Introduction to software security requirements Despite clearly understanding the importance of security requirements, organizations seem […]
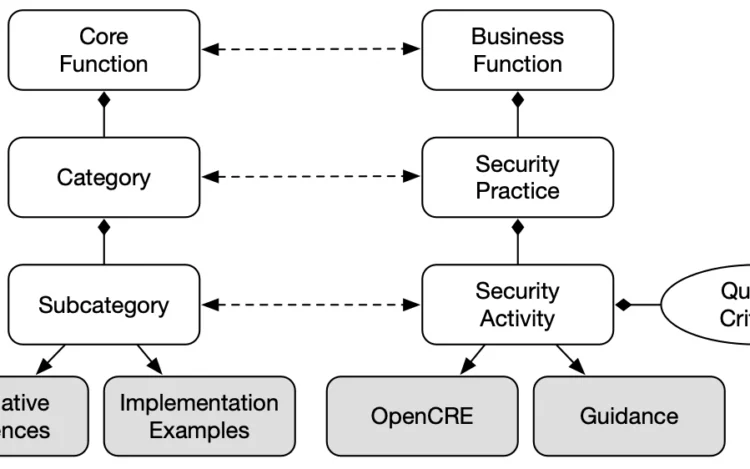
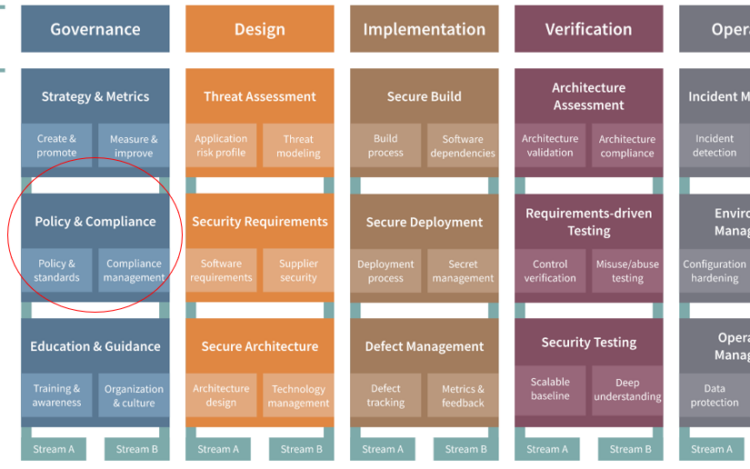
The OWASP Software Assurance Maturity Model (SAMM) is rapidly becoming the go-to framework for application[…]
It this article we explore the essentials of the EU Cyber Resilience Act (CRA), and[…]
Want to get started with SAMM? We have just the thing! Take the free OWASP[…]
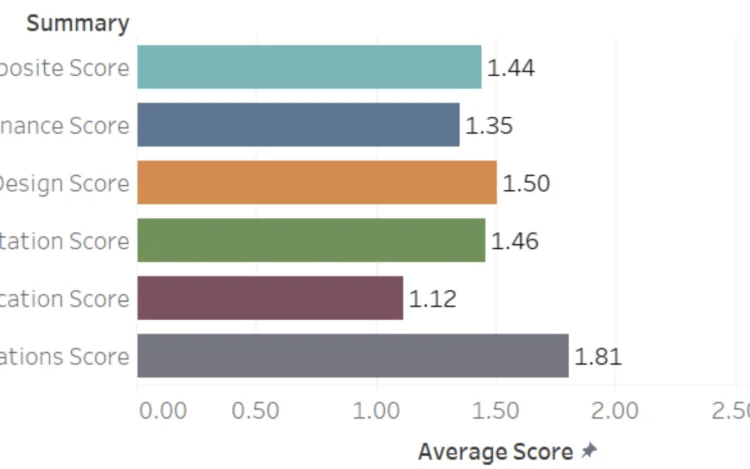
How to use OWASP SAMM for effective communication on security? Reporting with OWASP SAMM is[…]
Application security is a paramount concern for organizations that develop software. However systematically managing AppSec[…]
Application security requires a systematic approach and requires dealing with software security throughout every stage[…]
Official resources ISO 27001:2022 ISO 27001:2013 OWASP SAMM CRA NIST SSDF
NIST has finalized the Cybersecurity Framework (CSF) 2.0. CSF 2.0 focuses on understanding, assessing, prioritising,[…]
Is SOC 2 Worth It? In this blogpost we will be discussing SOC 2, what[…]
Is ISO 27001 worth it? In this blogpost we will be discussing ISO 27001. What[…]
OWASP is the Open Worldwide Application Security Project. It is a non-profit foundation that works[…]