Updated: 13 February, 2025
11 April, 2022
The secure deployment of your software is a central piece in your secure software development life cycle.
In this blog series, we present how Codific implements OWASP SAMM. In each blog we focus on a specific security practice and highlight the processes and tools we use to achieve a certain maturity level. If you want to learn more about OWASP SAMM consider taking the free SAMM training.
Extract from the OWASP SAMM Training
Find out more about all the things the Codific team does at OWASP.
My journey in application security (AppSec) started almost 20 years ago at the DistriNet research lab of the University of Leuven. Back in the days secure software development was more of a hobby driven by a handful of experts. AppSec took its place under the spotlight with the release of Microsoft Security Development Lifecycle. However it was the Open Web Application Security Project (OWASP) that pushed secure software development into the mainstream. 2 decades later there are currently over 100 active OWASP projects that include code, software, reference material, documentation, tools and community all working to secure the world’s software. One of these projects is the Software Assurance Maturity Model (SAMM). SAMM is an open framework to help organizations formulate and implement a strategy for software security that is tailored to the specific risks facing the organization. SAMM is the map and the itinerary in your security journey.
Key takeaways
- Invest in automating your build process. Ideally, no human interaction should be necessary to run the build.
- Harden / secure your build tools. Ensure that only authorized users can modify the pipeline definition.
- Introduce a software composition analysis tool and make the pipeline fail if a high/critical vulnerability is found.
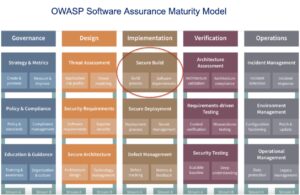
Implementing SAMM Secure Build
In this blog I will discuss how Codific implements the low hanging fruits in SAMM, namely the Secure Build practice. The Secure Build (SB) practice emphasises the importance of building software in a standardised, repeatable manner, and of doing so using secure components, including 3rd party software dependencies. SB consists of two streams:
- Build Process advocates fully automating the build process and adding automated security checks such as SAST and DAST to gain further assurance and flag security regressions early by failing the build, for example.
- Software Dependencies stream acknowledges the prevalence of software dependencies in modern applications. It aims to identify them and track their security status in order to contain the impact of their insecurity on an otherwise secure application.
Tools are instrumental in implementing both streams. One can also integrate easily most of these tools within the secure software development process. The tools we leverage are Gitlab CI/CD, SonarCloud, Debricked and SAMMY.
At the end of 2023 we had a look at our metrics from SonarCloud and we have realized that in a 12 month period the tool has not flagged a single true positive. From internal pen tests we know that there were a number of security issues. We would actually like to add some new rules to SonarCloud, however that is not possible with that tool. Hence, we will be dropping SonarCloud from 2024. We are still evaluating Semgrep and Snyk as alternatives to SonarCloud.
Secure Build -> Build Process
We leverage Gitlab’s CI/CD to automate most of our build processes. After approving a merge request in our code repository Gitlab’s CI/CD is automatically triggered and it starts by running in parallel both a SAST tool and a set of regression unit tests. SonarCloud analyses the source code and can detect a very broad spectrum of code quality issues. Depending on the severity of these issues SonarCloud can issue warnings or even fail the build pipeline. The regression unit tests include various security tests typically from the OWASP Top 10 Broken Access Control, Injection and Identification and Authentication Failures categories.
Extract from the OWASP SAMM Training
Secure Build -> Software Dependencies
Debricked is an SBOM / SCA tool that creates a list of dependencies used by the web application we are developing. We have integrated Debricked in our CI/CD pipeline as well. Vulnerabilities having a high score fail the build pipeline. In addition to security vulnerabilities, Debricked also analyses the dependencies for license risks.
Extract from the OWASP SAMM Training
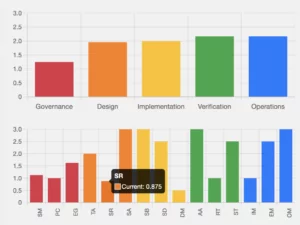
Manage your SAMM using the SAMMY tool
Codific has developed SAMMY that is a SAMM management tool. We use SAMMY to manage our SAMM posture and plan the improvements in term of application security.
Summary
In this blog we have presented how Codific implements the Secure Build practice. Secure Build is relatively easy to implement if you are developing web applications. It largely boils down to using the right set of tools. We leverage the Gitlab CI/CD, SonarCloud, Debricked to tackle both Secure Build streams. We also leverage SAMMY – our own SAMM management tool – to track each security practice in a systematic way.
What are the things we build with SAMM and SAMMY?
Codific is a team of security software engineers that leverage privacy by design principles to build secure cloud solutions. We build applications in different verticals such as HR-tech, Ed-Tech and Med-Tech. Secure collaboration and secure sharing are at the core of our solutions.
Videolab is used by top universities, academies and hospitals to put the care in healthcare. Communication skills, empathy and other soft skills are trained by sharing patient interviews recordings for feedback.
Top HR-Consultants leverage SARA to deliver team assessments, psychometric tests, 360 degree feedback, cultural analysis and other analytical HR tools.
SAMMY Is a Software Assurance Maturity Model management tool. It helps your organization assess and improve its security posture. That way other companies can help us build a simple and safe digital future. And we off course use it ourselves in all our application, including SAMMY.
We believe in collaboration and open innovation, we would love to hear about your projects and see how we can contribute in developing secure software and privacy by design architecture. Contact us.
Published April 2022, updated December 2023



