identification and authorization, further strengthening security.
Post-Quantum Encryption
Post-quantum cryptography (PQC) is an emerging field of cryptography designed to protect against attacks from future quantum computers. In August 2024, the U.S. National Institute of Standards and Technology (NIST) released its first three finalized post-quantum encryption standards.
- FIPS 203: Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM)
- This standard, based on the CRYSTALS-Kyber algorithm, serves as the primary method for general encryption. ML-KEM enables efficient and secure key exchanges, offering advantages such as relatively small encryption keys and rapid operation.
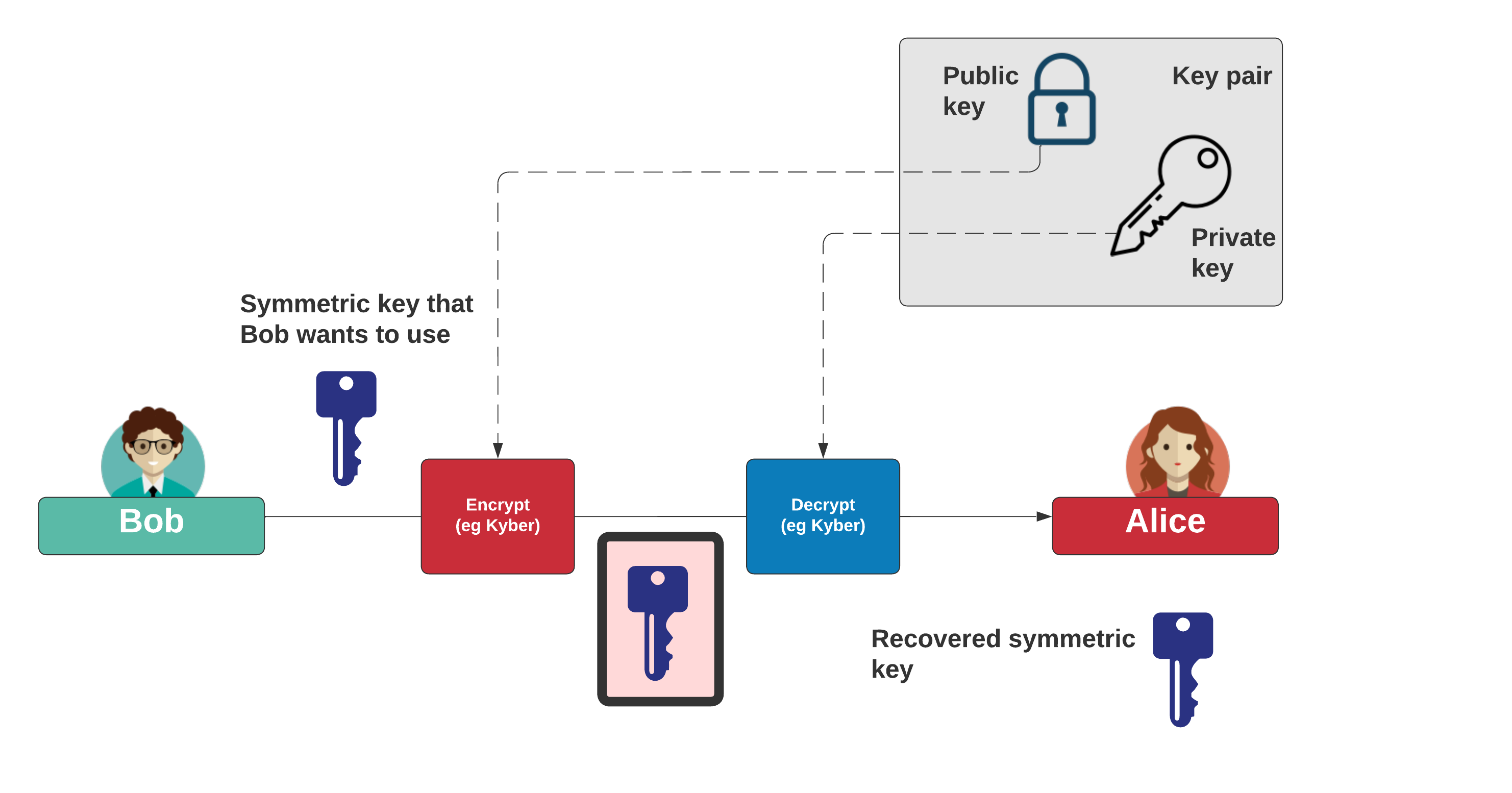
- This standard, based on the CRYSTALS-Kyber algorithm, serves as the primary method for general encryption. ML-KEM enables efficient and secure key exchanges, offering advantages such as relatively small encryption keys and rapid operation.
