Updated: 2 September, 2025
29 November, 2024
Application security is a complex discipline. To make things even harder for us, it is a moving target as the threat landscape shifts. Roughly a decade ago there was no Slack, no Teams, no Docker, no Kubernetes, no Github actions, no supply chain risk, no ransomware, no ChatGPT. In this ever-evolving world, security frameworks are the only systematic answer to guide organizations in achieving robust software development lifecycles (SDLCs). One such model, the Building Security In Maturity Model (BSIMM), has garnered attention for its unique data-driven approach. But how does BSIMM work, and why should organizations care? How does it compare to other frameworks, and what are its strengths and limitations? These are the questions we’ll answer in this comprehensive guide.
In this article, we’ll break down everything you need to know about BSIMM. We’ll start by explaining what BSIMM is, who created it, and who uses it. Next, we’ll explore why it’s important, followed by its advantages and disadvantages. We’ll also discuss alternative models that might better suit specific needs. Finally, we’ll examine how SAMMY, an innovative tool for managing AppSec programs, can complement frameworks like BSIMM, SAMM and NIST SSDF. By the end, you’ll have a clear understanding of whether BSIMM is the right fit for your organization and how it fits into the broader landscape of application security.
What is BSIMM?
The Building Security In Maturity Model (BSIMM) is a framework designed to help organizations measure and improve their software security initiatives. Unlike prescriptive models that provide a list of tasks to implement, BSIMM is descriptive, it is built by studying real-world practices used by hundreds of organizations across various industries.
BSIMM focuses on understanding what successful organizations are actually doing to secure their software. It provides a comprehensive set of activities grouped into specific domains that serve as a benchmark. By comparing their own security practices against these observations, organizations can identify gaps, prioritize improvements, and align their efforts with proven industry practices.
Who created BSIMM and when?
Let me give you a bit of a history lesson… Back in 2008, the OpenSAMM Beta version was released, whose development was led by Pravir Chandra. OpenSAMM is a free, open-source community-driven framework that later became OWASP SAMM when it was donated to the OWASP Community in 2009 (although the original OpenSAMM framework still exists as SAMM 1.0) . The OpenSAMM Beta was funded by Fortify which was a company founded by Brian Chess.
After the release of OpenSAMM Beta, Gary McGraw and Sammy Migues, together with another group of people from Cigital wanted to get involved with OpenSAMM. However, their vision for the framework deferred from that of Pravir as they sought to give it a more commercial nature rather than the open-source nature Pravir wanted to conserve. Therefore, both efforts forked and in 2009, BSIMM1 was released, which was based on the OpenSAMM Beta combined with the findings of a study of 9 big software companies. The three main co-authors were Gary McGraw, Sammy Migues and Brian Chess.
Since then, both the OpenSAMM and BSIMM frameworks followed distinct paths. OpenSAMM, became OWASP SAMM and stayed true to its open-source roots. It remains a free, community-driven framework, continually updated to align with modern software security needs. BSIMM, on the other hand, became a commercially licensed model. It built on OpenSAMM’s foundation by emphasizing data-driven insights derived from real-world practices across hundreds of organizations.
The split allowed OWASP SAMM to serve as a free resource for organizations of all sizes, while BSIMM focused on providing in-depth data and tailored guidance as part of a paid framework. Both models ultimately share the same goal of advancing application security maturity, but they take different approaches to achieve it. Below a table that summarizes the main differences between the models.
Main differences between OpenSAMM, BSIMM and OWASP SAMM
| Model | OpenSAMM | BSIMM | OWASP SAMM |
| Model Type | Open Framework | Descriptive Observational Model | Prescriptive Framework |
| Current Version | 1 | 15 | 2 |
| Focus Area | Software Assurance | Software Security Initiatives (SSI) | Software Security Assurance |
| Licensing | Open Source (Creative Commons Attribution-ShareAlike 3.0) | Commercial | Open Source (OWASP Foundation) |
| Structure | 12 Security Practices across 4 Business Functions | 12 Practices across 4 Domains (Governance, Intelligence, SDLC Touchpoints, Deployment) | 15 Security Practices across 5 Business Functions |
| Maturity Levels | 3 Levels | 3 Levels (observed practices) | 3 Levels |
| Primary Use Case | Assessment and Improvement of Security Practices | Benchmarking and Comparison | Planning and Maturing Security Programs |
| Community Involvement | High, community-driven via OWASP | Low, proprietary updates by Synopsys | High, open contributions via OWASP |
How Does BSIMM Work?
