“Cyber serenity to society” is more than a catchy tagline, it’s a high‐stakes promise.
Approach Cyber, a pure‑play cybersecurity and privacy partner, does exactly that. Known for its wide array of services, from phishing awareness and GRC to secure application development and cloud security, they empower organizations to focus on their core business while Approach Cyber handles the cyber risk landscape.
At this scale cybersecurity firms face increasing complexity and workload. That’s where SAMMY, comes into the picture. Originally born out of Codific’s internal needs for better AppSec tracking and prioritization, SAMMY now helps organizations globally turn static maturity models into dynamic, actionable roadmaps.
SAMMY isn’t just about assessments. It enables structured evaluation and validation of security activities, assigns responsibilities, and supports prioritization aligned with risk and business direction.
It was in this fertile intersection of expertise where Approach Cyber and Codific found their synergy. As a trusted SAMMY Implementation Partner, Approach Cyber has been able to integrate SAMMY into its secure‑development offerings, strengthening their ability to deliver tailored, measurable, and scalable AppSec programs for clients.
Listen to this episode on the Appsec Management Podcast.
In this interview we talk to Simon Monteyne, application security consultant at Approach Cyber, about their use of OWASP SAMM and SAMMY. We explore the successes and challenges involved with scaling AppSec consultancy business with SAMMY. More specifically:
- How Approach Cyber embedded SAMMY into their service portfolio, and how that transformed their client outcomes.
- Codific’s role in ensuring SAMMY remains open, flexible, and connected to frameworks like OWASP SAMM, NIST frameworks, and even OpenCRE.
- Preparing for CRA and other regulations: How SAMMY helps making compliance efforts more effective.
What is Approach Cyber?
Approach Cyber is a company specialising in cyber security solutions and consulting. Our core mission is to help organisations safeguard their digital assets, ensure compliance with evolving regulations, and build resilient security strategies tailored to their unique needs. By combining deep technical expertise with a hands-on, client-focused approach, Approach Cyber supports businesses in navigating complex cyber risks, implementing best practices, and responding effectively to threats as the digital landscape evolves.
Founded more than 20 years ago, Approach Cyber was first a classical IT company. Over the years, Approach Cyber has evolved alongside the industry and embraced the growing need for robust, adaptable digital protection in an era of rapid technological change.
What are the main service categories you provide?
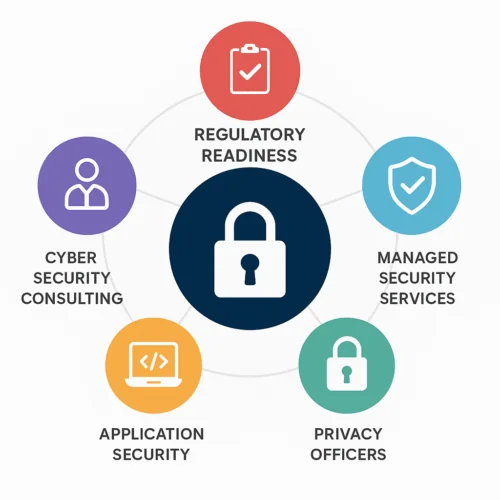
Approach Cyber delivers a comprehensive 360° portfolio of cyber security services aimed at addressing diverse challenges in the digital age. Our mission is to protect digital assets, ensure regulatory compliance, and develop tailored security strategies for organisations. The portfolio spans key areas such as cyber security consulting, managed security services, application security, privacy officers, and regulatory readiness.
How does OWASP SAMM fit in this picture?
In the Secure Application part of our portfolio, we do offer Secure Application Assessment, for which we use the OWASP SAMM framework. It is instrumental as it provides a structured framework to assess our customers’ maturity levels. By identifying strengths and gaps, SAMM enables us to design tailored application security programs that align with their specific needs and priorities, ensuring effective and scalable solutions, for which we also like to offer guidance and advisory services.
When did you start using OWASP SAMM?
Although we’ve already been using it in our own Software Factory, we started using the framework for external assessments around 5 years ago.
How is OWASP SAMM effective for your customers?
OWASP SAMM is highly effective for our customers because its framework not only identifies strengths and gaps but also introduces actionable metrics, enabling organisations to measure their progress across defined maturity levels. By simplifying complex processes into manageable steps, SAMM empowers teams to design and implement tailored application security programs that align with their goals, ensuring results that are both measurable and scalable.
How does SAMMY help you serve your customers?
SAMMY serves as a critical tool for enhancing collaboration among various stakeholders. By allowing multiple users to contribute input and conduct reviews, it fosters a cohesive approach to addressing application security challenges, as well as lowering the workload for us, as external assessors.