- FIPS 204: Module-Lattice-Based Digital Signature Algorithm (ML-DSA)
- Derived from the CRYSTALS-Dilithium algorithm, ML-DSA is the main standard for digital signatures. It ensures the authenticity and integrity of digital communications, providing a robust defense against potential quantum attacks.
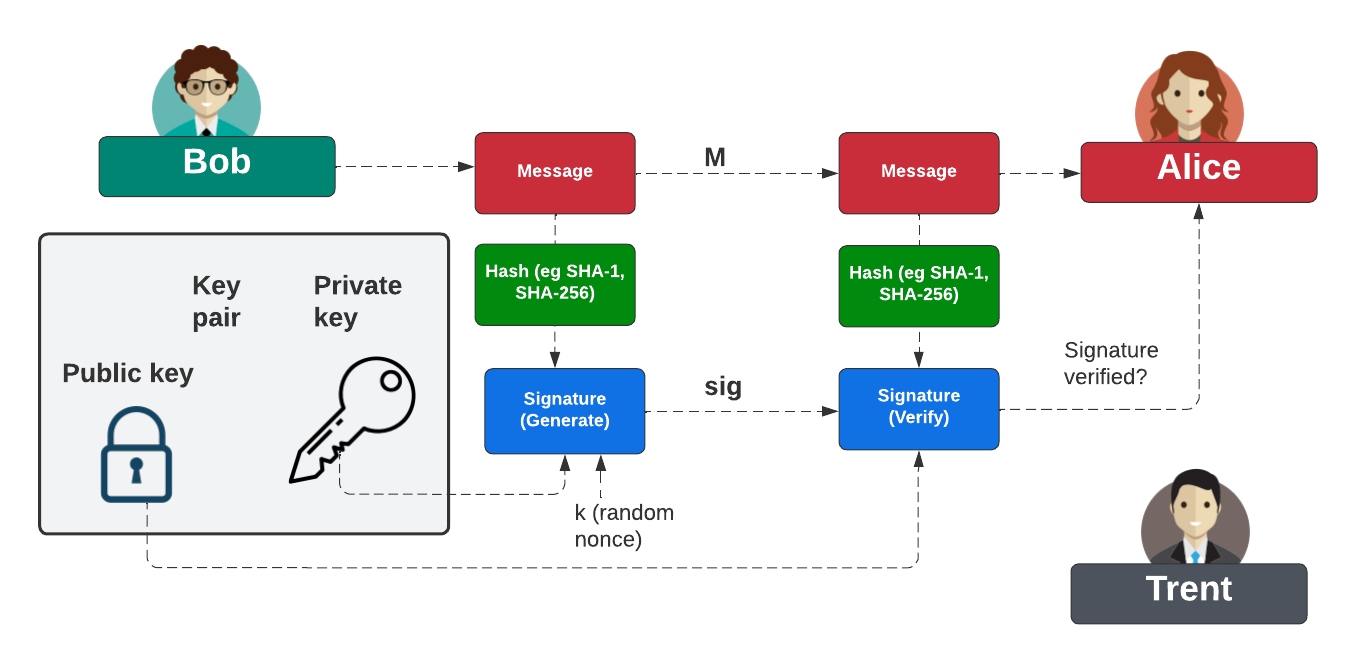
- Derived from the CRYSTALS-Dilithium algorithm, ML-DSA is the main standard for digital signatures. It ensures the authenticity and integrity of digital communications, providing a robust defense against potential quantum attacks.
- FIPS 205: Stateless Hash-Based Digital Signature Algorithm (SLH-DSA)
- Based on the Sphincs+ algorithm, SLH-DSA offers an alternative approach to digital signatures. Utilizing different mathematical foundations than ML-DSA, it serves as a backup to enhance cybersecurity diversity.