The Building Security In Maturity Model (BSIMM) operates as an observational framework designed to evaluate and improve an organization’s software security initiatives. At its core, BSIMM defines a Software Security Framework (SSF) of 12 practices across four domains. These domains represent the critical areas of focus for developing a robust software security program:
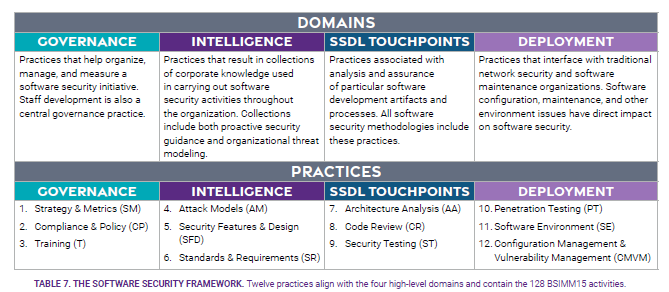
1. Governance
This domain focuses on practices that help organize, manage, and measure a software security initiative (SSI). It establishes the structural and procedural foundations needed for success. Governance practices typically include defining roles and responsibilities, creating policies, and monitoring security progress across the organization.
2. Intelligence
Intelligence involves building a collection of corporate knowledge that informs and supports software security activities. This includes practices like identifying security risks, maintaining threat intelligence, and creating internal standards and guidelines to ensure consistent application of security measures throughout the organization.
3. SSDL Touchpoints
This domain addresses activities related to the Software Security Development Lifecycle (SSDL). The practices here are focused on analyzing and ensuring the security of development artifacts and processes. Examples include performing static and dynamic analysis, implementing secure code reviews, and testing for vulnerabilities in applications.
4. Deployment
Deployment practices bridge the gap between software security and traditional network security or maintenance teams. This domain focuses on ensuring that software is deployed securely and that any vulnerabilities in production are managed effectively. Activities include incident response planning, operational monitoring, and integrating application security with deployment pipelines.
Who uses BSIMM?
BSIMM is widely adopted by organizations seeking to benchmark and enhance their software security practices. Its user base spans multiple industries, including finance, healthcare, technology, retail, and telecommunications, reflecting the growing need for robust software security across diverse sectors. Some notable examples of companies that use BSIMM include Lenovo, Bank of America and Johnson & Johnson.
The framework is particularly popular among large enterprises with mature software development lifecycles (SDLCs) that require tailored and data-driven insights. These organizations leverage BSIMM to measure the effectiveness of their security initiatives against industry benchmarks and to identify areas for improvement.
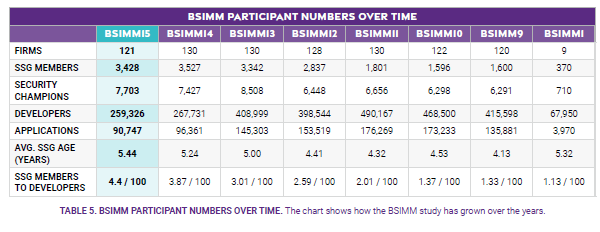
The table above highlights how BSIMM is predominantly used by mature organizations. In the latest BSIMM 15 release, the SSG per Developers ratio, a metric that reflects the number of security champions relative to developers, reached 4.5 for every 100 developers, indicating highly mature SDLCs. Another noteworthy observation is the relatively stagnant number of participating organizations since the release of BSIMM 11 in 2020, with BSIMM 15 having 121 organizations as compared to 130 in BSIMM 14. This suggests that BSIMM’s adoption has plateaued over the last few years and is even beginning to decrease.
