Updated: 24 September, 2025
31 January, 2025
In today’s digital landscape, cybercrime is escalating at an alarming rate, with projected damages reaching $10.5 trillion annually by the end of 2025. This surge underscores the critical need for robust contingency planning to safeguard information systems. The NIST 800-34 framework offers a structured approach to help organizations prepare for, respond to, and recover from such disruptions.
Originally developed by the National Institute of Standards and Technology (NIST) for federal agencies, NIST 800-34’s principles are equally valuable for private sector entities, including those in finance, healthcare, and technology. Implementing this framework can minimize downtime, safeguard sensitive data, and ensure compliance with industry regulations.
This guide provides a comprehensive breakdown of NIST 800-34, including its role in business continuity, its relationship with other NIST frameworks, and a step-by-step walkthrough of its seven-phase contingency planning process. It also examines real-world examples of business disruptions, highlights best practices for implementation, and explores how organizations can use NIST 800-34 to build resilience against cyber threats and operational failures. By the end of this guide, you’ll have a clear roadmap for applying NIST 800-34 to reduce risks, enhance recovery strategies, and ensure business continuity in the face of unexpected disruptions.
Listen to the summary of this article on The AppSec Management Podcast:
Key takeaways
- NIST 800-34 provides a structured approach to contingency planning, helping organizations prepare for and recover from disruptions caused by cyber incidents, system failures, or natural disasters.
- Effective contingency planning minimizes financial, operational, and reputational risks, ensuring business continuity even in the face of unexpected crises.
- A strong readiness assessment and gap analysis are essential to identify weaknesses in existing contingency plans and prioritize areas for improvement.
- Integrating NIST 800-34 with other security frameworks, such as NIST 800-53, ISO 27001, and NIST CSF, enhances efficiency and ensures alignment with broader risk management strategies.
- SAMMY streamlines NIST 800-34 implementation by automating readiness assessments, tracking progress, and providing structured improvement roadmaps, allowing organizations to maintain and enhance their security posture effectively.
- Successful contingency planning is an ongoing process, requiring regular updates, testing, and leadership engagement to remain effective in an evolving threat landscape.
Why Contingency Planning Matters?
Cyberattacks, IT failures, and natural disasters can bring business operations to a halt. Without a structured contingency plan, organizations risk financial losses, regulatory fines, and reputational damage.
Business disruptions are costly
The 2024 IBM Cost of a Data Breach Report found that the average global cost of a data breach reached $4.88 million, a 10% increase from the previous year. Businesses experiencing major operational shutdowns saw breach costs rise by 7.9% compared to those that remained operational.
Learn from the mistakes of other organizations
Some of the most damaging cyber incidents in recent history show what happens when organizations lack contingency plans:
- Maersk’s NotPetya Attack (2017): A ransomware attack shut down IT systems, halting operations across 76 ports. The company suffered losses between $200 million and $300 million and had to rebuild its entire infrastructure.
- British Airways IT Failure (2017): A power system failure led to the cancellation of more than 700 flights, affecting 75,000 passengers and resulting in an estimated £80 million (≈$100 million) in losses.
- Colonial Pipeline Cyberattack (2021): A ransomware attack forced a six-day pipeline shutdown, leading to widespread fuel shortages across the U.S. East Coast. The company paid a $4.4 million ransom to restore operations.
These cases demonstrate the high costs of poor contingency planning. Businesses that fail to prepare often face prolonged downtime and significant financial losses.
How NIST 800-34 Helps
A contingency plan aligned with NIST 800-34 enables organizations to:
- Identify critical business functions and plan for their recovery.
- Implement preventive measures like system backups and redundant infrastructure.
- Develop response strategies to reduce downtime and financial losses.
- Regularly test and update plans to adapt to emerging threats.
Organizations that follow NIST 800-34 guidelines can significantly reduce risks and maintain business continuity, even in the face of a major disruption.
NIST 800-34 Framework & How It Fits into the Bigger Picture
NIST 800-34 provides a structured approach to contingency planning, helping businesses and agencies prepare for IT failures, cyberattacks, and unexpected disruptions. It offers a roadmap for identifying risks, establishing recovery strategies, and maintaining operational resilience.
What NIST 800-34 Covers
The framework outlines seven key phases of contingency planning, from policy creation and business impact analysis to testing and ongoing maintenance. Its flexible approach allows organizations to tailor contingency plans to their specific needs.
By implementing NIST 800-34, organizations can:
- Develop systematic strategies for identifying and mitigating disruptions.
- Establish business continuity and disaster recovery plans to minimize downtime.
- Align contingency planning with broader risk management frameworks.
How NIST 800-34 Connects to Other Security Frameworks
NIST 800-34 is not a standalone framework—it integrates with other cybersecurity and risk management standards, creating a more comprehensive security strategy.
- NIST 800-61 (Incident Response Guide): Focuses on immediate incident handling, while NIST 800-34 ensures long-term recovery and operational continuity.
- NIST 800-53 (Security Controls Framework): Includes contingency planning controls that align with NIST 800-34’s recovery strategies.
- NIST Risk Management Framework (RMF): Helps integrate contingency planning into broader risk management efforts.
- ISO 27001 (Information Security Management System – ISMS): Requires business continuity and disaster recovery planning, aligning with NIST 800-34’s principles.
