Codific has grown out of a research team at DistriNet KU Leuven, one of the most renowned research labs in the academic security world, especially known for its research on threat modeling. At Codific we always look for the places where a profound analytical approach to abstract security principles meets practical implementation models in the industry. This led us to OWASP SAMM, the best system to measure, monitor and manage security processes at a software organization. So we decided to get involved in a variety of different ways…
Core contributors to OWASP SAMM
Several of our team members are core contributors to the OWASP SAMM project, with Aram Hovsepyan, our CEO, being a core team member in the project. Our team members are co-authors of the model and of all the documentation around it. This has grown out of an intrinsic belief in the model and a desire to contribute. Additionally the core contributors have gotten to know each other and many of them are now collaborators of Codific in different modalities.
Our team members continue to work on improving the project with the core team members getting together, at least once a year for a few days, to solve the hard problems in the project.
SAMMY Tool
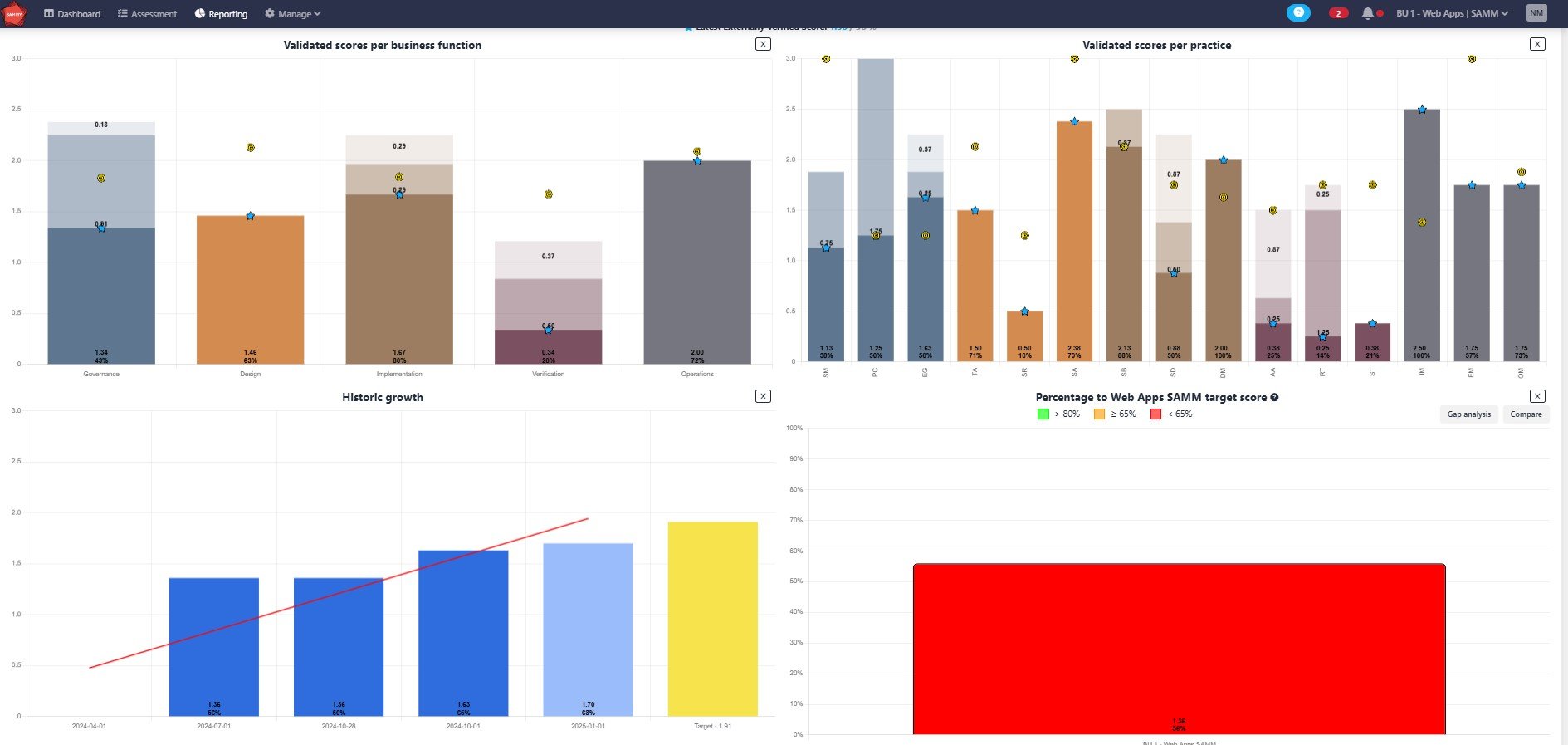
SAMMY started as an internal tool to continuously use OWASP SAMM to monitor the security posture of all our teams. The tool divides the process into different roles to evaluate, validate and improve maturity using SAMM. The three steps, assessment, validation and improvement turn it into a circular process of continuous improvement. Soon other people wanted to use our tool and we now offer a free version that is widely used across the industry which you can find here.
