Leading the security journey
As security threats grow in complexity, organizations are under increasing pressure to embed security practices directly into their software development processes. At Sigma Software, this is approached systematically through the adoption of mature, industry-recognized frameworks, most notably OWASP SAMM (Software Assurance Maturity Model). Guiding this effort is Oleksandr Zherebtsov, Head of the Information Security Department.
Oleksandr has played a key role in aligning Sigma Software’s security program with OWASP SAMM, enabling the company to assess, improve, and scale its secure software development practices. From secure design and implementation to operational security and governance, SAMM provides a structured methodology that Oleksandr and his team use to ensure consistency, traceability, and measurable improvements across projects.
In this interview, Oleksandr discusses how Sigma Software integrates OWASP SAMM into its workflows, the value it brings to clients, and how his team collaborates with development units to embed security from the ground up, across a wide range of industries and technologies.
In what context are you using OWASP SAMM?
Oleksandr Zherebtsov,
Head of the Information Security Department
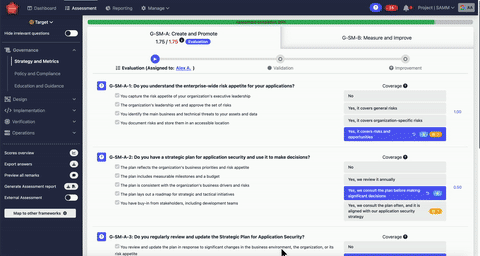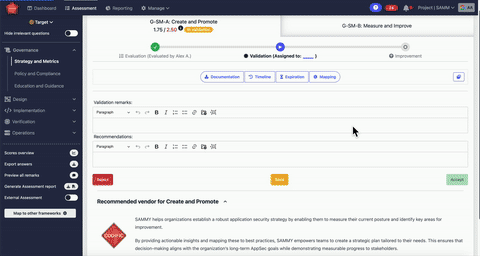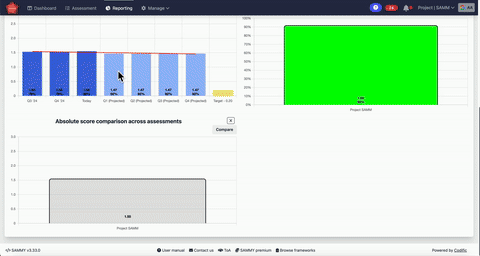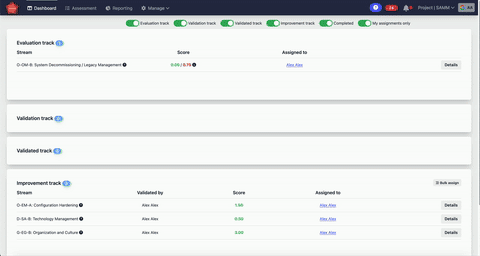
“We are using the OWASP SAMM (Software Assurance Maturity Model) framework in several key areas:
- Project-Level Assessment:
We apply SAMM to evaluate individual projects and the specific security approaches chosen by different teams. This helps us understand how well each project aligns with secure software development practices.
- Organization-Wide Maturity Evaluation:
Beyond individual projects, we use SAMM to assess the overall maturity of the entire organization in terms of software security. This provides a comprehensive view of where we stand across all teams and initiatives.
- Strategic Planning and Roadmapping:
The insights we gain from SAMM assessments allow us to identify gaps and areas for improvement. We use this data to build practical roadmaps for enhancing security practices both at the project level and across the company as a whole.
Overall, OWASP SAMM supports us in making informed decisions, improving processes, and driving continuous security maturity growth throughout the organization.”
Listen to the summary of this article on The AppSec Management Podcast:
When and why did your organization start using OWASP SAMM?
We started using OWASP SAMM approximately two years ago. Initially, it was applied selectively to certain projects where there was a strong focus on secure development practices. However, about a year ago, we adopted a more centralized and structured approach to using the framework across the organization.
The main reason for adopting OWASP SAMM was to gain better visibility into the maturity of our secure software development practices—both at the project level and organization-wide. It helps us identify strengths, gaps, and opportunities for improvement, enabling us to plan targeted actions and drive consistent security improvements across all teams.

What were the deciding factors to select OWASP SAMM?
One of the key deciding factors for selecting OWASP SAMM was its process-oriented approach, rather than focusing solely on specific tools or technical solutions. This allows us to evaluate and improve our security practices in a way that is flexible and adaptable to the unique needs of different teams and projects.
The framework provides a structured way to assess maturity while still giving us the freedom to choose how we implement certain practices. This balance between structure and flexibility makes SAMM a great fit for our organization, especially as we scale and standardize secure development across diverse teams.
What were the deciding factors for using SAMMY?
Beyond that, the overall implementation process has been relatively smooth—particularly because we’re using SAMMY, which makes it significantly easier to manage assessments and track progress in a centralized way. Without it, coordinating and analyzing the data would be much more difficult.
What are the biggest challenges in implementing OWASP SAMM?
The biggest challenge we’ve faced in implementing OWASP SAMM has been helping teams clearly understand the intent and meaning behind specific questions or practices in the model. It sometimes requires additional explanation to align everyone’s interpretation, especially when teams have different backgrounds or levels of experience with secure development.
What we really like about SAMMY is that it brings everything we need into one place
—assessments, progress tracking, and reporting are all centralized. Additionally, it offers automation features that save us time and reduce manual effort, making the whole process much more efficient and scalable. (Also, the ability to manage ISO27001 and NIST in the same tool)
What we appreciate most about working with Codific is the simple and non-intrusive communication. You always make sure to stay in touch without overwhelming us. Additionally,
your flexible approach to our needs has been incredibly valuable in adapting solutions to fit our specific requirements.