- NIST Cybersecurity Framework (CSF): Its Recover function closely aligns with NIST 800-34’s focus on minimizing downtime and ensuring system restoration.
Why Integrating NIST 800-34 with Other Security Frameworks Matters
Integrating NIST 800-34 with other security frameworks ensures that contingency planning is not treated as a separate function but embedded into a larger risk management strategy. This approach strengthens resilience, improves compliance, and reduces financial losses from unexpected disruptions.
The Seven-Step Contingency Planning Process
A strong contingency plan is not just about having a backup system—it requires a structured approach that ensures organizations can effectively respond to and recover from disruptions. NIST 800-34 outlines a seven-step process that organizations can follow to develop and maintain a reliable contingency plan. The contingency planning process follows a structured sequence, as shown in the diagram below.
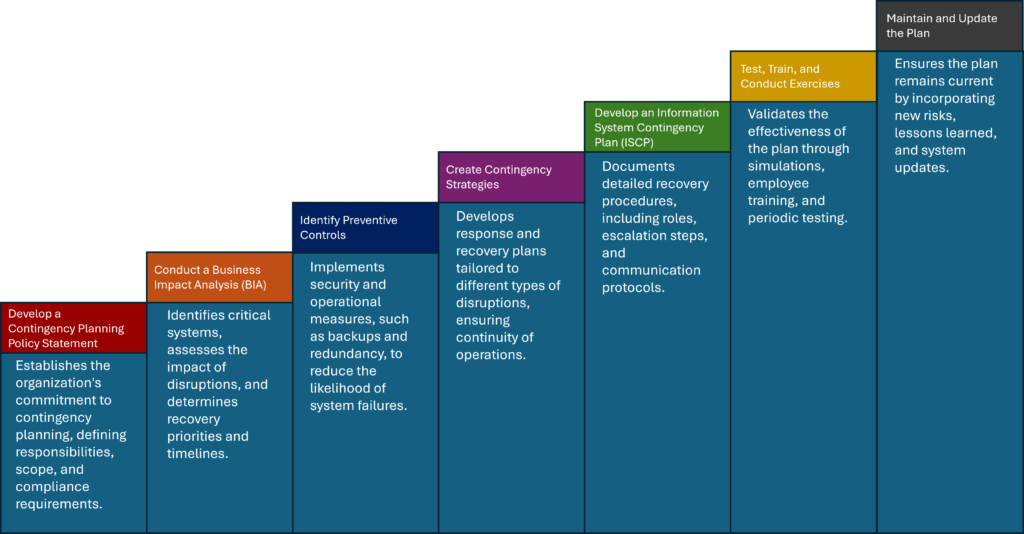
1. Develop a Contingency Planning Policy Statement
A clear policy statement sets the foundation for contingency planning. It should outline the organization’s commitment to preparedness, define key roles and responsibilities, and establish a framework for creating and maintaining the plan.
Key elements of the policy statement include:
- Purpose and scope: What systems and operations does the plan cover?
- Roles and responsibilities: Who is responsible for maintaining and executing the plan?
- Compliance requirements: What regulations and standards (e.g., NIST 800-53, ISO 27001) must be followed?
- Review and update schedule: How often will the plan be updated and tested?
2. Conduct a Business Impact Analysis (BIA)
A business impact analysis (BIA) identifies critical business functions and evaluates the impact of disruptions to determine which systems require urgent recovery and to define recovery time objectives (RTOs).
BIA is essential not just for NIST 800-34 but also for risk assessments, privacy compliance (GDPR, HIPAA), threat modeling, and penetration testing. Security teams conducting threat modeling or penetration testing need to assess whether a vulnerability—such as cross-site scripting (XSS)—has a real business impact rather than being a theoretical risk.
BIA also strengthens vulnerability management (VM) programs, which often focus on reducing the total number of vulnerabilities without evaluating their actual impact. In reality, over 80% of vulnerabilities pose little to no real risk, yet they are often treated with the same urgency as high-impact threats. A proper BIA ensures security efforts are prioritized based on business risk rather than just vulnerability count.
Steps to Conduct a BIA:
- Identify critical business functions and their dependencies.
- Assess the impact of disruptions on operations, finances, and compliance.
- Define RTOs and recovery point objectives (RPOs).
- Prioritize resources based on business impact.
By integrating BIA into broader security and compliance programs, organizations can ensure that incident response, vulnerability management, and contingency planning focus on real business risks, not just technical issues.
3. Identify Preventive Controls
Preventive measures reduce the risk of disruptions before they happen. Organizations should assess existing controls and implement new safeguards where necessary.
Common preventive controls include:
- Regular system backups stored in multiple locations.
- Redundant network and power supplies to prevent outages.
- Security controls such as firewalls, multi-factor authentication (MFA), and endpoint protection.
- Automated failover systems for mission-critical services.
Additional controls can also be found in frameworks like NIST 800-53, which you can find more about in this article.
4. Create Contingency Strategies
An effective contingency plan outlines how an organization will recover from disruptions, ensuring that recovery efforts align with the severity of the event and the organization’s risk profile.
One of the most widely used strategies is alternate processing sites, which ensure operations can continue if primary systems fail. Organizations typically choose between:
- Hot sites – Fully operational facilities with real-time data replication, allowing for near-instant recovery.