In addition to fostering teamwork, SAMMY centralises documentation in one accessible location, making information management seamless. This aggregation not only simplifies the process of maintaining consistency across records but also enables the direct generation of comprehensive reports. Such streamlined functionality saves time and effort while giving organisations the insights they need to measure progress effectively and make informed decisions.
Moreover, SAMMY provides a user-friendly interface that facilitates the tracking of progress throughout the implementation journey. Teams can monitor their advancement across maturity levels and identify areas requiring attention. Including the teams in the process really helps in changing mindsets across the organisation and making the teams grow in responsibility, ownership and maturity.
This all-encompassing approach transforms SAMMY into an invaluable ally for organisations striving for continuous growth and security excellence.

Simon Monteyne,
Application Security Consultant
What are some of the new regulatory requirements your customers are most concerned about?
Many of our customers have already begun conducting assessments to lay the groundwork for ISO27001 implementation or to ensure compliance with NIS 2 directives. At the same time, the pressure surrounding the upcoming Cyber Resilience Act (CRA) is intensifying. With a vast number of organisations likely to fall within the scope of this regulation, the momentum for preparations is expected to accelerate significantly in the coming months.
However, a key challenge remains: many small and medium enterprises (SMEs) are still unaware of these impending obligations. This gap in awareness poses a significant risk, as SMEs are often just as vulnerable to cyber threats as larger enterprises. Addressing this issue will require targeted outreach and education efforts to ensure that all organisations, regardless of scale, understand their responsibilities and take the necessary steps to comply with these evolving standards. Only through such collective action can we hope to create a resilient and secure digital landscape for all.
How do you help your customers prepare for these regulatory challenges?
One of the notable strengths of the OWASP SAMM framework is its inherent ability to map effectively with various other frameworks and regulations. This adaptability allows organisations to streamline their compliance efforts and ensures that their application security practices align with broader regulatory requirements.
Furthermore, SAMMY plays a pivotal role in automating these mapping processes. By centralising the framework’s capabilities, SAMMY reduces manual workload and enhances accuracy in identifying overlaps between SAMM and other frameworks or regulations.
What advice do you have for organizations preparing for CRA?
Start now. Truthfully, many organisations are not yet ready, and implementing a robust SSDLC takes time – on average, it takes up to 2 years to prepare for that kind of regulation. Furthermore, people are generally reluctant to change, so the implementation of new security practices should be done slowly, step by step, in order to boost adoption rate.
The first step would be of course to assess the current posture and plan what should be done.
Are the preparations different for different companies? If so, does it depend on scale, public vs private, anything else? And how is it different then?
The preparations indeed vary across organisations. Factors like size, industry-specific risks, and whether the entity is public or private significantly shape how they approach compliance. Generally, larger organisations already have a higher maturity, with processes in place, and should be more or less ready with CRA for example. The challenge lies for SMEs or public sector, where budget is often a constraint.
How has the Software/AppSec industry changed in the past years?
The evolution from traditional development and operational practices (dev/ops) to the streamlined collaboration of DevOps marked a significant shift in the software industry, breaking down silos and fostering efficiency. Now, we stand at another critical juncture with the emergence of DevSecOps, where security is no longer an afterthought but an integral part of the development lifecycle.
This transformative approach is driven by the principle of “shifting left,” embedding security practices earlier in the process—right from the design and development phases. By doing so, teams can proactively address vulnerabilities, ensure compliance, and mitigate risks without waiting for deployment.
What trends do you see going forward?
The integration of automated security tools, continuous monitoring, and secure coding practices will become more and more essential, as organisations strive to enhance their resilience against ever-evolving threats.
DevSecOps reflects the industry’s recognition that security cannot exist in isolation but must be woven seamlessly into collaborative workflows. This shift empowers teams to deliver secure, reliable software faster, setting the stage for a robust future in application security.

Is the industry evolving fast enough to face the changing threat landscape?
The latest annual pentest report from our red team highlighted that 37,9% of their findings for web/API were still High or Critical issues, showing that the industry still has some progress to do.
This situation arises because attackers are constantly evolving, seeking out new vulnerabilities and methods of exploitation, while security remains just one concern among many for businesses. Developers, often juggling tight deadlines and the demand for rapid innovation, must continuously balance the need for robust security with the pressure to deliver new features and updates.
Is the industry evolving fast enough to face the changing threat landscape?
Yet, there’s a silver lining: awareness of security’s critical importance has grown significantly. As this awareness spreads, organisations are implementing more structured processes and adopting tools designed to mitigate risks, striving to prevent as many vulnerabilities as possible without compromising the pace of development.
Involving more and more people in the security practices of an organisation and integrating them in the process are the main gates to higher our defences and prepare for a future that will bring even more threats.