Application security (AppSec) remains one of the toughest challenges modern organizations are facing. Despite heavy […]
Your DevSecOps pipeline is fast, automated, and built to scale. But is security truly integrated,[…]
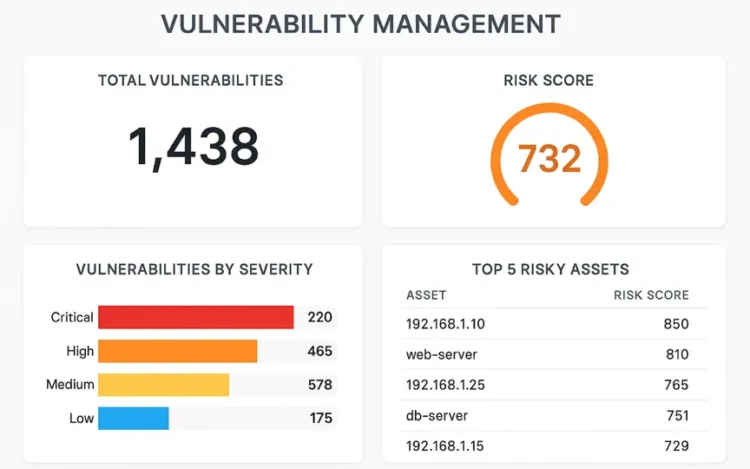
Understanding OWASP SAMM is only the beginning. The real value comes from using it to[…]
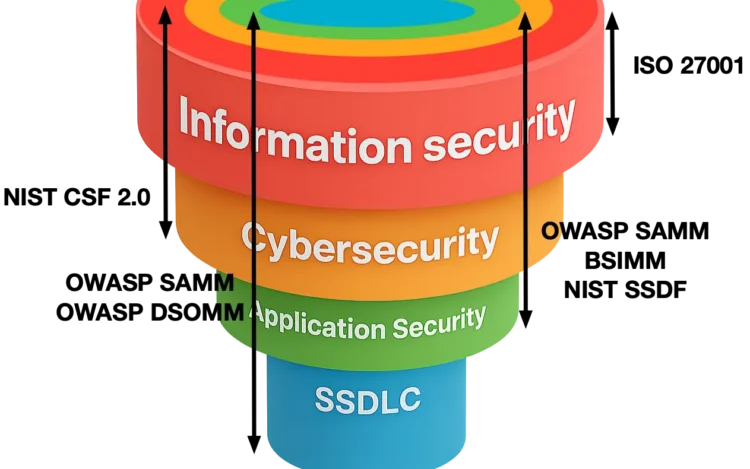
The terms information security and cybersecurity are often used interchangeably, which frequently leads to confusion.[…]
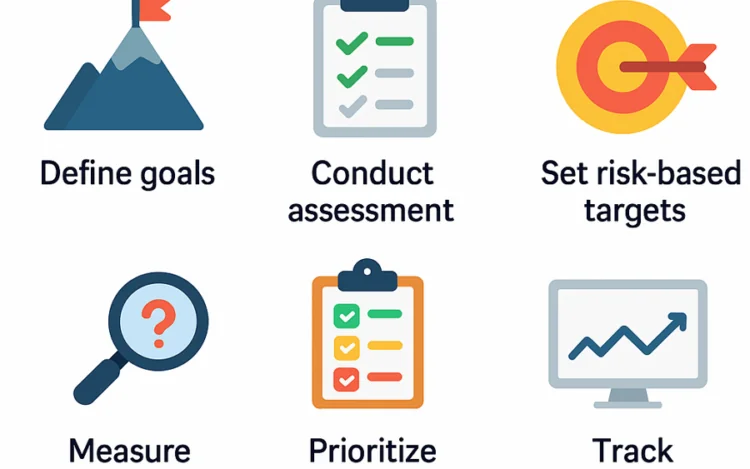
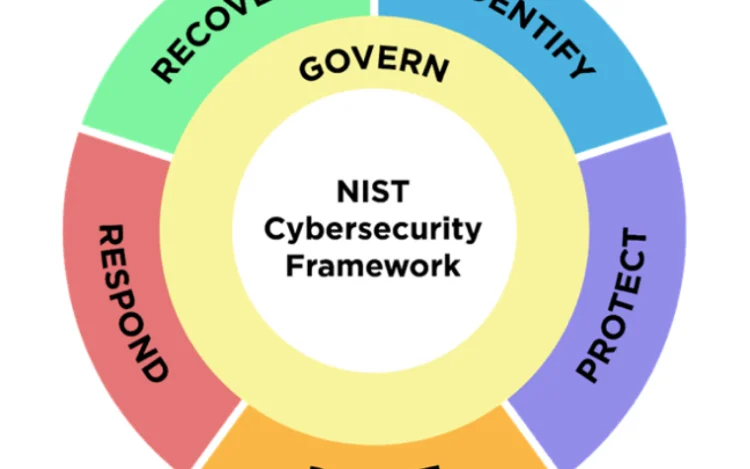
Managing cybersecurity risks requires a clear strategy combining people, processes, tools, and knowledge, all guided[…]
OWASP Software Assurance Maturity Model (SAMM) is one of the only comprehensive frameworks available for[…]
What is supplier risk management about? Outsourcing software development has become a cornerstone for many[…]
Introduction to software security requirements Despite clearly understanding the importance of security requirements, organizations seem[…]
Cybersecurity in general and application security (AppSec) in particular are extremely challenging topics. They run[…]
Application security requires a systematic approach and requires dealing with software security throughout every stage[…]
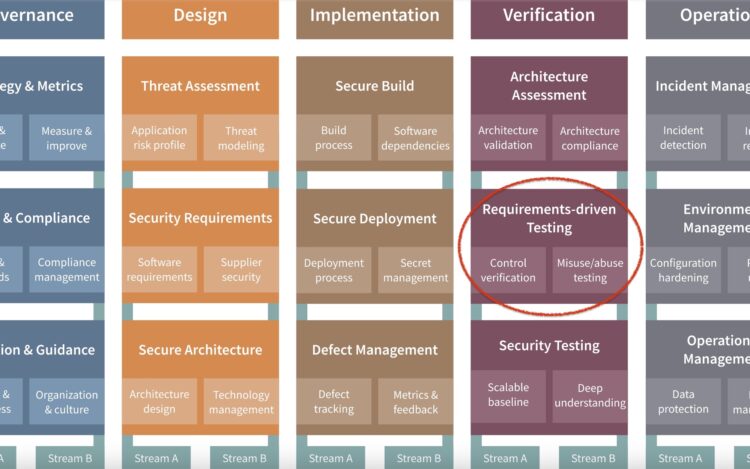
Security verification is about validating that a system or application adheres to predefined security requirements[…]
Codific is proud to receive the renewal of the ISO 27001 audit certification. ISO 27001[…]