- Warm sites – Partially configured environments that require some setup before resuming operations.
- Cold sites – Basic infrastructure with minimal pre-configured resources, requiring significant setup before use.
Choosing the right approach depends on business continuity needs, recovery time objectives (RTOs), and budget constraints. Organizations must weigh cost vs. recovery speed to ensure their contingency plan provides the necessary resilience without excessive overhead.
5. Develop an Information System Contingency Plan (ISCP)
A detailed contingency plan document ensures that recovery steps are clear, actionable, and easy to follow.
The plan should include:
- Contact information for key personnel and recovery teams.
- Step-by-step recovery procedures for restoring critical systems.
- Communication protocols for internal teams and external stakeholders.
- Escalation procedures for severe incidents.
- Testing and review schedules to keep the plan up to date.
6. Test, Train, and Conduct Exercises
A contingency plan is only effective if it works under real-world conditions. Regular testing and training ensure employees understand their roles and that recovery procedures function as intended.
At a minimum, organizations should conduct contingency plan exercises at least once a year, adjusting frequency based on risk exposure. The key is not just running exercises but using the results to improve the plan. Every test should lead to actionable improvements, whether refining response procedures, updating system dependencies, or improving communication flows.
How to Test Your Contingency Plan Effectively:
- Tabletop exercises – Walk through different disruption scenarios with key stakeholders, identifying gaps in response plans.
- Functional testing – Execute recovery steps in a controlled environment to verify effectiveness.
- Full-scale drills – Simulate real-world incidents involving multiple teams to assess cross-functional coordination.
If your organization regularly conducts exercises and incorporates findings into plan updates, you’re already ahead of most companies in contingency preparedness.
7. Maintain and Update the Plan
An outdated contingency plan can be as dangerous as having no plan at all. Organizations should schedule regular reviews and updates, ensuring their strategy evolves with new risks, system changes, and lessons learned from testing.
A best practice is to update the plan after every major incident or annual exercise. If test results reveal gaps, immediate adjustments should be made rather than waiting for a scheduled review.
How to Keep Your Plan Up to Date:
- After-action reviews – Conduct post-incident reviews to incorporate lessons learned into future planning.
- Annual risk assessments – Identify new vulnerabilities and update response priorities accordingly.
- Review team roles and contact lists – Ensure all personnel information remains accurate as teams evolve.
- Maintain executive buy-in – Keep leadership engaged to ensure contingency planning remains a business priority.
A well-maintained contingency plan is a living document, not a one-time exercise. Organizations that test, refine, and update their plans regularly will be far more resilient than those that simply create a plan and let it gather dust.
Why This Process Matters
Following the NIST 800-34 seven-step process ensures that organizations are prepared for disruptions, can respond efficiently, and can recover quickly without significant financial or operational impact.
A contingency plan is not just a technical necessity—it is a business-critical function that protects an organization’s ability to serve customers, maintain trust, and comply with regulations.
Implementing NIST 800-34 in Your Organization
Understanding the seven-step contingency planning process is one thing—implementing it effectively is another. Many organizations struggle with turning policy into action, integrating contingency planning into their daily operations, and maintaining it over time. This section provides practical steps for making NIST 800-34 work in real-world settings.
1. Building Internal Support & Buy-in
For contingency planning to be successful, it needs leadership support and dedicated resources. Without this, contingency plans often get deprioritized until an actual disaster strikes.
How to Gain Leadership Support
- Frame it as a business risk, not just IT risk – Emphasize how disruptions impact revenue, reputation, and regulatory compliance.
- Use real-world case studies – Examples like Equifax or Colonial Pipeline show the financial damage of failing to plan.
- Quantify the risk – Show potential costs of downtime, regulatory fines, and customer churn without a contingency plan.
- Propose a realistic roadmap – Leadership is more likely to approve plans that don’t require immediate large investments.
Who Should Be Involved?
- Executive sponsor (CIO, CISO, or COO) to drive prioritization.
- IT security and infrastructure teams to handle system resilience.
- Business continuity managers to align with broader disaster recovery efforts.
- Legal and compliance teams to ensure regulatory adherence.
- Key department heads (finance, HR, operations) to account for cross-functional risks.
2. Assessing Your Current Readiness
Before creating or improving a contingency plan, organizations need to assess their current level of preparedness. Conducting a readiness assessment and gap analysis helps identify weaknesses in existing processes and determine where improvements are most needed. However, manual evaluations can be time-consuming, inconsistent, and difficult to track.
This is where SAMMY provides a structured, efficient, and scalable approach to evaluating NIST 800-34 implementation.
Readiness Assessment with SAMMY
SAMMY is an AppSec management tool designed to help organizations evaluate, validate, and improve their security posture across multiple frameworks, including NIST 800-34.
One of its standout features is interactive framework visualization, allowing teams to see the full scope of NIST 800-34 at a glance. It incorporates a CMMI-based maturity model, helping organizations measure how well each element has been implemented.
How It Works
- Assigning Evaluations – A designated team member is assigned to evaluate specific elements of the framework.
- Adding Documentation & Remarks – After completing the evaluation, the user can upload supporting documentation and add remarks to justify their assessment.
