Your Guide to OWASP SAMM: Insights and Best Practices
The OWASP Software Assurance Maturity Model (SAMM) is a powerful tool for improving software security practices. It provides clear steps and a structured approach, enabling teams to assess their current security posture and build better strategies. Our OWASP SAMM Guidance page is here to help you make the most of this framework. It includes practical tips, expert advice, and useful resources to guide you through implementing OWASP SAMM in your organization.
Claude Code Security: Will AI Disrupt Application Security?
24 February, 2026 Everyone can now write code with Claude and get to production in a weekend. So we have solved the coding challenges. Time to fire the tech team. As of last week, Claude Code Security has also supposedly solved the application security challenges. There goes the AppSec team as well. Right? Neither idea holds. LLMs can write code, and they can do it quite well. But they tend to amplify rather than replace. As a newcomer, you can build a nice-looking hobby project over a weekend and maybe even take it somewhere. But as the codebase grows, you will likely end up in a complex mess. Strong engineers are gaining productivity with LLMs. Juniors can now turn a project into spaghetti at impressive speed. But let’s set the spaghetti aside. Who cares if AI manages it all, right? Not quite. The more pressing issue is security. AI is […]
OWASP Top 10 2025 – what it is, what changed, and what to do with it
13 December, 2025 If you build or look after web applications, you have probably bumped into the OWASP Top 10 at some point. It is a short, well known list of the most critical web application security risks, and many teams use it as a simple starting point for secure coding and testing. Today the project page lists both the stable 2021 edition and a 2025 release candidate. The new version reshapes the categories to reflect how modern applications are built and attacked, with more focus on themes like software supply chain issues and error handling. This blog explains how the Top 10 is built, what changed in the 2025 update, when to use it, when not to, and how to connect it with broader OWASP projects such as SAMM, ASVS and DSOMM to build a real application security program. What is OWASP and what is the OWASP Top 10[…]
OWASP ASVS: A Comprehensive Overview
25 November, 2025 As software systems grow more complex, proving that they are secure has become as important as making them work. Many organizations rely on multiple frameworks to guide development and compliance, yet few provide a clear, testable way to measure application security itself. This is where the OWASP Application Security Verification Standard (ASVS) stands out. ASVS defines what to verify in an application to demonstrate real assurance. It gives development and security teams a framework for building, testing, and maintaining secure software, supported by measurable requirements instead of abstract principles. In this article, we’ll explore what ASVS is, how version 5.0 modernizes the framework, and how it fits alongside frameworks like OWASP SAMM, NIST 800-53, and CIS Controls. You’ll also see how tools such as SAMMY make ASVS implementation practical. Key Takeaways OWASP ASVS gives a clear, shared set of security requirements so teams know exactly what[…]
Automated Application Security Testing with OWASP SAMM and SOOS
24 October, 2025 Automated Application Security Testing (AAST) refers to the use of software tools to identify vulnerabilities in applications with minimal human intervention. These tools continuously scan source code, dependencies, and running applications to detect flaws that could be exploited by attackers. By automating repetitive testing tasks, security and development teams can maintain coverage and consistency across every build and release. Automated testing can occur at different stages of the software development lifecycle. Static Application Security Testing (SAST) analyzes source code before it runs. Dynamic Application Security Testing (DAST) evaluates running applications in real time. Interactive Application Security Testing (IAST) combines both approaches. Software Composition Analysis (SCA) scans all software components, including open-source, proprietary, and internal libraries, and in modern platforms extends to container and SBOM analysis for complete visibility. Automation allows organizations to keep pace with agile and DevOps development cycles by embedding security directly into CI/CD pipelines[…]
Secure Code Training with Secure Code Warrior
