Easily manage your application security with SAMMY
SAMMY empowers organizations to efficiently manage their application security programs with comprehensive support for a variety of different maturity, program and compliance frameworks.
To further simplify assessments, SAMMY offers a customizable layer of controls and mappings between these frameworks, reducing redundancy and ensuring a seamless security management process.
What can you do with SAMMY?
Evaluate
SAMMY allows organizations to carry a variety of application security assessments using different maturity, program and control frameworks. These frameworks offer structured sets of best practices that allow for easy identification of gaps offering a simple, structured and measurable way to address them.

Maturity Frameworks

Assesments
Types
- Self-Assessments
- Top-down Assessments
- Bottom-up Assessments
- External Assessments
- M&A Assessments
The framework you need isn’t here? We can easily add it, just contact us.
Framework Mappings
SAMMY makes evaluations efficient by removing redundant work.
Once you have carried out an evaluation in one framework, you can map it to others to carry over the results, using three different types of mappings:
High-quality mappings are direct mappings that show you how elements map between frameworks. Ultra high-quality mappings allow you to map elements and automatically generate a new assessment based on the mapping.
Trusted by Industry Experts
Improve & Monitor
Improvement Roadmaps
Create, assign and set deadlines for your application security improvement plans.

Targets and Objectives
Set clear targets and provide detailed guidance on how to reach them for all your teams.

Maturity
Visualize maturity across all teams in your organization using frameworks like OWASP SAMM or BSIMM.