- Building a Strong Validation Process – Submitted evaluations serve as the foundation for validation and improvement roadmaps, ensuring organizations have clear evidence supporting their contingency planning posture.
By using SAMMY, organizations eliminate guesswork and ensure that readiness assessments are structured, repeatable, and backed by evidence.
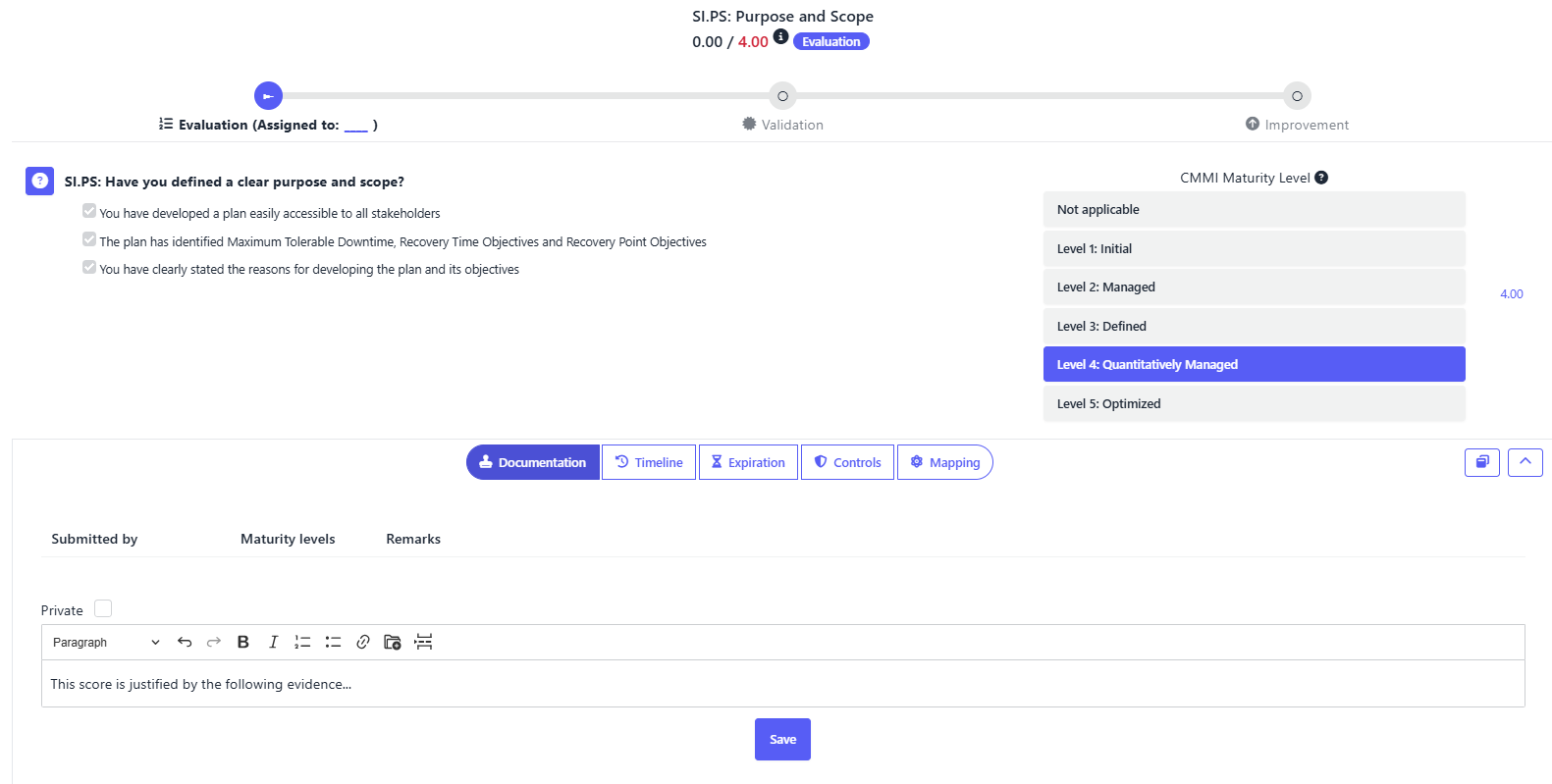
Additionally, you can set an expiration date for the evaluation, ensuring that teams periodically reassess and update their assessment of each element. This proactive approach aligns with the final step of the NIST 800-34 framework, which emphasizes continuous review and improvement to maintain an effective contingency plan.