Sharing the tool with others was a fantastic idea as it gave us great insights to improve it. Following feedback from our customers, implementation partners and internal teams we improved SAMMY in a variety of ways, ultimately also benefitting the OWASP SAMM Project, some of this include:
- Adding assessment models from NIST, ISO, IEC, and more organizations. As well as mappings between the different models.
- Adding target scopes that allow organizations to set their target maturity of the different SAMM practices for their different teams,
- Adding reports to visualize assessment results and visualize gaps.
And if all that wasn’t enough, we made SAMMY v2 open source, here is the link to the GitHub repository.
OWASP SAMM PDFs
In our HR-Tech tool called SARA we have built a versatile PDF engine that can quickly turn complex information into comprehensible PDFs. As there was a need for always up to date PDFs of the SAMM model we built an adapted engine for OWASP. This engine pulls all the latest information from online repositories and produces the PDF guide to the latest version of the model.
You can download the OWASP SAMM model 2.0 PDF here.
Model mappings
A lot of work has been done mapping OWASP SAMM to NIST and ISO standards, the idea is that having done a SAMM assessment most of the legwork towards other standards should be done and easily transferable. There is another OWASP project called OpenCRE, that enumerates common requirements between frameworks to make mapping between them easier. Our team contributes to the integration and collaboration with OpenCRE.
OWASP SAMM Fundamentals course
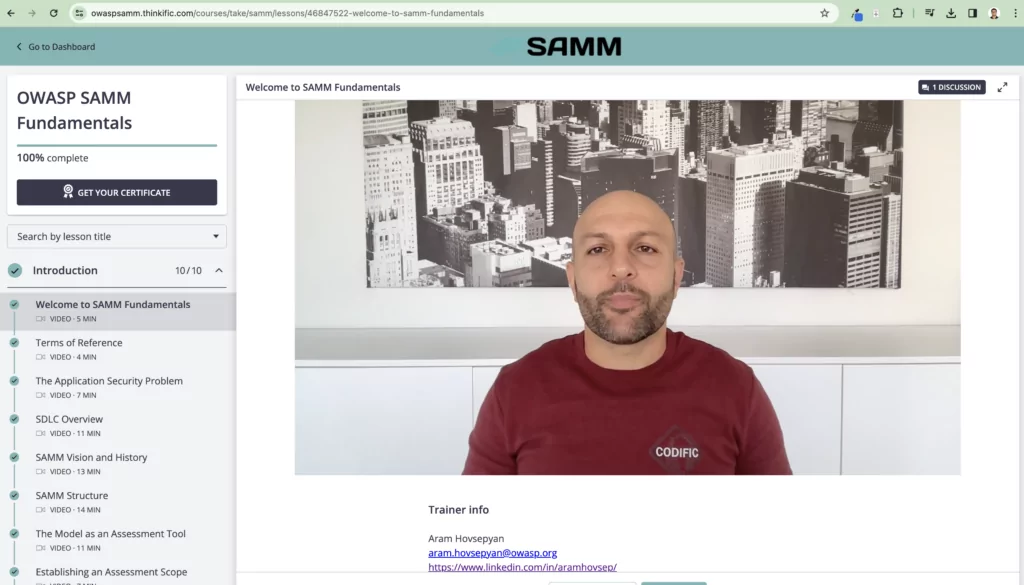
The Codific team, and especially Aram spent many hours creating the OWASP SAMM fundamentals course. The training consists of 79 lessons with a total of 5 hours of video content. It also includes two practical case studies to practice SAMM assessments. The instructor of the course is Aram.
Find out everything about the free OWASP SAMM training here.