Consultancies and security service providers also use BSIMM to guide their clients in building or refining their software security programs. Additionally, BSIMM’s commercial nature makes it a tool of choice for companies with sufficient resources to invest in proprietary solutions, as it provides access to detailed metrics, expert analysis, and regular updates.
While BSIMM is designed for organizations that are already invested in software security, its reliance on real-world observations makes it a valuable resource for any enterprise aiming to align its practices with proven methods adopted by industry leaders.
Why is BSIMM important?
BSIMM plays an important role in helping organizations advance their software security initiatives by offering a real-world, data-driven approach to measuring and improving security maturity. Its importance stems from several key factors:
- Benchmarking Against Industry Leaders: BSIMM is based on practices observed in hundreds of successful organizations. This allows companies to compare their software security efforts against proven benchmarks and identify areas for improvement.
- Focus on Practical Implementation: Unlike theoretical frameworks, BSIMM is rooted in actual practices, making it highly actionable. It outlines specific activities that organizations can adopt to align with industry standards.
- Insightful Metrics for Decision-Making: BSIMM provides organizations with detailed metrics and trends across industries, offering valuable insights for making informed decisions about where to focus security investments.
- Guidance for Program Evolution: As a maturity model, BSIMM doesn’t prescribe a one-size-fits-all approach. Instead, it helps organizations understand where they stand and how to strategically advance their software security programs over time.
- Adaptable to Different Industries: With data gathered from various sectors, BSIMM offers guidance that can be tailored to the unique needs and challenges of specific industries, ensuring its relevance across diverse organizational contexts.
In essence, BSIMM is important because it bridges the gap between theory and practice, providing a clear, evidence-based roadmap for improving software security. Its emphasis on what organizations are actually doing—and succeeding with—makes it a valuable tool for aligning efforts with real-world success stories.
What are the main advantages of BSIMM?
BSIMM offers several distinct advantages that make it a valuable tool for organizations aiming to enhance their software security initiatives:
- Data-Driven Insights:
BSIMM is based on real-world observations from hundreds of organizations, providing an evidence-based framework. This makes it uniquely reliable for benchmarking and improving security practices. - Tailored Benchmarking:
By analyzing data from organizations across various industries, BSIMM allows users to compare their own software security programs to peers in their sector or against industry leaders. This helps in identifying specific gaps and improvement opportunities. - Actionable Guidance:
Instead of prescribing theoretical solutions, BSIMM focuses on activities that have been successfully implemented by other organizations. This makes the framework practical and results-oriented. - Comprehensive Coverage:
BSIMM encompasses a wide range of software security domains, including governance, training, testing, and deployment. This ensures that organizations address security holistically rather than in isolated silos. - Support for Maturity Growth:
BSIMM helps organizations assess their current maturity level and provides a clear roadmap for progressing. This incremental approach ensures continuous improvement without overwhelming the organization. - Industry Trends and Expertise:
As a commercial framework, BSIMM benefits from regular updates and ongoing analysis by experts. Organizations gain access to the latest industry trends and best practices, keeping their programs up-to-date. - Flexibility Across Industries:
With its vast dataset drawn from different sectors, BSIMM can be adapted to meet the specific needs of various industries, ensuring its relevance and applicability regardless of organizational focus.
By combining real-world data, practical guidance, and the ability to benchmark against industry leaders, BSIMM empowers organizations to make informed decisions and strategically improve their software security practices.
What are the main disadvantages of BSIMM?