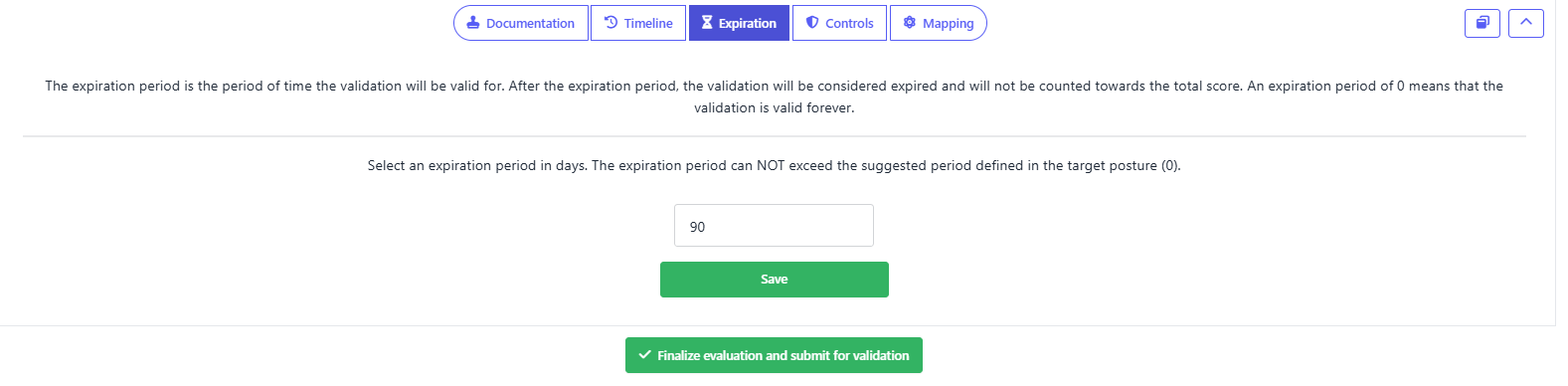
After completing the evaluation, you can optionally proceed to a validation step, assigning it to another team member. This person is responsible for reviewing the provided evidence and determining whether the assessment is accurate. They can either accept the evaluation if they agree with it or reject it if the evidence does not support the assessment.
Gap Analysis with SAMMY
This thorough readiness assessment ensures organizations have a clear understanding of their current contingency planning posture. The next step is conducting a gap analysis, an area where SAMMY also excels.
SAMMY allows you to define a target posture, representing the longer-term objective for each element in the NIST 800-34 framework. This helps organizations establish where they want to be and, in turn, identify the gaps between their current and desired states.
SAMMY’s gap analysis includes:
- Target Posture Definition – Set long-term objectives for each element within NIST 800-34 to align contingency planning efforts with organizational goals.
- Visual Gap Identification – Red targets indicate unmet elements, while green targets signify successfully implemented ones.
- Quantifiable Metrics – Hover over an element’s target to view a percentage value, offering a precise measurement of the gap between the current and desired state.
By leveraging these insights, organizations can prioritize improvements effectively and create data-driven roadmaps for closing gaps in contingency planning.
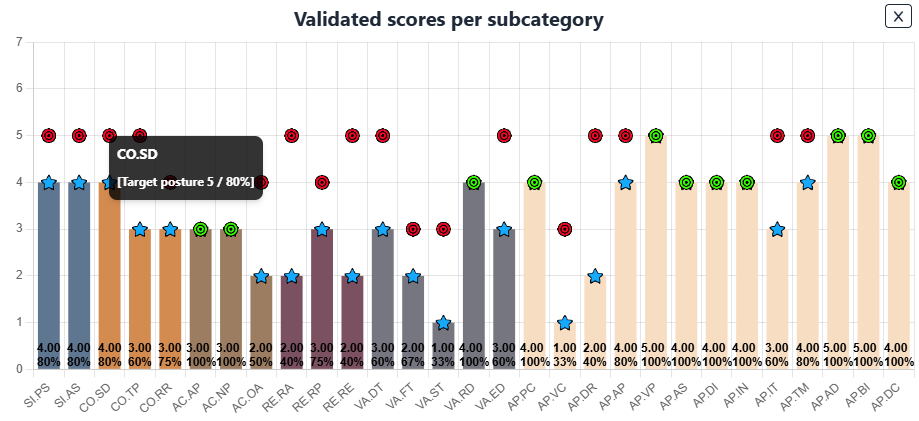
Moreover, you can add guidance to each target for every element, providing clear instructions to help implementation teams understand the necessary steps to achieve their objectives. This ensures that teams have actionable direction on how to close gaps and align with NIST 800-34 requirements effectively.

In addition, you can view the overall percentage to target for a business unit, allowing you to compare progress across different units. You can also download a gap analysis Excel report, which provides a detailed breakdown of each element, indicating whether the target has been met or not.
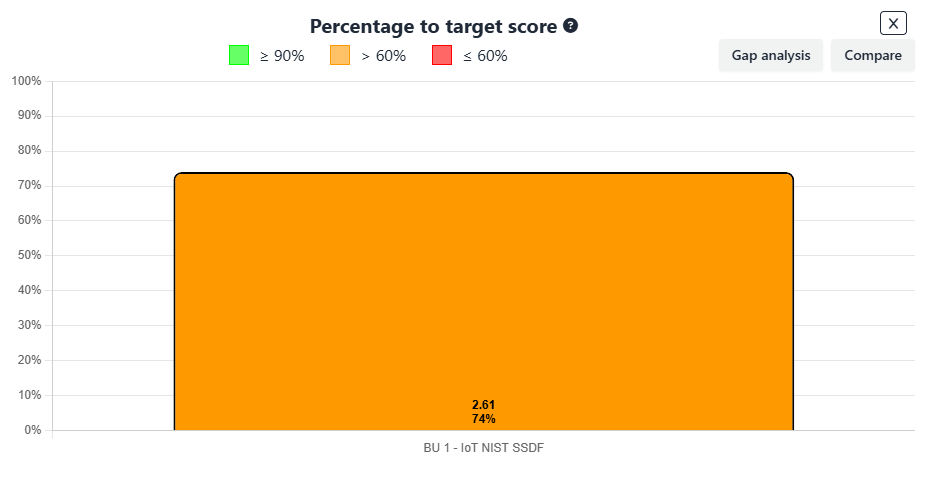
This enables you to conduct a comprehensive gap analysis, providing valuable insights that will guide the next phase: developing a structured implementation roadmap in Step 3.This enables you to conduct a comprehensive gap analysis, providing valuable insights that will guide the next phase: developing a structured implementation roadmap in Step 3.