Updated: 30 September, 2025 24 September, 2025 Developers are under pressure to deliver fast, but often without the tools to build securely. As vulnerabilities slip through, the need for practical, hands-on secure code training becomes clear. That’s where secure code training comes in. Whether you’re building web apps, APIs, or embedded systems, the people writing the code are your first line of defense. Equipping them with practical, role-specific skills is one of the most effective ways to reduce software risk early. We’ll break down what secure code training is, why it’s essential for modern development teams, and how to do it right. We also look at how Secure Code Warrior supports secure code training in practice. While SCW delivers the training experience, our SAMMY platform helps organizations track maturity and progress, shifting from checkbox compliance toward a culture of security, training, and awareness. What is secure code training? Secure code[…]
Top Application Security Failures in Fortune 500 Companies
Updated: 1 December, 2025 20 September, 2025 Application security (AppSec) remains one of the toughest challenges modern organizations are facing. Despite heavy investments and the adoption of frameworks like OWASP SAMM, OWASP DSOMM, and BSIMM, many companies struggle to make meaningful progress. Teams keep on patching and mitigating vulnerabilities, yet the backlog keeps growing. But why is that? We have massive knowledge basis, AI-powered tools, and widespread training programs. What’s going wrong? Are we making some small mistakes here and there or are we focusing on the wrong things entirely? Over the past three years, I’ve worked alongside several OWASP SAMM core team members to conduct structured evaluations across several organizations. We have seen the same critical issues across most of them. Most mistakes boil down to two root causes. First, tools alone do not solve problems, they create some. Their purpose is to support people and processes, not replace[…]
How to Implement Security Defect Tracking with OWASP SAMM and DefectDojo
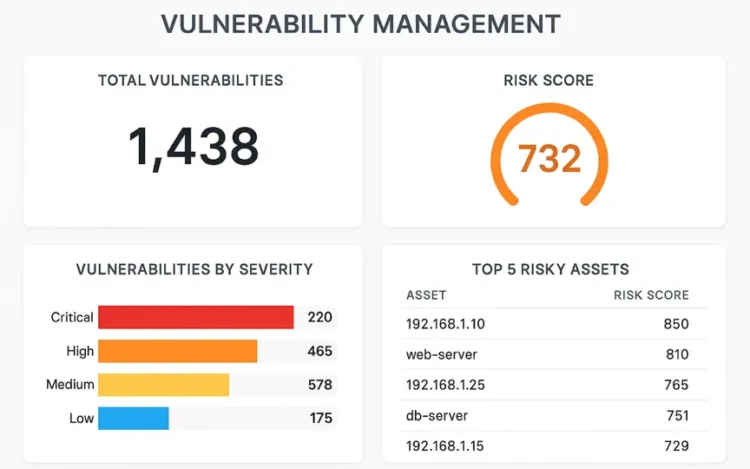
Updated: 24 September, 2025 28 August, 2025 Finding vulnerabilities is not the hard part anymore. Every build and every pipeline produces a flood of scanner results. The real challenge is turning that flood into a focused set of security defects that actually get fixed. That is where security defect tracking comes in. Before tracking can work, teams need strong vulnerability management. This means taking raw findings from many tools and turning them into something usable by aggregating, normalizing, removing duplicates, and triaging by risk and context. This produces a confirmed set of vulnerabilities that require remediation. Those items become security defects and move into issue tracking in tools such as Jira for fixing. DefectDojo excels at this stage. It aggregates findings across your stack, normalizes vulnerabilities, deduplicates them, supports triage and then hands off to your issue tracker. In this post we start with what defect tracking is, explain why[…]
OWASP DSOMM: A Comprehensive Introduction
Updated: 1 December, 2025 30 July, 2025 Your DevSecOps pipeline is fast, automated, and built to scale. But is security truly integrated, or just assumed? The OWASP DevSecOps Maturity Model (DSOMM) helps teams answer that question with clarity and structure. DSOMM provides a way to assess how well your security practices align with the way your teams actually build and operate software. It helps identify blind spots, track progress, and support consistent improvement. In this post, we will explore how the model works, how it compares to other maturity frameworks, and how you can begin applying it to improve security across your DevSecOps workflows. For those looking to operationalize DSOMM assessments, we also introduce SAMMY, a platform built for maturity tracking and team collaboration. Listen to the summary of this article on The AppSec Management Podcast: Key Takeaways DSOMM is a maturity model focused on integrating security directly[…]
DSOMM vs SAMM
Updated: 1 December, 2025 29 July, 2025 About 4 years ago I have joined the OWASP Software Assurance Maturity Model (SAMM) project as a core team member. Ever since I have been regularly coming across the OWASP DevSecOps Maturity Model (DSOMM). It seems that many people have the impression that SAMM is at odds vs DSOMM. But is that so? What are the key differences between the two frameworks? Who are the key stakeholders in the context of these frameworks? Which framework shall you pick as an organization? In this blog, I will dive deep into the key differences of the two frameworks. I have been coming across so much AI-generated noise lately that I am officially allergic to it. It is also very clear that AI can never figure out these insights on its own without some serious prompting. So I have decided to keep AI out of this.[…]
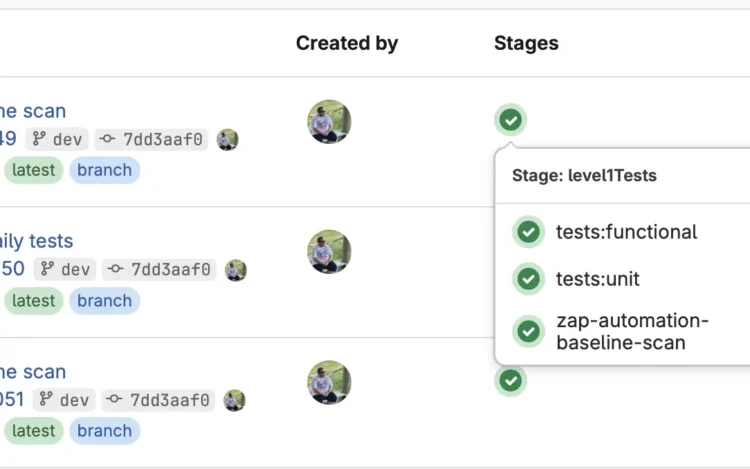
