Security is a journey, not a destination. SAMM is your map and the OWASP SAMM assessment places you on that map. Codific provides the necessary guidance for your organization to start bulking up on security based on SAMM.

Why OWASP SAMM?
OWASP is the Open Worldwide Application Security Project, a non profit foundation that is the world’s leading publisher of security threats, guidelines and standards for software development in an open world. SAMM is the Software Assurance Maturity Model, it is a structured catalog of OWASP knowledge. With that it is the best guide for your organization to manage your security program from a holistic perspective.
OWASP SAMM assessments
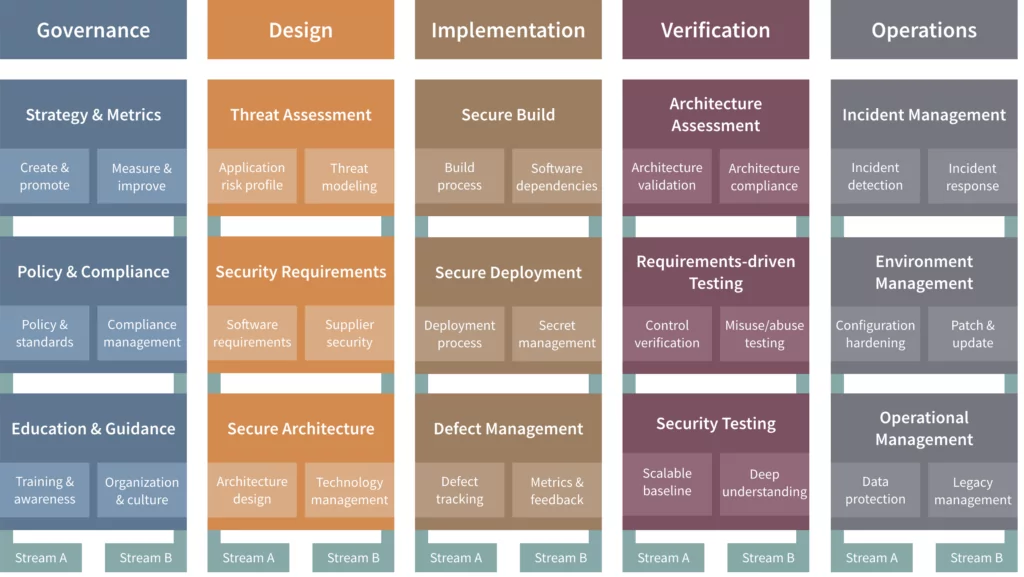
OWASP SAMM is a framework that enables your organization to:
- Assess its current security posture;
- Formulate a tailored Application Security program based on the risks your organization is facing;
- Measure and demonstrate improvements.
SAMM is prescriptive and has a list of quality criteria organized per maturity level. This allows organizations to align targeted security investments with application risk and organizational risk appetite. It provides the structure for a nuanced and efficient security strategy.
How can you use OWASP SAMM?
There are some spreadsheets available to do SAMM assessments. But, because we are not a big fan of doing this in spreadsheets, we have developed a free online tool to do this. The tool is called SAMMY. SAMMY allows you to identify different roles per activity and to create granular improvement tracks for your organization.
OWASP SAMM Assessments
OWASP SAMM as a model is built around the principle of regular assessments. SAMMY turns this into a continuous process. Either way situations will have to be assessed, benchmarked and analyzed. There are several ways you can go about this, self assessment, external assessment and validation audits.

OWASP SAMM Self Assessments
Self assessment is the quickest and most accessible way to get started with OWASP SAMM. The best way to do this is to assign each activity to the most relevant stakeholder for evaluation. These stakeholders should be in a role that gives them clear visibility to the process being analyzed and he should have access to the documentation. Their findings and the evidence to support their statements are uploaded in the SAMMY system. In this case the validator is an internal supervisor that reviews the statements and supporting evidence.
Everybody likes to get good scores, and the natural tendency in self assessment is to be too lenient with the required thresholds. But not always, sometimes teams are too hard on themselves. That is where the role of validator comes in, it is his or her responsibility to check whether adequate evidence is presented to clear a given threshold.

OWASP SAMM External Assessment
The more objective way to do this is via an external assessment. Here the external assessor will fill in the model together with each stakeholder. Codific can be your external assessor. Having done these types of assessments for many different products and organizations we have a deep understanding of the nuances and the expectation on each activity. An external assessment is also the preferred assessment type when OWASP SAMM is used in a supplier audit.
Together with your team we will define your organization’s targets and recommend a security implementation roadmap. Note that SAMM does not insist that all organizations achieve nor aspire to obtain maturity level 3 in each category. Hence, your security growth strategy will be tailored to the risks your organization is facing.
OWASP SAMM Validation Audit
The third option is a hybrid of the self assessment and the external assessment. The stakeholders self assess but the validator is an external auditor rather than an internal supervisor. Codific can be your external auditor. The auditor reviews the evidence presented by the different stakeholders on each activity and evaluates the proposed maturity level. When the auditor rejects a given maturity level on an activity he provides information as to why, and a suggestion of the current maturity level. The stakeholders resubmit until all activities are validated and maturity levels are established.

OWASP SAMM Assessment Training
OWASP SAMM as a model is high level prescriptive. This is by design to be broadly applicable in different contexts. The disadvantage of this is that the specific implementation in your context may create some ambiguity. In order to address the implementation, extensive guidance has been provided by the OWASP community linking the different activities to the different OWASP projects providing tools and standards. To accelerate your team’s learning curve with OWASP SAMM we also offer a one-day SAMM training. During the hands-on workshop we will do a deep-dive into each of the 30 SAMM security streams. Every stream contains three maturity levels that prescribe progressive improvements in your security activities. Your team will get a thorough understanding of the complete security landscape.
SAMM Improvement Guidance
For each organization the priorities are different, and no organization should try to achieve maximum maturity on all activities. So where should you start? What are the low hanging fruits? And how exactly is the next maturity level implemented in those activities? Codific will passionately help you answer these and many more questions in either one of the assessments or trainings.
SAMM Assessments Additional Resources
We have created a page with several additional resources that are very useful to effectively carry out SAMM Assessments. This include a 14-page whitepaper written by two organizations that are experts in carrying SAMM Assessments, Codific and Toreon. Moreover, you can find a one hour podcast between four members of the OWASP SAMM core team, that provides you with valuable practical tips for your assessments. In addition, there is also a link to the SAMMY tool, that was specifically designed to streamline the workflow in these assessments. Finally, you get more resources from the OWASP community like a link to the official OWASP SAMM page that contains a lot of guidance and a link to the SAMM Fundamentals training, that should always be your first step to learning SAMM. Check out all of these resources here.


SAMMY
Find out more about our free tool and the easiest way to implement OWASP SAMM
If you want to learn more about OWASP SAMM you can take the free SAMM training.
What does Codific build with SAMM & SAMMY?
Codific is a team of security software engineers that leverage privacy by design principles to build secure cloud solutions. We build applications in different verticals such as HR-tech, Ed-Tech and Med-Tech. Secure collaboration and secure sharing are at the core of our solutions.
Videolab is used by top universities, academies and hospitals to put the care in healthcare. Communication skills, empathy and other soft skills are trained by sharing patient interviews recordings for feedback.
SARA is used by top HR-Consultants to deliver team assessments, psychometric tests, 360 degree feedback, cultural analysis and other analytical HR tools.
Attendance Radar: is an easy and secure way to record attendance in higher education.