While BSIMM provides significant value as a benchmarking tool for software security, it has several limitations that organizations should carefully consider before adopting it. These drawbacks can impact its suitability for smaller or less mature organizations. Below are the main disadvantages of BSIMM:
- Commercial Licensing Costs
Unlike open-source models like OWASP SAMM, BSIMM requires a paid subscription, creating barriers for smaller organizations with limited budgets. - Descriptive Rather than Prescriptive
As a descriptive model, BSIMM documents what successful organizations do but doesn’t prescribe steps to follow. This can leave less mature organizations uncertain about where to begin. While consultancy support is available, it often comes at a high cost. - Focus on Large, Mature Organizations
BSIMM is designed around practices observed in established enterprises. Smaller companies or those new to software security may find its recommendations less applicable and cost-prohibitive. - Limited Customization
BSIMM’s standardized approach doesn’t always align with the unique cultural or operational needs of every organization, making implementation more challenging. - Dependence on Observational Data
Since BSIMM relies on data from participating organizations, its findings may not reflect emerging or innovative security practices. - Steep Learning Curve
Interpreting BSIMM data and converting it into actionable strategies often requires expertise in software security, which some organizations may lack. - Commercial Nature
As a proprietary framework, BSIMM lacks the community-driven collaboration and transparency of open-source models like OWASP SAMM, limiting user influence on its evolution.
Although BSIMM is a powerful benchmarking tool, these drawbacks emphasize the importance of assessing its fit with an organization’s resources, maturity, and goals. For many, open-source options or hybrid approaches may be more practical.
What are Alternative Models to BSIMM?
While BSIMM is a valuable tool for benchmarking and improving software security, other models offer alternative approaches that may better suit specific organizational needs. Two notable frameworks are OWASP SAMM and NIST SSDF. Below, we compare these models to BSIMM.
Main differences between BSIMM, OWASP SAMM and NIST SSDF
| Aspect | BSIMM | OWASP SAMM | NIST SSDF |
| Model Type | Descriptive Observational Model | Prescriptive Framework | Prescriptive High-level Framework |
| Licensing | Commercial | Open Source | Public Domain |
| Approach | Descriptive: Documents observed practices | Prescriptive: Provides actionable steps | Prescriptive: Recommends practices and outcomes |
| Focus Area | Software Security Initiatives (SSI) | Software Security Assurance | Secure Software Development Lifecycle (SDLC) |
| Target Audience | Mature organizations | Organizations at all maturity levels | Universal (all sizes and industries) |
| Cost | Paid | Free | Free |
| Community Involvement | Low (Proprietary) | High (Community-driven) | Moderate (Government-backed) |
OWASP SAMM
The Software Assurance Maturity Model (SAMM), maintained by the OWASP Foundation, is a free, open-source framework designed to help organizations develop and improve their software security practices. SAMM breaks down security into detailed streams across five business functions: governance, design, implementation, verification, and operations. Its structure includes prescriptive guidance and clear maturity levels, making it both flexible and actionable.
Similarities with BSIMM:
- Both focus on improving software security maturity.
- They provide measurable activities that organizations can use to benchmark and enhance security practices.
- Both are adaptable across industries and organizational sizes.
Differences with BSIMM:
- Open-Source Advantage: SAMM is entirely free and maintained by a vibrant community, while BSIMM is a commercial, proprietary framework requiring paid access.
- Prescriptive Guidance: SAMM offers clear, actionable steps for improving security practices, whereas BSIMM is descriptive, focusing on documenting what successful organizations already do.
- Accessibility for All Sizes: SAMM is designed to be accessible to organizations at all maturity levels, from small startups to large enterprises, while BSIMM tends to cater to already mature organizations.
- Community-Driven Updates: SAMM evolves based on input from the global OWASP community, making it highly responsive to emerging security trends.
Is SAMM Better Than BSIMM?
For most organizations, especially those in the early to mid-stages of building their security programs, SAMM offers significant advantages. Its prescriptive nature provides a clear roadmap for improvement, and its open-source model makes it accessible to any organization, regardless of budget. While BSIMM shines as a benchmarking tool for mature organizations, SAMM’s flexibility, cost-effectiveness, and actionable guidance make it the better choice for a wider range of use cases, even those of mature organizations.
If you would like to learn more about the comparison of BSIMM vs SAMM then you can refer to this article.
NIST SSDF
The NIST Secure Software Development Framework (SSDF) Version 1.1 provides a high-level set of practices to ensure secure software development. Published by NIST, SSDF focuses on mitigating the risk of vulnerabilities during development and across the software lifecycle. Unlike BSIMM, which relies on observations, SSDF provides clear recommendations for integration into existing software development workflows.