Project-Level Assessment

Organization-Wide Maturity Evaluation

Strategic Planning & Roadmapping
What are objectives in the use of OWASP SAMM and SAMMY. What do you hope to achieve?
Gain a Clear, Organization-Wide View:
We want to understand the overall maturity level of our secure development practices across all projects and teams. This helps us identify strengths, weaknesses, and trends at a glance.
Track Progress and Drive Improvement:
With SAMMY, we can monitor how each project evolves over time. This allows us to build structured improvement plans and track how our efforts translate into real progress.
What role do you think OWASP SAMM will play in the future for the industry?
I believe OWASP SAMM will evolve to become something similar to NIST in the future—a widely recognized and standardized framework for assessing and improving software security practices. As the industry continues to prioritize security, SAMM’s structured yet flexible approach will be essential for organizations looking to measure and enhance their security maturity. Its influence will likely grow, and it may become a go-to resource for businesses aiming to establish strong, sustainable security practices across their software development lifecycle.
Do you use any other frameworks other than OWASP SAMM?
Yes, we also use NIST and ISO frameworks, and I’m very pleased with how well they’re implemented. These frameworks provide valuable additional perspectives, allowing us to assess projects not just from the OWASP SAMM standpoint but also using broader, more holistic security and compliance benchmarks. Being able to evaluate projects across multiple frameworks gives us a deeper understanding of their security posture and helps ensure that our practices align with both industry standards and regulatory requirements. It adds another layer of robustness to our security assessments and planning.
What are your three favorite features or functionalities of SAMMY?
Additional Descriptions for Assessment Questions:
The extra descriptions provided for assessment questions are extremely helpful. They clarify the intent behind each question, ensuring that teams understand exactly what is being asked and can provide more accurate responses. This has improved the consistency and reliability of our assessments.
Would you recommend the use of OWASP SAMM to others? And if so, for which kind of situations/organizations would it fit best?
Yes, we definitely recommend using OWASP SAMM. It’s an excellent framework for assessing and improving internal development processes. It works particularly well for organizations that want to gain a structured understanding of their current security maturity and plan for improvements over time.
SAMM is also a great fit for internal projects, especially when aiming to build or standardize secure development practices. Additionally, it’s a valuable tool for organizations that offer security audits or assessments to clients—SAMM provides a clear, professional, and flexible framework to evaluate and communicate maturity levels in a consistent way.

Would you recommend the use of SAMMY to others? And if so for which kind of situations/organizations would it fit best?
Yes, I would definitely recommend SAMMY to others. It’s a great service
that makes the implementation and management of OWASP SAMM much easier and more efficient.
The platform simplifies assessments, centralizes data, and provides clear insights through dashboards and reports.
Do you have any advice for those who start implementing OWASP SAMM?
Yes—my main advice is to start by taking the training available on your portal. It provides a solid foundation for understanding the framework, its structure, and how to apply it effectively. The training will help teams interpret the questions correctly and get the most value out of their assessments from the very beginning.
Do you have any advice for those considering working with SAMMY?
Yes—just go for it. SAMMY is a very intuitive and well-designed platform that makes working with OWASP SAMM much more manageable. If you’re planning to assess multiple projects or want a centralized view of your security maturity, it will save you a lot of time and effort.
Also, take a bit of time to explore the features—like dashboards, reports, and question descriptions—early on. They really enhance the experience and help ensure your assessments are both accurate and actionable.
Is there anything we forgot to ask in these questions that you think is important? Anything you would like to add?
“I’d highlight the importance of community engagement and shared learning. Hearing how others use the framework, the challenges they face, and how they solve them can really accelerate adoption and improvement. It’s great to see that the ecosystem around SAMM is active and growing.
And finally—just a big thanks! Having tools like SAMMY and frameworks like SAMM makes our work not only more structured but also more impactful.”

Conclusions
This conversation with Oleksandr Zherebtsov underscores the growing need for structured, measurable approaches to application security, especially as development cycles accelerate and regulatory demands increase. Sigma Software’s adoption of the OWASP SAMM framework, and their use of tools like SAMMY, reflects a forward-thinking approach to building and maturing secure software practices.
By leveraging SAMMY to assess and continuously improve their security posture, Sigma Software is not only aligning with industry best practices but also driving real, actionable improvements across teams. The platform’s ability to operationalize OWASP SAMM and facilitate transparent, data-driven conversations around security maturity has made it a valuable asset for Oleksandr’s team.
Together, Sigma Software and Codific are demonstrating how practical tooling and a strong methodological foundation can help organizations embed security by design, effectively turning secure development from a challenge into a competitive advantage.