Compliance Efforts
Evaluate, analyse gaps and set plans to ensure compliance with frameworks like ISO 27001.
Communicate
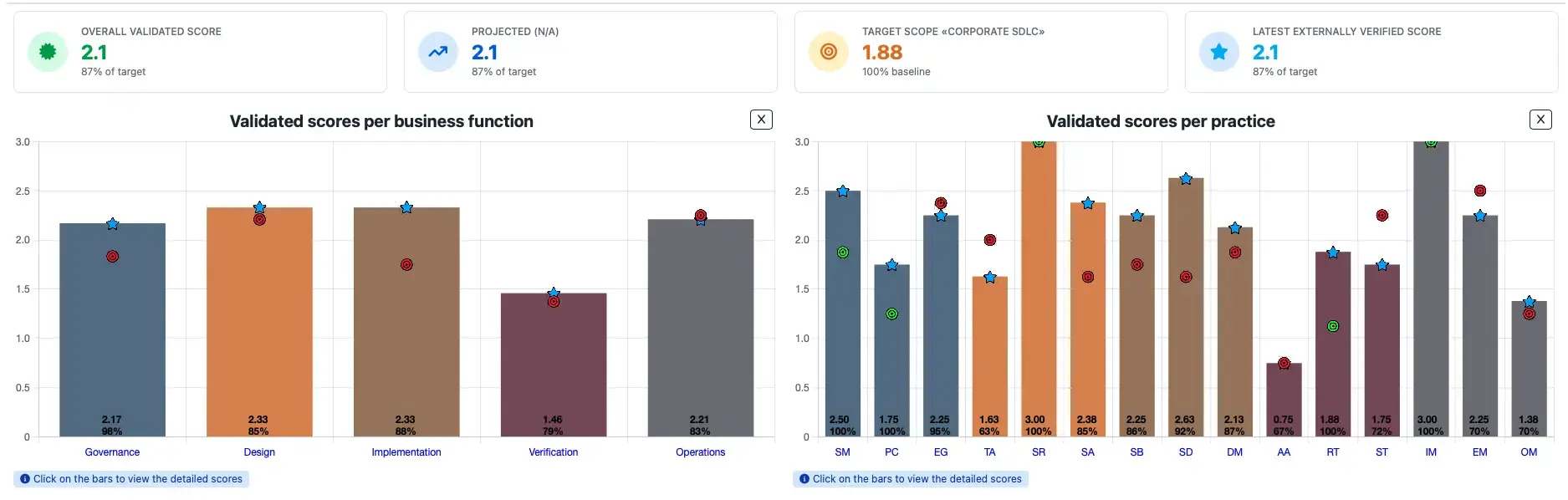
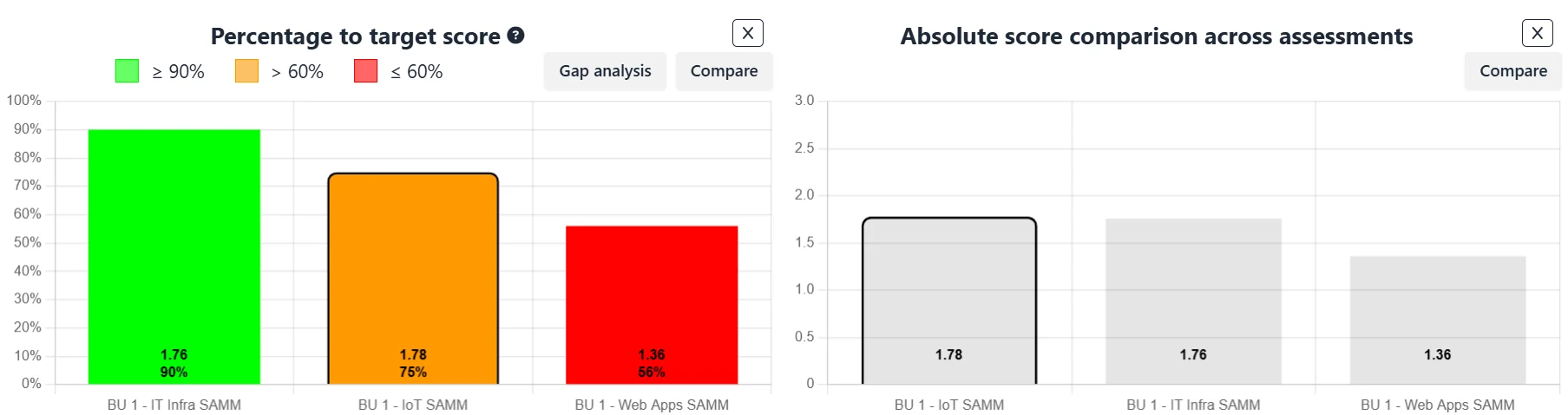
Live Dashboard:
Ensure you are always on top of things by accessing a complete dashboard of different reports that are updated live as you carry out assessments, validate them and set improvement plans and targets.
Internal Reporting:
Support your internal decision making processes by reporting internally on absolute maturity scores, track progress towards set targets and compare across different teams. Gap analysis reports can also be exported to Excel.
External reporting:
Prepare for audits and certifications easily by automatically generating beautifully formatted PDF reports that provide a complete picture of your assessments.
Start using SAMMY to manage your application security with your framework of choice
Managing AppSec
Organizations
Assessments
The SAMMY Community
SAMMY not only provides a cutting-edge tool for application security management, but it also contributes to the community in other ways.
Involvement in OWASP SAMMY v2: Open SAMMY
The predecessor to the current version of SAMMY was donated to the OWASP Community and is now a community-driven OWASP Project called Open SAMMY.
Open SAMMY is an open-source version of SAMMY that allows organizations to manage their AppSec using OWASP SAMM and very soon, OWASP DSOMM as well.
OpenSAMMY is one of many of Codific’s contributions to the OWASP Community. Learn more about Codific @ OWASP.
Our Partner Programs
SAMMY’s Partner Programs bring together organizations from the application security community to drive the shared goal of improving application security.
Implementation Partners Program
SAMMY is built entirely in-house by AppSec specialists, but security consultancy requires more capacity than we can handle alone. To bridge this gap, we’ve partnered with top industry consultants—many of whom have contributed to OWASP standards and guidelines—to provide deep expertise and drive SAMMY adoption. These are called our Implementation Partners.
Want to become an Implementation Partner? Contact us
Recommended Vendors Program
OWASP SAMM is the main framework used in SAMMY, but finding the right vendors to support security maturity can be challenging. To address this, we created the Recommended Vendor program, carefully selecting vendors whose solutions align with SAMM’s 30 streams. These vendors are vetted based on alignment, ease of use, proven results, and reputation, ensuring SAMMY users get the best support.
Want to become a Recommended Vendor? Apply here
Free Training and Guidance
As AppSec specialists, we give back to the community by offering free, accessible guidance and training. To maximize value, we focus on the AppSec program we know best: OWASP SAMM.
OWASP SAMM Training
Learn OWASP SAMM through specialized training, empowering teams to build and maintain secure software.
OWASP SAMM Guidance
Get expert OWASP SAMM guidance to enhance your security framework and align with industry best practices.
Do you need more?
Would you like to run SAMMY on prem? Integrate with your other tools? Have customized of workflows and reports? Or just want to make sure to have a SLA with us?
Free
For small
organizations
per user /month
(limits apply)
Free
features:
3 Scopes
Standard Reporting (Limited Use)
Multiple Assessment Frameworks
Mappings with OpenCRE
Full Data Privacy
Premium
For growing
organizations
per user /month
(limits apply)
Everything from
Free plus:
Maximum 5 user accounts
Maximum 5 scopes
Unlimited Standard Reports
Additional frameworks
Control Management
Premium Direct Mappings
Mapping Reports
JIRA Integration
Online self-serve
Pro
For medium-sized
organizations
(invoiced annually)
Everything from
Premium plus:
Maximum scopes: 5x user count
Branded Reports
Standart Single Sign-On
SLA
Custom vendor onboarding
Priority Support
Enterprise
For enterprise
organizations
(minimum 5 users)
Everything from
Pro plus:
Custom Models
Custom Integrations
Custom Features
Custom Reports
Custom Single Sign-On