The upcoming Cyber Resilience Act (CRA) is a EU regulation that was published on November […]
The warning shots are over. The NIS 2 Directive is live, and enforcement has begun.[…]
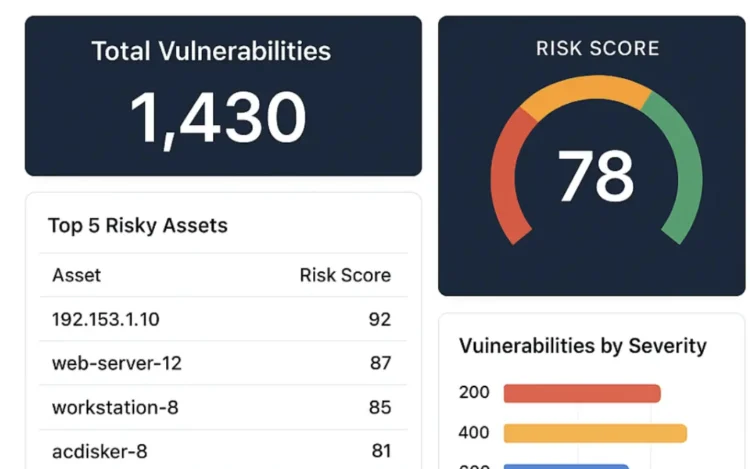
Most organizations conduct security assessments, yet few turn them into meaningful improvement. Traditional cybersecurity gap[…]
Your DevSecOps pipeline is fast, automated, and built to scale. But is security truly integrated,[…]
This article contains a variety of different cybersecurity statistics and trends of 2025 and recent[…]
You’ve probably heard the saying, “You can’t manage what you don’t measure.” If you are[…]
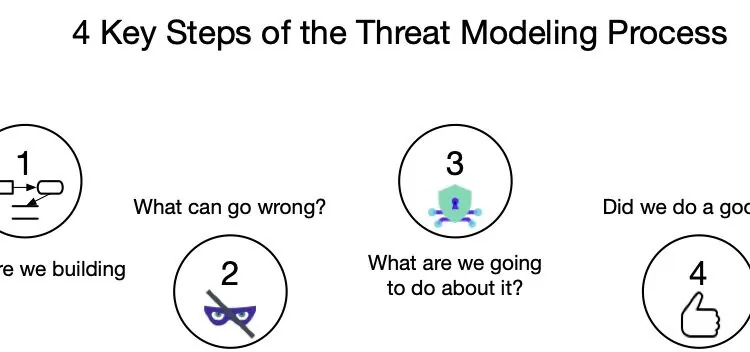
Threat modeling shaped my AppSec career. It helped me wrestle with one of security’s most[…]
Modern software development moves fast, and so do the security challenges that come with it.[…]
Have you every been hacked? It sucks right? But don’t worry now, let’s make sure[…]
In today’s digital landscape, cybercrime is escalating at an alarming rate, with projected damages reaching[…]
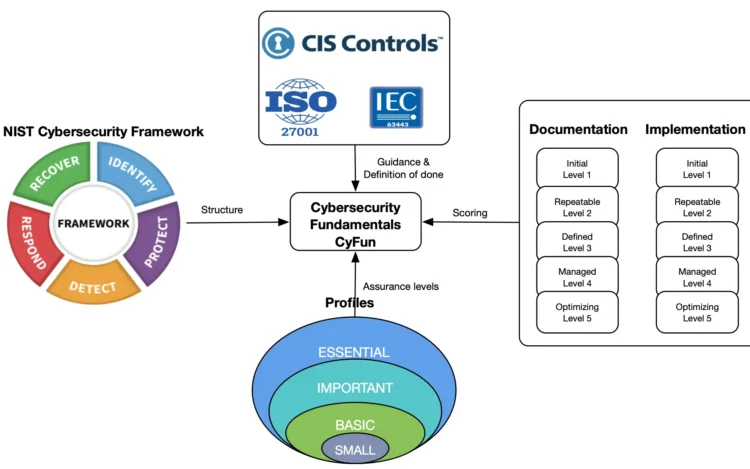
Introduction In this blog, we will focus on helping you understand what is Cybersecurity Fundamentals[…]
Dear disgruntled employee (let’s call you Mallory): Tired of working long hours with no holidays,[…]