Most security issues in software stem from one simple problem: teams try to fix them […]
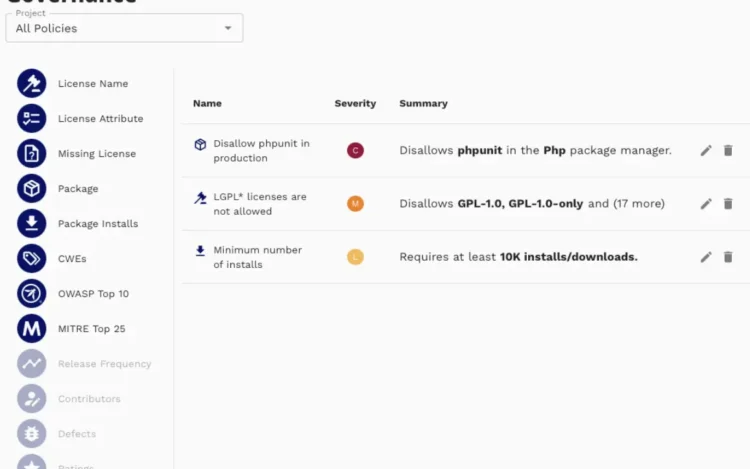
Dependency management has become one of the most critical aspects of modern software development. Third-party[…]
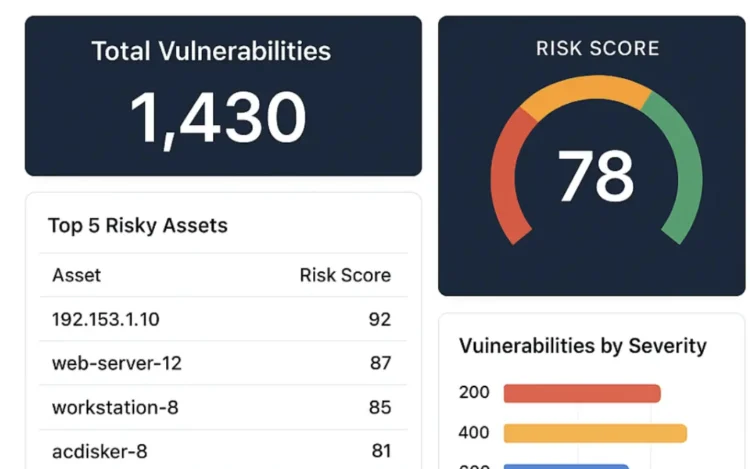
You’ve probably heard the saying, “You can’t manage what you don’t measure.” If you are[…]
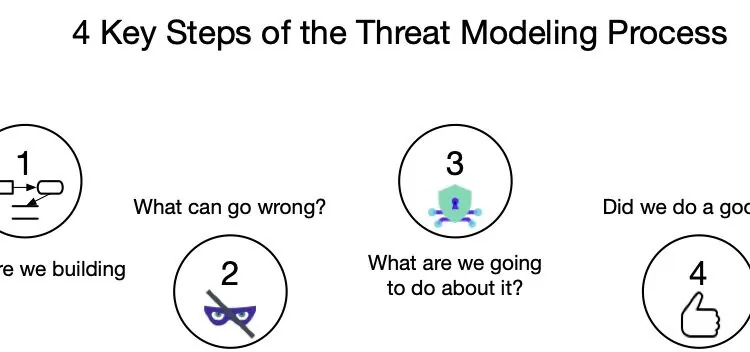
Threat modeling shaped my AppSec career. It helped me wrestle with one of security’s most[…]
Modern software development moves fast, and so do the security challenges that come with it.[…]
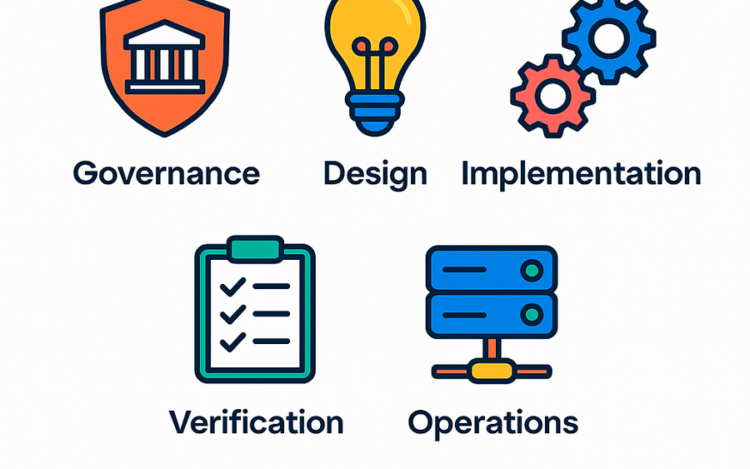
Understanding OWASP SAMM is only the beginning. The real value comes from using it to[…]
As I reflect on my experience at the 4YFN conference in Barcelona, one thing stands[…]
Have you every been hacked? It sucks right? But don’t worry now, let’s make sure[…]
Fraud against government programs costs taxpayers billions of dollars every year, threatening the integrity of[…]
In today’s digital landscape, cybercrime is escalating at an alarming rate, with projected damages reaching[…]
In today’s rapidly evolving digital landscape, ensuring software security is more critical than ever. Recognizing[…]
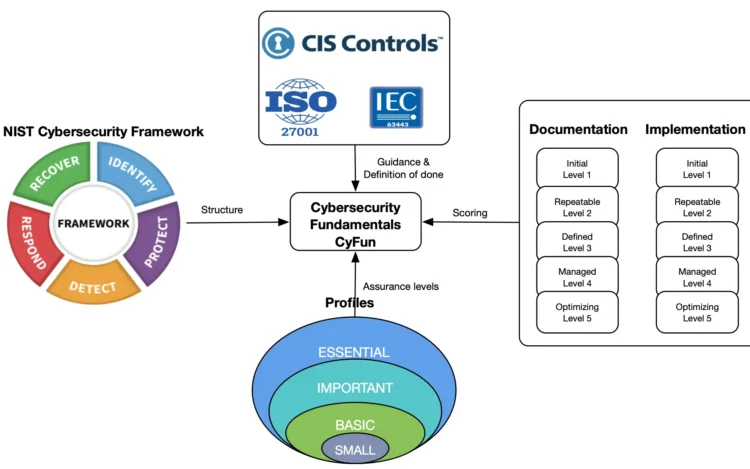
Introduction In this blog, we will focus on helping you understand what is Cybersecurity Fundamentals[…]