3. Developing a Step-by-Step Implementation Roadmap
After conducting a readiness assessment and gap analysis, organizations need a clear roadmap to systematically improve their NIST 800-34 implementation. This step involves setting specific improvement objectives, tracking progress, and ensuring that planned enhancements align with overall contingency planning goals.
Implementation Planning with SAMMY
SAMMY provides a structured approach to implementation planning by allowing organizations to define and track improvement steps for each element in the NIST 800-34 framework. This ensures that teams have actionable plans in place to close identified gaps.
As shown in the screenshot below, SAMMY enables users to:
- Set an improvement target date to establish clear timelines for implementation.
- Define improvement steps for each element, ensuring that the necessary policies, processes, or technical controls are implemented.
- Attach supporting documentation to outline detailed execution plans.
- Track progress using CMMI maturity levels, ensuring that each improvement aligns with an organization’s overall security posture.
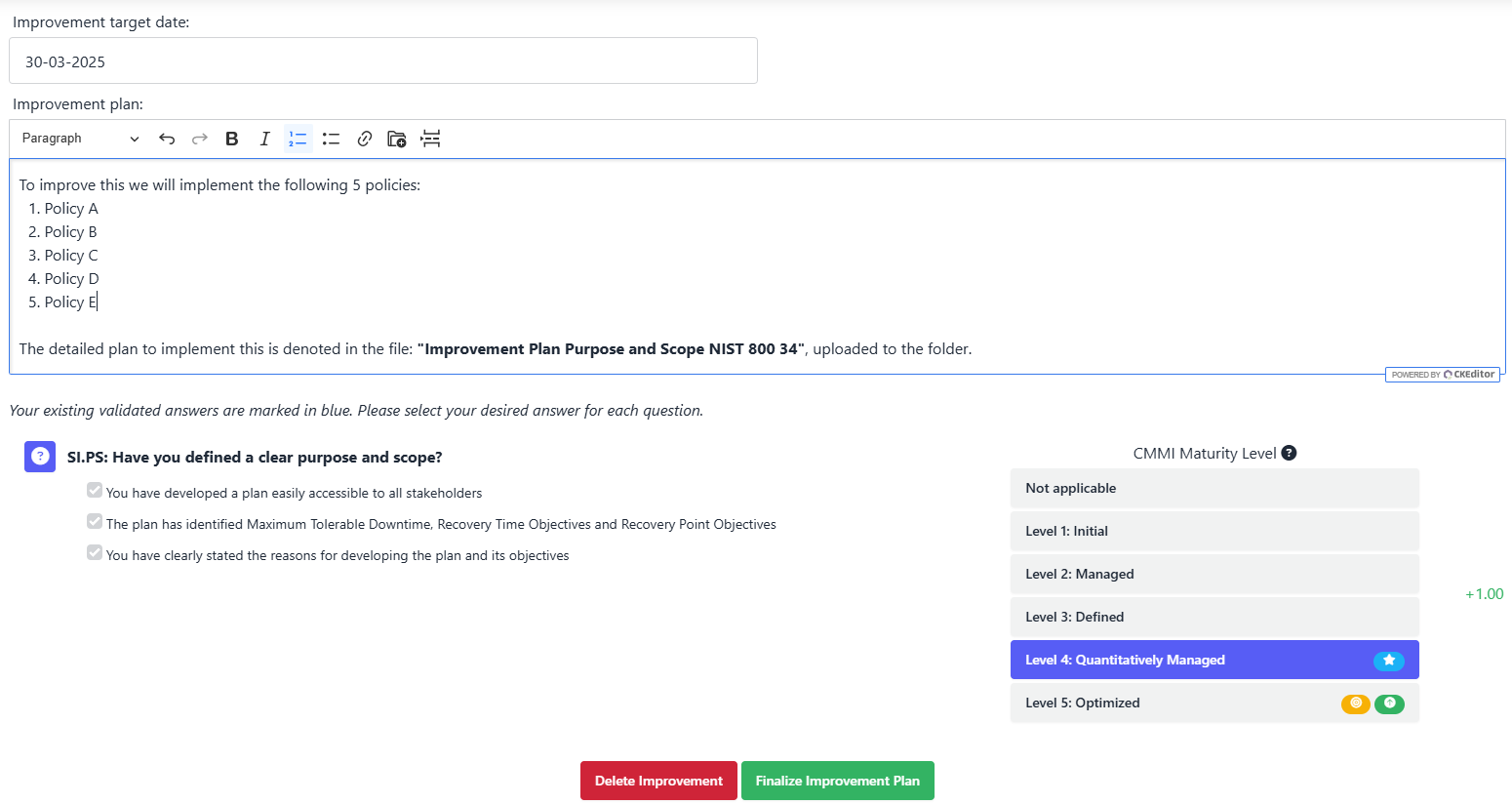
By leveraging SAMMY’s improvement step feature, organizations can ensure that remediation efforts remain structured, measurable, and aligned with business priorities. This approach helps avoid ad-hoc fixes and instead fosters a continuous improvement process that strengthens contingency planning over time.