How to integrate Checkmarx ZAP in GitLab
Updated: 7 October, 2025 17 July, 2025 In this technical article, we will explore how to improve your DevSecOps processes by integrating Checkmarx ZAP in your GitLab’s CI/CD pipeline. Note that doing this for Github is largely similar with Github actions. Application security is becoming a priority on a worldwide scale. Both the US (NIST SSDF and Memorandum M-22-18) and the EU (CRA) have recently introduced legislations to aim at high common level of application security and cybersecurity. Meanwhile, the application security state-of-the-practice in large and small firms is far from ideal (to put it mildly). The attack sophistication and absolute numbers are increasing. Paradoxically, we have known the systematic solution to the security challenge. We (the actual security experts) name it a secure software development lifecycle or an AppSec program. There are several AppSec programs out there (NIST SSDF, Microsoft SDLC, BSIMM, etc) with OWASP SAMM being by far the simplest one[…]
What Is the SSDLC? A Guide to Secure Development
Updated: 24 September, 2025 11 June, 2025 Most security issues in software stem from one simple problem: teams try to fix them too late. The Secure Software Development Lifecycle (SSDLC) changes that by bringing security into each phase of development, not just the end. In this article, we explain what the SSDLC is, why it matters, and how to make it work in practice using clear steps and proven frameworks. Key takeaways The Secure Software Development Lifecycle (SSDLC) is a practical approach to embedding security into every phase of software development. Implementing the SSDLC helps teams reduce risk, improve software quality, and address vulnerabilities earlier and more effectively. The SSDLC includes seven key phases, from planning and analysis to maintenance, each requiring tailored security practices. OWASP SAMM offers a structured way to implement the SSDLC and is widely adopted by the security community. Supporting functions like governance and operations, while[…]
Master Dependency Management with SOOS and SAMM
Updated: 30 September, 2025 3 June, 2025 Dependency management has become one of the most critical aspects of modern software development. Third-party dependencies now make up the majority of most codebases. What once felt like the holy grail of software reuse in the early 2000s is now the default. That shift has fuelled faster development, but it also introduced a massive security problem. According to Verizon’s Data Breach Investigation Report from 2024 the number of breaches caused by third parties has increased 68% from 2023. That is surprising as we have tools to systematically scan applications for dependencies and flag known vulnerabilities. Software Composition Analysis (SCA) tools have become a commodity. Frankly, my team could build a basic SCA tool in a week. The real challenge lies elsewhere. You need the right people, mature processes and clear ownership. And you need tools that fit your workflow, not tools that force[…]
Why Choose OWASP SAMM?
Using OWASP SAMM can help you pinpoint weak spots in your software development process and uncover actionable ways to improve. This framework is structured to assess your current practices, provide clear benchmarks, and guide you toward a more secure development lifecycle. Furthermore, whether you’re just starting with OWASP SAMM or aiming to refine your existing approach, our OWASP SAMM Guidance delivers the tools and insights you need to succeed.
Unlock Additional Resources
Our guidance connects you to a wealth of additional resources. For example, these include best practices for secure design, development, and deployment. Moreover, internal links throughout this page will direct you to case studies, practical tips, and related articles. By exploring these, you can expand your knowledge and implement improvements step by step.
How SAMMY Supports OWASP SAMM
By focusing on OWASP SAMM Guidance, your team can build stronger, more secure software. Additionally, this framework works seamlessly with SAMMY, our innovative security software. SAMMY integrates OWASP SAMM principles to simplify security assessments and streamline the improvement process. Therefore, for organizations aiming to boost their security quickly and effectively, SAMMY is an invaluable tool.
Take the Next Step
Start your journey today and discover how OWASP SAMM and SAMMY can transform your development processes. With the right tools and guidance, you can ensure your software meets the highest security standards. Furthermore, dive into our related content to explore practical steps for integrating SAMMY into your OWASP SAMM journey. Together, these frameworks empower you to protect your software and strengthen your security posture.