Financial institutions prefer investing in the installation of post-quantum encryption APIs and VPNs between backend systems and devices. This strategy safeguards against the “harvest now, decrypt later” attack scenario. Ensuring long-term security for sensitive data and communications while maintaining crypto-agility, allowing systems to adapt to new cryptographic standards. However, integrating PQC into existing systems presents several challenges.
Challenges of Post-Quantum Cryptography Implementation
- Computational load: PQC algorithms generally require more processing power, potentially slowing down operations and increasing energy consumption by 2-3 times compared to classical cryptography.
- Resource constraints: The higher CPU cycle and memory usage pose challenges for small devices like smartphones, IoT devices, and sensor networks.
- Key sizes: PQC algorithms often require much larger key sizes. For example, Kyber768 has a public key size of 2400 bytes, significantly larger than RSA or ECC equivalents.
- Signature sizes: PQC signatures are also larger. ML-DSA, for instance, has a signature size of 2,430 bytes, compared to 384 bytes for RSA-3072.
- Memory limitations: Larger key and signature sizes may exceed the memory capacity of some devices, particularly in IoT and embedded systems.
- Bandwidth issues: Increased data transmission volumes due to larger keys and signatures can impact network performance, especially in constrained environments.
- Key management: The labor required to generate and validate keys is often substantially more than with classical cryptography.
- Backward compatibility: Ensuring new PQC solutions work with existing systems and protocols is challenging, especially for legacy systems.
- Interoperability: During the transition period, PQC algorithms must be compatible with systems still using classical cryptography.
- Protocol adjustments: Larger key sizes and signatures require modifications to protocols like DTLS, QUIC, and conventional TLS to accommodate increased data volumes.
- Implementation vulnerabilities: The complexity of new PQC primitives introduces potential new vulnerabilities.
Network Tokenization
Network tokenization is an advanced cybersecurity measure that replaces sensitive payment card data with unique, randomized tokens. Subscription-based services as well as global payment networks mentioned adopting network tokenization for enhanced security and efficiency. This method significantly reduces fraud risk. Since it replaces Primary Account Numbers (PANs) with unique tokens, making stolen data useless to attackers. This improves authorization rates and reduces false declines, simplifying operations through automated token management. Network tokens can lead to a 4.3% authorization rate lift, potentially recovering millions in revenue for large merchants. Network tokenization aids in meeting regulatory requirements as it helps businesses comply with data privacy regulations like GDPR and PCI DSS.
ISO 27001 Certification
ISO 27001 certification is a globally recognized standard for information security management systems (ISMS). This certification was a common denominator amongst large telecom companies. It is likely this certification was chosen to demonstrate a commitment to information security best practices. ISO 27001 helps organizations plug cybersecurity gaps, reduce the risk of successful cyber attacks, and implement robust information security measures. It not only provides a framework for identifying and mitigating security but as an internationally recognized certification, it enhances customer trust and confidence in data handling.
Certification Process
The ISO 27001 certification process typically involves the following steps:
- Project Planning: Define the scope, get management buy-in, and decide on resources.
- ISMS Development: Create an Information Security Management System tailored to the organization’s needs.
- Risk Assessment: Conduct a thorough risk assessment and gap analysis.
- Implementation: Design and implement necessary controls and security measures.
- Documentation: Prepare required documentation and collect evidence of compliance.
- Internal Audit: Conduct an internal audit to ensure readiness for certification.
- Certification Audit: Undergo a two-stage external audit process:
- Stage 1: Review of ISMS documentation
- Stage 2: In-depth evaluation of business processes and controls
- Certification: Upon successful completion, receive the ISO 27001 certificate, valid for three years.
- Ongoing Compliance: Maintain the ISMS through regular internal reviews and annual surveillance audits.
The 4YFN conference in Barcelona proved to be an enlightening experience. What became evident is that large multinationals are not resting on their laurels when it comes to protecting their digital assets. Instead, they are adopting a multi-faceted approach to security, implementing several advanced measures that promise to reshape the cybersecurity landscape in the years to come.
Official resources
- FIPS 203
- FIPS 204
- FIPS 205
- CRYSTALS-Kyber algorithm
- CRYSTALS-Dilithium algorithm
- Sphincs+ algorithm
- GDPR
- DCI PSS
- ISO 27001