4. Integrating with Existing Security & Compliance Programs
Organizations rarely operate within a single security framework—many follow multiple standards, such as NIST 800-53, ISO 27001, and the NIST Cybersecurity Framework (CSF). To maximize efficiency and avoid redundant work, it’s essential to align contingency planning efforts under NIST 800-34 with other security and risk management programs already in place.
How NIST 800-34 Aligns with Other Frameworks
NIST 800-34 provides a structured approach to contingency planning, and its principles overlap with several well-established security frameworks. By mapping these connections, organizations can build upon existing controls rather than creating processes from scratch.
| Framework | How It Connects to NIST 800-34 |
| NIST 800-53 | Contains contingency planning controls that align with NIST 800-34. |
| NIST Cybersecurity Framework (CSF) | The “Recover” function aligns directly with NIST 800-34’s principles. |
| ISO 27001 | Annex A.17 focuses on business continuity, similar to NIST 800-34. |
| Disaster Recovery (DR) Plans | NIST 800-34 enhances and complements DR planning. |
Rather than treating NIST 800-34 as a standalone effort, organizations should map its requirements to existing security initiatives, ensuring consistency, efficiency, and compliance.
Implementing Framework Integration Using SAMMY
SAMMY simplifies cross-framework integration by enabling organizations to map NIST 800-34 elements to other security standards. While mappings for NIST 800-34 are not yet available, SAMMY offers a framework mapping module that allows organizations to:
- Generate mappings to other frameworks using multiple mechanisms.
- Leverage OpenCRE mappings, where frameworks are linked via a common requirements enumeration (CRE).
- Utilize Codific’s direct mappings, which provide high-quality framework alignments (available for premium customers).
- Apply transitive mappings, which connect frameworks via OpenCRE but with some trade-offs in precision.
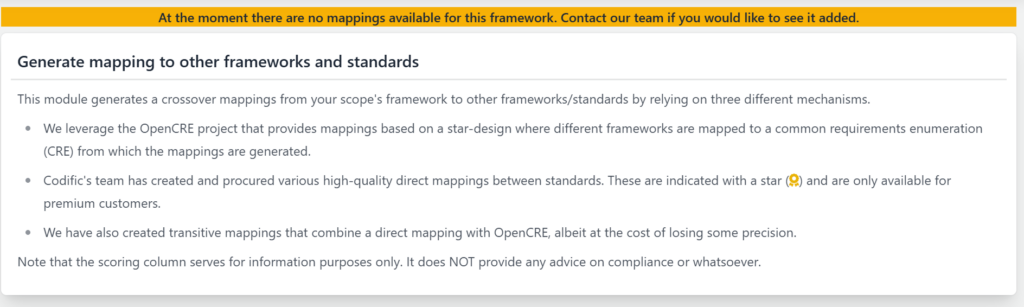
At present, there are no predefined mappings for NIST 800-34. However, if organizations are interested in integrating contingency planning with other security frameworks, SAMMY’s team is open to adding these mappings upon request.
By leveraging SAMMY’s framework mapping features, organizations can streamline compliance, reduce duplication of effort, and ensure their contingency planning aligns with broader security strategies.
5. Avoiding Common Pitfalls in Implementation
Even with a well-defined plan, many organizations struggle with contingency planning implementation due to poor execution, lack of engagement, or outdated processes. Recognizing these pitfalls in advance helps organizations navigate challenges more effectively and ensure long-term success.
Common Pitfalls & How to Avoid Them
- Creating a static plan that is never updated
- A contingency plan should be a living document that evolves with the organization’s needs.
- Solution: Schedule regular reviews and update plans after incidents or significant system changes.
- Overcomplicating the plan
- Complex, overly detailed plans often lead to confusion and lack of adoption.
- Solution: Keep documentation clear, concise, and actionable, avoiding unnecessary complexity.
- Failure to test the plan regularly
- Without testing, organizations cannot be sure their contingency plan will work when needed.
- Solution: Conduct annual tabletop exercises and full-scale simulations to validate effectiveness.
- Ignoring non-technical risks
- Many organizations focus solely on IT disruptions, overlooking supply chain failures, personnel availability, or physical security threats.
- Solution: Consider all potential risks that could impact business continuity.
- Lack of leadership engagement
- If executive leadership does not prioritize contingency planning, it often lacks the funding and attention needed to be effective.
- Solution: Involve executive sponsors and clearly communicate the business impact of poor contingency planning.
By proactively addressing these challenges, organizations can ensure their contingency planning efforts are sustainable and effective.
Conclusion: Making NIST 800-34 Implementation a Success
Successfully implementing NIST 800-34 requires more than just checking boxes—it demands a strategic, ongoing effort that integrates with existing security programs and adapts to evolving threats.
Key Takeaways for Implementation Success
- Readiness assessments and gap analysis provide the foundation for a structured contingency plan.
