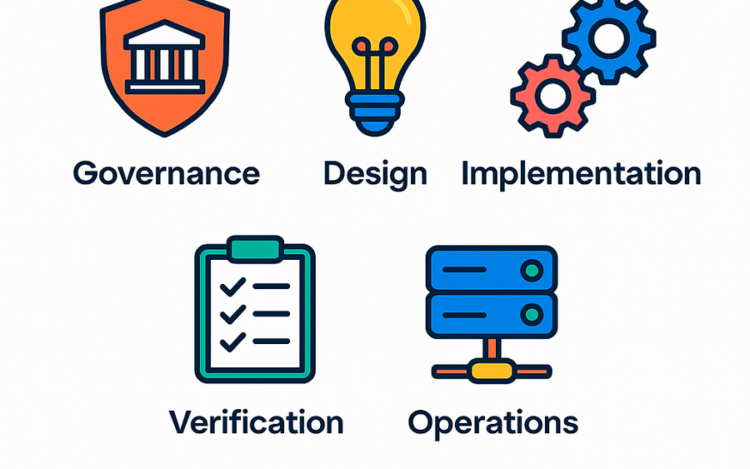
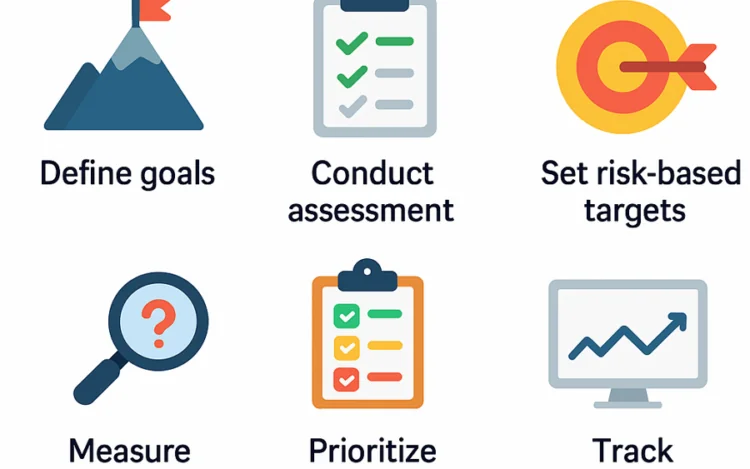
Security programs rarely fail because teams do not care. They fail because the work gets […]
The warning shots are over. The NIS 2 Directive is live, and enforcement has begun.[…]
As software systems grow more complex, proving that they are secure has become as important[…]
Most organizations conduct security assessments, yet few turn them into meaningful improvement. Traditional cybersecurity gap[…]
Automated Application Security Testing (AAST) refers to the use of software tools to identify vulnerabilities[…]
Finding vulnerabilities is not the hard part anymore. Every build and every pipeline produces a[…]
Your DevSecOps pipeline is fast, automated, and built to scale. But is security truly integrated,[…]
This article contains a variety of different cybersecurity statistics and trends of 2025 and recent[…]
Most security issues in software stem from one simple problem: teams try to fix them[…]
Modern software development moves fast, and so do the security challenges that come with it.[…]
Understanding OWASP SAMM is only the beginning. The real value comes from using it to[…]
Have you every been hacked? It sucks right? But don’t worry now, let’s make sure[…]