The Benchmark project

Our team members also play a fundamental role in the SAMM Benchmarking initiative. We have set up the infrastructure to anonymously collect and aggregate data and are now fully in collection mode. Please feel free to donate data to the benchmark. Once we have robust benchmark data this will be made available and integrated into the SAMMY tool. Moreover, if you are interested in getting some in-depth insights about the benchmark, straight from Aram, then make sure to read this article.
Core Team Guidance
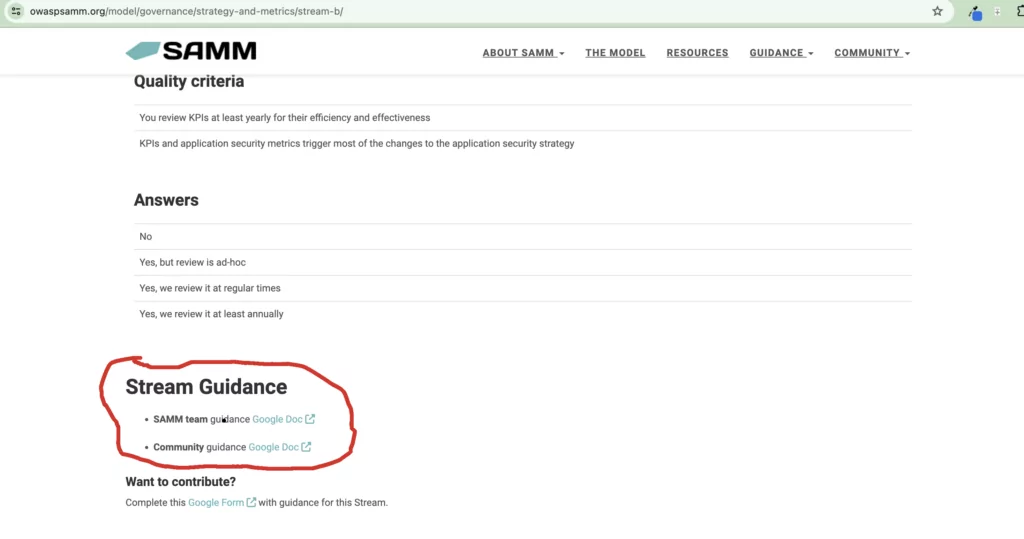
Around the SAMM model there is Core Team Guidance and Community Guidance. This guidance helps users with interpretation and implementation of each stream. The Codific team has written large parts of the core team guidance. The Community guidance is open to everyone, feel free to contribute.
You can find the guidance at the bottom of each stream.
Sponsorship
We also put our money where our mouth is. Codific is a “Gold Sponsor” (that is the highest level) of the project, providing financial support for the maintenance and further development of OWASP SAMM.
SAMM Content Creation
Our team recurrently publishes blog post articles that share valuable insights related to the SAMM model, the projects that relate to it and also wider insights from the field of AppSec. While this is not directly contributed to the OWASP SAMM website, we still believe this is a valuable contribution to the SAMM project as it drives attention to it and to the field of AppSec. Moreover, our team members have also contributed in video content creation. For example, Aram helped by moderating an incredibly insightful podcast on how to to carry out SAMM Assessments with his fellow colleagues, SAMM core team members and security experts, Brian Glas, Maxim Baele and Rob van der Veer. You can see this below:
Attending and speaking at OWASP Conferences
Last but not least, our team members and even our clients not only love attending OWASP Conferences but also speaking in them. In 2024 we attended both the Global AppSec Lisbon and San Francisco Conferences. In Lisbon, Aram delivered a talk about automating security test cases based on ASVS which he also delivered in San Francisco. You can find the recording of the talk below:
Moreover, one of our beloved clients, Dr. Jasyn Voshell, delivered a talk about maturing SDLC at a Fortune 500 company. The company in question being the company he works for, Zebra Technologies, which is one of the main enterprise users of our SAMMY Tool. You can check out Jasyn’s talk below and also if you are interested you can learn more about how SAMM was used to mature the SDLC in this article written by Aram.
Additionally, at San Francisco, Dimitar Raichev, one of our secure software engineers delivered a talk on how to harness OpenCRE for effective mapping between different frameworks. Finally, our Chief Growth Officer also delivered talks both in Lisbon and San Francisco, during the SAMM User Days about how to influence boardroom strategy, using OWASP SAMM as a communication tool.