- Developing a clear improvement roadmap ensures organizations stay on track with well-defined goals.
- Integrating with existing frameworks like NIST CSF, ISO 27001, and NIST 800-53 reduces duplication of effort and enhances alignment.
- Avoiding common pitfalls prevents organizations from falling into the trap of outdated or ineffective contingency planning.
The Role of SAMMY in Streamlining Implementation
SAMMY plays a crucial role in this process by simplifying readiness assessments, tracking implementation progress, and offering framework mapping capabilities to align NIST 800-34 with broader security initiatives.
By leveraging SAMMY’s structured approach, organizations can ensure that contingency planning efforts are measurable, effective, and continuously improving.
Final Thoughts
Organizations that treat contingency planning as a continuous process rather than a one-time exercise will be best positioned to mitigate risks, respond to disruptions effectively, and maintain operational stability in an increasingly unpredictable landscape.
Real-World Examples of Contingency Planning Failures & Successes
Effective contingency planning can mean the difference between a minor disruption and a catastrophic failure. While Section 2 covered major incidents caused by poor contingency planning, this section explores contrasting case studies—where organizations either failed or succeeded in implementing NIST 800-34-style contingency strategies.
Failure: Equifax Data Breach (2017) – Lack of Incident Preparedness
In 2017, Equifax, one of the largest credit reporting agencies, suffered a data breach that exposed the personal information of 147 million people. A critical flaw in their incident response and contingency planning worsened the crisis.
What Went Wrong?
- Lack of patch management: A known vulnerability in Apache Struts (CVE-2017-5638) remained unpatched for over two months, leading to the breach.
- Ineffective incident detection and response: The breach lasted 76 days before it was discovered.
- Poor communication strategy: Delays in notifying the public and authorities resulted in severe reputational damage and lawsuits.
Lessons Learned
- Proactive contingency measures like automated patching policies could have prevented the breach.
- Stronger incident response protocols could have contained the damage earlier.
- Transparent crisis communication would have helped mitigate the fallout.
Success: GitHub’s Response to the Largest DDoS Attack (2018)
In 2018, GitHub, the world’s largest code hosting platform, faced a record-breaking 1.3 Tbps DDoS attack. Unlike Equifax, GitHub had a well-executed contingency plan in place, ensuring rapid recovery.
What Went Right?
- Automated traffic rerouting – Within 10 minutes, GitHub redirected attack traffic to a DDoS protection service, neutralizing the threat.
- Cloud-based redundancy – The company’s use of a highly distributed cloud infrastructure prevented extended downtime.
- Proactive monitoring and response – GitHub’s contingency team acted immediately, ensuring full service restoration within 20 minutes.
Lessons Learned
- Preemptive cloud-based defenses can reduce attack impact.
- Rapid incident detection and response minimize downtime and protect operations.
- Automated failover systems ensure seamless recovery.
Why Contingency Planning Determines Business Survival
Both cases illustrate how preparedness defines an organization’s ability to survive crises. Companies that follow NIST 800-34 principles, such as continuous monitoring, redundancy, and clear recovery protocols, are better positioned to recover quickly and protect their customers.
Key Takeaways
- Ignoring contingency planning leads to disaster, as seen in Equifax’s failure.
- Proactive planning ensures resilience, as demonstrated by GitHub’s success.
- Organizations should integrate NIST 800-34 guidelines to reduce risk, improve response times, and maintain business continuity.
Conclusion: The Importance of NIST 800-34 in Organizational Resilience
In today’s rapidly evolving threat landscape, disruptions are inevitable. Whether caused by cyberattacks, system failures, or natural disasters, unplanned incidents can cripple organizations that lack a structured contingency plan.
The NIST 800-34 framework provides a clear roadmap for ensuring operational resilience through policy creation, risk analysis, preventive measures, recovery strategies, and ongoing testing. Implementing these principles strengthens an organization’s ability to recover quickly, minimizing financial losses, regulatory risks, and reputational damage.
From Framework to Implementation
Successful contingency planning requires more than just documentation—it demands structured implementation, continuous testing, and alignment with broader security frameworks. This is where SAMMY plays a key role.
By using SAMMY to assess readiness, track implementation progress, and align NIST 800-34 with other security frameworks, organizations can:
- Streamline contingency planning with automated evaluations and validation steps
- Conduct gap analyses to measure progress and identify improvement areas
- Integrate contingency strategies into a centralized security management system
- Track continuous improvement efforts through structured implementation roadmaps
Final Thoughts
The lessons from major cyber incidents such as Equifax’s failure and GitHub’s success demonstrate that contingency planning is essential for business survival. Companies that embrace NIST 800-34, invest in proactive planning, and leverage automation tools will be best positioned to mitigate disruptions, protect critical operations, and maintain stakeholder trust.
With the right framework and tools, organizations can move beyond reactive crisis management and build a resilient security posture that ensures long-term stability.
Official pages of all frameworks and regulations mentioned in this article
- NIST 800-34 framework
- NIST 800-61 framework
- NIST 800-53 framework
- NIST Risk Management Framework (RMF)
- NIST Cybersecurity Framework (CSF)
- ISO 27001 framework
- Capability Maturity Model Integration (CMMI)
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)