Similarities with BSIMM:
- Both emphasize improving software security across the SDLC.
- Provide structured approaches to ensure security practices align with industry standards.
Differences from BSIMM:
- Broader Applicability: SSDF is designed for use by any organization, regardless of size, sector, or maturity, whereas BSIMM is tailored for mature organizations.
- Prescriptive Guidance: SSDF offers explicit practices for secure software development, whereas BSIMM is descriptive, focusing on what organizations already do.
- Free Access: SSDF is freely available and supported by NIST, making it a cost-effective choice compared to BSIMM’s paid model.
- Focus on Outcomes: SSDF defines clear outcomes for each practice without prescribing specific tools or methods, ensuring flexibility.
Is SSDF Better Than BSIMM? SSDF is ideal for organizations seeking a prescriptive framework with clear recommendations for integrating security into their development processes. While BSIMM is a robust tool for benchmarking existing practices in mature organizations, SSDF provides a more universally applicable framework for building secure software from the ground up. Organizations can benefit from using SSDF in combination with BSIMM for benchmarking or OWASP SAMM for detailed guidance.
If you would like to learn more about the comparison of NIST SSDF vs SAMM then you can refer to this article.
While BSIMM excels as a benchmarking tool, OWASP SAMM distinguishes itself as a more accessible and adaptable framework, particularly for organizations across varying maturity levels. When combined with broader frameworks like NIST SSDF, SAMM offers practical, cost-effective guidance for building and enhancing comprehensive software security programs.
Managing your SDLC AppSec program with SAMMY
Whether you choose to use BSIMM, SAMM, or NIST SSDF to guide your application security program, SAMMY is the ideal partner to help you implement and manage these frameworks effectively.
SAMMY is an innovative AppSec Program Management tool initially designed for OWASP SAMM. Recently, it has expanded to include support for BSIMM and NIST SSDF, making it a versatile solution for organizations following different security frameworks.
Why Use SAMMY for Your AppSec Program?

Here are the key advantages of using SAMMY:
- Free to Use: No cost to get started, making it accessible to organizations of any size.
- Team Collaboration: Work with your team to perform SAMM assessments and ensure alignment across stakeholders.
- Effortless Organization: Manage assessments and documentation in one place, streamlining your AppSec workflow.
- Automated Reporting: Generate detailed assessment and gap reports with just a few clicks.
- Framework Mapping: Map your assessments to multiple frameworks, including ISO, OWASP, NIST, IEC, and many more.
- Tool Integrations: Seamlessly integrate with tools you already use, such as JIRA, Confluence, and others.
Ready to Try SAMMY?
If you’re looking for a comprehensive and easy-to-use tool to manage your application security program, SAMMY is the solution.
What’s New in BSIMM 15?
The latest edition of the Building Security In Maturity Model, BSIMM 15, builds on the same foundation of twelve practices across four domains. But it also introduces key updates that reflect how software security is evolving in practice.
Here are the most important changes:
-
New activities added
BSIMM 15 includes two additional activities. One focuses on setting standards for adopting new technologies. The other addresses securing development endpoints. Both signal a stronger focus on innovation and developer environments. -
Increased focus on AI and adversarial testing
The use of adversarial testing has more than doubled. Around thirty percent more organizations now have dedicated teams researching new attack methods. This points to growing attention on threats related to AI and machine learning. -
Growth in supply chain security practices
There is a twenty-two percent increase in the adoption of Software Bills of Materials. Even more notably, Software Composition Analysis on code repositories is up by sixty-seven percent. This shows a clear push to manage open source risk earlier in the development process. -
Decline in basic security training
Only around half of the organizations surveyed still provide security awareness training. This is the lowest rate ever recorded in BSIMM and may be a warning sign for long-term cultural investment. -
A shift in how BSIMM is framed
BSIMM is now described as a Software Security Framework. The structure remains the same, but the updated terminology reflects how the model is used to benchmark and guide mature security programs.
These updates confirm that BSIMM continues to track the realities of secure software development, helping organizations understand where they stand and what comes next.