As software systems grow more complex, proving that they are secure has become as important […]
Finding vulnerabilities is not the hard part anymore. Every build and every pipeline produces a[…]
Your DevSecOps pipeline is fast, automated, and built to scale. But is security truly integrated,[…]
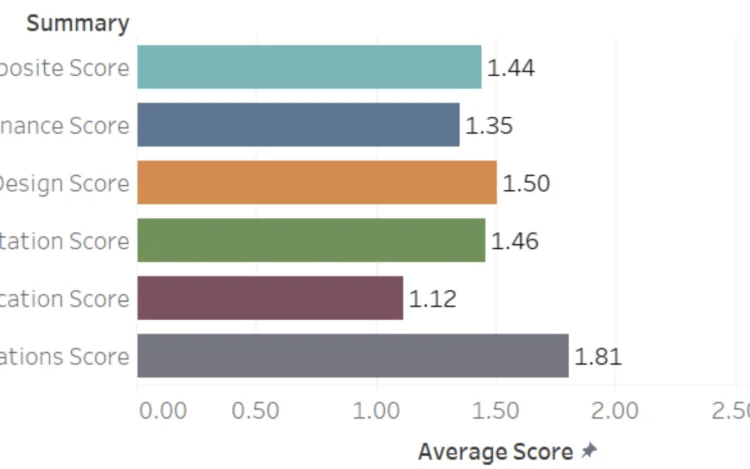
Over the past year, our SAMMY tool has grown significantly. It now supports not just[…]
OWASP Software Assurance Maturity Model (SAMM) is one of the only comprehensive frameworks available for[…]
What is supplier risk management about? Outsourcing software development has become a cornerstone for many[…]
Introduction to software security requirements Despite clearly understanding the importance of security requirements, organizations seem[…]
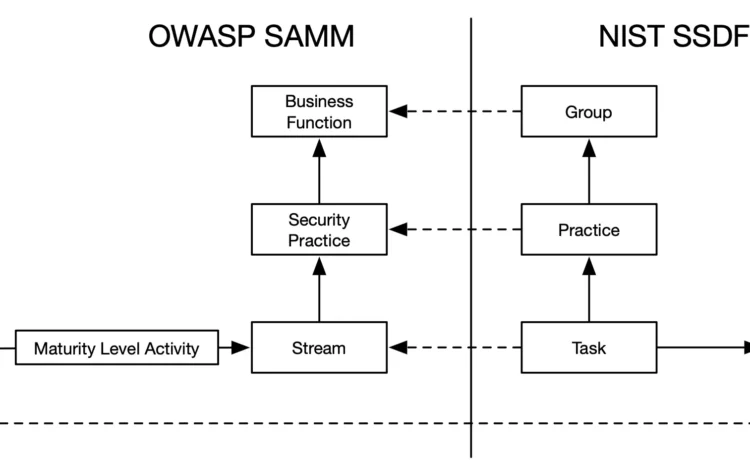
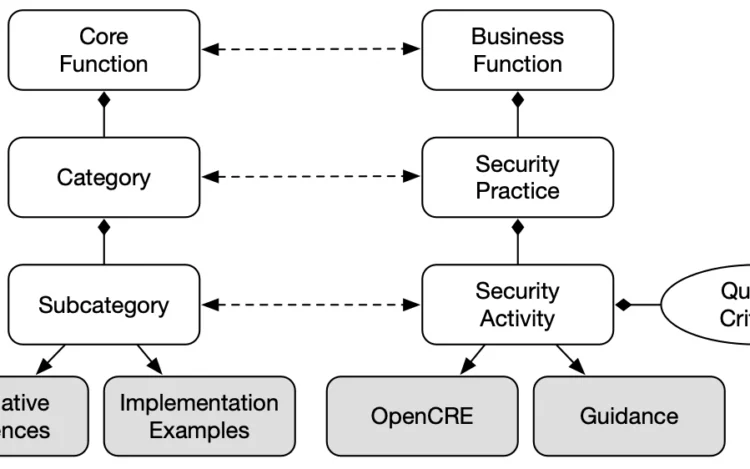
The OWASP Software Assurance Maturity Model (SAMM) is rapidly becoming the go-to framework for application[…]
Cybersecurity in general and application security (AppSec) in particular are extremely challenging topics. They run[…]
Want to get started with SAMM? We have just the thing! Take the free OWASP[…]
How to use OWASP SAMM for effective communication on security? Reporting with OWASP SAMM is[…]
NIST has finalized the Cybersecurity Framework (CSF) 2.0. CSF 2.0 focuses on understanding, assessing, prioritising,[…]