Dear disgruntled employee (let’s call you Mallory): Tired of working long hours with no holidays, […]
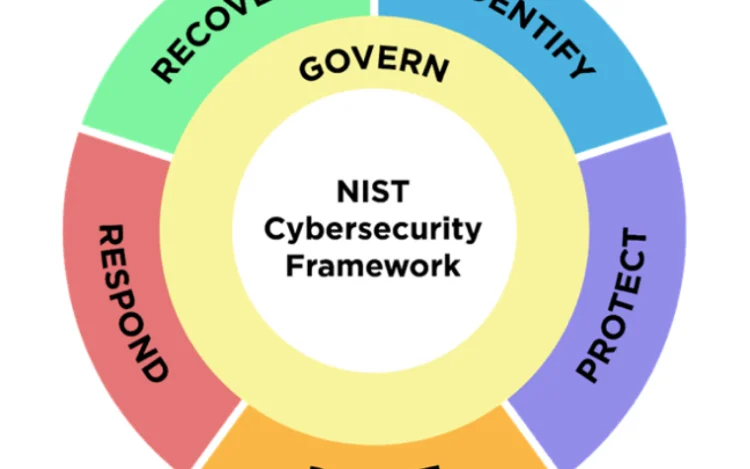
Navigating the complexities of cybersecurity frameworks can be challenging, but understanding how to implement NIST[…]
In the evolving landscape of cybersecurity, organizations face the challenge of protecting their systems and[…]
Implementing ISO 27001 is crucial for organisations looking to protect sensitive information and ensure compliance[…]
HIPAA, the Health Insurance Portability and Accountability Act of 1996, is a critical federal law[…]
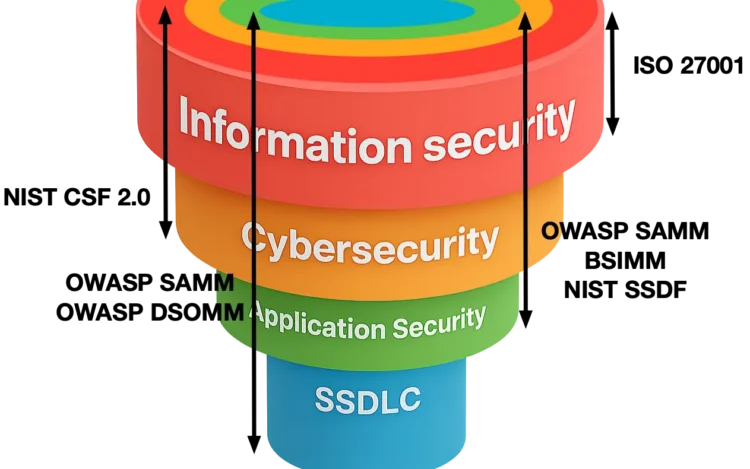
The terms information security and cybersecurity are often used interchangeably, which frequently leads to confusion.[…]
The U.S. cybersecurity strategy seems to be lightyears ahead of the EU. I strongly believe[…]
Application security is a complex discipline. To make things even harder for us, it is[…]
What is FISMA and why is it important? The Federal Information Security Modernization Act (FISMA)[…]
Managing cybersecurity risks requires a clear strategy combining people, processes, tools, and knowledge, all guided[…]
OWASP Software Assurance Maturity Model (SAMM) is one of the only comprehensive frameworks available for[…]
What is supplier risk management about? Outsourcing software development has become a cornerstone for many[…]